
News: Bloodsucking Flies Act as 'Flying Syringes' to Detect Malaria & Other Emerging Diseases in Wild Animals
Researchers have been studying the blood meals of flies to understand the flow of infectious pathogens in wild animals.


Researchers have been studying the blood meals of flies to understand the flow of infectious pathogens in wild animals.

When we think of pickling, we usually think of using veggies like cucumbers, carrots, and peppers. However, with summer upon us, we found ourselves thinking about fancy pickled berries as a novel way to use all those gorgeous gems that are popping up at the market.

As you get barbecuing this summer, you're likely to encounter a few grills that aren't exactly the cleanest. At parks or campgrounds and even on your friends' grills (or, um, your own), no one wants to place food on gunked-up grill grates.

Summertime means lots of parties, picnics, and barbecues—and wherever a group of fun-loving adults can be found basking in the sun's rays, delicious cocktails are sure to flow freely.

Google is pushing out an update for its namesake Google app that lets you get a little creative with the way the Google logo appears. You'll be able to add your own color scheme to the Google logo, and include colors beyond the traditional blue, red, yellow, etc.
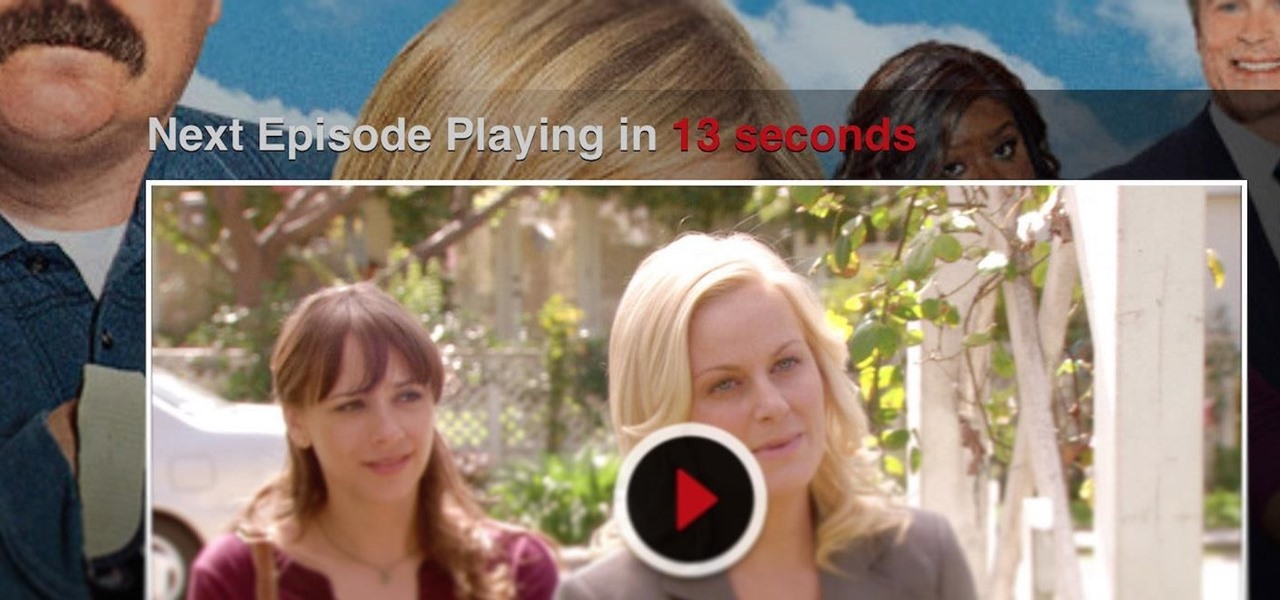
Cord cutters are changing everything about TV—the more of us that sever ties with cable, the more changes we start to see. In fact, viewing habits have already changed so drastically that waiting a week to see the next episode in a series is no longer acceptable, as binge watching has completely eclipsed this old-fashioned format.

The notification light on phones and tablets is slowly disappearing. The once staple feature is now only found on a few devices, and a bevy of other notification systems have sought to fill the gap. The most popular of these systems is Ambient Display, which has grown in popularity with OEMs over the last couple of years; even Google's own Nexus line of phones have made the plunge.

It's easy to grab a box of pre-prepared microwave popcorn at the grocery store. Yet with so much salt, butter, and other unpronounceable ingredients, microwave popcorn can go from a healthy snack to a complicated one.
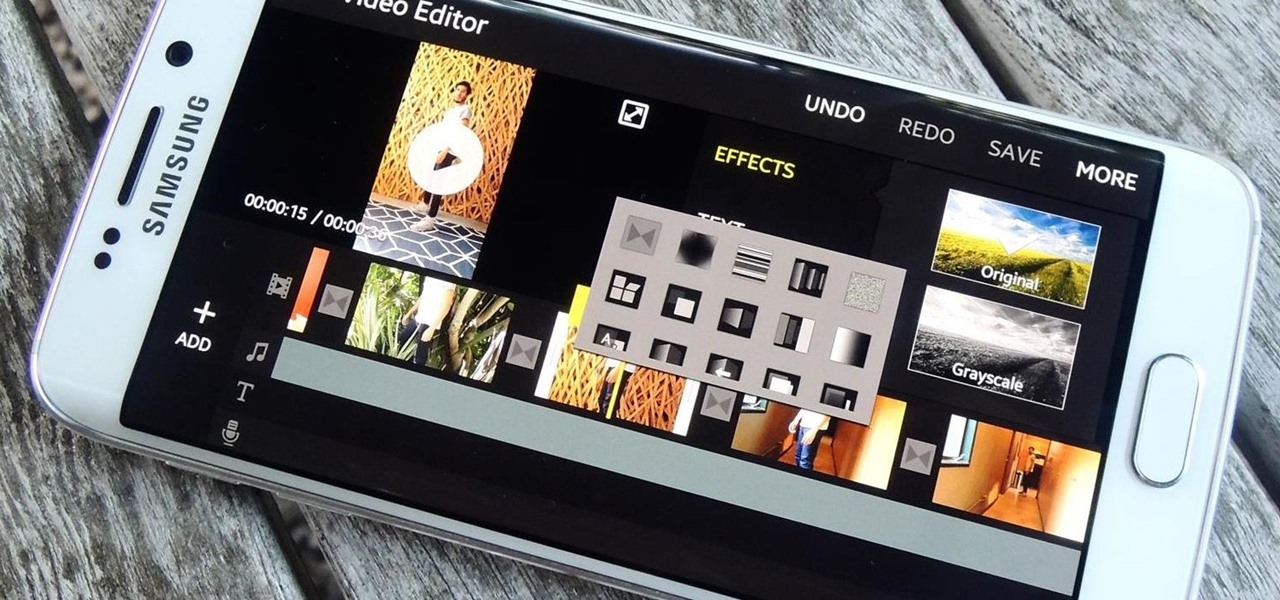
Editing a video by trimming or adding audio is fairly simple on Galaxy devices, but if you want to include other clips or transition animations and really get those creative juices flowing, you might find the standard editing tools limited—unless you know how to unlock Samsung's hidden video editor.

What's not to love about a glass of wine? It tastes delicious. It takes the edge off your day. It helps you and your guests unwind and lets the conversation flow. All in all, it's a beautiful thing. What's not so beautiful is having someone knock over a giant glass of red and leave an indelible stain on your carpets or furniture.

Meat tenderizers are absolutely necessary when dealing with leaner, tougher cuts like flank or skirt steaks. And while fruit like papaya, kiwi, and pineapple contain enzymes that can tenderize meat, the results can be hit-or-miss, and impart a fruity flavor that you may not always want.

How many times do you think you press the Home button on your iPhone? You probably can't place a number on it, but you know it's a lot.

As you already know, Hong Hong has been rocked in recent weeks by protests against their Beijing overlords. Promised free and fair elections, Beijing has reneged on this promise and is now telling Hong Kongians (that's what they're called, aren't they?) that they will only be able to vote on Beijing-selected candidates. All that is interesting from a political perspective, but from a technological perspective, the more intriguing story is how the protesters are communicating. Faced with their...
If you've followed our guide on unlocking KitKat's real full screen capability using the immersive mode mod, then your status and navigation bars will be hidden when not in use, giving you a more expansive full screen experience.

Sometimes, ceiling fans just don't cut it. They spin meekly, barely generating any air flow to cool down your sweltering room. Or, when turned up high, they can wobble wildly, shaking and vibrating as if the ceiling is about to come crashing down. If this sounds like your ceiling fan, chances are the solution is a simple as flipping a switch.

You've seen the Samsung Fingers and the Emoji Translator, and I know you spent a good part of the day catching Pokémon, but now that April Fool's Day is officially upon us, the flood of gags has reached a tipping point. Here's the best of what we've seen today.

I never really cared much for the clock widget on my Nexus 7, mainly because it only gave me two styles—analog and digital. There are many different styles of clock widgets available on Google Play, but the majority of them just don't look good enough for me.

I know that after seeing 8 Mile for the first time, you and your friends tried a few freestyles yourself. Nothing to be embarrassed about. As one person dropped the beat, you started your stuttering flow, and everyone else nodded their head. And for a second you probably thought you sounded pretty good, until the beat maker started coughing and threw you off.

You have an abundance (or scarcity) of alcohol, liqueurs, and chasers, but don't know how to combine or mix them together to produce some kind of enjoyable concoction for friends. What do you do? Mix things you think will taste good together? They probably won't. There's rules about clear alcohol vs. dark alcohol and how they pair with juices and sodas, so what's the best way to know what goes well with what?
The first alarm clock in recorded history can be traced back to ancient Greek philosopher Plato, known for laying the foundations of Western philosophy and science. Plato was said to possess a very large water clock with an alarm signal similar to that of a water organ.

Ever wondered what the inside of a burning rocket looks like? Well, thanks to Valve engineer Ben Krasnow, now we know. He built a homemade hybrid rocket engine that's see-through so you can actually watch how it works. And even though it's probably a really bad idea to try this at home, he made a video so you can build one, too. Just don't say I didn't warn you.

Destroying crowds of little people has been a favorite passtime of dictators since time immemorial, but also a colossal waste of manpower. Now you can get some of the same thrill without all the needless death using 3D Studio MAX. This video will show you how to model, animate, and duplicate with particle flow a series of small robots. Then it will show you how to use a collision object (here a meteor) to destroy them all in fiery glory.

Find out how everything in a chemistry lab works, from pipettes to burners to recrystallization to storage. You'll get precise instructions on how to work and perform certain scientific duties in the chem lab, whether it's chemical or just ordinary high school science.

The video shows you in simple easy steps how to draw Snoopy from Charlie Brown. It starts with a single line drawing the ear and the head then adding the neck, nose and eye, adding shading. Then a simple triangular shape for the body, adding the hands. Simple circles are used for the feet, connecting them to the basic triangle shape and adding a tail. Removing the triangle shape then gives the body flow and then adding the collar and feet finally gives you the Snoopy character from Charlie Br...

This video massage tutorial shows how to perform a Swedish massage on the back. The massage techniques are performed twice to demonstrate the detailed techniques, including biomechanics, as well as to show proper flow of a massage. Watch this instructional video and learn how to give a back massage using the Swedish style.

This video massage tutorial shows how to perform a Swedish massage on the abs, chest, neck, and face. The massage techniques are repeated a few times, to allow thorough explanation of how to flow through the moves, as well as detail about the biomechanics of massage. Watch this instructional video and find out how to give a Swedish massage.

Whether you're in an airport, restaurant or waiting room, the insidious grip of televisions on human life is omnipresent. Sometimes it's nice to talk to other human beings while looking at them directly—actually hearing what they have to say.

In a previous guide, I demonstrated how to extract images from a security camera over Wi-Fi using Wireshark, provided you know the password. If you don't know the password, you can always get physical with the Hak5 Plunder Bug. Using this small LAN tap, we can intercept traffic like images from a Wi-Fi or IP security camera if we can get physical access to the Ethernet cable carrying the data.

As people continue to upgrade their PCs to Microsoft Windows 8, more and more developers are adding content to the Windows Store. While the offerings are not as vast as Google Play or the iTunes App Store, it does have some solid apps for both productive users and those looking to just while away the time.

This is a video teaching how to freestyle rap using three rules. The first rule is to freestyle all the time. Freestyle by yourself. Listen to some beats by yourself in your room with the first thing that comes into your mind. The second thing is to make sure it flows. Do not stutter. Keep practicing until it comes out smoothly. The third rule is do not stop rapping. In other words, don't take breaks for weeks or months otherwise you will get rusty. It will take time to get good at it again i...

In this video tutorial, you'll find a demonstration on how to iron a skirt, using Primula Flex 1242 ironing table. The PRIMULA Flex 1242 ironing table has a working surface 120x42cm with a sleeve ironing buck. The board also features suction and blowing with stepless adjustment of air flowing, automatic interchange suction or blowing from the working surface to the buck in addition to heating of the working surface and buck. The technical parameters are as follows: Power supply 400V/50Hz, suc...

Partner Yoga is a unique physical and spiritual practice which combines powerful techniques and exercises from yoga. Partner yoga uses poses (asanas) to focus the mind and increase strength, stamina and flexibility. The poses are combined with breathing techniques (prananyams)

Partner Yoga is a unique physical and spiritual practice which combines powerful techniques and exercises from yoga. Partner yoga uses poses (asanas) to focus the mind and increase strength, stamina and flexibility. The poses are combined with breathing techniques (prananyams)

Partner Yoga is a unique physical and spiritual practice which combines powerful techniques and exercises from yoga. Partner yoga uses poses (asanas) to focus the mind and increase strength, stamina and flexibility. The poses are combined with breathing techniques (prananyams)

Partner Yoga is a unique physical and spiritual practice which combines powerful techniques and exercises from yoga. Partner yoga uses poses (asanas) to focus the mind and increase strength, stamina and flexibility. The poses are combined with breathing techniques (prananyams)

According to Google at their 2018 I/O conference, Google Assistant is now available on over 500 million devices. Now that the assistant is available on iPhones as well, Google has to give iOS users a reason to switch to its assistant over the built-in Siri. Today, Google has eight more reasons for users to do so.

In the perpetual search for a renewable and convenient energy source, our bacterial friends have once again stolen the limelight.

How do I get rid of these zits?! Whether its pimples, blackheads, or whiteheads, the name is the same, and the name is acne.

By now, nearly everyone with any type of media access is aware that Sony Pictures Entertainment was hacked on November 24th. Although there can be many interpretations and lessons drawn from this audacious act, there is one indisputable conclusion: it and its ripples across the globe underlines how important hacking has become in our all-digital 21st century. As I have emphasized so many times in this column, hacking is the discipline of the future. From cybercrime to cyber intelligence to cy...

The drinking straw isn't just there to help you make annoying noises when you get to the bottom of your soda. That little tube of plastic is extremely versatile and can make your life a lot easier with a little know-how. Curious? Read on to find out more.