
How To: Recognize the early signs of autism
Early intervention is important for children with autism, a developmental disorder that inhibits socialization. So be on the lookout for warning signs.


Early intervention is important for children with autism, a developmental disorder that inhibits socialization. So be on the lookout for warning signs.
Nmap ("Network Mapper") is a free and open source (license) utility for network exploration or security auditing. Many systems and network administrators also find it useful for tasks such as network inventory, managing service upgrade schedules, and monitoring host or service uptime. Nmap uses raw IP packets in novel ways to determine what hosts are available on the network, what services (application name and version) those hosts are offering, what operating systems (and OS versions) they a...

Approximately 4 percent of women are diagnosed with gestational diabetes during pregnancy. Here's how to manage it.

Help yourself win that must-have item with these tips. You Will Need: a computer with internet access, money, & patience. Create an account. Browse the categories to familiarize yourself with the site, especially if you don’t have a specific item in mind. If you know what you want, start searching by using broad terms and synonyms to yield the most results. Add quotes around your search terms or qualifiers, such as a specific color or size, to narrow the field. You can also post on the “Want ...

Step 1: What Exploit Development Is and Why Should I Be Interested on About This Topic

Using just a small sticky note, we can trigger a chain of events that ultimately results in complete access to someone's entire digital and personal life.

The first few times I posted on some of the Android forums out there, I asked things like "Does anybody how I can make my phone do this or that?" Without fail, the responses to these types of questions were always one word—Tasker.

T-Mobile's credit-checking system was recently hacked, and this one is about as bad as it gets. The names of 15 million customers, their date of birth and social security number, as well as driver's license numbers and additional information was illegally accessed, meaning the potential for identity theft here is huge.
This video will show you 4 useful tricks related to you windows7 operating system. This video includes areas like speedier mouse, preventing display rotation, restore previous versions and monitoring of audio recording. Watch the video and follow these computer support tips.

So you want to know what that person who is always on their phone is up to? If you're on the same Wi-Fi network, it's as simple as opening Wireshark and configuring a few settings. We'll use the tool to decrypt WPA2 network traffic so we can spy on which applications a phone is running in real time.

Smartphone users often wish for a privacy, where no one is able to poke his/her nose in their personal stuff. Unfortunately, none of the smartphones have been able to guard their privacy in this fashion. Smartphones usually come up with none or almost negligible built-in security to serve your purpose.

If you are anything like me, you have a knack for taking silly selfies of yourself, i.e., taking scotch tape and wrapping it around your face to make yourself look like the blob, or perhaps you like taking selfies of yourself in weird or unusual situations doing weird and unusual things.

A man-in-the-middle attack places you between your target and the internet, pretending to be a Wi-Fi network while secretly inspecting every packet that flows through the connection. The WiFi-Pumpkin is a rogue AP framework to easily create these fake networks, all while forwarding legitimate traffic to and from the unsuspecting target.

Welcome back, my greenhorn hackers. When Wi-Fi was first developed in the late 1990s, Wired Equivalent Privacy was created to give wireless communications confidentiality. WEP, as it became known, proved terribly flawed and easily cracked. You can read more about that in my beginner's guide to hacking Wi-Fi.

While MacOS computers have been spared from some of the most famous malware attacks, there is no shortage of malicious programs written for them. To keep your computer safe from some of the most common types of malware, we'll check out two free tools. These tools can automatically detect ransomware encrypting your files and watch for unauthorized access to your microphone and camera.

Complex shell scripts can be implanted into photo metadata and later used to exploit a MacBook. In addition to obfuscating the true nature of an attack, this technique can be used to evade network firewalls as well as vigilant sysadmins.

In a previous guide, I demonstrated how to extract images from a security camera over Wi-Fi using Wireshark, provided you know the password. If you don't know the password, you can always get physical with the Hak5 Plunder Bug. Using this small LAN tap, we can intercept traffic like images from a Wi-Fi or IP security camera if we can get physical access to the Ethernet cable carrying the data.

The interactive displays of the future as visualized in Steven Spielberg's science fiction classic Minority Report, as well as the augmented reality interfaces used by millionaire playboy Tony Stark in the Marvel Cinematic Universe, are now closer to becoming reality in the military realm.

Once you've installed Ubuntu with security in mind and reduced the possibility of network attacks on your system, you can start thinking about security on an application level. If a malicious file is opened on your system, will an attacker be able to access every file on the computer? The chances are much slimmer if you put the proper defenses in place.

Dating websites allow you to see a person in a very intimate context, framing their successes and accomplishments in life to an important audience. The information contained in these profiles often can't be found elsewhere, offering a unique look into the personal life of the user.

A new telemedicine application for the Microsoft HoloLens is promising paramedics and EMTs a new tool for diagnosis and treatment of patients in the field.

Now that we've had significant time with Samsung's Oreo Beta for the Galaxy S8, many interesting features have come to light. As we continue using the new software, we have uncovered more subtle changes. The home screen already received a few new customization features, it's only fitting that the edge screen get some love, too.

Artificial intelligence and augmented reality go together like spaghetti and meatballs, and Lenovo has some ideas on how to spice up the recipe.

It's no secret that devices leak data, but sometimes they do so in ways you may not expect. Your phone, laptop, printer, and IOT devices leak Wi-Fi information that can (and is) used to track you.

Both the US and UK seem to be leaning toward requiring level 3 autonomous cars to train their "eyes" not just on the outside world, but even on the driver itself.
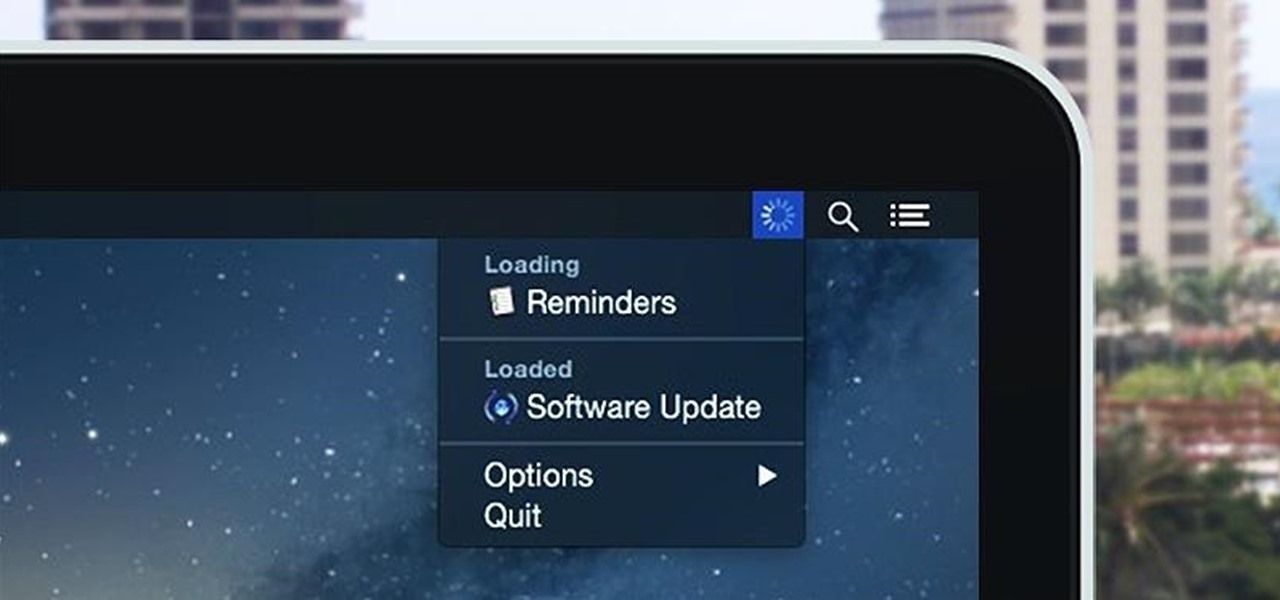
Monitoring your Mac with widgets can be the first step in identifying bandwidth issues, but finding the root of the problem can be a completely different story. Usually you will have to open up Activity Monitor in Mac OS X to look for apps hogging your bandwidth, but with Loading, you can get a detailed data usage report right from your menu bar.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Throughout history, the idea of the future has always promised better days, advanced technology, and of course—hover cars. Although we were correct about the better days (depending on who you ask) and advanced technology, we are still without hover cars, or pretty much any hovercraft vehicles—The Jetsons and Back to the Future were a lie!

There's something missing on your brand new Samsung Galaxy S4, and if you're a softModder like me, you know exactly what it is already. If you don't know, keep reading, because you should—anyone who wants a better Android experience should.
Monitoring your storage space is always a nuisance, whether you have a desktop, tablet, or smartphone; having enough space for all of your files, music, and videos is a constant battle. One movie file can take upwards of 1GB of memory, and for people who travel a lot, it becomes extremely impractical to have those huge files on your portable device.

After finding and monitoring nearby wireless access points and devices connected to them, hackers can use this information to bypass some types of security, like the kind used for Wi-Fi hotspots in coffee shops, hotels, and in flights high above the ground. By swapping their MAC address for that of someone already connected, a hacker can bypass the MAC filter and connect freely.

Your home has walls for privacy, but Wi-Fi signals passing through them and can be detected up to a mile away with a directional Wi-Fi antenna and a direct line of sight. An amazing amount of information can be learned from this data, including when residents come and go, the manufacturer of all nearby wireless devices, and what on the network is in use at any given time.

Equifax reported on Sept. 7 that it discovered a breach on July 29 which affects roughly half of Americans, many of whom don't realize they have dealings with the company. Hackers got away with social security numbers, addresses, and driver's license numbers, foreshadowing a "nuclear explosion of identity theft." Let's explore what really happened and what you and those around you can do to protect yourselves.

Battery management is a never-ending struggle. To be on the safe side, you likely won't want to leave your home with less than 100% battery, but continually checking your charging iPhone is a hassle. Instead of continuously monitoring your battery's power level, have your iPhone tell you when it's reached a full charge.

There are countless ways in which you can turn your love of tech and coding into a full-fledged career — from developing apps and websites as a freelancer to working in the IT departments of small startups or major tech companies. But one of the best ways that you can put your programming skills to good use is to join the increasingly important world of cybersecurity.

The deadly Wuhan coronavirus outbreak has not only has claimed lives in China but also has caused disruption around the globe, particularly in the tech industry. To date, the virus has claimed more than 1,000 lives in China, according to the country's officials.
Every iPhone since the 5S has come equipped with a microchip called a motion coprocessor, which collects data from integrated accelerometers, gyroscopes and compasses, and can then transfer that information to fitness apps that track physical activity. Essentially, the chip knows whether you're running, walking, sleeping, or driving — but what if you don't want it to?

The HoloLens 2 hasn't even reached most of the market, but it's already a big-time TV star. Microsoft's augmented reality device made its primetime debut on FOX TV last night on an episode of the hospital drama The Resident.

In their first head-to-head major contract clash, Microsoft has emerged victorious over Magic Leap, as the US Army has awarded a $480 million contract to the HoloLens maker.

Augmented reality and drones already go together like turkey and stuffing, but a new iOS app adds some spice to the combination with a new kind of flight path automation.