Nearly every native app on the iPhone received an upgrade or new features in iOS 14 — and Safari is no exception. The web browser now has better password protection, faster performance, privacy reports, and built-in translations, just to name a few. Some of the Safari updates went unnoticed by many, but they're there and ready to use in iOS 14.

The original iPhone SE was, for some, the perfect iPhone. It brought back the popular one-handed form factor of the iPhone 5 but packed in the internals of the then-new iPhone 6S. Now, the second-generation iPhone SE is here for 2020, but can it live up to what made the first-generation iPhone SE so popular?

You might think you need to buy a thousand dollar phone to get a great experience while streaming movies and TV shows from services like Netflix, Hulu, and YouTube, but that's just not true anymore. While phone prices keep rising and the midrange segment now ranges from $300–$500, there are still cost-effective options that come with top-notch displays and media features.

You can mod every aspect of your phone's software with root, but if you want to make changes at the hardware level, you'll need a custom kernel. If you've looked into custom kernels before, one name undoubtedly kept coming up: ElementalX. It's easily the best custom kernel out there, and the reason for that is its awesome developer, flar2, aka Aaron Segaert.

Apple's successor to the iPhone X is a beautifully made smartphone with much of the same characteristics, including a 5.8-inch OLED screen, two storage choices, and Face ID. But many features set the iPhone XS apart from its predecessor, as well as the other 2018 lineup of iPhones, making it a worthy choice to upgrade to if you're in the market for a new mobile device.

Airgeddon is a multi-Bash network auditor capable of Wi-Fi jamming. This capability lets you target and disconnect devices from a wireless network, all without joining it. It runs on Kali, and we'll cover installing, configuring, and using its jamming functionalities on a small, inexpensive Raspberry Pi. When done correctly, it will deny service to a wireless network for up to several blocks.

No more carrying around heavy laptops and thousands of Linux Live CDs and USBs to always be ready for pentesting on the fly!

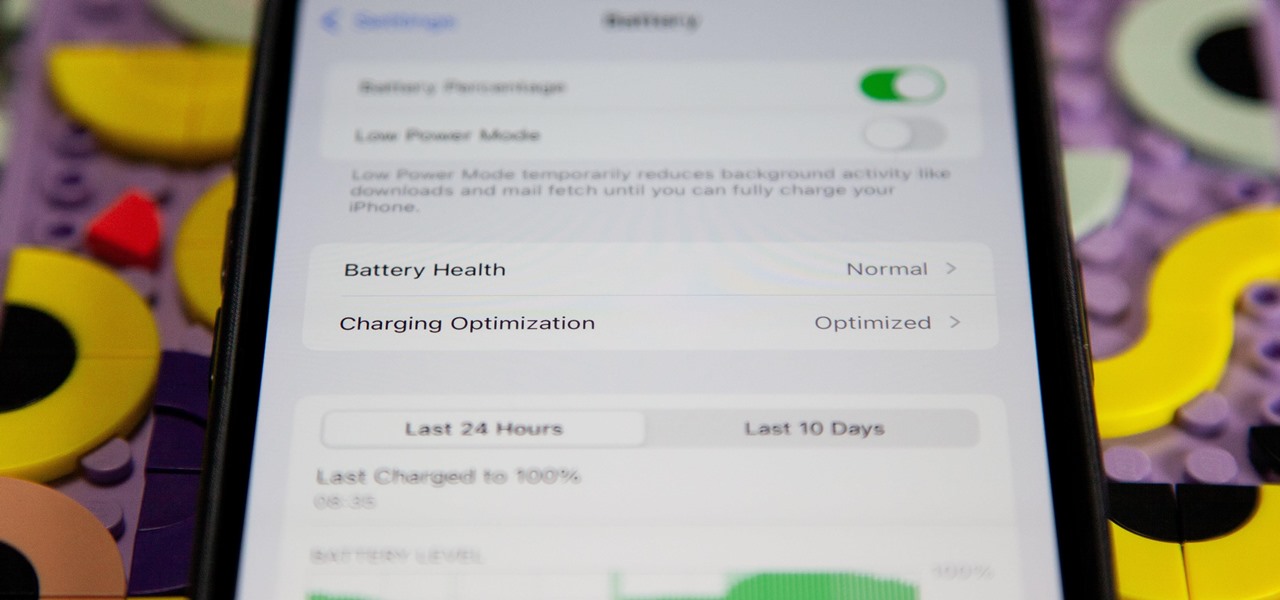
If you're ever curious about your iPhone's battery health, there are easy-to-access stats that let you know the last charge amount, which apps are eating away at most of your power, and even your battery's remaining capacity. Now, a new update makes it easier to know how well your battery is doing.

It can feel pretty chaotic when you have a lot of open windows on your Mac that are different sizes, but there's an easy way to organize the mess in just a few seconds.

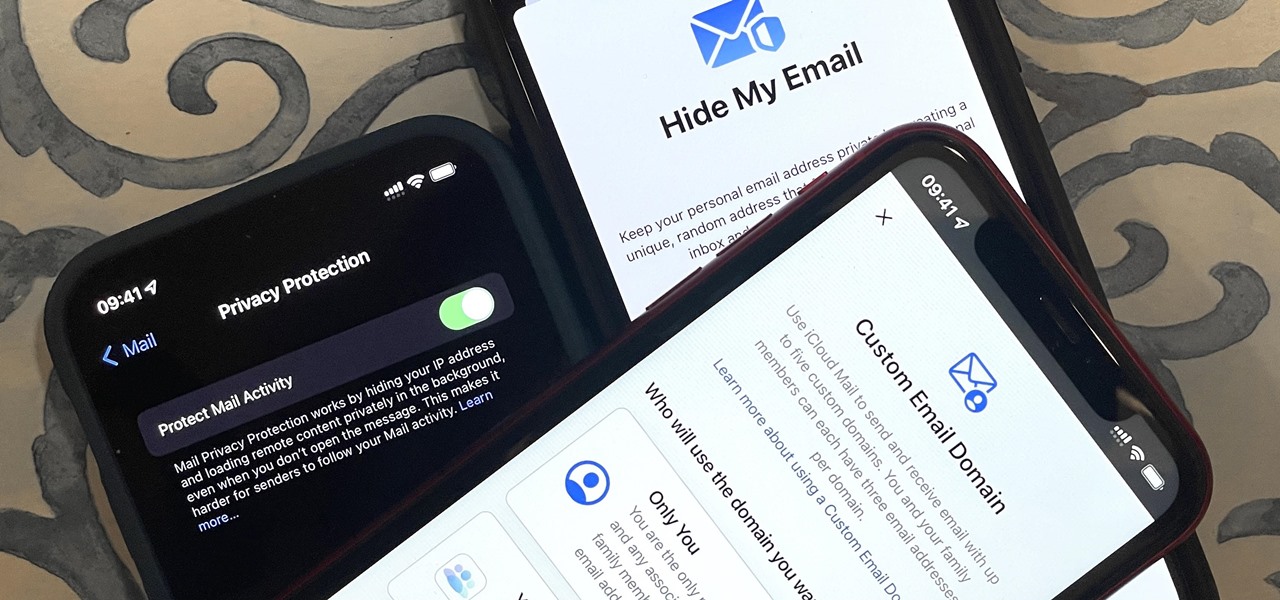
Privacy is a growing concern in the tech industry, but Apple has fallen behind many of its peers when it comes to email security. Fortunately, iOS 15 changes that. Your email address is the key to a vast amount of personal information, not to mention a stepping stone into your other online accounts, so it's great to see new features for iPhones that protect email accounts and their contents.

Facebook Reality Labs chief Andrew "Boz" Bosworth does a lot of hinting and teasing of what's coming next at Oculus, often with only a vague timeline on the horizon.

Apple released the fourth beta for iOS 14.7 today, Tuesday, June 29. The update comes 15 days after iOS 14.7 beta 3, and restores battery service messages that may have disappeared after reboot on some iPhone 11 models.

After tapping Nvidia for its first AR headset, Magic Leap is calling in reinforcement for its future enterprise-focused efforts.

Having the right air quality can turn a room into an atmosphere. With a humidifier, you can see your skin dewy and your sinuses clear. Proper temperature control will keep you comfortable and content, and the right air purifier will give you clean air and peace of mind. If you're in the market for a humidifier, an air conditioner, a heater, or an air purifier but just need to find the perfect one to match your needs and your budget, then check out some of these great deals.

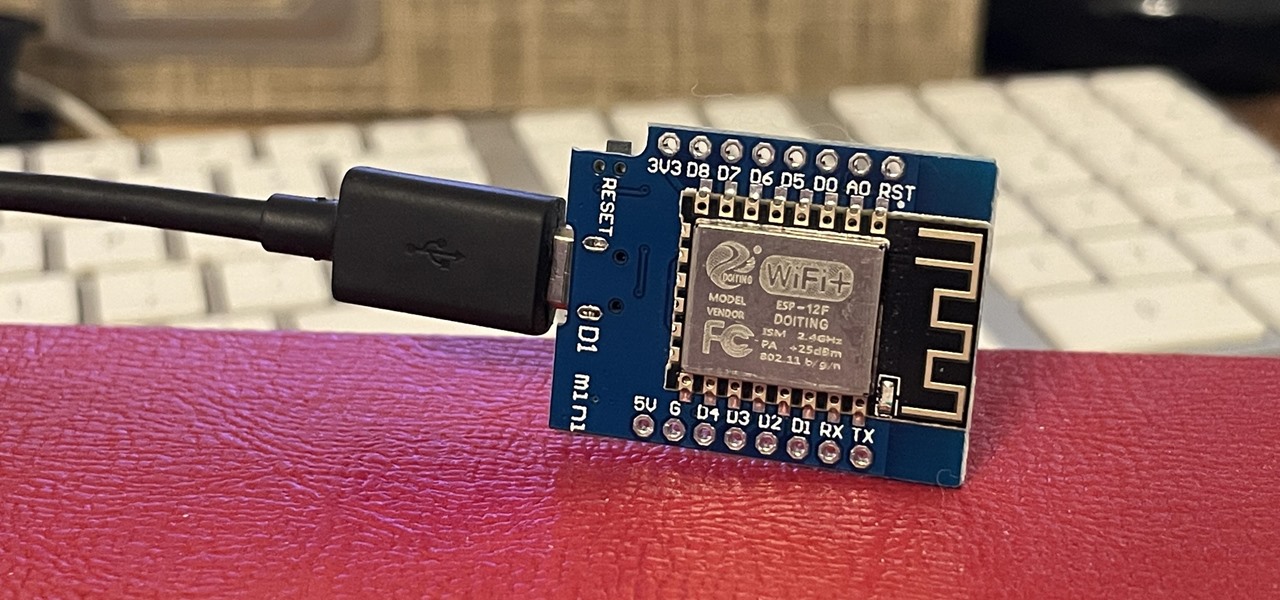
If you've wanted to get into Wi-Fi hacking, you might have noticed that it can be pretty challenging to find a safe and legal target to hack. But you can easily create your own test network using a single ESP8266-based microcontroller like the D1 Mini.

While there are completely legitimate reasons to use Bitcoin, it's also used by terrorists, drug dealers, and other shady people that need to be investigated. That's where SpiderFoot comes in, which has a command-line interface to search for Bitcoin wallet addresses on a website and query the balances associated with them.

On a PC, you can play sound from multiple apps at once. It's great, but it can also be confusing — there's a volume slider in each app, then the system-wide one, and probably another knob on your speakers. To avoid this dysfunction, Android only has one sound stream for media. But that has its own problems.

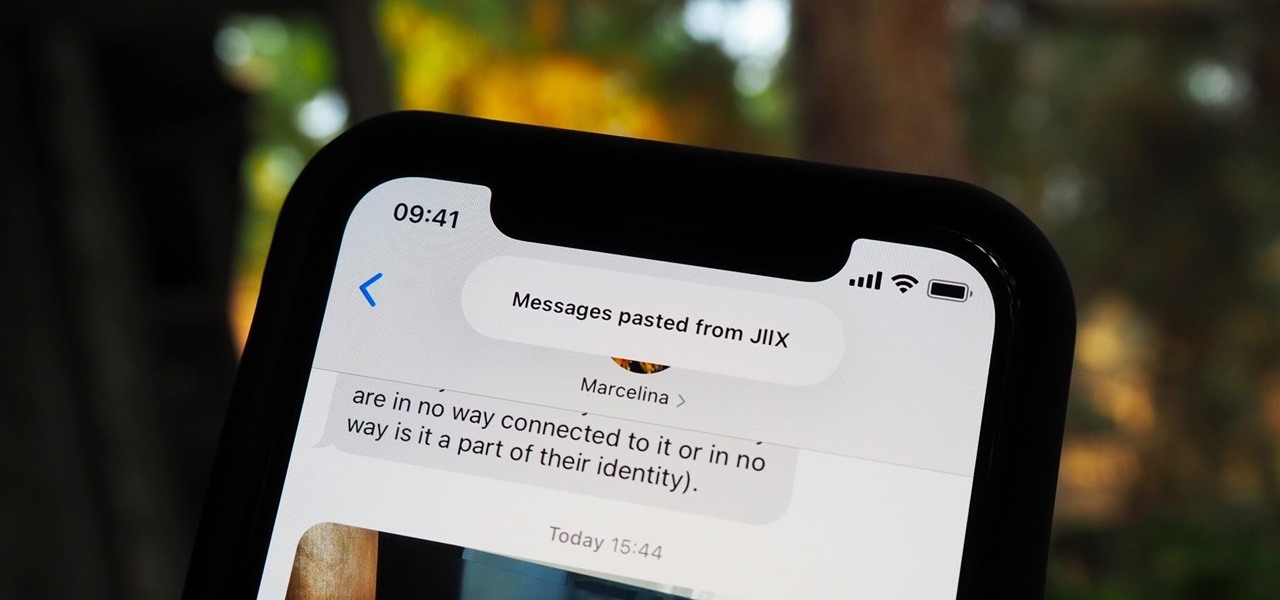
Continuity connects all of your Apple devices so that they all work seamlessly together. For instance, you can start tasks on one device and finish them on another, view and send text messages or make calls on your iPhone from your iPad, iPod touch, or Mac, and even use an iPad as a monitor for your Mac. Its Universal Clipboard feature is also really useful, but it can also be quite annoying in iOS 14.

One thing about the small round little Pixel Buds — they might get lost easily if you have a terrible habit of misplacing stuff. Or worse, imagine someone taking a liking to them a little too much and stealing them when you aren't looking. Google thought ahead about these issues, so just like your smartphone, you can track your wireless earbuds from anywhere with ease.

Battery management is a never-ending struggle. To be on the safe side, you likely won't want to leave your home with less than 100% battery, but continually checking your charging iPhone is a hassle. Instead of continuously monitoring your battery's power level, have your iPhone tell you when it's reached a full charge.

Despite some early and optimistic predictions that the world would have returned to normal by now, the surprisingly stubborn and resilient coronavirus continues to upend and alter how we live our lives when it comes to working from home instead of the office.

At the beginning of every year, Samsung drops a fantastic phone in the Galaxy S series, and then tries to top it with the Galaxy Note series in August. This year, Samsung had their work cut out for them. But they managed to improve on their predecessor and properly challenge Apple's best.

In a world that's becoming increasingly dependent on a variety of AI and machine learning applications, Big Data reigns supreme. As the primary forces behind everything from self-driving cars and surgical robots to home automation systems and even space exploration, Big Data and AI stand at the heart of today's most important innovations.

Attacks against databases have become one of the most popular and lucrative activities for hackers recently. New data breaches seem to be popping up every week, but even with all of that attention, databases continue to be a prime target. All of these attacks have to start somewhere, and we'll be exploring a variety of methods to gather information on PostgreSQL databases with Metasploit.

While we haven't covered Amazon Web Services, or AWS, on Null Byte before, Amazon's cloud computing platform is ripe for attack by hackers, pentesters, and cybersecurity researchers. It's also an excellent cloud hosting service to build or use vulnerable-by-design AWS setups and frameworks.

The 2020 iPhone SE had been through the rumor mill for a long time, but Apple finally unveiled the second-generation iPhone SE on Wednesday, April 15. While it doesn't sport the 4-inch design of the original SE, it combines a small form-factor with modern specs. The big question, of course, is when and how you can get your hands on one.

Using a strong password is critical to the security of your online accounts. However, according to Dashlane, US users hold an average of 130 different accounts. Memorizing strong passwords for that many accounts is impractical. Fortunately, password managers solve the problem.

Whether you're trying to become an influencer or just want to share better photos and videos, the best camera to start with is your smartphone. It is likely the only camera you always have on you and it's probably capable of excellent pictures and video capture. But with a little help, it could definitely be better.

Are you thinking about upgrading your iPhone this year? Apple sure wants you to. Of course, that's no different than any other year, but Apple really wants you to upgrade this year. How do we know this? The rumors point to not three, not four, but five brand new iPhones in 2020, with two very different release schedules. All this begs the question what the hell is Apple thinking?

Back when I worked in the music industry, I never imagined there would be a day that I'd be able to sit in a room surrounded by virtual album covers while listening to beats, but that day is really here.

The year 2019 was filled with all the normal peaks and valleys of the tech business cycle, but this year was particularly important in a space as relatively young as the augmented reality industry.

Chance are, you or someone you know is that person in the gym: flexing in front of a mirror, posing for the perfect photos to show off your workout results. But finding the right picture is hard. The thing is, it doesn't need to be.

Black Friday is upon us. Whether you prefer to duke it out in stores or calmly shop online, there's no doubt you'll find great deals on the items you're looking for this holiday season. It's the perfect time of year to buy something expensive, like a good pair of AirPods, Beats, or Bose, at a much more opportune price.

Windows 10 passwords stored as NTLM hashes can be dumped and exfiltrated to an attacker's system in seconds. The hashes can be very easily brute-forced and cracked to reveal the passwords in plaintext using a combination of tools, including Mimikatz, ProcDump, John the Ripper, and Hashcat.

Christmas is just one week before Jan. 1. That means a lot of New Year's resolutions filled with promises to better ourselves with increased productivity, focus, and work ethics — but getting started can be challenging. Give the people in your life a leg up this holiday season with these smartphone gifts to keep them on-task in 2020.

You may not have thought of dorks as powerful, but with the right dorks, you can hack devices just by Googling the password to log in. Because Google is fantastic at indexing everything connected to the internet, it's possible to find files that are exposed accidentally and contain critical information for anyone to see.

So you've been playing Call of Duty Mobile for some time but can't seem to get MVP at the end of the battle. Well, since the game is a competition of players and bots, you're in an uphill battle. But you don't have to languish at the bottom. With the help of these tips, you might just nab your first MVP.

Apple has seemingly always made it a priority to show how much it cares about user security and privacy — enough that it has a page dedicated to it, proclaiming that "privacy is a fundamental human right." It's true that there are few issues more important than user privacy when it comes to technology, and Apple only makes things better in iOS 13.

So you can't figure which one to buy. It's understandable. Apple released three iPhones, each designed for a different segment of the market. But which one is right for you? The iPhone 11, iPhone 11 Pro, or iPhone 11 Pro Max? That's a good question.

Surprising? No. Exciting? Absolutely. After a grand introduction by at the Apple event on September 10, 2019, the iPhone 11 is finally here. We may have known nearly everything about this new iOS device ahead of time, thanks to the usual surge of reliable leaks and rumors.