With tools such as Reaver becoming less viable options for pen-testers as ISPs replace vulnerable routers, there become fewer certainties about which tools will work against a particular target. If you don't have time to crack the WPA password or it's unusually strong, it can be hard to figure out your next step. Luckily, nearly all systems have one common vulnerability you can count on — users!

You've likely seen light-up musical keyboards that teach you how to play a song with visual cues, but few of those devices exist and have a limited number of songs you can actually learn. But Karl Baumann and his HoloLens Hackathon team figured out that in mixed reality, you can learn music with visual cues with any piano.

Mixed reality filmmaking isn't a new concept. Disney managed to make it work in 1988 with Who Framed Roger Rabbit, but not without an enormous amount of work. We haven't seen many mixed reality films of that scope since, and perhaps that's because it's still hard to accomplish. Filmmakers don't look through a viewfinder or monitor and see the fully rendered result on screen—but that can change with mixed reality headsets like the HoloLens.

If you've noticed a tiny discolored spot on your computer screen that just doesn't seem to go away, chances are you have a stuck pixel. With modern LCD and OLED screens, there are millions of incredibly small dots (pixels) that make up all of the contents of your display—and within these pixels, there is a set of red, green and blue subpixels. These mix together at various levels to create all of the different colors you see.
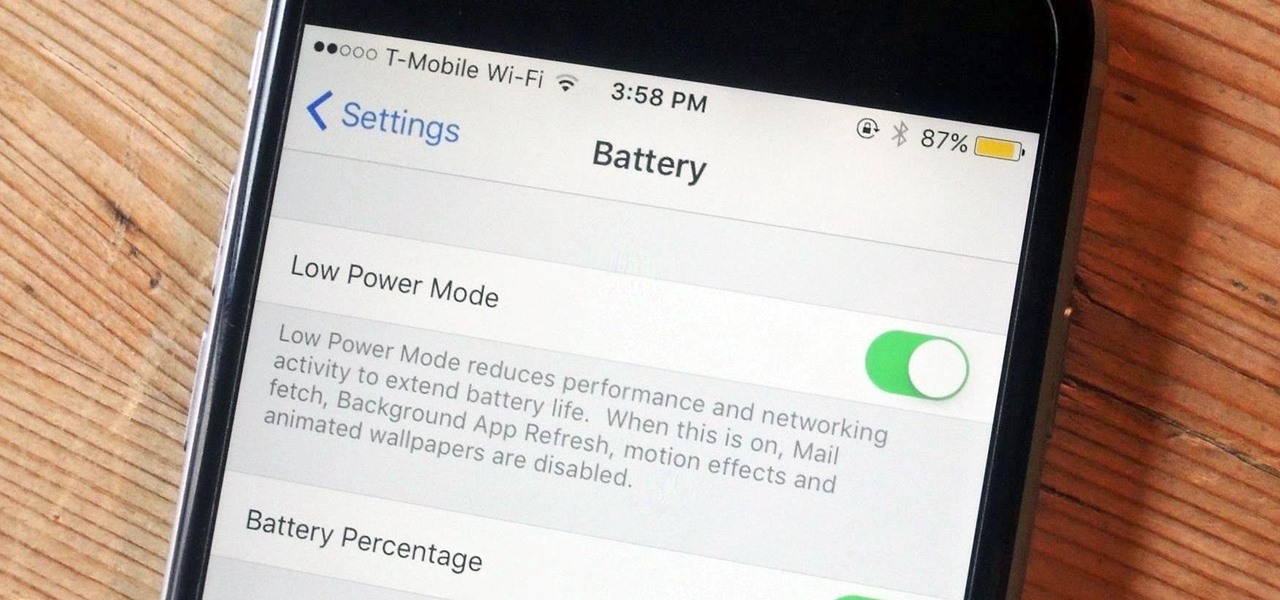
One thing Apple users universally complain about is battery life, whether it's on an iPad, iPhone, or Apple Watch. Apple did include a Battery Usage feature in iOS 8 to help us monitor which apps suck up the most energy, but it's too big a pain to deal with. Now, in iOS 9, there gave us something that actually matters—Low Power Mode.

Welcome back, my aspiring hackers! In many of my earlier tutorials, I mentioned the complementary nature of hacking and forensics. Both disciplines, hacking and forensics, benefit from a knowledge of the other. In many cases, both disciplines will use the same tool. In this tutorial, we will use another tool that can be used in either discipline—Sysinternals—a suite of tools developed by Mark Russinovich.

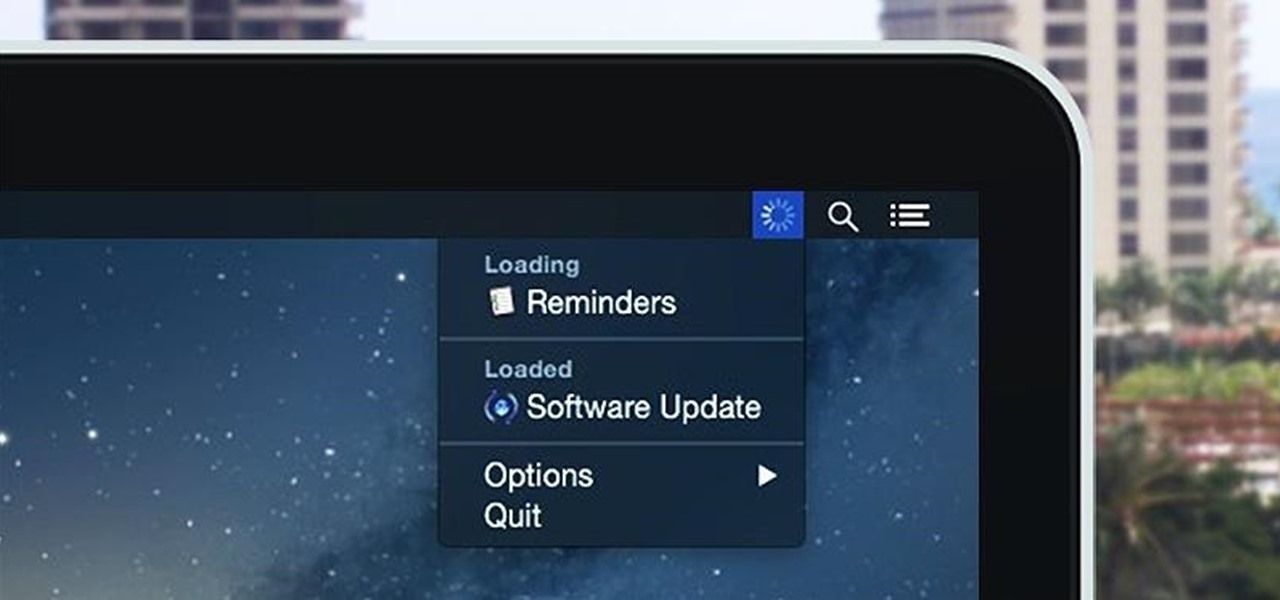
Monitoring your Mac with widgets can be the first step in identifying bandwidth issues, but finding the root of the problem can be a completely different story. Usually you will have to open up Activity Monitor in Mac OS X to look for apps hogging your bandwidth, but with Loading, you can get a detailed data usage report right from your menu bar.

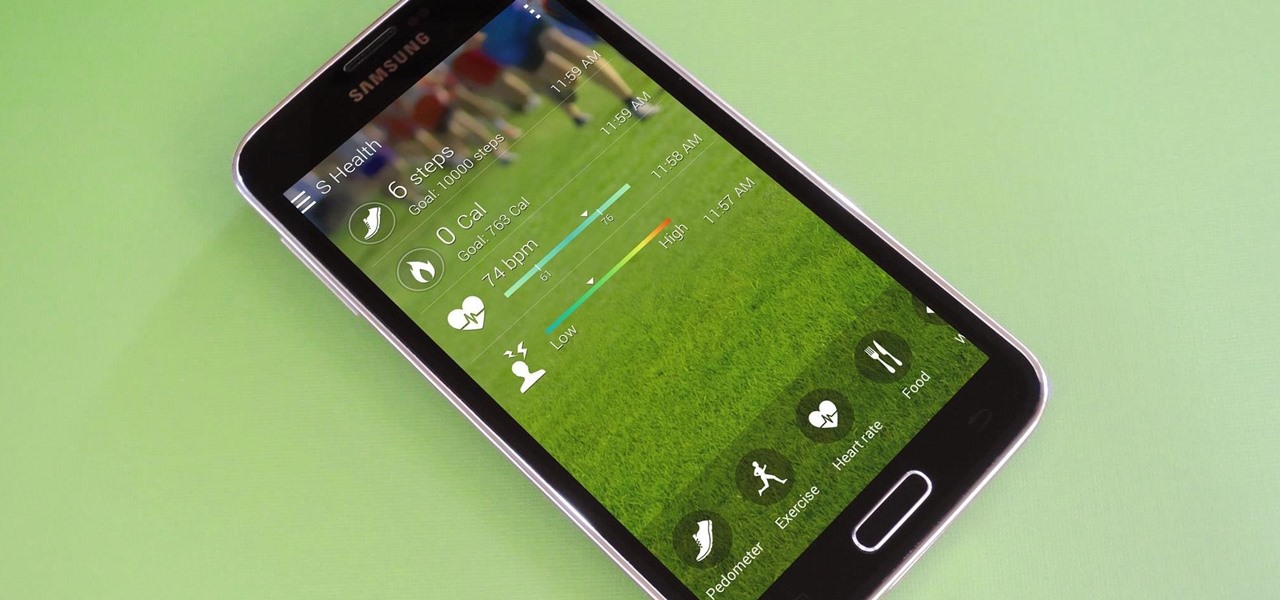
S Health is one of the biggest selling points for newer Samsung Galaxy devices. It offers a centralized place to view and manage data collected by all of the various sensors like the heart rate monitor.

Wearables were everywhere at CES 2015... you literally couldn't walk 10 feet without seeing some new and innovative device. Among the sleep, fitness, dog, and baby wearables, we came across one with a different, more important purpose—the Linx IAS injury prevention headband.

Lending someone your phone to make a call is always an awkward situation, as you closely monitor them to make sure they stick to a phone call rather than wandering off into private applications like your photo or messaging apps. You don't necessarily want to eavesdrop on their conversation, but trusting people with your phone is difficult, especially if you have some risqué or embarrassing pictures stored on it.

Smartphones and TVs aside, most of the electronics industry is focused on making everything smaller. From cars to cameras to computers to memory, we want power and convenience to go hand-in-hand. Professor John Rogers at the University of Illinois is ready for the next wave of medical tech with his smart electronic biosensors.

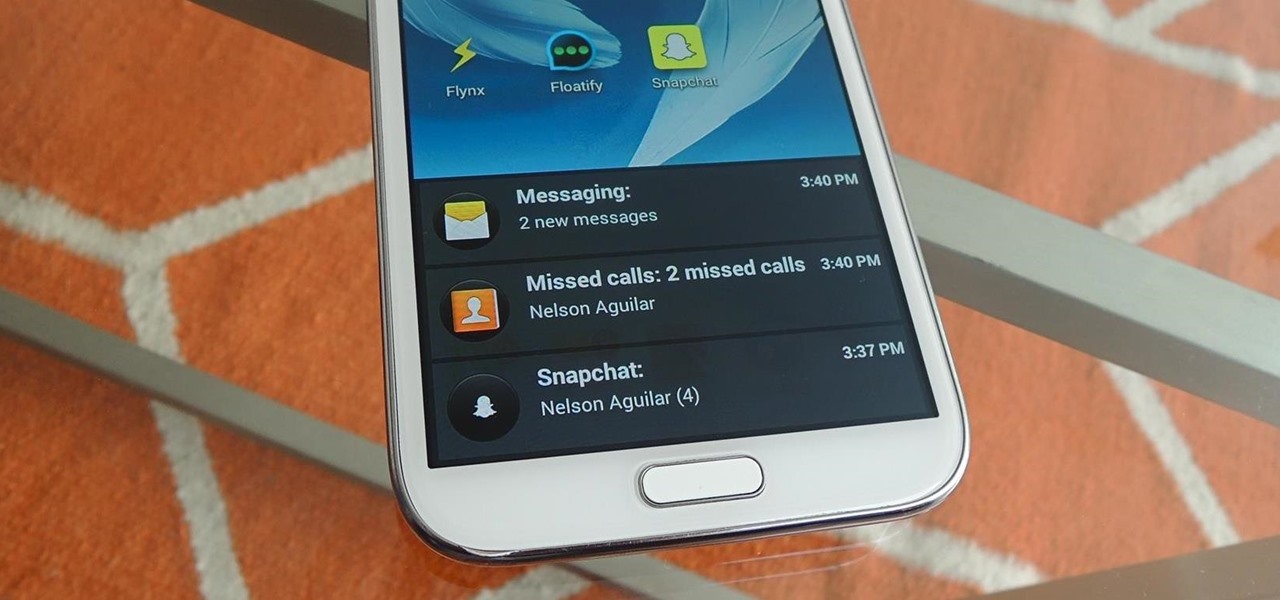
Included among the many new features in Android L is the new "Heads Up" notification system, showing notifications as interactive floating windows anywhere on your device. Floating windows are nothing new, though, as we've already showed you how to get floating widgets, floating application shortcuts, and even floating notifications.

Samsung is helping photographers in getting more utility out of their cameras with their new Samsung Smart Camera App. With it, your device becomes a powerful viewfinder for your Samsung camera, allowing you to not only frame shots, but control multiple aspects of the camera, right through your phone.

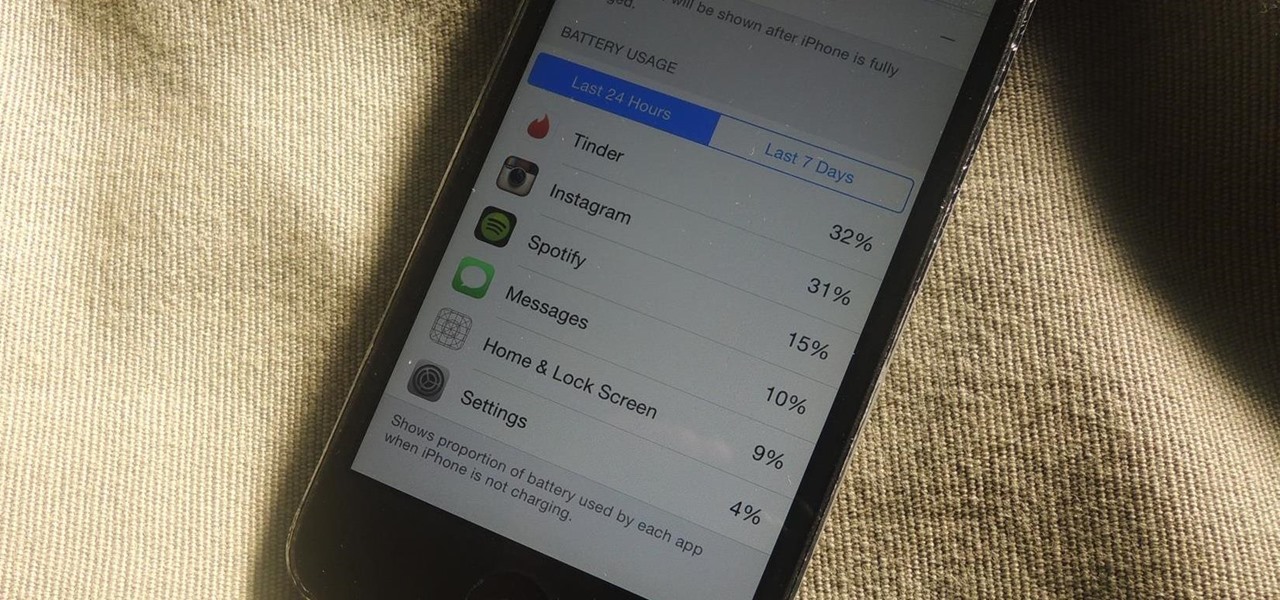
Battery life is and most likely always will be an issue with iPhones and other smartphones and tablets, but Apple is making it easier for us to save juice when we need to. To help monitor per-app battery usage, iOS 8 now lets us view battery usage stats for individual apps.

If rapid battery drain is something that's been an issue for you in the past, Apple is now making it easier to monitor what might be the problem. In the new iOS 8, you can now check battery usage for every app on your device.

Adding to the recent recent slew of bugs and issues within iOS 7, it now seems that emails sent with attachments are not encrypted, despite Apple's claims that they are.

Welcome back, my neophyte hackers! Have you ever had a neighbor that you're certain is up to no good? Maybe you've seen him moving packages in and out at all hours of the night? Maybe you've seen people go into his home and never come out? He seems like a creep and sometimes you hear strange sounds coming from his home? You know he's up to no good, but you aren't sure what it is exactly.

Those of you using iOS 7 probably know by now that swiping down on an app's preview screen in the multitasking menu does absolutely nothing. Swiping up force closes the app, but down is useless—unless you're jailbroken.

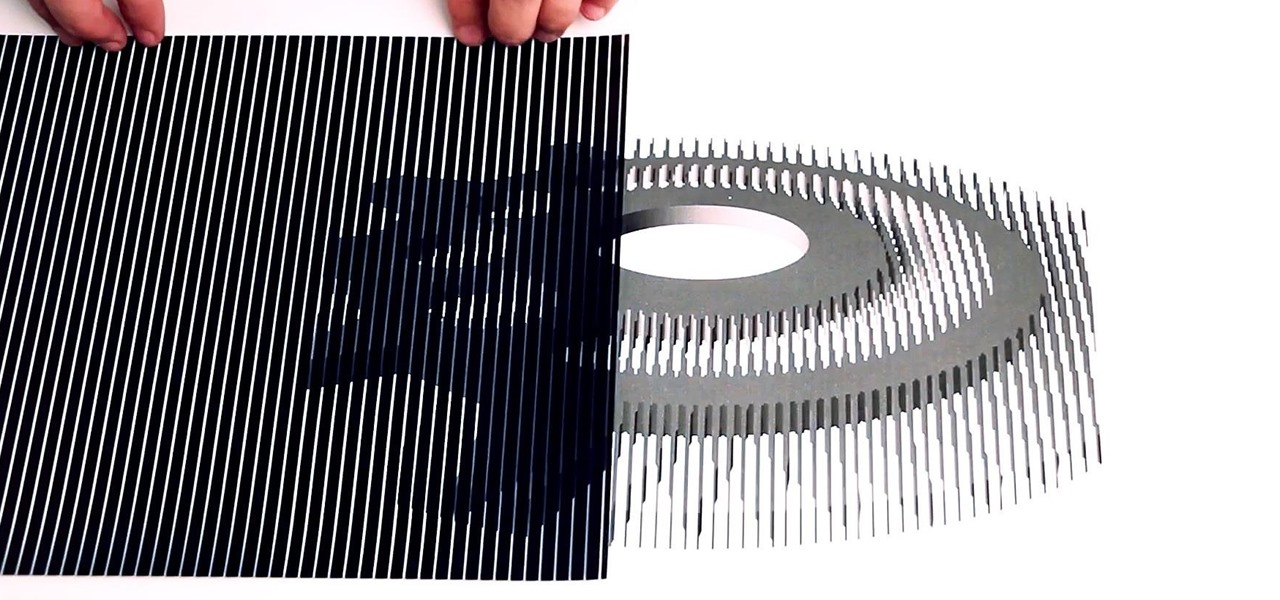
YouTube illusionist Brusspup has used everything from mirrors to fire to create his optical illusions, but his latest trick is a little more 2D. Using a printer, a transparency sheet and a piece of regular paper, he made several illusions that trick your brain into thinking they're actually animated when the transparency is slid across the paper.

Welcome back, my greenhorn hackers! Recently, I asked the Null Byte community what subject they would most like me to cover in future tutorials. Many of you cited scripting, and I decided it's best to cover this subject soon, so here goes.

Photographers have been using the Pepper's Ghost Illusion for over a century to play up the level of creepiness in their photos. Many of the pictures that claim to be real "sightings" use this technique to project a ghostly figure into the background of their images. Today, it's still used in theatre, "scary" rides at amusement parks, and haunted houses all over the world, which makes it a great photography trick for Halloween time. As shown in the tutorial below by Make's Jason Poel Smith, t...

Most of the time, if you're actually using your computer, it won't just go to sleep on you. But when you're reading a long article or watching a video and don't move the mouse or use the keyboard for a while, the screen automatically dims or goes into sleep mode.

Tons of people listen to music while going to sleep, but some don't like to leave it playing all night. If you hate waking up in the middle of the night and having to turn off your music, why not make your smartphone do it for you?

As an avid Steam user, I'm faced daily with high prices for all of the games I want to download and play. It's gotten to the point where I don't even bother going on Steam altogether because I might end up spending a bunch of money I don't have.

There's absolutely nothing better than seeing the look of pure and utter shock on someone's face, and that is why I absolutely love this. It is by far one of the best pranks ever, and one of the best videos that I've seen in a while. Seriously. If you've ever used the drive-thru, you've gotta watch this.

A faulty or broken thermostat can be one of the most annoying things to ever happen to your house. It's always too hot or too cold, and you can end up wasting money on your electricity bill.

Thanks to Flutter, it's now possible to control the music on your computer simply by making a few hand gestures. The app is available for both Windows and Mac and uses your computer's webcam to monitor your hand movements. Through the use of a few simple hand movements, you can play, pause, forward or replay your music. Flutter works with iTunes, Spotify, Quicktime, MPlayerX and a few other programs.

You can do a lot with water guns. Have trouble waking up? Make a water gun alarm clock that (almost) no one could sleep through. Prefer real ammo? Turn your water gun into an airsoft BB gun. And if you don't have one, you can even make your own.

I've never really liked to type on a flat or low keyboard. Even the small flip-up stands underneath most keyboards were not good enough for me, as those little legs aren't usually more than 2 or 3 centimeters high. I'd like a minimum of 5 cm, so I decided to make this keyboard base for myself. Aside from giving me the right height and angle, this DIY keyboard base also features LEDs that light up my monitor, the table, and gives a nice background to my desktop. It's even got a built-in stand ...

Dropbox announced Tuesday that a recent security breach compromised a list that included the email addresses of certain Dropbox users. To avoid future complications, the service announced that it would be implementing two-factor authentication, and even more useful, a security page that lets you monitor all activity on your account. In light of this and other recent web security threats, you might also want to know that services like Gmail, Facebook, and Yahoo! Mail have similar pages where y...

Gerridae—you've probably seen these weird bugs gliding across the surface of the water when you're out swimming or fishing. These insects are commonly referred to as water striders, or more cleverly, Jesus bugs, for their ability to "walk on water". It's a pretty cool trick, but what could it do for science, right? Turns out, quite a bit. Photo by felixtsao

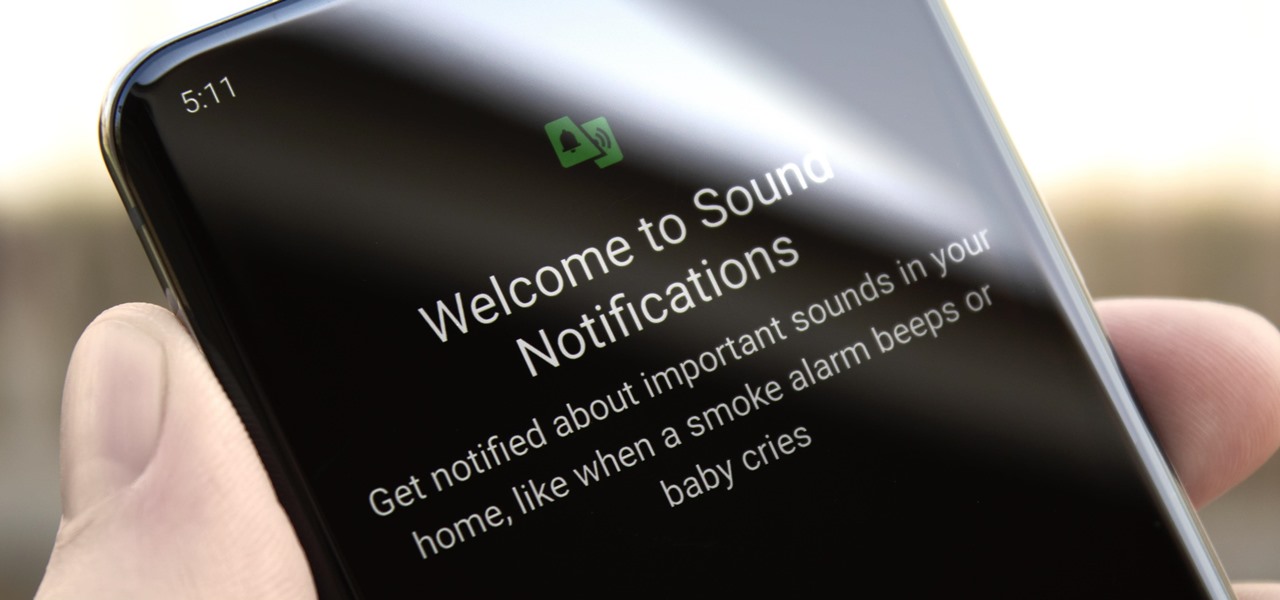
You don't have to be hearing impaired to appreciate one of Android's best audio accessibility features. This one can notify you when a baby is crying, a smoke alarm is going off, or when various nefarious sounds such as breaking glass are heard.

The Windows 10 desktop and microphone can be livestreamed without using Remote Desktop Protocol (RDP) software and without opening any ports on the target computer. A hacker with low user privileges can monitor and exfiltrate a target's every move and private conversation in real time no matter where they are. Hackers are watching and listening, and there are few ways to protect yourself.

A relay is an electrical component that works like a light switch, where it's turned on or off with an electrical signal. By connecting a relay to a Wi-Fi connected microcontroller like an ESP8266, you can build a connected switch that can be controlled from the web browser of any device connected to the same Wi-Fi network — all for just a couple of dollars.

After testing a series of Android 8.0 builds, Essential hit the reset button and jumped to Android 8.1 Oreo. The beta program didn't last long, as Essential has now released the official 8.1 update to the masses. The features from the 8.0 betas are all still there, plus a few goodies specific to the updated version. We'll highlight the standouts here.

Coinhive, a JavaScript cryptocurrency miner, was reportedly discovered on the BlackBerry Mobile website. It was placed there by hackers who exploited a vulnerability in the site's e-commerce software that allowed them to anonymously mine cryptocurrency every time the website was viewed. There's no doubt Coinhive, an innovative mining method, is being abused and exploited by hackers in the wild.

The Watch Dogs video game series came out in 2014, enamoring audiences with the idea of a seemingly magical smartphone that could change traffic signals, hack web cameras, and even remotely control forklifts. This may sound like science fiction, but The Sonic uses a customized flavor of Kali Linux to allow you to unleash the power of Kali from any smartphone — all without the need to create a hotspot to control it.

Equifax reported on Sept. 7 that it discovered a breach on July 29 which affects roughly half of Americans, many of whom don't realize they have dealings with the company. Hackers got away with social security numbers, addresses, and driver's license numbers, foreshadowing a "nuclear explosion of identity theft." Let's explore what really happened and what you and those around you can do to protect yourselves.

Surveying a target's Wi-Fi infrastructure is the first step to understanding the wireless attack surface you have to work with.
Hello and welcome to my article. I have made this article for anyone who wants to become a hacker, and wants to know how to get started.