Last Friday's mission was to accomplish solving HackThisSite, Realistic 5, the fifth and last in my series of realistic hacking simulation missions. This time, telemarketers are invading people's privacy, and it was up to us to stop them! The job was to get root on the site and delete the contact database in order to return the right of privacy to its victims.

No longer do you need to crowd around your tiny smartphone to watch a funny YouTube video with your friends. If you've got a display nearby with a web browser and internet access, you can take control of it with your mobile device for free with the new Clik app.

Last Friday's mission was to accomplish solving HackThisSite, realistic 4. The fourth in a series of realistic simulation missions was designed to be exactly like a situation you may encounter in the real world. This time, we are told "Fischer's Animal Products is a company that slaughters animals and turns their skin into overpriced products which are then sold to rich bastards! Help animal rights activists increase political awareness by hacking their mailing list."

In this article I'll show you how to make a simple IP address notifier. The program will text you your new IP address, in the event that it changes. For those of you with dynamic IPs, this is very useful. I'm constantly frustrated when my IP changes, and it's handy to be notified via text when it happens. To use the program, you'll need Python 2.7 or later, urllib2, and a program called "text" (see this article here to get it).

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server. If you missed this Workshop check out the follow up tutorial Techniques in Architecture.
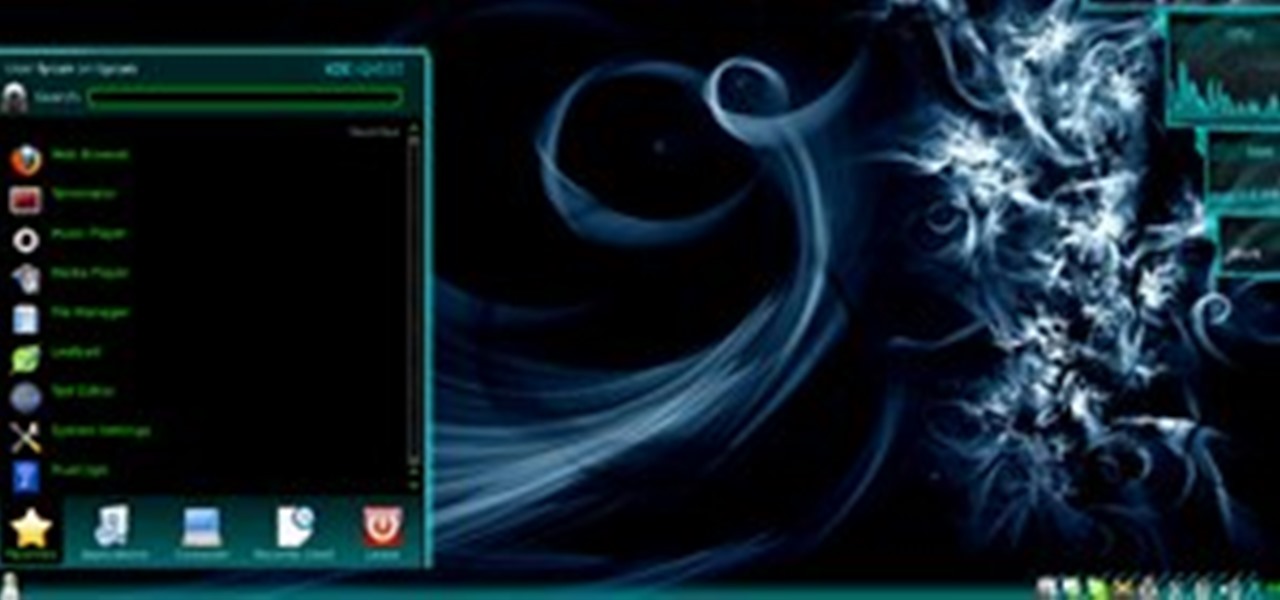
Linux can have the most beautiful interface in the world, because it is simply what you make of it. You can change every little detail with relative ease because that's what Linux is all about: Freedom and OpenSource.

A few weeks ago, I discovered something awesome on the way home from work. Mozza, that LA pizza mecca, is on my route. And I could pick up a pizza or two from their takeout place - Mozza2Go.

Welcome to Pizza Perfect. I'm a novice pizza maker with one goal: to master the art of the homemade crust. The cheese (fresh mozzarella), the sauce (endless options or super basic), and the toppings (the sky is the limit) are all easy. But the crust I've found to be somewhat elusive.

Web-spying technologies like FaceNiff, Firesheep and Newstweek are out there showing the world just how easy it is to see what you're doing online, but they're amateurish in comparison to what real hackers could do to you if they catch you browsing unsecured websites.

So you just bought Photoshop, a DSLR camera and your first flash. Now what? If you have some experience with photography, but you're not completely fluent with the software and equipment, WonderHowTo's newly featured World Lights! Camera! Photoshop! is essential.

What do you get when you combine eBay, foursquare, and Craigslist want ads into a single mobile application? A really gnarly mobile bazaar called Zaarly that lets you post wanted products or services based on local proximity and timeliness. It's not a new idea, but it's the first to get it right.

Android users are probably already familiar with the doubleTwist Player (free) from doubleTwist, available on the Android Market. They recently added AirPlay support for users with AirSync ($4.99) that allows streaming to Apple TV and DLNA devices, which is sure to provoke some cease and desist requests from Apple. But their second, newly unveiled feature is more enticing—doubleTap, which adds proximity-based file sharing for Android devices.

Advertisng is the key of selling products. Internet is one of advertising media, So many websites on the internet just making money from the online advertising. In online advertising the one that play an important part is traffic or page rank, the website is not valued by appearance or designing only, nor the cheap or the special products only, but the most have a role is traffic. Eventhough the appearance and your produst on the site is cheap you can't get buyer or visitor with the weak page...

For travelers on-the-go, or penny pinchers who like to surf the web for free in public places, there are necessary precautions one must take when accessing sensitive information over a public WiFi connection. For advice on doing this safely, check out Glenn Fleishmann'sguide to staying protecting your private information. Fleishmann outlines how to:

How is it that we use Firefox tremendously and yet not care for its needs? You might have noticed Firefox sometimes tends to slow and not respond often. You might have installed countless add-on in Firefox to enhance your using experience, to get the most out of your Firefox use these Hacks. The about:config page contains all most all of the tweaks and enhancements available for Firefox to day.

Black Roses are here! These are the first of Limited Edition giftable seeds that you can master! This was announced in the last podcast.

On your farm Once you get your frame, you will need 8 of each building material (nails, bricks and boards) to build your Haunted House frame. There are 3 stages of expansion for this constructible building.

Say hello to "Meet Eater," the world's most social garden. Seriously — say hello! Its life may depend on it:

Update! We've now sent 1 billion school supplies!

From LAist: As Los Angeles law stands today, you can only own and register up to three cats and/or dogs. More than that would require a resident to qualify for a kennel permit. Now a motion to increase that number to five is gaining traction on both sides of the issue, finds the Daily News.

In the past you may have blocked wall posts so you wouldn't get fuel, goods, and other random things from your applications. But you may wish to rethink this, at least for a while as the new truffle hunting feature requires wall posts.

Expires 10/26 at midnight. One day left on the Gemstone collection and now we can collect items for the Toy collection!
I'm having a hard time finding my older posts, so I'm sure you are too. I'll put them all here so you can find them easily. You can bookmark this if you want :)

You need lots of items to help you on your homestead! Why not let your neighbors know what you're looking for by posting a wishlist?

The medical field has known for some time now that negative pressure (re: suction) can drastically speed up wound recovery time. However, the machines that are currently available are quite expensive, and not an option for third world countries. Enter MIT student Danielle Zurovcik. The doctoral student has created a hand-powered suction-healing system that could completely revolutionize first aid in developing nations. Her device goes for only 3 bucks a pop.

IP Hider masks the real IP of a user, allowing him to browse all kind of pages without ever worrying that the ISPs or any other marketing tool is monitoring your surfing habits or spammers are attacking your computer. The simplest way to do this is to have traffic redirected through anonymous proxies.

Facebook's mobile app lacks many features from the desktop site. Even if you open Facebook in your phone's browser and request the desktop version, all that does is basically resize the mobile app. But there's a simple workaround that will force Facebook to appear in all its desktop glory on your mobile browser of choice.

As much as streaming services like Apple Music and Spotify have dominated the music industry, radio is still alive and well. And why wouldn't it be? Free music, 24/7? It's a great deal. That's why it's so cool that your iPhone can instantly tune in to your favorite radio station, even one across the country.

I use my iPhone's personal hotspot all the time. Whether I need a connection on the train, in a coffee shop with no Wi-Fi, or when my friends don't have service, my personal hotspot is a lifesaver. But all that data comes from somewhere, of course, that somewhere being your cellular plan. Luckily, you can see how much data your hotspot has used, as well as who or what used more of it.

Apple has revealed software improvements and new hardware users can look forward to today, including a new and improved Control Center for iOS 11. This recent announcement shows that the Control Center will now be consolidated into one panel as opposed to two, and all commands will be displayed by small icons.

Welcome everyone Today i will show you a simple but very useful way to stop your ip leaks . In order to stay anonymous on the web you HAVE to do this.

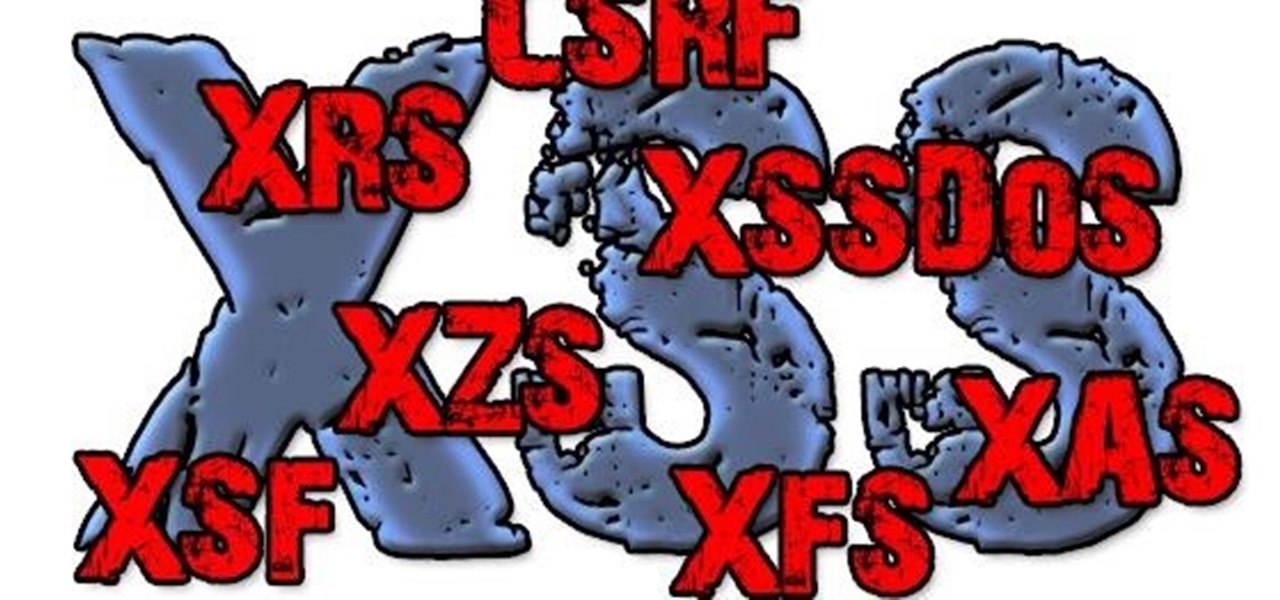
BeEF is an XSS-exploiting framework that lets you "hook" or gain control of victim web browsers. In this part of XSS exploitation, we will be working on finding an XSS-vulnerable website. We can simply do this by Google Dorking.

You might want to switch countries on iTunes for many reasons. Today I will show you how to switch countries to get apps before they release in Canada (or even sometimes the US). Many apps usually release in New Zealand before they come to USA and Canada. Canadians might also want to switch to American iTunes since there is way more apps.

In this how-to I will show you how to get Google Music in Canada (or any other country) without a VPN or Proxy. And it will only take 5 minutes

Notes for Gmail now allows you to insert sticky notes directly onto your email threads in Chrome. The browser extension, currently in beta, allows you to annotate your emails as a whole (thread)—or individually. You can add as many sticky notes as you would like and they all appear at the top of the webpage for easy accessibility. To download the application, go to this page and request an invitation. They add users everyday—I was added almost instantly after I applied. Once you've downloaded...

In my Wireshark article, we talked a little bit about packet sniffing, but we focused more on the underlying protocols and models. Now, I'd like to dive right back into Wireshark and start stealing packets.

Imagine you're in Paris and you need to get to Versailles. Looking around for directions, you come to a cold realization—you do not speak a lick of French! How are you going to get to Versailles and what happens if there is a detour? It will be a difficult struggle, and you'd probably get lost and eventually fail. This is why it's important to know some of the country's language before taking that trip in the first place.

Remember that scene in The Matrix when Trinity uses a realistic Nmap port scan, followed by an actual SSH exploit (long since patched) to break into a power company? Well, believe it or not, but that scene is not far fetched at all. If you want to exploit vulnerabilities and root boxes, you'll need to learn how to perform the necessary reconnaissance first. In fact, you will spend far more time researching your target then you will exploiting it. In this article, I am going to show you the fi...

You've probably seen those deep-web images floating around on the Internet. Usually, it goes something like this: There is a towering iceberg and the deeper the underwater portion extends, the more “hidden” and “exotic” the content is described to be. Sometimes these images are accurate to a point, but most are just making things up.

Before you start snapping away and submitting your photos, please take some time to read the official rules below!