While all eyes might be on the next beta release for iOS 13, Apple is still pumping out updates for iOS 12. The company released iOS 12.4.1, the first update since iOS 12.4, on Aug. 26. The latest update includes a patch for the jailbreak vulnerability recently discovered in 12.4. One month later, on Sept. 26, iOS 12.4.2 came out for older iPhone models.

In the realm of internet security, it's becoming clear that augmented reality is not immune to the increasing wave data breaches plaguing users.
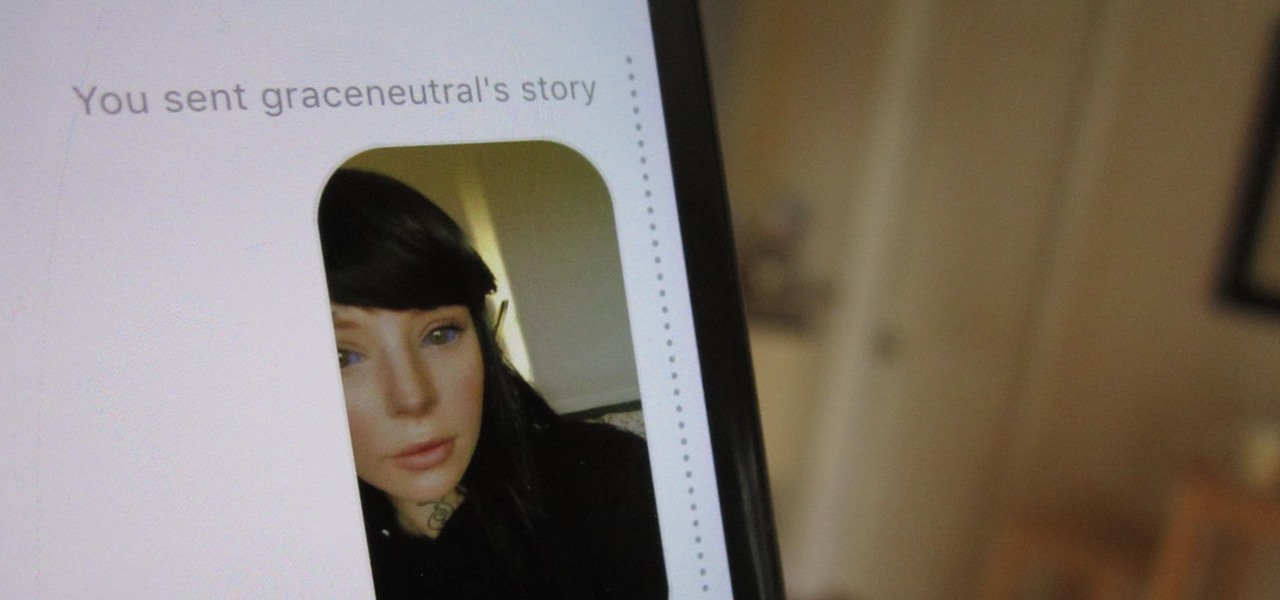
Instagram introduced a new feature in September 2018 that lets you share other users' Stories via Instagram Direct, the app's private messaging tool for solo and group messages. Problem is, it works both ways, so whenever you add to your ephemeral Story, everybody that sees it can share it directly with anyone else.

Get ready for more software testing. Just two days after the official release of iOS 12.1, Apple seeded public software testers iOS 12.1.1 — one day after developers received the update. While the rest of the iOS world is just getting to know all of the cool, new 12.1 features, testers are now sinking their teeth into what the next iteration of iOS has to offer.
While iOS 12 is arguably the best iteration of Apple's mobile operating system yet, one major fault so far is security. On Sept. 26, Videosdebarraquito discovered a passcode bypass that gave access to contacts and photos from the lock screen. Apple has since patched that security flaw, but Videosdebarraquito has discovered a new one that affects all iPhones running iOS 12.1 and 12.1.1 beta.

Two-factor authentication (2FA) is a great way to add another layer of security to sensitive third-party apps and websites like Venmo. However, before iOS 12, to log into a particular 2FA-secured app or site on your iPhone, you'd have to memorize or copy the SMS code from Messages, then jump back in a timely manner to log in. Apple's latest iOS version streamlines this process.

BlackBerry has formally unveiled its latest flagship, the KEY2, during an exclusive event in New York. The Android-powered KEY2 retains its distinctive BlackBerry aesthetics with a physical QWERTY keyboard. Here's all the juicy details regarding Blackberry's followup to the venerable KEYone.

As of 2016, there are approximately 1.85 billion Android smartphones worldwide. This growing popularity has led to an increasing number hacks and cyber attacks against the OS. Unfortunately, Android users need more protection than what is offered by Google. The good thing is that there are a number of options available.

Your email is just that — yours. You shouldn't have to worry about other people gaining access to it on your iPhone. Fortunately, Outlook agrees, and has included a way for you to protect your messages with one of two keys no one possesses but you — your face or fingerprint.

T-Mobile has just pushed out a new update to the Samsung Galaxy Note 8, bringing the build number to N950USQU2BQLA. Here's what to expect.

The photo-centric Instagram app is a great way to share "evergreen" pictures and videos when compared to Snapchat and Facebook's new Messenger Day feature. But like all social media, keeping the account secure is an essential aspect, as it restricts unwanted viewers from seeing your content and can prevent unauthorized users from accessing your account. Instagram has several methods for locking down the account including a new two-factor authentication (2FA) mechanism.

Smartphones have been around for nearly a decade now, so we've had plenty of time to develop preconceptions and bias. People that have never owned an iPhone will tell you that Apple devices are restrictive and bland, while others might say that stock Android is boring compared to manufacturer skins like HTC's Sense, despite never having owned a Nexus or Pixel.

What happens if you unknowingly connect a malicious USB drive and it starts infecting your entire office network? Instead of having a panic attack and working all night to find a fix, you can just put on a mixed reality headset like Microsoft's HoloLens and point.

As many of you know, I have been running a couple of series here on Null Byte about digital forensics called Digital Forensics for the Aspiring Hacker and Digital Forensics Using Kali. Although many readers have seemed to enjoy these series, just as many seem to be pondering, "Why should I study digital forensics?"

Hackers are claiming money for a security flaw in Apple's new update. Quick Summary:

T-Mobile's credit-checking system was recently hacked, and this one is about as bad as it gets. The names of 15 million customers, their date of birth and social security number, as well as driver's license numbers and additional information was illegally accessed, meaning the potential for identity theft here is huge.

Security researcher Samy Kamkar, best known for his MySpace Worm, and most recently for his online calculator that can help you crack any Master Lock combination, is at it again. This time he's figured out how to break into security doors that have a motion-sensing egress system.

A four-digit passcode is what protects your iPhone, and the sensitive material within it, from strangers or nosey friends. Four digits are the only thing preventing someone from snooping through your pictures and posting them online for the public to see, and that's if you even have passcode security enabled.

Whether you're a serious, sweating athlete or just need to recover after a night of drinking, chances are you've replenished your body's fluids with a sports drink at some point. Those electrolytes aren't the only thing entering your systems, though. Sports drinks are sugary, sweet, and loaded with calories—but there's a way you can still recharge your body without ingesting the unhealthy additives.

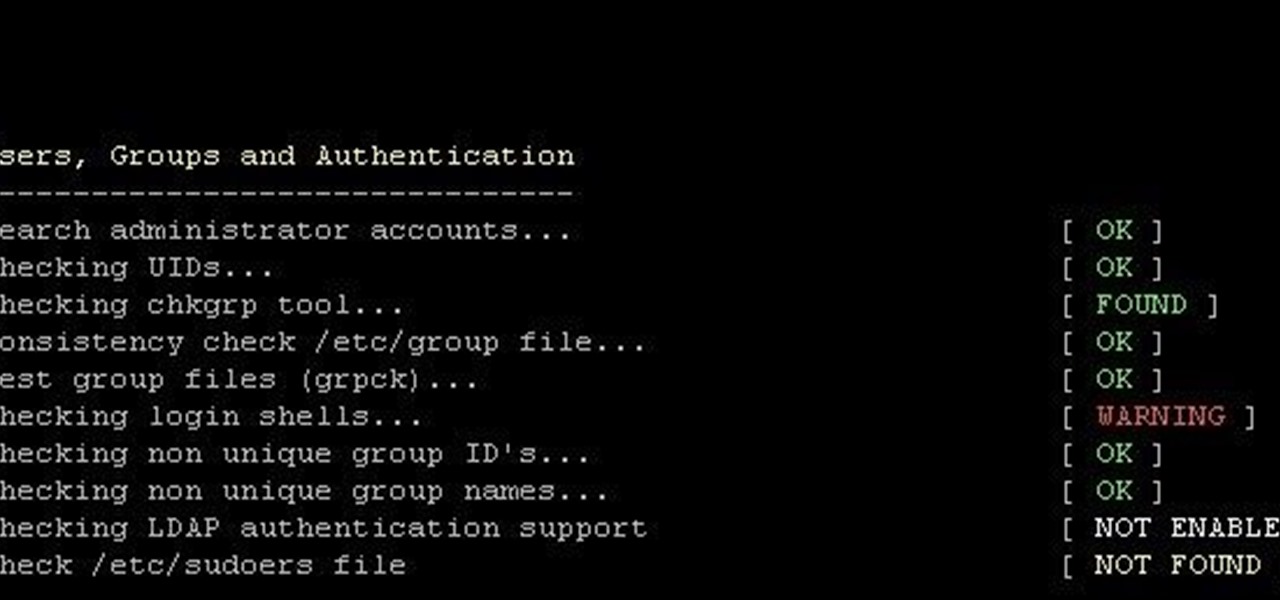
This is finding some of your vulnerability using Lynis. This tool Lynis is used on Unix and Linux type operating systems (sorry windows). So lets get started

In February of this year, the Higher Court of Berlin ruled that Facebook must follow strict German data protection laws, which Facebook's terms of services and privacy policies circumvent.

Back in August, Google introduced Android Device Manager. This new service allowed you to locate, lock, or wipe a lost or stolen Android device from either a companion app or a web interface. Effectively, this is the "kill switch" that legislators are clamoring for.

Locking up your iPhone with a passcode prevents mischievous friends from looking at your pics and emails, and makes it harder for thieves to access your data before you get around to wiping it. For even more security, there's the password option, which gives you more than just 4 lonely digits.

Welcome back, my fledgling hackers! Awhile back, I demonstrated one of my favorite little tools, netcat, which enables us to create a connection between any two machines and transfer files or spawn a command shell for "owning" the system. Despite the beauty and elegance of this little tool, it has one major drawback—the transfers between the computers can be detected by security devices such as firewalls and an intrusion detection system (IDS).

Sprint has announced that it will be the first U.S. carrier to release Jelly Bean 4.1 for the Samsung Galaxy S III. The over-the-air updates have already started, with users receiving a notification on how to update on their phone. The reason Jelly Bean has garnered so much attention is due to several, well-known features like Google Talk, Project Butter and expandable notifications.

The newest update of the Firefox web browser was released yesterday, and whether you were upgraded automatically or manually, Mozilla is advising that you downgrade to Firefox 15.0.1 as soon as possible. Firefox 16 is Mozilla's latest release, and is apparently extremely susceptible to malicious sites hacking their users complete browsing history.

What's your Twitter handle worth? If it's considered "desirable" (aka short and simple), it'll get you around 100 bucks, or, if you prefer, the affections of a teenage girl.

Okay, we're pretty sure that Victoria's Secret Angel Adriana Lima could go bare-faced and wear a potato sack and still put the rest of us to shame. But she looks like a veritable glowing bombshell when she wears bronzy, shimmery makeup for the lingerie and beauty brand.

While the holiday season offers a lot of festive joy in putting up holiday decor, shopping for Christmas presents, and baking cookies, it also offers up a lot of opportunites to spend money. So that means that by the time you've purchased the presents, wrapped them in tissue paper and wrapping paper, and send them off in a box, your wallet is probably shedding a tear.

Did you know that garlic breath is really garlic lungs? According to the Mayo Clinic, garlic breath stems from chemicals in the garlic that get absorbed into your bloodstream and that cause you to give off garlic breath.

In this tutorial, we learn how to draw Maggie Simpson. First, you will draw the head of Maggie. Remember that she has spikes on the top of her head for her hair. Then, you will draw in her eyes, nose, and mouth. The moth should have pacifier in it. After this, draw in the eyelashes and the pupils inside the eyes. Then, draw in the ears and add in additional details around the face and on the hair. Once finished with this, draw in the body with the clothing around it. When finished, you will h...

Low on time but got a bunch of hungry mouths to feed? Don't fret; simply take a gander at this video to learn how to whip up a simple chicken meatball and rice dish.

Once you start making your own scones you'll never go back. While those hardened, several days old scones you get in packs at Costco are great if you're running low on time in general and just need a flaky doughy thing in your mouth fast, the best scones are fresh and homemade.

Spring makeup is all about fresh colors that burst with brightness and flirtiness. But using bright colors together can be intimidating, especially if you're a girl who's used to doing colorless smoky eyes and nude lips.

In this video we learn how to pronounce the Japanese "R" sound. About 90% of people learning this language have problems saying this. The "R" sound is a combination of different sounds, not just the "R" sound like it is in English. There are five different ways to say the "R" pronunciation. You will combine all of these sounds together in one sound, unlike English. To help say these more correctly, start out by making out normal English words, pushing your tongue against the top of your mouth...

Now you can have your flowers and eat them too! While we don't advocate you chomp down on the next bouquet your boyfriend gives you, there is a way to consume your favorite flowers if they're made out of sugar.

This is a video tutorial in the Education category where you are going to learn how to make a miniature vortex cannon. For this you will need normal plastic drinking cup, punching bag type balloon, black electrical tape, lighter, candle, scissors and a drill. Drill a hole in the bottom of the cup and cut off a big circle at the bottom. Cut the punching bag balloon in half and stretch it over the mouth of the cup and tape it up nicely. The cannon is ready. Now light the candle, hold the cup aw...

Don't forget your nails when you're dressing up for Halloween! Like your noggin' and your body, your nails want to put on their spooky best for the fun holiday. If you're looking for interesting nails that are totally Halloween themed without being over the top or tacky, then these nails are it.

Grapes as dessert? After watching this food video you'll think twice about these juicy purple orbs. While we think popping some grapes into our mouths is delicious enough as it is, this recipe combines grapey goodness with icy coldness for a delicious, almost popsicle like snack.

Casseroles don't have the best reputation. After all, they are a Thanksgiving table staple, and we all know that Thanksgiving foods aren't known for being the healthiest foods you can put into your mouth.