In this video tutorial, Chris Pels will show you how to implement tracing in an ASP.NET web site to monitor or measure the performance and to diagnose errors. Learn how to add tracing to an entire web site as well as individual pages. See how to add custom trace messages in pages and business objects to aid in assessing site performance and in diagnosing errors. Learn the differences between tracing in an ASP.NET page and in using System.Diagnostics.Trace for tracing information in business o...

Wi-Fi networks come in two flavors: the more common 2.4 GHz used by most routers and IoT devices, and the 5 GHz one offered as an alternative by newer routers. While it can be frustrating to attack a device that moves out of reach to a 5 GHz Wi-Fi network, we can use an Alfa dual-band adapter to hack Wi-Fi devices on either type of network.

In order to kill bed bugs with a dry ice trap, you will need the following: a dog bowl, a towel, a cooler, a cotton ball, painter's tape, and talc powder.

This video tutorial from Magix presents how to burn (S)VCDs and DVDs using Magix Movie Edit Pro 15 application.First you need to group videos you want to burn.If you want to play movies using remote control you have to place chapter markers. You can set markers manually or choose automatic? marker setting which places markers before each new scene.Once all chapter markers are placed, click Burn button.Here you can choose Start Menu Templates. To change movie titles and chapter headings double...
The perfect way to avoid boredom at work or in the classroom is with a good old-fashioned prank, and this one is for tech-minded. In the video below, you'll see how to change your coworker's (or classmate's) computer screen to be display upside-down, which will totally freak them out when they return from lunch or the restroom. The best part is watching them try to revert it back to normal!

Pushups are a great workout at any level of bodybuilding. However, if you feel that you're ready for something more advanced, dumbbell rows are a good option for the next step in your advancement. They offer a new challenge and a different way to work out the same muscles you do with pushups.

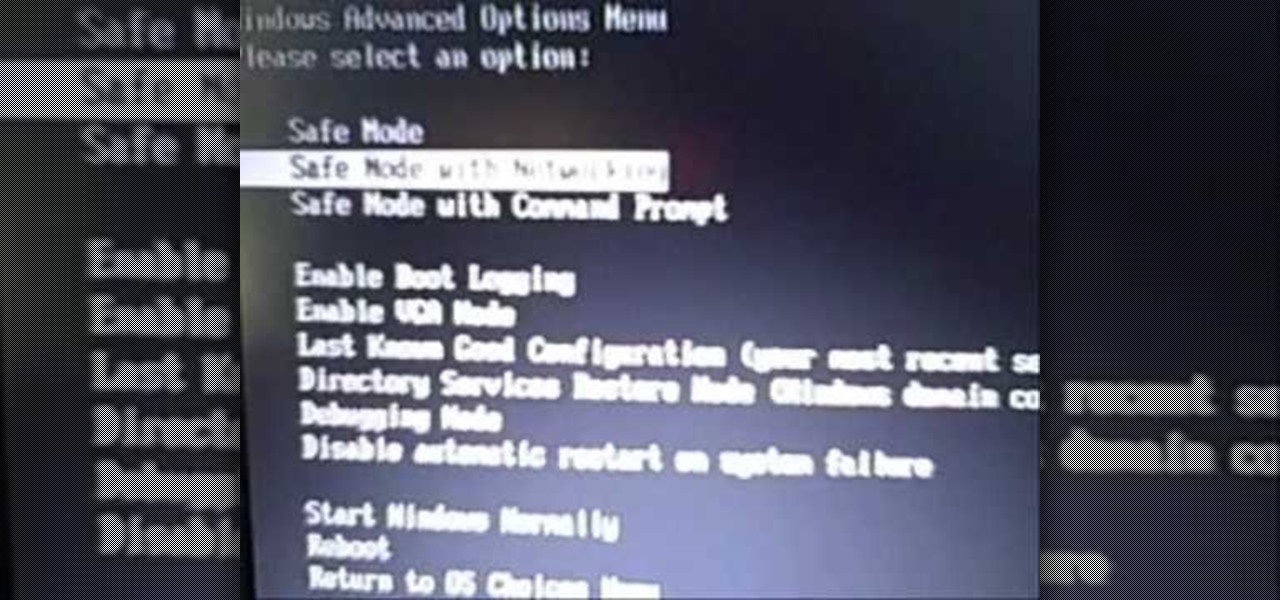
There are times when you must start up your Windows XP computer system in Safe Mode, for example if you need to remove certain viruses, key loggers, adware, etc. that cannot be removed while in standard mode. If you want to learn how to boot in safe mode in Windows XP, you should watch this. 1. Turn on your computer. Make sure your monitor is on and you do not step away from your computer, as booting into safe mode happens within the first minute of when you turn on your computer. You should ...

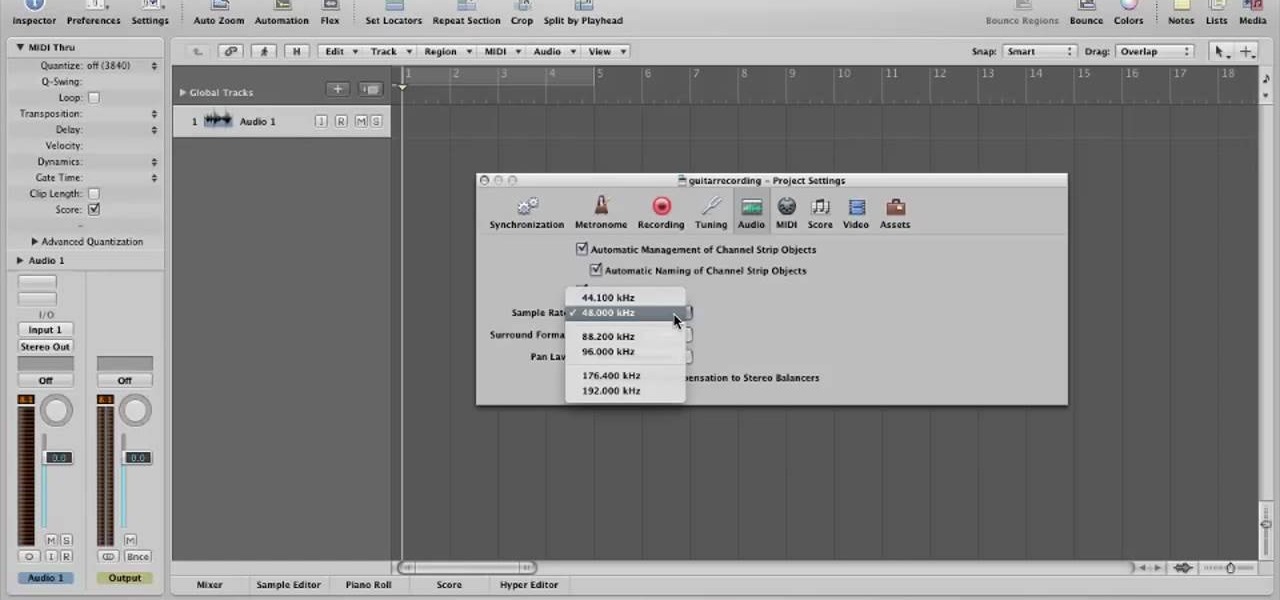
In this video, you will learn how to record using Apple Logic Pro 9. First, open the program and save the session. Make sure your audio interface is set before recording. Go to global settings and navigate to audio. Click on the general tab and change the audio settings. Wave files are the industry standard. Make sure 24-bit recording is checked. Software monitoring will allow you to monitor the audio. Save this and change the project settings. You can adjust the sample rate of your recording...

Use snow tires in the winter. Special patterns in the tread encourage the tires to grip the road better than regular tires. Snow tires are especially helpful if your car has rear wheel drive to discourage fish tailing.

This how-to video is about how to make a roasted lamb for dinner.

Worried about your baby or toddler either wrecking or wrecking themselves in your home? Baby proofing time! Make sure your house is safe and secure for your child when they start exploring their turf.

Dust is everywhere. Here are some novel ways to remove it. You Will Need

Early intervention is important for children with autism, a developmental disorder that inhibits socialization. So be on the lookout for warning signs.

The heart needs exercise just like any other muscle. Live longer and healthier by pumping it up! You Will Need

Watch this automotive video tutorial to see how to scan your automobile for diagnostic trouble codes.

It's common for IoT devices like Wi-Fi security cameras to host a website for controlling or configuring the camera that uses HTTP instead of the more secure HTTPS. This means anyone with the network password can see traffic to and from the camera, allowing a hacker to intercept security camera footage if anyone is watching the camera's HTTP viewing page.

After finding and monitoring nearby wireless access points and devices connected to them, hackers can use this information to bypass some types of security, like the kind used for Wi-Fi hotspots in coffee shops, hotels, and in flights high above the ground. By swapping their MAC address for that of someone already connected, a hacker can bypass the MAC filter and connect freely.

Your home has walls for privacy, but Wi-Fi signals passing through them and can be detected up to a mile away with a directional Wi-Fi antenna and a direct line of sight. An amazing amount of information can be learned from this data, including when residents come and go, the manufacturer of all nearby wireless devices, and what on the network is in use at any given time.

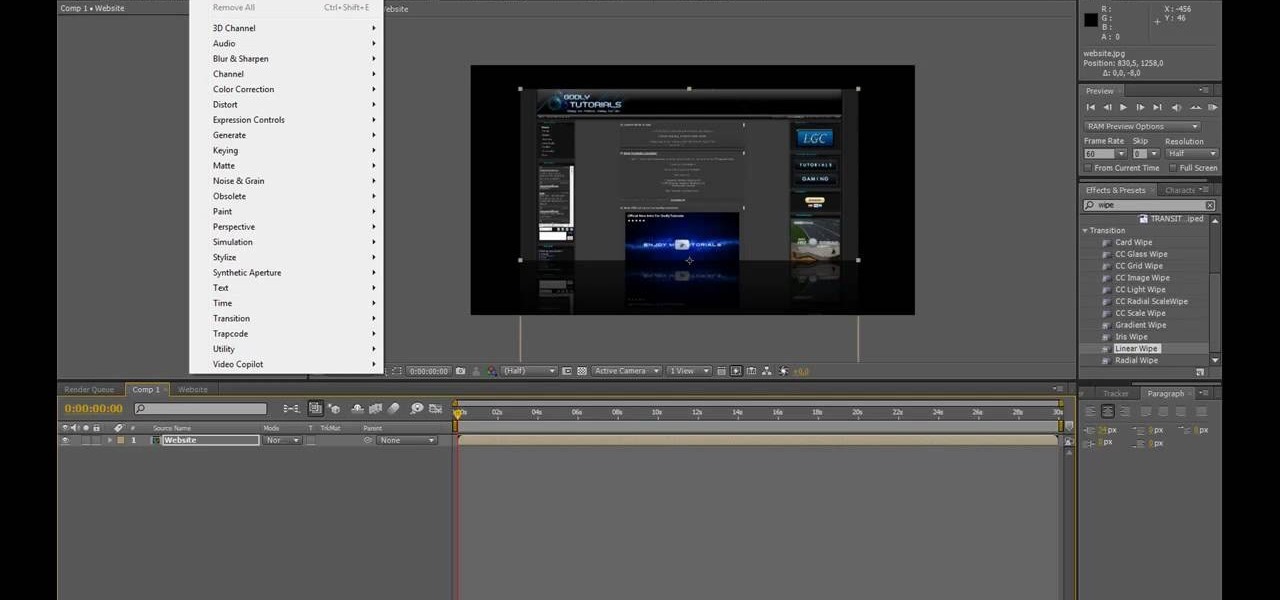
Open After Effects. Create a new composition by selecting "Composition" and "New" from main menu. Use default NTSC DV preset. Keep 30-sec default duration unless you need more time for the video scene to edit. Import several video clips by selecting "File," then "Import" from menu. Navigate to video files you want. Import at least 3 different video files using Import File dialog box. Double click on 1st video file you want to add to your timeline. The file will now open in a video monitor win...

Learn how to immobilize an ankle. The ankle is a complex joint, so when an injury occurs, and you can't get help right away, the first thing to do is keep it from moving – you'll prevent any more damage to the surrounding nerves and tissue.

What if you could easily visualize which access point every Wi-Fi device nearby is connected to in a matter of seconds? While programs like Airodump-ng can intercept this wireless information, making it easy for hackers to use and understand is another challenge. Fortunately, a tool called Airgraph-ng can visualize the relationships between Wi-Fi devices from only a few seconds of wireless observation.

I have gotten comments from my last tutorial on not being able to do anything because of a lack of a monitor. In order to address this problem I'm gonna show you how to connect and control the Rasberry Pi through a SSH client on Linux, Mac, Windows, and Chromebook computers. This will probably we a long tutorial so please bear with me. Anyway, lets get to work.

Long time reader, first time 'How To' poster. This tutorial has been highly requested. Here are the steps to perform a Pixie Dust attack to crack a WiFi password that has WPS enabled.

Wi-Fi devices are continually emitting "probe frames," calling out for nearby Wi-Fi networks to connect to. Beyond being a privacy risk, probe frames can also be used to track or take over the data connection of nearby devices. We'll explain how to see nearby devices emitting probe frames using Probequest and what can be done with this information.

One of the best uses for an old Android device is to turn it into a security webcam that can be accessed over the internet. But most of the time, this is a rather difficult process, because existing apps usually require you to mess around with network settings and configure a personal web server.

In this Electronics video tutorial you will learn how to connect a laptop or PC to your TV with an RGB cable. Take your RGB cable and plug it in to the back of the TV as shown in the video. You can also do this with the HDMI cable. Now take other end of the RGB cable and plug it in to the laptop or PC. Then you right click on your desktop, go down to graphics options > output to > monitor. Now you have to change the input to your TV. This will depend on the make and model of your TV. Once tha...

With Sprint already rolling out their Jelly Bean updates to Samsung Galaxy S III owners here in the United States, international users have already had a chance to check out Android's newest OS on their S3, but all is not gravy.

You may have heard of a signal jammer before, which usually refers to a device that blasts out a strong enough radio signal to drown out the reception of nearby devices like cell phones. Purpose-built jammer hardware is outright illegal in many countries. Still, Wi-Fi is vulnerable to several different jamming attacks that can be done with Kali Linux and a wireless network adapter.

If you're one who enjoys a good DIY project, or if you're just tired of paying exorbitant labor fees to have your vehicle serviced every 5,000 miles, changing your own oil can be a rewarding endeavor. Even though cars and trucks are becoming increasingly over-engineered these days, manufacturers generally see to it that the basic maintenance items can still be taken care of in your driveway with a few common tools.

If you've recently built a Wi-Fi spy camera out of an ESP32-CAM, you can use it for a variety of things. A baby monitor at night, a security camera for catching package thieves, a hidden video streamer to catch someone going somewhere they shouldn't be — you could use it for pretty much anything. Best of all, this inexpensive camera module can perform facial detection and facial recognition!

Working from home is going to be a reality for more people than ever. With Twitter CEO Jack Dorsey announcing that his employees will be working remotely for an extended period of time (and even permanently, in some cases), the workforce is rapidly changing. More companies are certain to follow suit.

When learning Wi-Fi hacking, picking a compatible Wi-Fi network adapter is the first step to learning to crack Wi-Fi passwords.

Electronic warfare tactics work by jamming, disrupting, or disabling the technology a target uses to perform a critical function, and IoT devices are especially vulnerable to attacks. Wireless security cameras like the Nest Cam are frequently used to secure critical locations, but a hacker can surgically disable a webcam or other Wi-Fi connected device without disturbing the rest of the network.

A man-in-the-middle attack places you between your target and the internet, pretending to be a Wi-Fi network while secretly inspecting every packet that flows through the connection. The WiFi-Pumpkin is a rogue AP framework to easily create these fake networks, all while forwarding legitimate traffic to and from the unsuspecting target.

Greetings aspiring hackers. I have observed an increasing number of questions, both here on Null-Byte and on other forums, regarding the decision of which USB wireless network adapter to pick from when performing Wi-Fi hacks. So in today's guide I will be tackling this dilemma. First I will explain the ideal requirements, then I will cover chipsets, and lastly I will talk about examples of wireless cards and my personal recommendations. Without further ado, let's cut to the chase.

We are most certainly not machines. We all need some downtime every once in a while to set our sanity scales back in balance, which in turn, makes us more productive workers. This is a premise that several forward-thinking employers fully understand, but these types of companies are few and far between in corporate America.

When I tried to set up an eviltwin for a MitM-constelation in kali 2.0, I couldn't provide internet to the victim. The origin was the brctl bridging. I have read many tutorials but all of them where explained in backtrack and older versions of kali. So i was searching for a solution without using brctl and this solution will be explained now. This will just work on unencrypted wireless-environments.

Google has a practice known as dogfooding, where they use their employees to test new and upcoming features for their various services. Back in March, they accidentally released a dogfood version of YouTube on Google Play, and many Android users got their first behind-the-scenes glance at the internal testing features.

A flaw in WPS, or WiFi Protected Setup, known about for over a year by TNS, was finally exploited with proof of concept code. Both TNS, the discoverers of the exploit and Stefan at .braindump have created their respective "reaver" and "wpscrack" programs to exploit the WPS vulnerability. From this exploit, the WPA password can be recovered almost instantly in plain-text once the attack on the access point WPS is initiated, which normally takes 2-10 hours (depending on which program you use).