Airgeddon is a multi-Bash network auditor capable of Wi-Fi jamming. This capability lets you target and disconnect devices from a wireless network, all without joining it. It runs on Kali, and we'll cover installing, configuring, and using its jamming functionalities on a small, inexpensive Raspberry Pi. When done correctly, it will deny service to a wireless network for up to several blocks.

Due to weaknesses in the way Wi-Fi works, it's extremely easy to disrupt most Wi-Fi networks using tools that forge deauthentication packets. The ease with which these common tools can jam networks is only matched by how simple they are to detect for anyone listening for them. We'll use Wireshark to discover a Wi-Fi attack in progress and determine which tool the attacker is using.

Design flaws in many routers can allow hackers to steal Wi-Fi credentials, even if WPA or WPA2 encryption is used with a strong password. While this tactic used to take up to 8 hours, the newer WPS Pixie-Dust attack can crack networks in seconds. To do this, a modern wireless attack framework called Airgeddon is used to find vulnerable networks, and then Bully is used to crack them.

To hack a Wi-Fi network using Kali Linux, you need your wireless card to support monitor mode and packet injection. Not all wireless cards can do this, so I've rounded up this list of 2019's best wireless network adapters for hacking on Kali Linux to get you started hacking both WEP and WPA Wi-Fi networks.

Task Manager got revamped quite a bit in modern versions of Windows. First introduced in Windows NT 4.0, it's become pretty popular among more advanced users. In Windows 10, Task Manager is not just a task manager anymore, it's also a system monitor, startup manager, history viewer, user controller, and the list goes on.

Welcome back, my budding hackers. So many of you are interested in hacking Wi-Fi that I have decided to revisit my Wi-Fi Hacking series with some updated and more in-depth material. I strongly suggest that you look at some of my earlier posts, such as "Getting Started with Terms and Technologies" and "Getting Started with the Aircrack-ng Suite of Wi-Fi Hacking Tools," before continuing here. If you're ready, you can also check out our updated 2017 buying guide here.

Privilege escalation is the technique used to exploit certain flaws to obtain elevated permissions relative to the current user. There are a vast number of methods out there to go from user to root on Linux, and keeping track of them all can be difficult. This is where automation comes into play, and a privilege escalation script called Linux Smart Enumeration is one to take advantage of.

Black Friday and Cyber Monday are becoming almost synonymous these days, but there are still plenty of awesome deals that you can only get starting on the Monday after Thanksgiving. Amazon, for instance, will be hosting a week-long Cyber Monday sale, and of course, most big-box retailers will follow suit with their online stores.

The Google Chromebook may be simple, but it is not limited. Watch this video to see how the Chromebook works as a kind of rudimentary Google TV when hooked up to a large monitor. This easy mod will let you enjoy your Cr-48 Chromebook in a whole new way.

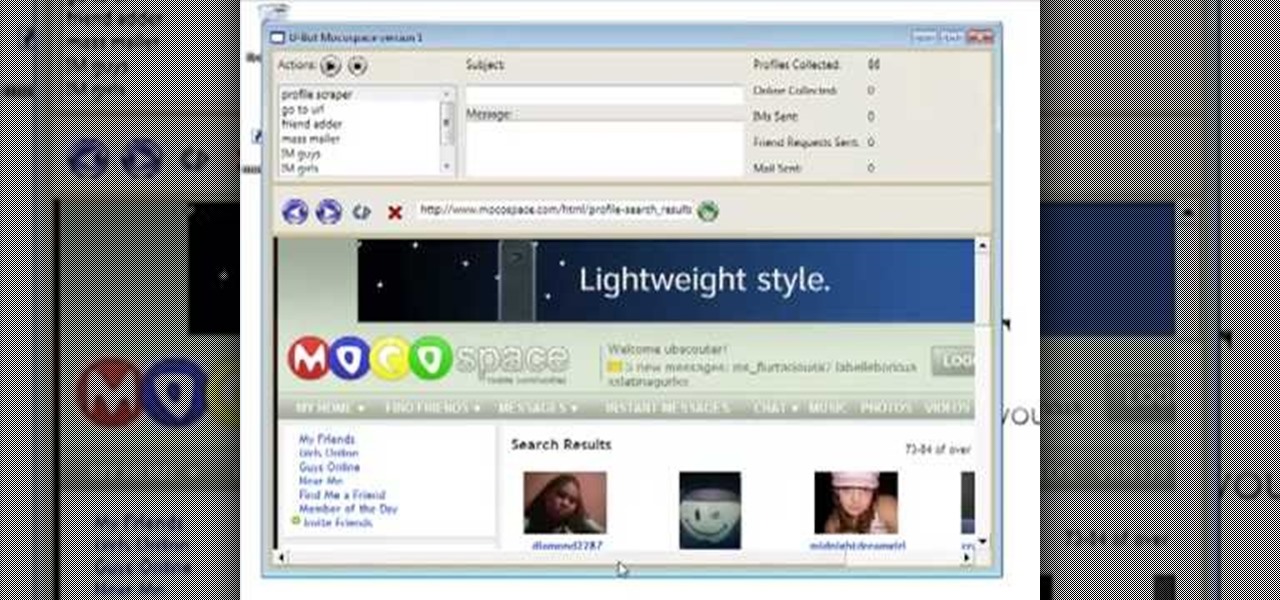
MocoSpace is a newly emerging social network, aimed and designed primarily for users of smartphones and other mobile devices. This tutorial shows you how to use the Ubot software to work with and monitor activity for your clients and customers on MocoSpace.

In this clip, you'll learn how to monitor your posture and maintain positive body language when flirting with a person you fancy. As a general rule, when flirting with someone, it's important that you be confident and natural. But, if you're feeling nervy, there's little shame in doing a little prep work with silly videos like this one. For more information, and to get started using this tip for yourself, take a look.

Sparky is a wireless, web-based video-chat robot from the Gomi Style crew. You can learn how to make your own Autonomous Telepresence robot using spare computer parts, some old toys and a bit of custom software (that we provide at gomistyle.com). This robot is operated with a Make controller circuit board. Sparky is a retired electric wheel chair with a monitor as a head.

From brute force hardware-based solutions like pointing a camcorder at your monitor to more elegant, software-based solutions like (the free and open source) Xvidcap, there are no shortage of ways to create a screencast while running Linux. In this how-to from Linux Journal Online, Shawn Powers offers a comparative look at many of the most popular techniques employed by Linux users.

Jeff Schell shows you some of the options and configurations available when working with images that do not match the dimensions of your program monitor in Premiere Pro CS3. In addition, Jeff will introduce you to the 'Automate to Timeline" feature that helps you quickly create a photo montage or slide show with the click of a button.

Arduino is a language that's easy to learn and supported on many incredibly low-cost devices, two of which are the $2 Digispark and a $3 ESP8266-based board. We can program these devices in Arduino to hijack the Wi-Fi data connection of any unlocked macOS computer in seconds, and we can even have it send data from the target device to our low-cost evil access point.

Cracking the password for WPA2 networks has been roughly the same for many years, but a newer attack requires less interaction and info than previous techniques and has the added advantage of being able to target access points with no one connected. The latest attack against the PMKID uses Hashcat to crack WPA passwords and allows hackers to find networks with weak passwords more easily.

Remember going to the doctor when you were a kid? If the word 'traumatizing' comes to mind, you'll love the RoboDoc by MarkusB, a robotic doctor that makes checkups a little less scary (and a lot more fun) for kids. It all started when Markus took his 14-month-old daughter for a checkup. The finger clip that the doctor used to check her pulse terrified her, so Markus decided to build a heartbeat monitor just for kids that's much more likely to make them laugh than cry.

Welcome back, my nascent hackers! In previous tutorials for my Wi-Fi Hacking series, I have shown you how to crack WEP and WPA2 passwords, break a WPS PIN, and create Evil Twin and Rogue access points. In this continuation of the series, let's look at slightly different approach to attacking wireless.

Welcome back, my nascent hackers! Like anything in life, there are multiple ways of getting a hack done. In fact, good hackers usually have many tricks up their sleeve to hack into a system. If they didn't, they would not usually be successful. No hack works on every system and no hack works all of the time.

It's one hell of a device, but the Samsung Galaxy S5 is still susceptible to the many hazards that other smartphones are prone to: theft, cracked screens, poor battery life, and particularly, overheating.

Welcome back, my neophyte hackers! As part of my series on Wi-Fi hacking, I want to next look at denial-of-service (DoS) attacks, and DoSing a wireless access point (AP). There are a variety of ways to do this, but in this tutorial we'll be sending repeated deauthentication frames to the AP with aircrack-ng's aireplay. Remember, hacking wireless networks isn't all just cracking Wi-Fi passwords! Our Problem Scenario

Thanks to numerous smartwatch deals this holiday season, many people are receiving their first one. But what exactly can they do? In regards to fitness, quite a lot. With a growing list of sensors and software updates, these small devices can be the very thing you need to ultimately reach your fitness goals.

Smartphones and other Wi-Fi enabled devices send radio signals called probe frames to locate nearby wireless networks, which makes them easy to track by listening for their unique MAC address. To show how this kind of tracking works, we can program a NodeMCU in Arduino to sniff the air for packets from any device we want to track, turning on an LED when it's detected nearby.

Whether you want to give a gift that your loved one has wanted all year or one that they never even knew existed, there's something awesome for everyone in these gifts. Just as exciting as their innovative features is their price.

Less than a month after launching its augmented reality Swim Goggles, wearables startup Form is preparing to add a major new feature for aquatic athletes.

By now, you've probably already seen Andy Serkis and his performance capture demo for Magic Leap. And sure, marrying motion capture acting and augmented reality sounds compelling, but how does it really work as an experience?

Hackers and makers are often grouped under the same label. While hackers draw on computer science skills to write programs and find bugs, makers use electrical engineering to create hardware prototypes from microprocessor boards like the Arduino. We'll exercise both sets of skills to program a $6 NodeMCU to display the status of a Wi-Fi link via an LED, allowing us to monitor for jamming attacks.

Samsung emphasized its goal of streamlined user experience with the unveiling of the Galaxy Note 9, highlighting the flagship's capabilities of seamlessly connecting with other devices. The Note 9's DeX mode makes it easier than ever to interface with a wide array of displays and monitors.

The future of augmented reality isn't on your smartphone or face, it's in the everyday items all around us. At least that's the belief of Gordon Meyer, the vice president of marketing at New York-based startup Lampix.

Not only has there been difficulty finding consensus on a name for driverless, autonomous, self-driving, or automated vehicles, there is also the issue of what we actually mean when we say a vehicle is self-driving, automated, and so on.

Mixed reality headsets have limited hardware capabilities and naturally imprecise interfaces. While that works just fine for games and entertainment, can they actually function as a tool for productivity?

While password cracking and WPS setup PIN attacks get a lot of attention, social engineering attacks are by far the fastest way of obtaining a Wi-Fi password. One of the most potent Wi-Fi social engineering attacks is Wifiphisher, a tool that blocks the internet until desperate users enter the Wi-Fi password to enable a fake router firmware update.

If you have a limited or restricted data plan, monitoring your usage can be the difference between escaping the month without overage fees or emptying out your wallet.

No offense to T-Mobile, but if you head over to their support page for the Samsung Galaxy Gear, you get the information below on how to take a screenshot of your smartwatch. Oh, thank you for that.

Now that iOS 7 has rolled out to the general public, with an overwhelming fit of mass hysteria, it's only custom for people to start bitching about battery drain—and I don't blame them. I was experiencing some rapid battery drain after first updating my iPhone 5, as well.

Welcome back, my greenhorn hackers. When Wi-Fi was first developed in the late 1990s, Wired Equivalent Privacy was created to give wireless communications confidentiality. WEP, as it became known, proved terribly flawed and easily cracked. You can read more about that in my beginner's guide to hacking Wi-Fi.

For anyone who uses computers regularly, the screen can become cluttered with different windows, tabs, and applications in no time. One solution to that mess is dual monitors, which allow users to be more organized and divide their work into two halves. The problem is that not everyone is fortunate enough to have access to more than one monitor.

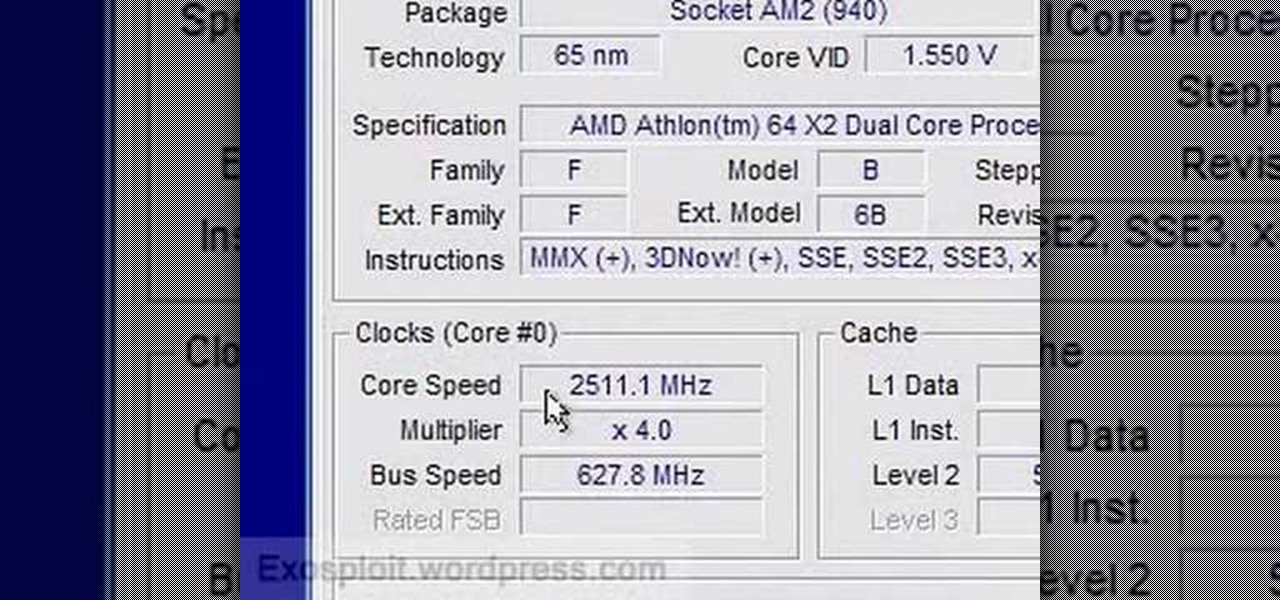
In this video from exosploit we learn how to find your system specs in Windows XP. If someone is trying to help your computer, you might need this information. Right click My Computer, and click Properties. Here you'll see your operating system, service pack, and how much RAM you have. Also google cpuz. Go to the first link and download it. Extract it and click the main file. Here it will tell you your processor, mother board, what bios version you have, how much RAM you have, and it will tel...

In order to use ThermaPure heat system to eradicate bedbugs, you will need a professional, with the appropriate equipment, including surface temperature readers.

One of the best ways to monitor your diet is by measuring your body fat content. In this three part tutorial, learn how to measure body fat using a caliper. A caliper is a device used to pinch and measure the fat on your body. A caliper is cheap, fast and accurate and makes an excellent alternative to electronic devices. Check out this video and stay on top of your new workout regime - mind the scale and use the caliper to know what's muscle and what's excess.