
News: ProntonMail under DDoS Attack
Recently the newly famous ProtonMail service was under attack by DDoS attack. This attack was believed to be the hacking group Armada Collective.


Recently the newly famous ProtonMail service was under attack by DDoS attack. This attack was believed to be the hacking group Armada Collective.
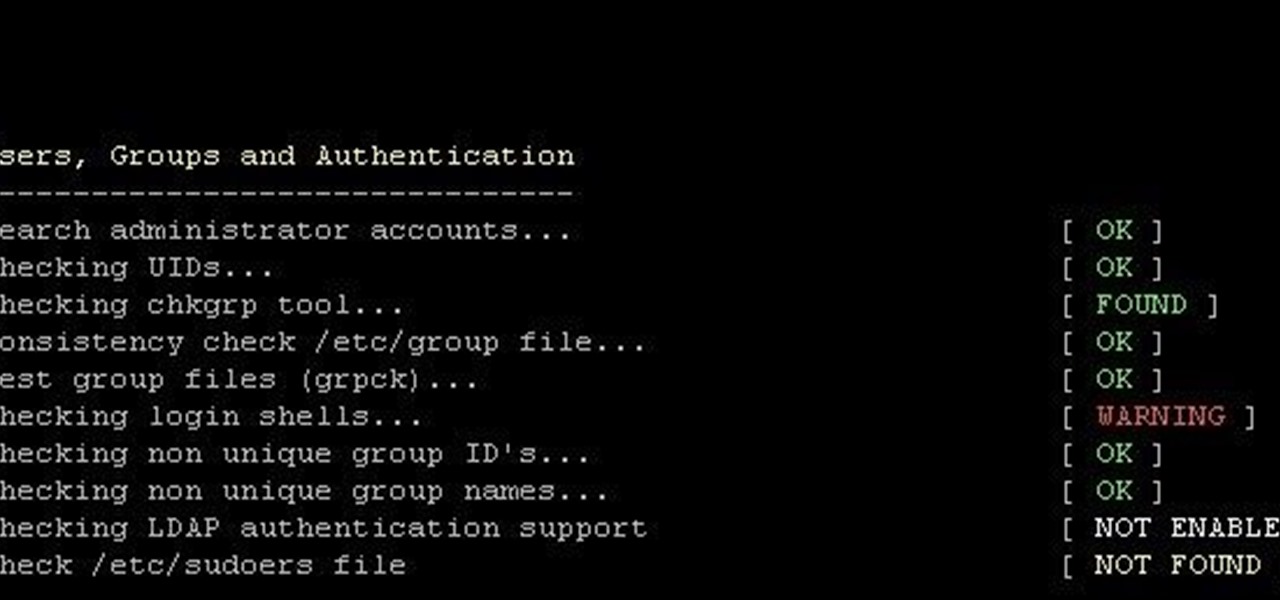
This is finding some of your vulnerability using Lynis. This tool Lynis is used on Unix and Linux type operating systems (sorry windows). So lets get started

A field hockey midfielder is the quarterback of the team, and must advance the ball from the defense to the offense. Learn how to play midfielder in field hockey in this video tutorial.

For a field hockey offense to score, their attacking must be better than the defense's tackling. Speed and accuracy are essential for an effective field hockey attack. Learn how to attack in field hockey in this video tutorial.

Shaun Alexander was an amazingly productive NFL running back. In this video, he takes some time to explain for young running backs how to hold the ball properly, protecting it from the defense and potential fumbles. Proper finger positioning and placing the body between opponents and the ball are both crucial elements.

This explores Fischer's opening strategies versus various openings. This video looks at one of his defenses against the King's Pawn Opening. The match was played in 1966 in Santa Monica against Wolfgang Unzicker.

Learn the correct position for playing defense on the low post as a basketball player.

Learn how to draw the defense and kick the pass on the basketball court with the help of this exercise.

Self-defense is essential in a violent society where anything can happen. Should you ever find yourself in a choke hold, keeping your wits about you and knowing what to do will help you escape safely. Watch this video to learn how to escape a choke hold.

In this sports how-to video, Farmington HS boys basketball coach Shane Wyandt and team demonstrate the shell four defense drill. The shell four drill is an effective way of training for basketball. Follow along with this video demonstration and improve your game with this drill.

This is a video of Peter Gade demonstrating backhand defense for going to the backhand side of the court, sorry no English translation of it.

It's exciting to get that reverse shell or execute a payload, but sometimes these things don't work as expected when there are certain defenses in play. One way to get around that issue is by obfuscating the payload, and encoding it using different techniques will usually bring varying degrees of success. Graffiti can make that happen.

As long as you're on the internet, you can be hacked. With an estimated 2.65 billion social media users, these apps are prime targets for hackers.

Web application firewalls are one of the strongest defenses a web app has, but they can be vulnerable if the firewall version used is known to an attacker. Understanding which firewall a target is using can be the first step to a hacker discovering how to get past it — and what defenses are in place on a target. And the tools Wafw00f and Nmap make fingerprinting firewalls easy.

Users are often the weakest link when probing for vulnerabilities, and it's no surprise they can be easily fooled. One way to do this is called clickjacking. This type of attack tricks the victim into clicking something they didn't mean to click, something under the attacker's control. Burp Suite contains a useful tool called Clickbandit to generate a clickjacking attack automatically.

One of the things that sets a seasoned hacker apart from the script kiddies is the ability to effectively sneak past antivirus defenses when executing an attack. One way to do this is to use custom shellcode in an exploit. Not everyone is an expert at writing shellcode, but luckily there's an easy way to do this that is both quick and effective.

If you didn't get the memo, passwords aren't enough protection for your online accounts. Even a long and complex password offers only one line of defense which can falter. Two-factor authentication adds an additional layer, bolsters your defense, and decreases the risk of your account becoming compromised.

As the third-largest smartphone manufacturer in the world, Apple devices are a constant target for hackers everywhere. While iOS has seen fewer common vulnerabilities and exploits (CVEs) in recent years, iPhones still aren't hack-proof. Fortunately, you can strengthen your security with the help of a few apps.

A vaccine against HIV might prevent the disease that we can't seem to cure. Some HIV patients make antibodies that can take down the virus, much the way a vaccine might. But, scientists haven't been able to provoke that type of response in other people. However, in a process that might work in humans, a group of researchers has successfully generated antibodies in cows that neutralize multiple strains of HIV.

Once we recover from the respiratory infection pneumonia, our lungs are better equipped to deal with the next infection — thanks to some special cells that take up residence there.

New research explores how the bacteria on the penis can leave men more susceptible to infection with HIV.

The leading platforms enabling augmented reality technology lead our headlines in Market Reality this week.

Our quest to find novel compounds in nature that we can use against human diseases —a process called bioprospecting — has led a research team to a small frog found in India. From the skin slime of the colorful Hydrophylax bahuvistara, researchers reported finding a peptide — a small piece of protein — that can destroy many strains of human flu and can even protect mice against the flu.

New weapons are needed to combat antibiotic-resistant bacteria. Instead of drugs, scientists have discovered in an animal study that they may be able to harness vampire bacteria to vanquish pneumonia.

If you missed out on Black Friday this year, you've got a second chance at saving some big bucks on apps, mobile devices, HDTVs, and other tech. See below for all of the hot Cyber Monday deals from Amazon, Apple, Google, Microsoft, and other online retailers. This list will be continuously updated throughout the day, so bookmark it to stay up to date on all the of Cyber Monday discounts.

Fish is delicious, and as the Harvard School of Public Health points out, incredibly good for you. There are many studies that show regularly consuming a couple of servings of fish per week can help prevent heart disease and may well reduce your chances of stroke, depression, and getting Alzheimer's. After all, there's a reason why fish is called "brain food."

Welcome back, my aspiring hackers and those who want to catch my aspiring hackers! As most of you know, this series on digital forensics is inspired by the motivation to keep all of you all out of custody. The more you know about the techniques used by law enforcement and forensic investigators, the better you can evade them.

As long as you have the meeting ID, you can join and interrupt virtually any video call on Zoom. And that's how we get terms such as "Zoom-bombing," where someone jumps into a chat to say or visually show vulgar and inappropriate things to the other participants. However, hosts can put an end to it.
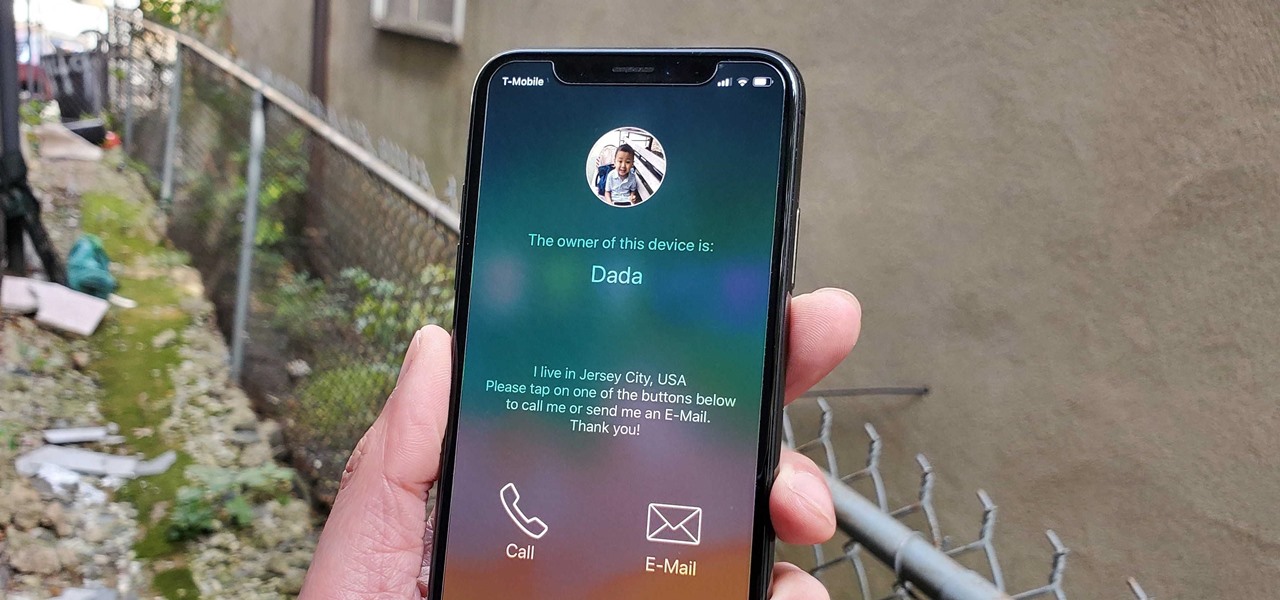
The prospect of loss or theft is something we constantly live with. Stolen iPhones fetch a premium price on the black market for parts like OLED display assemblies, frames, and charging ports. Making matters worse, if someone were to steal your phone, they could simply turn it off to avoid anti-theft features like Find My iPhone.

Following on the heels of the announcement that ThirdEye's Gen X2 MR glasses began shipping in September, ThirdEye has revealed it has developed an app that helps soldiers aim their weapons during battle situations.

With the latest version of ARKit and a new set augmented reality development tools set to arrive this Fall with iOS 13, Apple has taken an unprecedented step in recruiting Chinese developers to fill the App Store with mobile AR apps now, likely with an eye to the future.
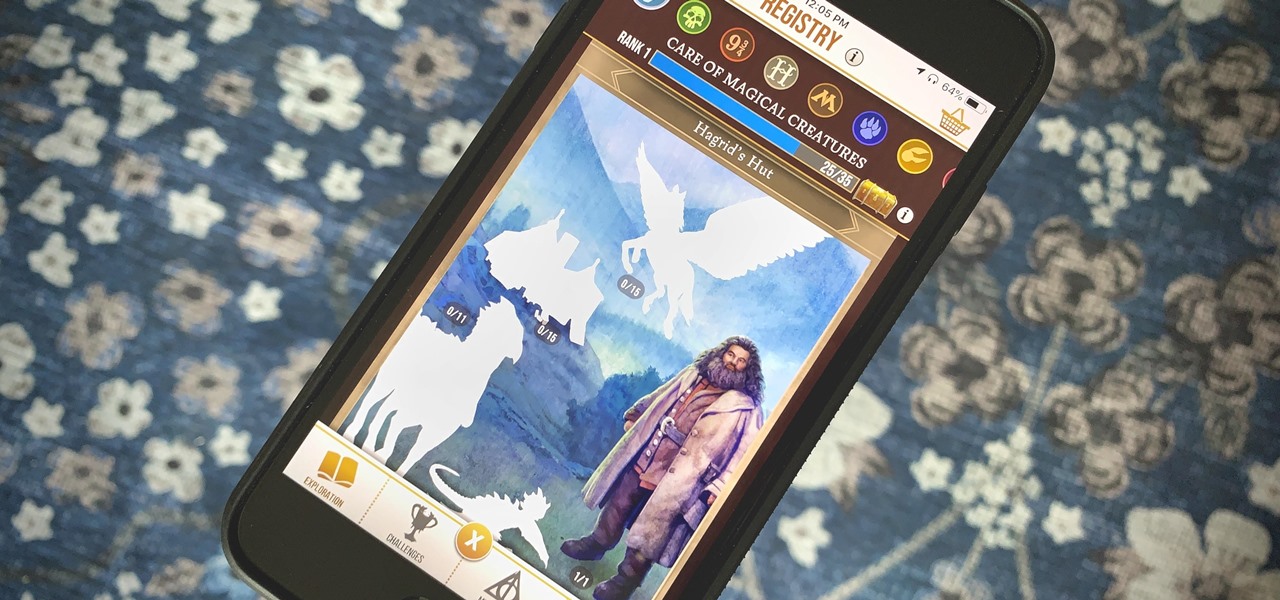
From the first moments of booting up Harry Potter: Wizards Unite to the hours of walking you're bound to experience, one thing is clear — encountering Foundables and defeating their Confoundables is a significant plot point of the AR game. While you receive rewards each time you retrieve a Foundable, the real treasure comes from completing parts of the Registry, called "Families."

It turns out that the video Magic Leap released earlier today was indeed a teaser for the public release of the Game of Thrones experience for meant for all Magic Leap One users.

To build hype for the HoloLens 2 among developers, Microsoft is borrowing a page out of Magic Leap's playbook.

In their first head-to-head major contract clash, Microsoft has emerged victorious over Magic Leap, as the US Army has awarded a $480 million contract to the HoloLens maker.

Leading augmented reality headset makers Microsoft and Magic Leap are among the companies now vying for a military contract for battlefield heads-up displays.

The fortunes of ARKit and ARCore are still in the hands of developers, who have been increasing the number of mobile augmented reality apps on the market, but perhaps not as fast as companies like Apple might have expected. But one new product is looking to literally kickstart mobile AR gaming by introducing a few key components that harness the traditional board game model.
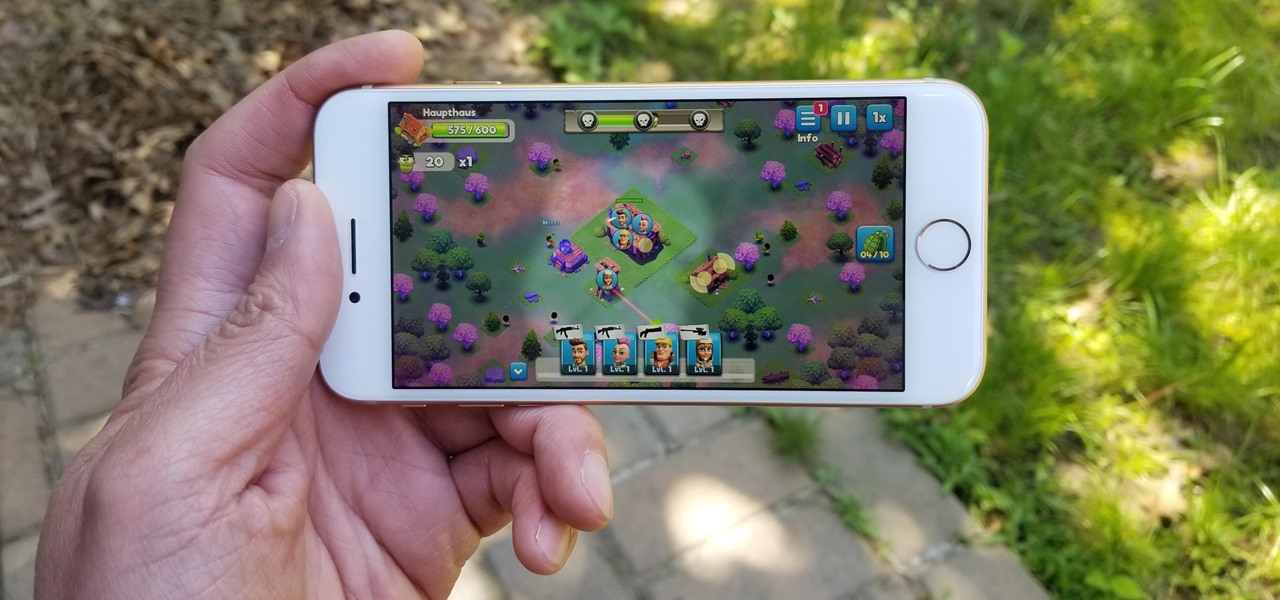
With tons of titles to choose from on the iOS App Store, you'll never be lacking when it comes zombie shooters. Unfortunately, the same can't be said if you're more interested in base-building and defending against the undead. PlayStack aims to change this, and they've soft-launched Survival City in the Philippines for further development. With a simple hack, you can try the game yourself right now.
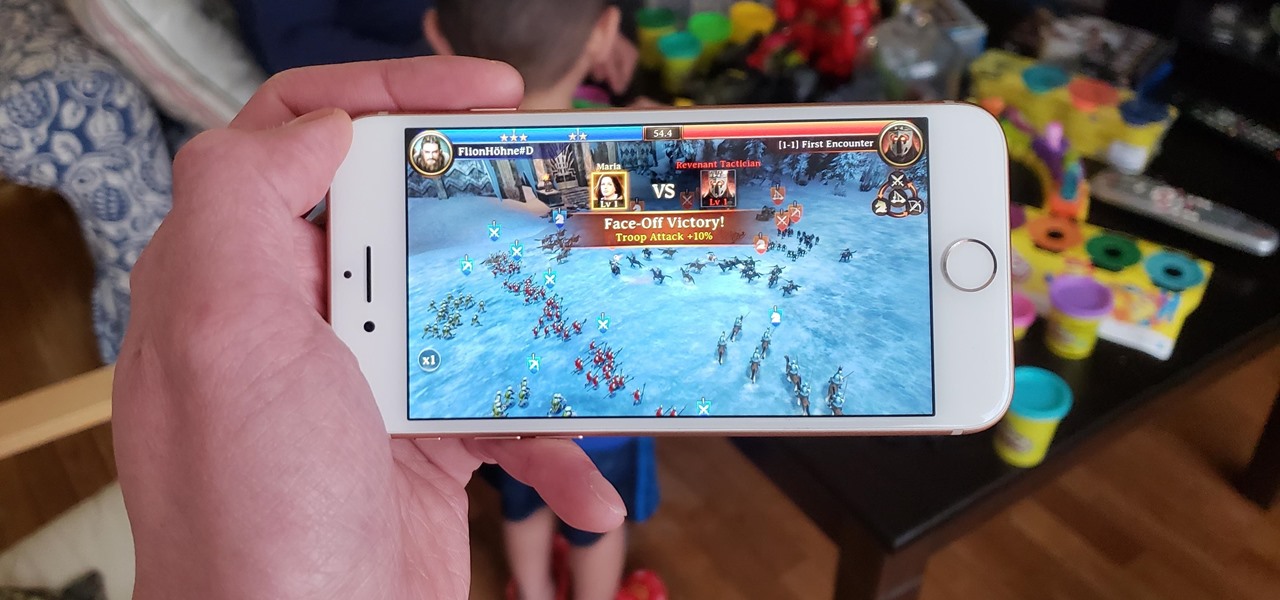
Netmarble has released a new MMORTS game called Firstborn: Kingdom Come to go up against competing games like Lords Mobile. Unfortunately, the game seems to be stuck in development as a soft launch in select countries, limiting its exposure to gamers worldwide. But don't let this hiccup deter you — we've found a simple workaround to play the game on your iPhone right now.

A weak password is one that is short, common, or easy to guess. Equally bad are secure but reused passwords that have been lost by negligent third-party companies like Equifax and Yahoo. Today, we will use Airgeddon, a wireless auditing framework, to show how anyone can crack bad passwords for WPA and WPA2 wireless networks in minutes or seconds with only a computer and network adapter.