Take an egg, and boil it for some time. Then take the boiled egg into your hand, then hit the smaller edge of egg to a hard object and remove some peel and take the larger side and do same procedure and remove peel. Then blow with your mouth heavily into the smaller side so that you will get an egg into your hand which does not have any type of peel. Then serve it.

The hardest part in the Ashland level of Darksiders on the Xbox 360 is probably the boss fight between you and Stygian. At the start of this battle, Stygian will be wearing a metal cage around its mouth. This prevents you from doing any damage to the beast so you'll have to remove it if you wish to kill the creature. As Stygian does circles around the field, ride Ruin along side its head so that you can swing your Chaoseater at the cage. Use Ruin's turbo to keep up with Stygian. Smash the loc...

This video tutorial shows you how to install a glass vessel sink or countertop. First you need to make sure that the glass vessel sink or countertop has all of the pieces needed and that none of the pieces are scratched or broken. You then need to place the mouthing ring on the countertop where the sink is going to go. Make sure that the rubber side is facing down. Then carefully set the sink on the mouthing ring. You must then take off the tail piece of the pop up drain. Take off the ridge a...

This trick will show how to magically diffuse two pieces of dental floss together. The magic trick works like this: Take two pieces of dental floss. Put the ends in your mouth. When you take them out the two pieces have magically become one.

iPod and iPhone home automation remote control using Girder is only an install away. Run the lights, heat, security system among other things in your space age home for the 21st century. Make your home a modern marvel with this app for iPhone.

Thaw a beef properly so you don’t lose the precious fluids. The more juice that escapes during defrosting, the less juice that goes in your mouth. Watch this video to learn how to thaw beef properly without making it dry.

In this installment from the Unorthodox Hacking series of Internet security tutorials, you'll learn how to get a shell on a Microsoft SQL Server (or SQL Server Express.) See how easy it is to obtain a shell in a Microsoft SQL database with this how-to.

In this installment from the Unorthodox Hacking series of computer security tutorials, you'll learn a number of methods for hacking Windows shares as well as means of mitigating those hacks. For detailed instructions on Windows shares, and what you can do with them, watch this helpful video guide.

Vegan meals are not only healthy to prepare, but they are super easy and delicious. This how to video demonstrates how to make a tofu cajun salad vegan style. It is a mouth watering, simple dish, served up with out any meat. Watch and learn what you will need to make a vegan cajun tofu salad.

Check out this how-to video for tips on cooking sausage and shrimp jambalaya with brown rice. Take it from chef John on how to have a jambalaya party in your mouth, especially if you like sausage and brown rice to boot! Be careful because sometimes the sausage is very salty.

Check out this how-to video for making traditional naan that is so delicious that it makes your mouth water. To illustrate how naan are traditionally made, virtually visit one of your favorite Indian restaurants (Jaipur Grille in Toronto, Canada) and ask the chef to demonstrate how naan are baked in a Tandoor oven. Enjoy!

This romantic chocolate recipe will help you create the perfect romantic evening .In this how to video we will show you step by step how to make a chocolate lava cake which without doubt is irresistible. Its perfect liquid center literally melts in your mouth.

This is one of the ways that artist Merrill Kazanjian makes his caricatures. He shows the viewer how to make a traditional/digital hybrid (tradigital) collage portrait. Look for interesting eyes, noses and mouths from different photographs. Make an oval for the head and paste down the facial features. Watch to learn more.

Grilling vegetables is a great way to create a super-nutritious, super-delicious entree salad for family or guests. Try this mouth-watering salad that combines a variety of vegetable flavors. Don't forget the coconut oil.

Destroy filler words, overcome stuttering, speak smoothly, improve enunciation, and get better at public speaking all around with just marbles and your mouth! This video is best for people learning to reduce stuttering or students learning English as a second language (ESL).

Here's a cheaper way to get a quality airbrush. You can make this out of household objects and power it by blowing.

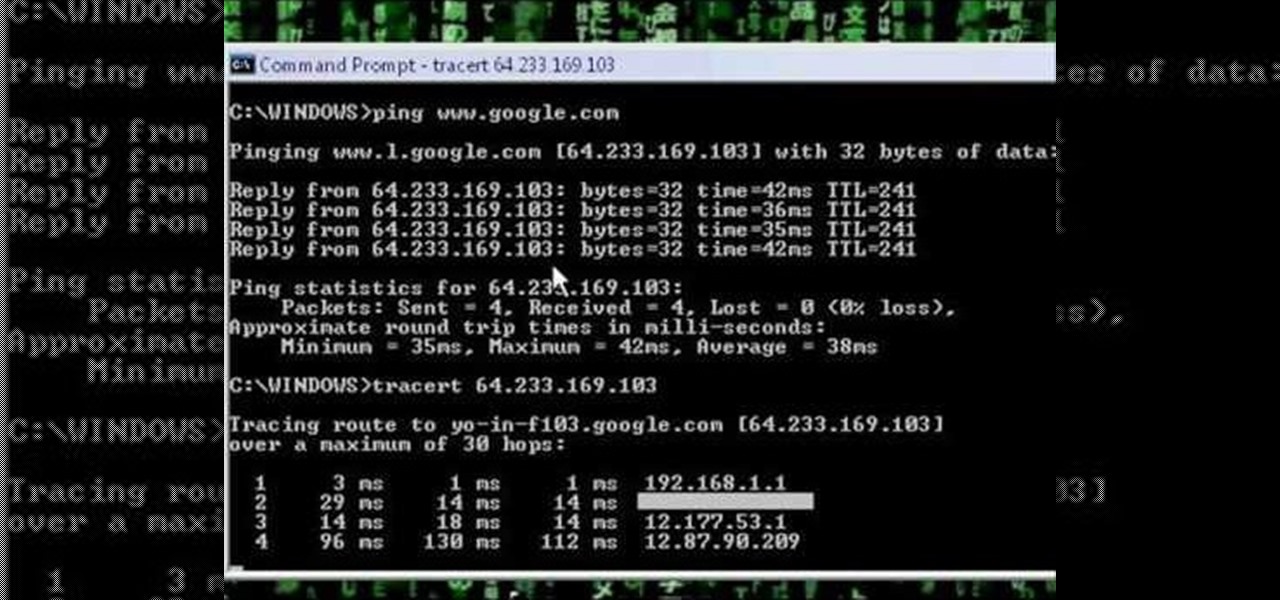
A network security tutorial on using ping and tracert to show th IP of a webserver, your own IP, your ISP's IP, who they connect to, and what computers your request goes through before reaching a destination.

You can learn how to draw a face quickly. You should draw the parts of the face in the following order: eyes, eyebrows, nose, mouth, hair.

Gum is fun to chew on, but no so fun when it pops out of your mouth and lands on the carpet. This video shows you one of the quickest and easiest methods for removing gum in your carpet.

This video demonstrates how give an child CPR in case of an emergency. The video walks you through waking the child, calling 911, breathing twice in the victims mouth, and compressing their chest 30 times.

Many of our online accounts now come with an added two-factor authentication (2FA) functionality to help keep our data safe. This essentially means no one would be able to access the account until a specific set of requirements were met. It could be a combination of a password with a security key or even a passcode with some form of biometrics, like a fingerprint or face scan.

We need to take our privacy and security much more seriously. Whether it's malware-infected apps or the mishandling of our data by companies like Facebook, there are threats all around us in this digital world. Fortunately, some smartphones are simply designed to protect us better.

As smartphone users, we live in dangerous times. The value of phones continues to rise, making them prime targets for thieves. In 2015, the FCC estimated that one million phones are stolen each year, and with several devices starting to hit the $1,000 mark now, these numbers are sure to rise. But what do you do if you fall victim to phone theft?

It seems like there's a cyber security scare every day. Consumers are growing increasingly concerned about the safety of their accounts, and they have reason to be. Hackers will maliciously attack you anywhere — and we mean anywhere — they can to get your private information.

Google's monthly Android security updates are generally welcome—at the very least, they provide a feeling of security that our device is now somewhat safer than it was 30 days ago. Vulnerability patches, slight enhancements to performance, and overall bug fixes are generally included in the monthly OTAs, but as it turns out, they're not always for the better.

When Google released the Nexus 5X and Nexus 6P, they added official support for fingerprint scanning to Android's main code base. On the surface, this was done to ensure that the fingerprint scanner in their own devices could be used to its full extent, but because it was added to AOSP, this meant that the new Fingerprint API could be used by any Android manufacturer.

If you keep sensitive data on your phone, you've surely considered a "lockout" app before. There are many such apps that can add an extra layer of security to other apps within Android. For instance, you can require a PIN or password before anyone is able to launch a particular app.

Most hardcore Android fans loathe carrier or manufacturer additions to the Android operating system. Whether it's bloatware or changes to the user interface, many enthusiasts prefer the clean look of stock Android.

Video: . Step 1: The Face Shape

» Homeland Security Report Lists ‘Liberty Lovers’ As Terrorists. A new study funded by the Department of Homeland Security characterizes Americans who are “suspicious of centralized federal authority,” and “reverent of individual liberty” as “extreme right-wing” terrorists. » British police get battlefield weapons.

iPhone and Android both have a lot of great features. Enjoy the best of both worlds when you install Android lock on your iPhone. This is a great way to secure your iPhone. Use Android lock to get an extra layer of security.

With the TSA's full-body scanners occupying a great deal of airports nationwide, the debate remains as to whether air travelers should continue to be subject to immoral security techniques and possible health risks due to the x-ray scanning devices. The "advanced imaging technology" may help keep obvious weapons out of major airports, but scanning naked bodies seems more voyeuristic than crucial to national security. But while the argument continues, one woman is taking a stand… well, not rea...

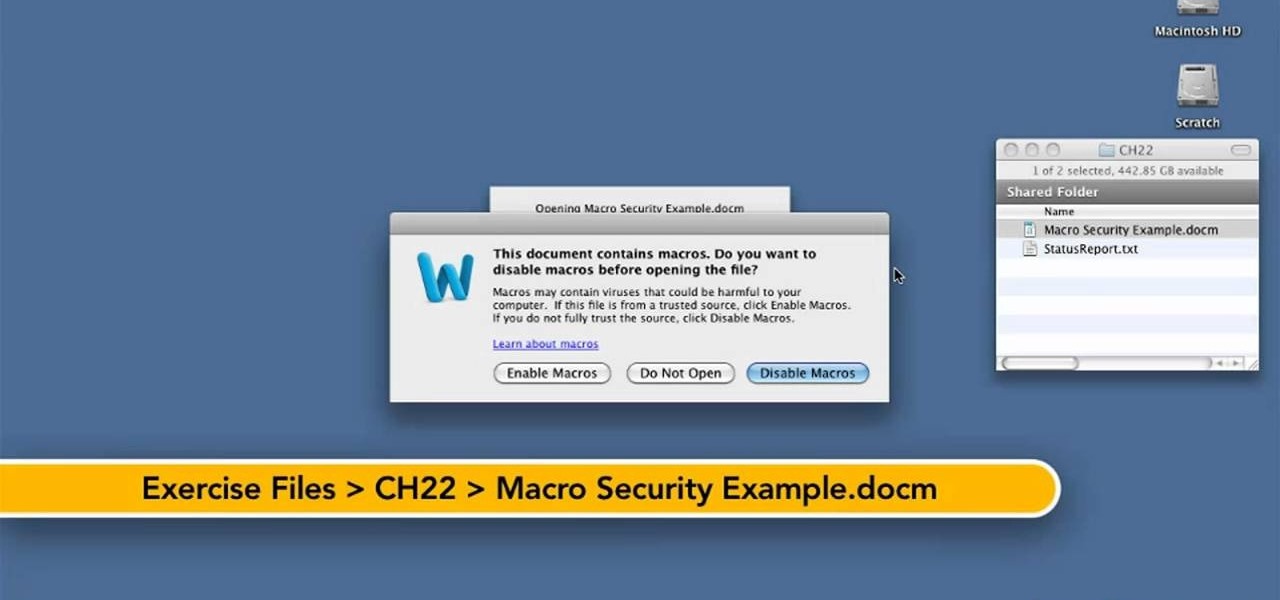
Want to know how to keep safe when using macros in Word for Mac 2011? This video will show you how it's done. Whether you're new to Microsoft's popular word processing application, new to MS Word 2011 or even an expert merely looking to brush up on the fundamentals, you're sure to be well served by this quality video tutorial from the folks at Lynda. For detailed, step-by-step instructions, watch the video.

If you have children who are still your dependents and have been living in your household for at least half of the year, and have their own social security number, you can actually get a major tax credit with a simple worksheet. In this video you will learn the requirements for the tax credit and also how to fill out the worksheet and calculate your credit.

In this clip, you'll learn how to crack a WEP or WPA key on a GNU/Linux computer with GRIM WEPA. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.

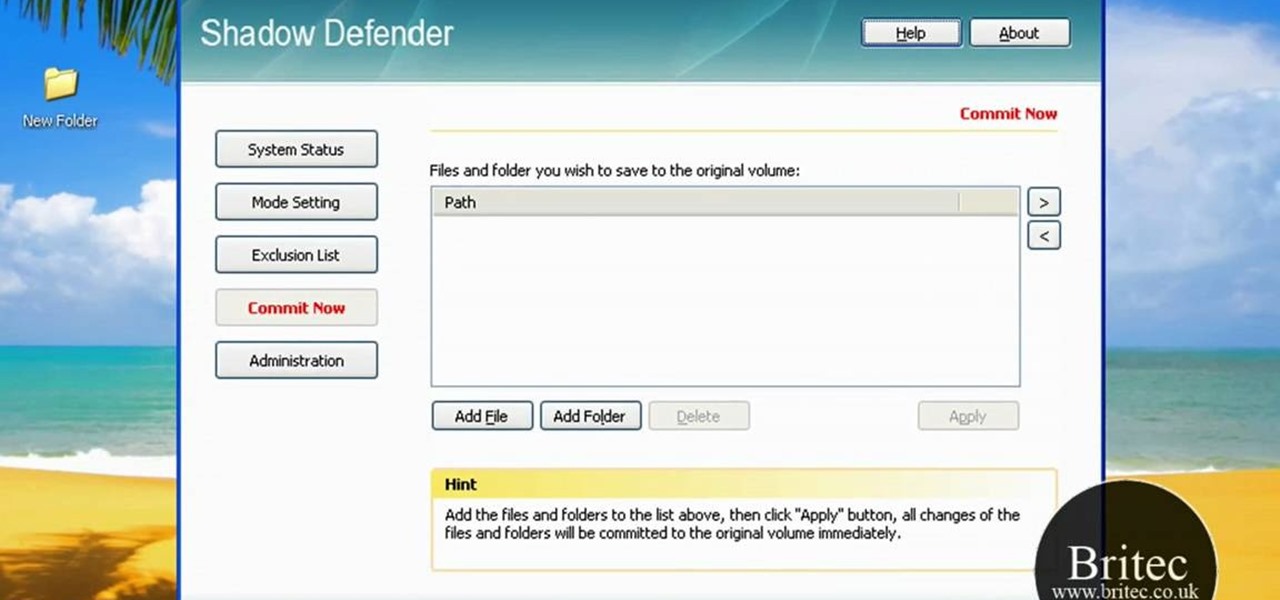
Looking for a security solution for your Microsoft Windows PC? With Shadow Defender, it's easy! So easy, in fact, that this home-computing how-to from the folks at Britec can present a complete overview of the process in just under ten minutes. For more information, including step-by-step instructions on how to get started using Shadow Defender to protect your own desktop computer or laptop, take a look.

In this tutorial, we learn how to draw small faces on paper. This is best for drawing on comic books, because the faces are smaller than on regular drawings. First, give yourself a scale size to see how large you want the faces on the paper to be. If you are new at drawing, use the square method to learn how to measure the face and learn how to draw the face so the body is scaled to the size of the head. Start out by drawing the head and adding in shading details. You will start with the guid...

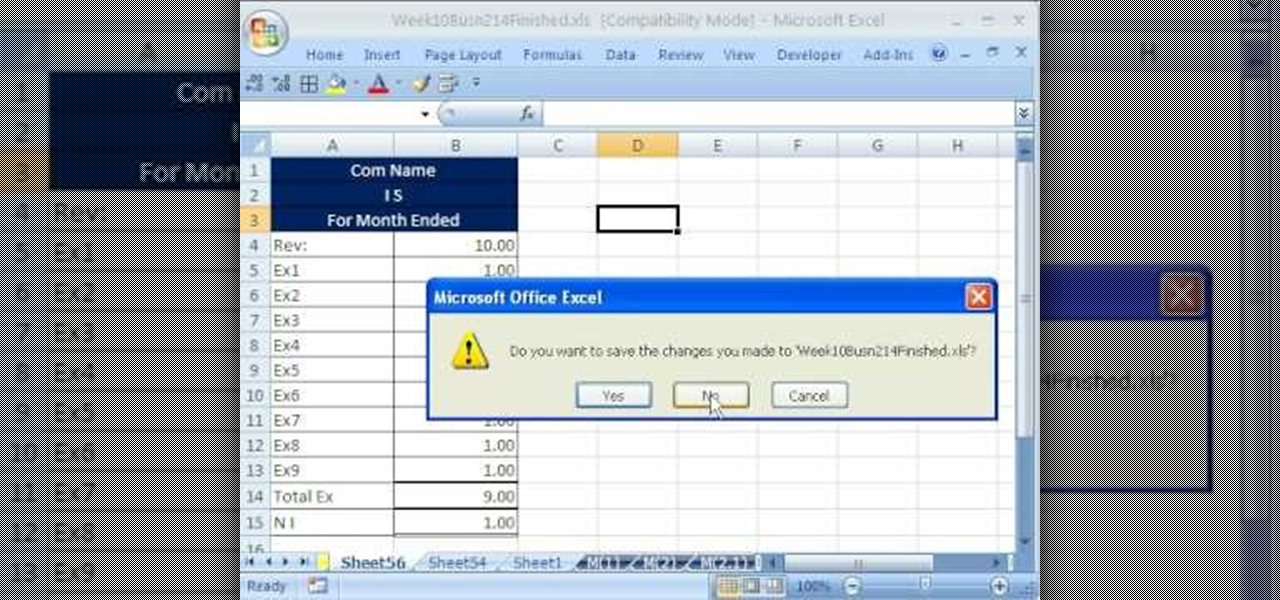
hether you're interested in learning Microsoft Excel from the bottom up or just looking to pick up a few tips and tricks, you've come to the right place. In this tutorial from everyone's favorite digital spreadsheet guru, ExcelIsFun, the 52.5th installment in his "Highline Excel Class" series of free video Excel lessons, you'll learn about macro security. For more information on how to use macros safely, watch this free video guide.

This how to video shows you how to make your avatar look like the Joker from Batman Arkham Asylum. First, go to the avatar edit menu. Hold the button down for 60 seconds until the box tilts. Now, search for spiky hair and choose a green color. Now, move on to the eyes. Choose evil eyes and select any eye color. For the eyebrows, choose a curved shape for an evil look and select a black color. For the ears, choose long ears. For the nose, select a wide or defined nose. For the mouth, select a ...

In this how to video, you will learn how to draw a cartoon fish. First, draw a circle for the body. Add a curly fin at the top and bottom. Next, draw a triangular shaped tail at the back. With the basic outline finished, draw in the details of the face, such as the eyes and pointed mouth. Re-trace the outline of the fish with a bumpy line. Next, draw in bubbles near the mouth. Draw details in the fins such as lines running through them. Add some texture lines through out the body. Once this i...