
While many have their own strong opinions on Apple and their products, few have complaints about the way they embrace accessibility. Apple typically finds ways to make products functional to all customers, regardless of their situation. This philosophy can be seen in Apple's partnership with Cochlear, as the two develop a new cochlear implant sound processor for iPhone.

Amazon has been toying with the idea of opening physical retail stores for some time now, even opening old-fashioned bookstores in select locations and teasing cashier-less convenience stores. But the online retailer has some new ideas in the works, including implementing virtual and augmented reality into retail home stores.

Escape rooms, those real world puzzle games that challenge teams to solve a mystery and gain their freedom from a locked room, are all the rage right now. But augmented reality games such as The Lockdown could make them obsolete.
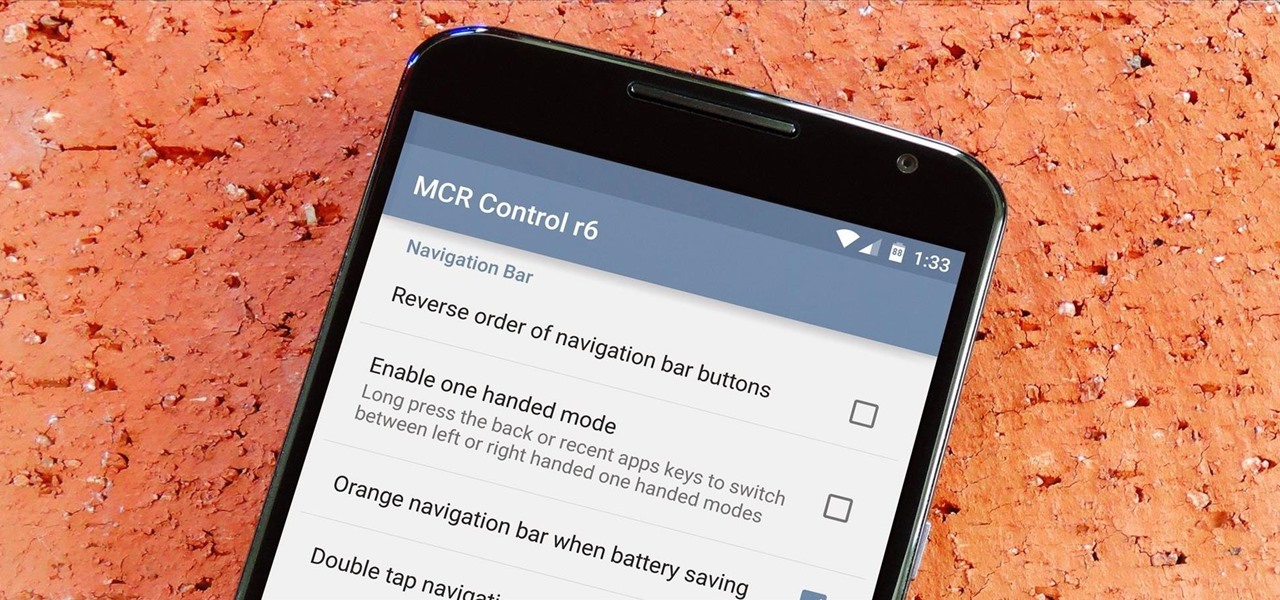
If you've ever flashed a custom ROM on any of your devices, one of your main motivations for doing so was likely the set of neat tweaks and extra options that come with something like CyanogenMod. Another deciding factor was probably the fact that most custom ROMs offer a much cleaner interface than manufacturer skins.

Null Byte users have often requested video content, but the question has always been what format would best serve our community. This week, we partnered with Null Space Labs, a hackerspace in Los Angeles, to test the waters by hosting a series of talks on ethical hacking for students in Pasadena Computer Science Club. We invited students and Null Byte writers to deliver talks on Wi-Fi hacking, MITM attacks, and rogue devices like the USB Rubber Ducky.

It seems like a new, dangerous Android exploit is uncovered every month or two. The latest headliners are NightMonkey and Chronos from the list of CIA hacks reported by Wikileaks, which have been billed as gaping security holes in the world's biggest mobile operating system.

It's easy to have your password stolen. Important people like executives, government workers, journalists, and activists face sophisticated phishing attacks to compromise their online accounts, often targeting Google account credentials. To reduce this risk, Google created the Advanced Protection Program, which uses U2F security keys to control account access and make stolen passwords worthless.

One could argue that, at least for the moment, software development is more important to the augmented reality experience than hardware. Since a viable augmented reality headset has yet to emerge for the broader, mainstream consumer market, currently, the same devices that make texting and selfies possible are leading the charge to enable easy-to-use AR experiences.

After installing Ubuntu as your primary OS, you should have protected against USB Rubber Ducky payloads, defended against hard drive forensics, and reduced the overall attack surface against physical strikes. When defending against network-based attacks, you'll want to minimize hardware disclosures, prevent packet sniffers, harden firewall rules, and much more.

You've protected your Ubuntu system from physical attacks, annoyed network hackers, and sandboxed potentially malicious applications. Great! Now, the next logical steps to locking down your OS include thoroughly auditing Ubuntu for weak points, using antivirus software that respects your privacy, and monitoring system logs like a boss.

Once you've installed Ubuntu with security in mind and reduced the possibility of network attacks on your system, you can start thinking about security on an application level. If a malicious file is opened on your system, will an attacker be able to access every file on the computer? The chances are much slimmer if you put the proper defenses in place.

Anybody who spends most of their day on the internet should know all about lulz. Lulz are most often jokes made at the expense of web users, as popularized on 4Chan. Today, a consortium of hackers called LulzSec is attempting (and in some cases succeeding) in efforts to shut down some of the games that offer web users a giant share of their online fun. World of Warcraft, League of Legends, EVE Online, and Bethesda Softworks have all been targeted by LulzSec's hacking efforts in the last week,...
I read Timothy Keller’s The Reason for God on the recommendation of a philosophical friend and before I had finished it I was adding Keller’s The Prodigal God to my list of books to read. Keller has a gift for succinct and wise writing. I believe he truly has his finger on where society currently is spiritually, and where it might be going. In The Reason for God, Keller says that our society is both more spiritual and more secular than it has ever been. The book is a great look at the Christi...

This Null Byte is the first part in a mini-series on the art of Social Engineering. I will be teaching you how to effectively defend yourself against it.

The Xbox 360 is America's video game system. It was designed in America, it has better market share in America than anywhere else, and it has the most overtly macho game catalog of any console. For many Xbox fanboys, gaming heaven is shooting hordes of really well-animated things in the most intuitive way possible. Trouble Witches NEO - Episode 1: Daughters of Amalgam, released last week on Xbox Live Arcade (XBLA) for $10 by Japanese developer Adventure Planning Service, is a typical Xbox 360...

At the beginning of every class, or almost every class, we do a series of exercises. The Japanese word for this sort of calisthenic exercise isundo. These exercises derive from the Goju style of karate created by Miyagi Sensei in Okinawa in the early part of the 20th Century. In devising these exercises Miyagi no doubt borrowed liberally from the Chinese, whose influence on the southernmost island of the Japanese archipelago was immense.
















