Smartglasses startup Nreal enjoyed some highs and endured some lows this week, as the company landed a product placement with Kevin Bacon but then faced production issues related to the coronavirus outbreak.

Nearly every connection to the internet is dependent on the Domain Name System. DNS, as it's more commonly called, translates domain names like gadgethacks.com into IP addresses, which is what network devices use to route data. The problem with DNS servers is that they don't have your privacy in mind.

In a stunning end-of-year twist to the Magic Leap versus Nreal legal saga, the China-based startup is now filing a motion against Magic Leap.

Is the augmented reality magic fading down in Plantation, Florida? That's the first question some may be asking following a casual revelation over the weekend that Magic Leap, the maker of the Magic Leap One, has assigned much of its patent portfolio over to JP Morgan Chase as collateral.
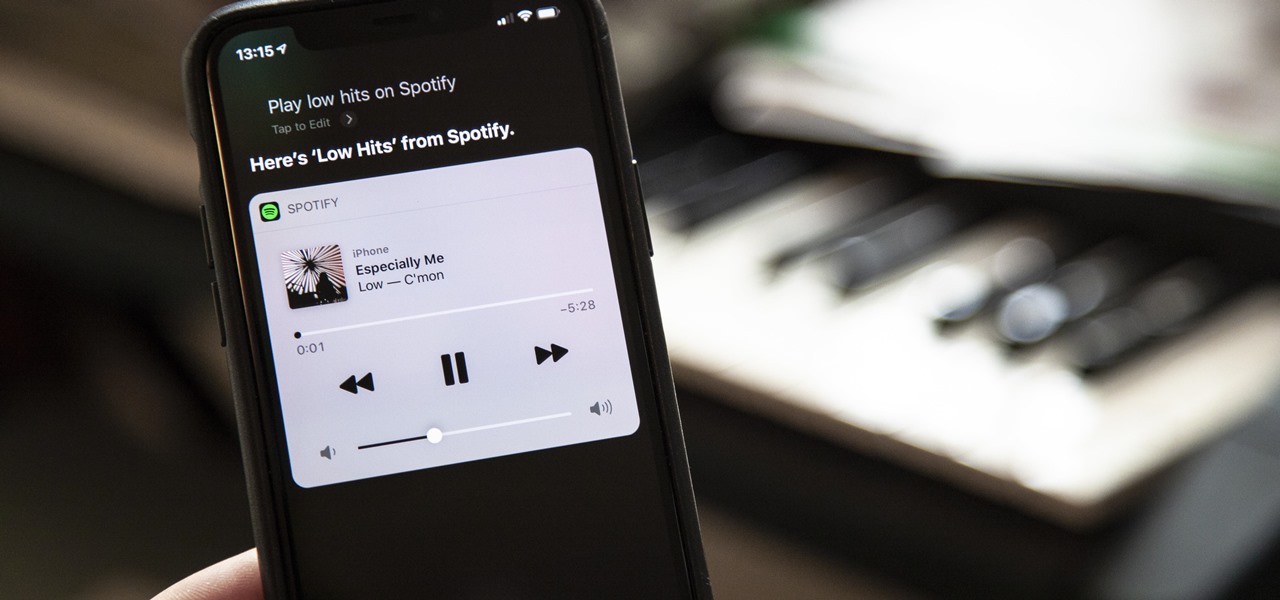
Finally, Spotify now works with Siri! It's been a long time coming, but as of Spotify Music version 8.5.6 for iOS 13, you can make Siri or Hey Siri on your iPhone play and control music in your Spotify account. But what commands can you use? We've built a list of everything you can tell Siri to do on Spotify right now, and as time goes on, the list may grow even more powerful.
There's no denying that native Dark Mode in iOS 13 is awesome. Stock apps that were blindingly white for over a decade can now be comfortably used in the middle of the night. You might find, however, that some of your third-party apps aren't taking the hint. Why won't YouTube switch to dark mode when iOS as a whole does? We put together a troubleshooting checklist to get your apps cooperating.

Your Xbox Wireless Controller is a great way to play games on both Xbox One consoles and Windows 10 computers. However, you don't need to have any of those devices to enjoy your controller with your favorite games — you can seamlessly connect the Xbox Wireless Controller to your iPhone for an enhanced mobile gaming experience.

A long-standing request for the iPhone has been a way to quickly browse and connect to available Wi-Fi networks and Bluetooth devices without having to dig through the Settings app. With iOS 13, Apple has finally built this essential feature into Control Center, giving you quick access to wireless settings from anywhere, including the lock screen.

Some of the Pixel 3's coolest features are software related, which means you can get many of them on non-Pixel devices. "Flip to Shhh" is a perfect example of this. It lets you quickly put your phone into do not disturb mode by placing it face down, and this can be replicated on other Android phones with the help of a simple app.

Long before the HoloLens or the Magic Leap One, a California-based team of independent filmmakers envisioned what the future of augmented reality might look like.

While the Smart Invert feature was an excellent first step toward a dark mode, it's nowhere near what a true dark mode should be for iPhone. After years of rumors and disappointment, Apple finally has the dark mode everyone's been wanting, and it's one of the most significant new features in iOS 13.

Complex shell scripts can be implanted into photo metadata and later used to exploit a MacBook. In addition to obfuscating the true nature of an attack, this technique can be used to evade network firewalls as well as vigilant sysadmins.

Featured on MTV's Catfish TV series, in season 7, episode 8, Grabify is a tracking link generator that makes it easy to catch an online catfish in a lie. With the ability to identify the IP address, location, make, and model of any device that opens on a cleverly disguised tracking link, Grabify can even identify information leaked from behind a VPN.

Though many were hoping for it, a notification indicator around the Galaxy S10's front camera punch hole never came to fruition. Since then, we've been finding other uses for the camera cutout, from turning it into a circular battery meter to using creative wallpapers. Thankfully, there's now an app that will give you LED-style alerts with a ring around your S10's camera.

To borrow from the canon of Game of Thrones, what is dead may never die. And while the Meta Company that we knew this time last year is no more, the patent infringement lawsuit filed against the company lives on.

Websites are often misconfigured in ways that allow an attacker to view directories that are not ordinarily meant to be seen. These directories can contain sensitive information such as private credentials or configuration files that can be used to devise an attack against the server. With a tool called Websploit, hackers can scan targets for these hidden directories without difficulty.

As Microsoft continues to bask in the glow of its HoloLens 2 unveiling and begins ramping up the hype to launch, Nreal and Vuzix are carving out their own niches in the AR hardware landscape.

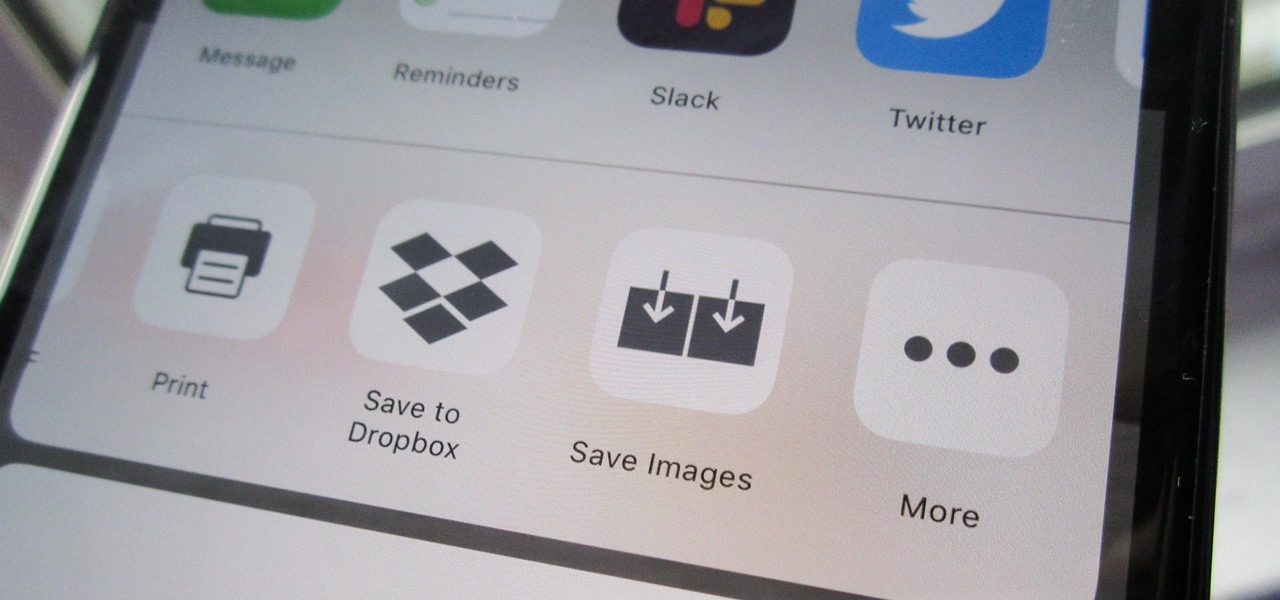
Some websites block image downloads on their webpages so you can't save them for reuse. That means long-pressing or force-pressing on protected images in Safari on your iPhone will not do anything or will omit the "Save Image" option. Taking a screenshot is the obvious solution to bypass restrictions, but you won't get the best quality. Thankfully, there's another way.

Auditing websites and discovering vulnerabilities can be a challenge. With RapidScan and UserLAnd combined, anyone with an unrooted Android phone can start hacking websites with a few simple commands.

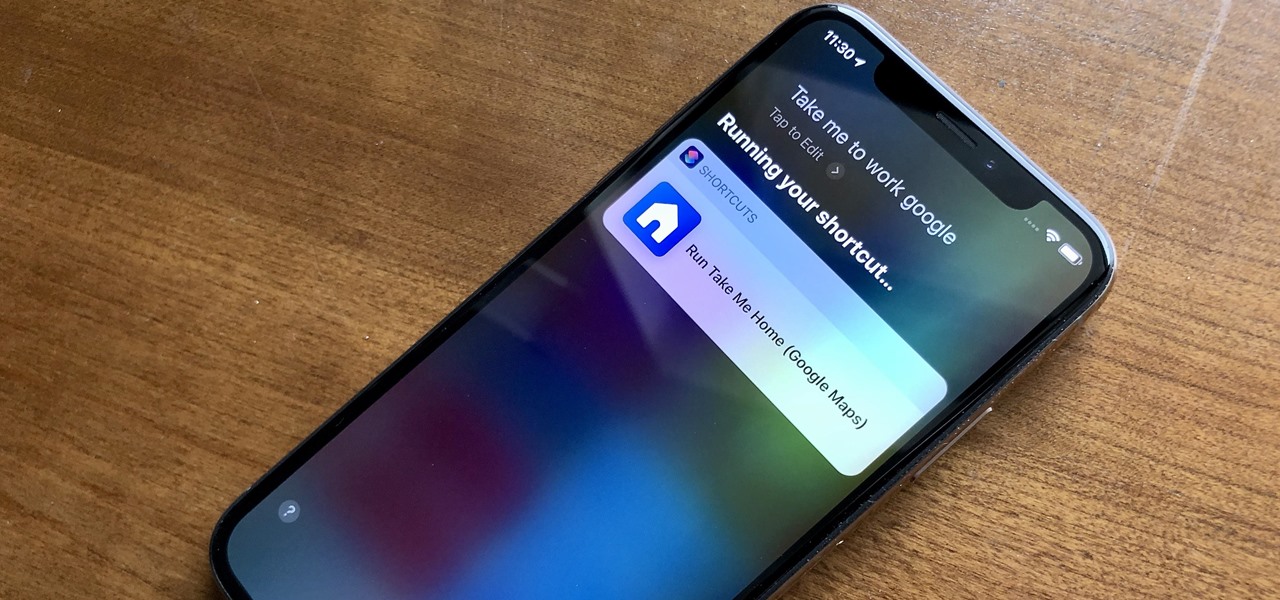
When driving, you can get directions hands-free by asking Siri. You can also make general map searches, show a location's details, call a query's phone number, and view traffic details. However, Siri defaults to Apple Maps for all those. If you prefer Google Maps, Waze, or another third-party navigation app, the map-based Siri commands won't work. But that doesn't mean you can't still use Siri.

The saga of augmented reality startup Meta appeared to be at end, but there are new developments unfolding in real time that may either sink Meta deeper into trouble, or provide a tenuous lifeline for the beleaguered augmented reality company.

To combat their poor coverage in rural areas, T-Mobile spent nearly $8 billion on 600 MHz spectrum in 2017, which was converted to LTE Band 71. With such a low frequency, the signal can travel further, providing LTE speeds to more Americans. But your phone also has to support this frequency, and so far, only a handful do.

Everyone from first responders to hotel cleaning staff use radios operating in the sub-megahertz range to communicate, often without even encoding the transmission. While encoding and encryption are increasingly used in radio communication, an RTL-SDR adapter and smartphone are all it takes to start listening in on radio conversations happening around you.

In the world of technology, there's often a trade-off between convenience and security. The Java Remote Method Invocation is a system where that trade-off is all too real. The ability for a program written in Java to communicate with another program remotely can greatly extend the usability of an app, but it can also open up critical vulnerabilities that allow it to be compromised by an attacker.

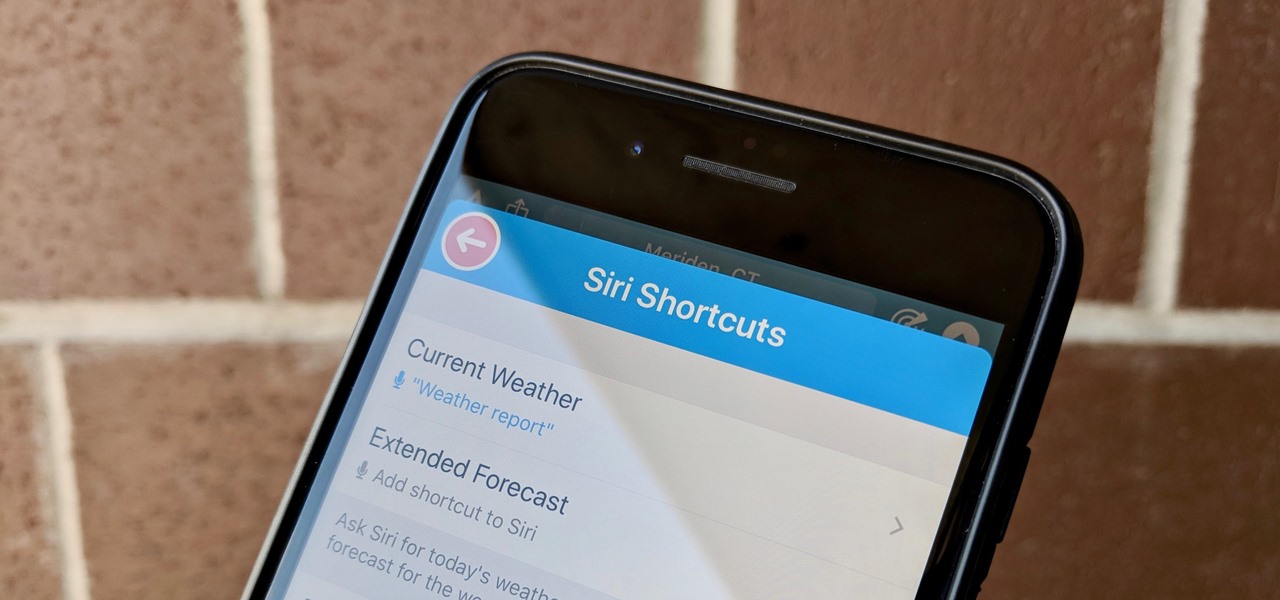
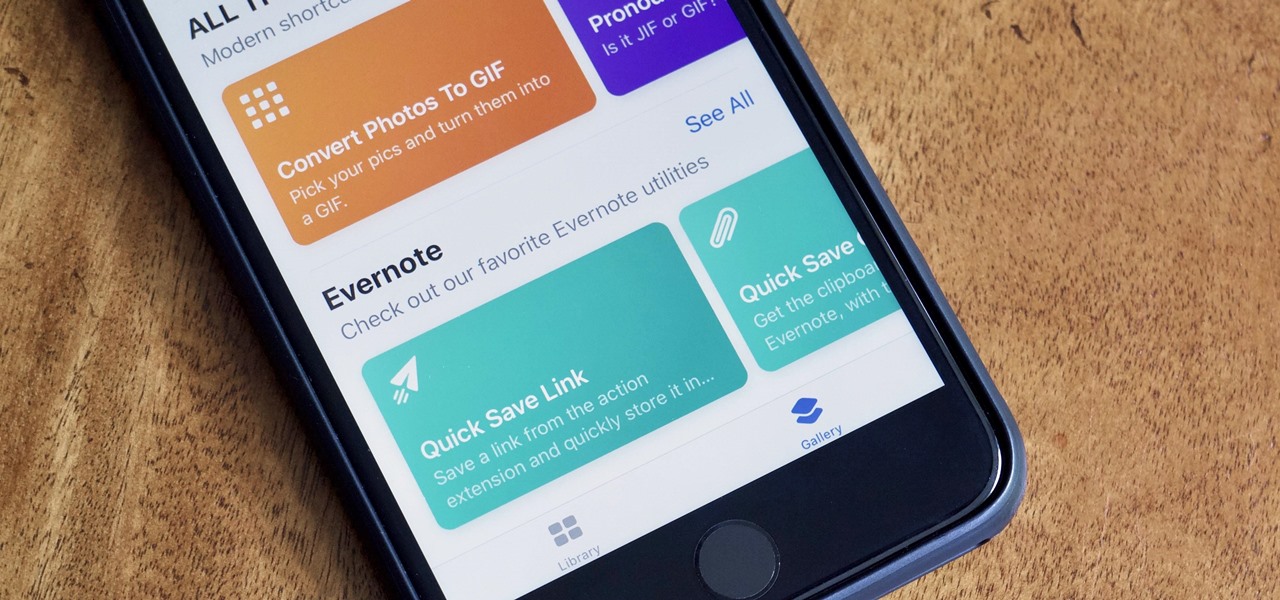
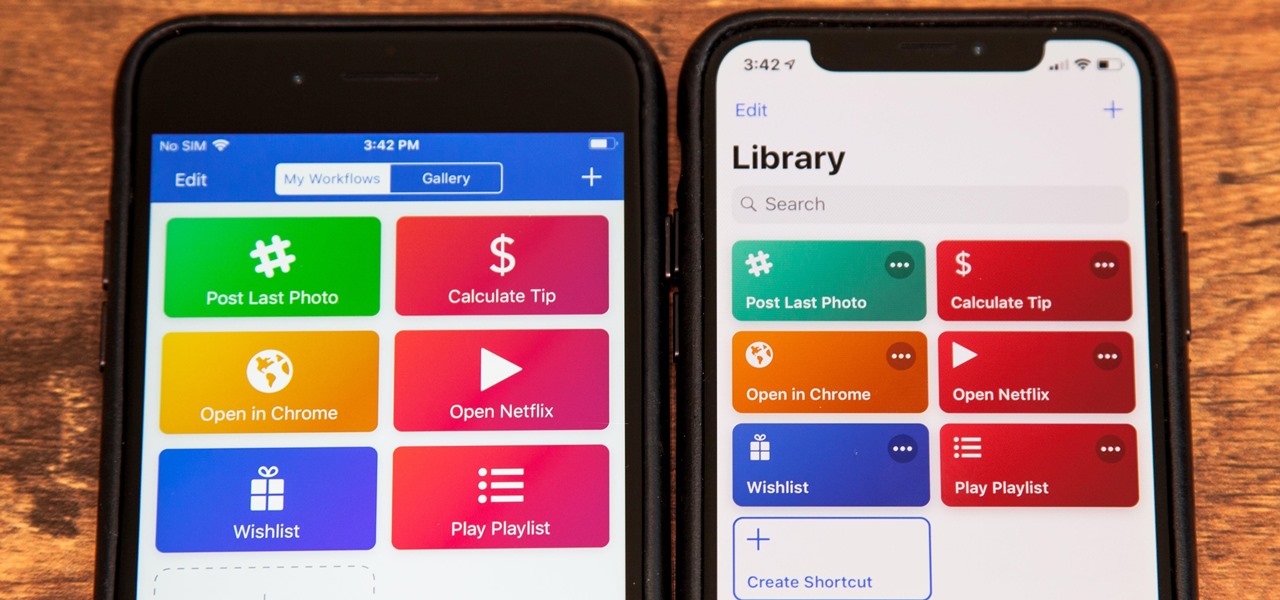
Since its humble beginnings on the iPhone 4S, Siri has come a long way. While each iteration of iOS sees new features for the iPhone assistant, iOS 12 offers users some of the best advancements in Siri we've seen in a long time, not the least of which is support for Shortcuts, Apple's replacement to the Workflow app.

After months of beta testing, Siri Shortcuts has finally arrived on all iPhones that support iOS 12. Anyone familiar with Workflow will understand how useful it is to set custom Siri commands for your favorite apps. Of course, your favorite apps need to be compatible with Shortcuts in order to take advantage of the new feature.

Despite a very vocal distaste for Bixby, Samsung continues to push their voice assistant on customers. For many, the button is not only a waste, but placed perfectly for accidental presses. While it appears Samsung has no intention of giving up on Bixby, with the help of an excellent app, you can get rid of it yourself.

With iOS 12, iCloud Keychain has become a more useful password manager for your iPhone with strong password suggestions, password reuse auditing, and Siri support. However, before you jump ship from your current password manager, you should consider all the reasons why iCloud Keychain doesn't make sense as your primary password manager.

Net neutrality is dead and your internet service providers can collect all the data they want. While VPNs are a great way to protect some of that privacy, they're not perfect. There is another option, though, called Noisy, which was created by Itay Hury. It floods your ISP with so much random HTTP/DNS noise that your data is useless to anyone even if they do get it.

There are dozens of apps like Glympse, Family Locator, and Find My Kids that let parents see where their children's phones are, but they all have one fatal flaw: It's incredibly easy to spoof locations to make it look like the phone is somewhere else.

On August 1, Google Play started requiring new app submissions to target at least Android 8.0 Oreo's API. Then, as of November 1, all updates to existing apps were required target the same API. While at first glance, this change may mean little to you, it will have a profound impact on Android. Now, your favorite apps will be getting better.

Apple's testing a new app for iOS 12 called Shortcuts, and it has a lot of overlap with their existing Workflow app. So much overlap, in fact, that Workflow won't be sticking around for much longer.

Action Launcher has some exclusive features that add real value to your overall experience. One such feature is Shutters, and like with most aspects of Android, there's a workaround that will let you enjoy this functionality on other launchers.

Whichever web browser you use, each comes with a way to surf the net "secretly." While nothing on the internet is truly anonymous, private browsing modes can help keep your movements hidden from those who might have access to your data. The "secret mode" for the Samsung Internet app goes a step further on Android, by locking your private browsing behind a unique password.

While it's very easy to enable "Low Power Mode" on your iPhone, since Apple will prompt you to enable it once your battery dips below a certain percentage, it's not as obvious as to how to disable it. If you start charging your iPhone, it won't automatically disable it right away, but there are a few ways you can manually disengage it to get your iPhone running at top speeds again.

Traditional subdomain enumeration techniques create a lot of noise on the target server and may alert intrusion detection systems to an attacker's intentions. For a stealthier approach, there's a tool with the capability of finding hundreds of subdomains related to the target website without alarming the server administrators.

We know Android 9.0 will have the formal designation of Pie, following Google's age-old tradition of naming their OS after items you'd normally find on a dessert menu. And thanks to a slew of new features that centers around your overall security, P could also stand for Privacy.

Chrome is the browser of choice for millions of iPhone and Android users, largely thanks to its user-friendly interface and native Google support. But with concerns over sharing private information with massive companies growing, many people are starting to want a little less Google integration in Chrome.

You may have noticed improved photo quality in the Android Snapchat app in recent months. Believe it or not, this is because Snapchat only just recently started using a decade-old camera API that predates every Android phone in existence.

Passwords stored in web browsers like Google Chrome and Mozilla Firefox are a gold mine for hackers. An attacker with backdoor access to a compromised computer can easily dump and decrypt data stored in web browsers. So, you'll want to think twice before hitting "Save" next time you enter a new password.