No matter what you think of Slipknot's music, you gotta admit they have a cool, horror movie look. This video will walk you through how to make your own Slipknot full head masks. You'll be surprised how simple the process is.

Watch this science video tutorial from Nurd Rage on how to compare regular ice with liquid nitrogen-cooled ice with Dr. Lithium.

Fresh sautéed spinach will help wash the taste of 14 consecutive nights of pizza out of your mouth. You will need:

It's sometimes possible to recognize when you've recently contracted HIV from signs and symptoms such as fever, rash, or swollen lymph nodes. This video will teach you how to recognize signs and symptoms of primary HIV infection that are experienced by between 40 and 90% of individuals after they are first infected with HIV. Primary HIV infection occurs during the first few weeks or months after a person first becomes infected with HIV. Symptoms include rash and/or fevers, possibly in combina...

This is my first contribution in an ongoing series on detailing the best free, open source hacking and penetration tools available. My goal is to show you some of the quality tools that IT security experts are using every day in their jobs as network security and pen-testing professionals. There are hundreds of tools out there, but I will focus and those that meet four key criteria:

Everyone remembers the day Tupac Shakur sadly passed away at the hands of gunfire, but his memory and music live on, and so does his ruggedly handsome look, which you can recreate in a 2Pac portrait. Merrill K shows you how he draws Makaveli in this drawing tutorial, so grab your art supplies and follow along. Pause the video when needed.

The idea of a world without passwords used to be a pipe dream. But as we inch closer to making that a reality, we have services now that securely store all of our passwords under a single master password. It's a convenient way to keep our accounts safe and sound without having to remember all of their credentials. And there's no reason to be afraid — I'll explain why.

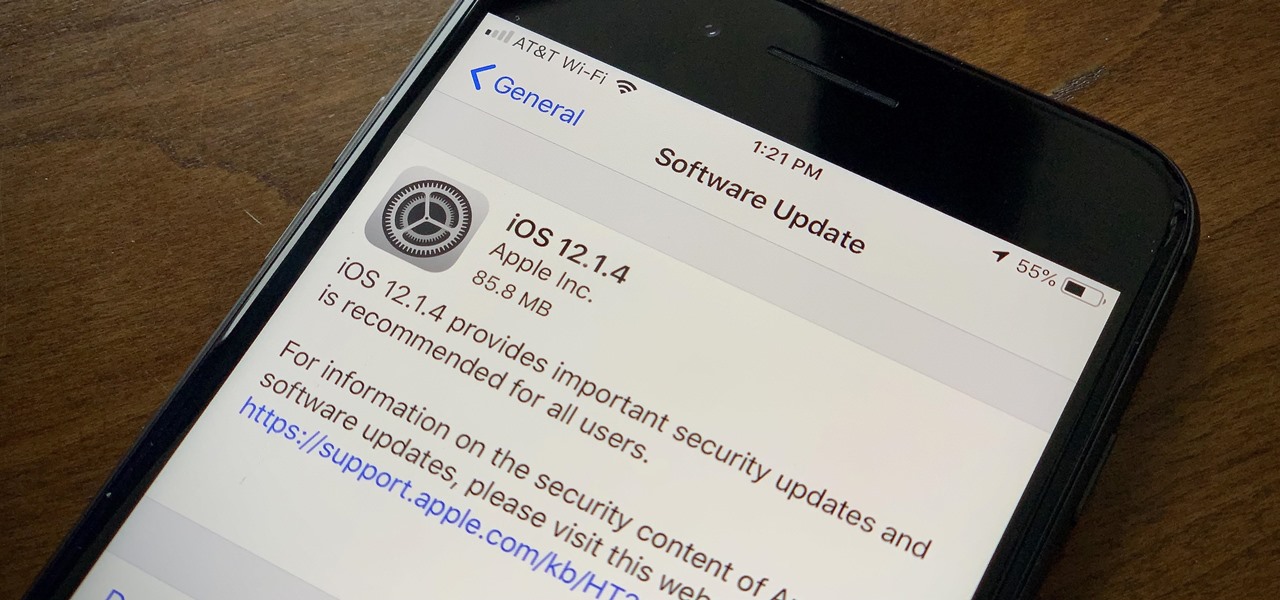
Apple found itself in serious trouble last week when a teenager discovered a critical FaceTime bug that threatened the security of nearly every iPhone user. The bug enabled a user using Group FaceTime to access either the microphone or the camera of a recipient before they answered the call. According to Apple, the issues have been fixed in an iOS 12.1.4 update released Thursday, Feb. 7.

While privacy and security are cornerstones of Apple's ecosystem, your iPhone isn't bulletproof. Creating a strong passcode will protect you from most threats, but there exist tools that can break through even the toughest passcodes via the Lightning port. Luckily, Apple has implemented a new security feature to disable your Lightning port and keep your data safe and secure.

Whichever web browser you use, each comes with a way to surf the net "secretly." While nothing on the internet is truly anonymous, private browsing modes can help keep your movements hidden from those who might have access to your data. The "secret mode" for the Samsung Internet app goes a step further on Android, by locking your private browsing behind a unique password.

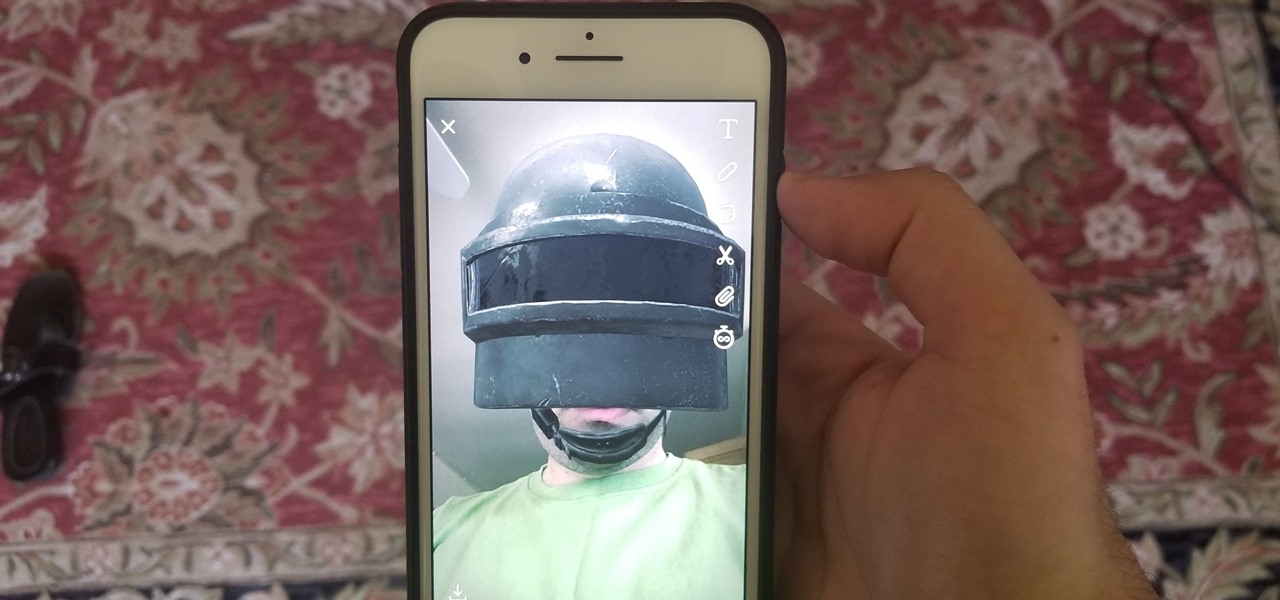
Spring is finally here (in earnest now), and a new batch of great augmented reality Snapchat lenses have come along with it. New life has been breathed into meme culture with the spring lineup of TV shows, Mark Zuckerberg's ongoing investigation, and college kids with too much time on their hands.

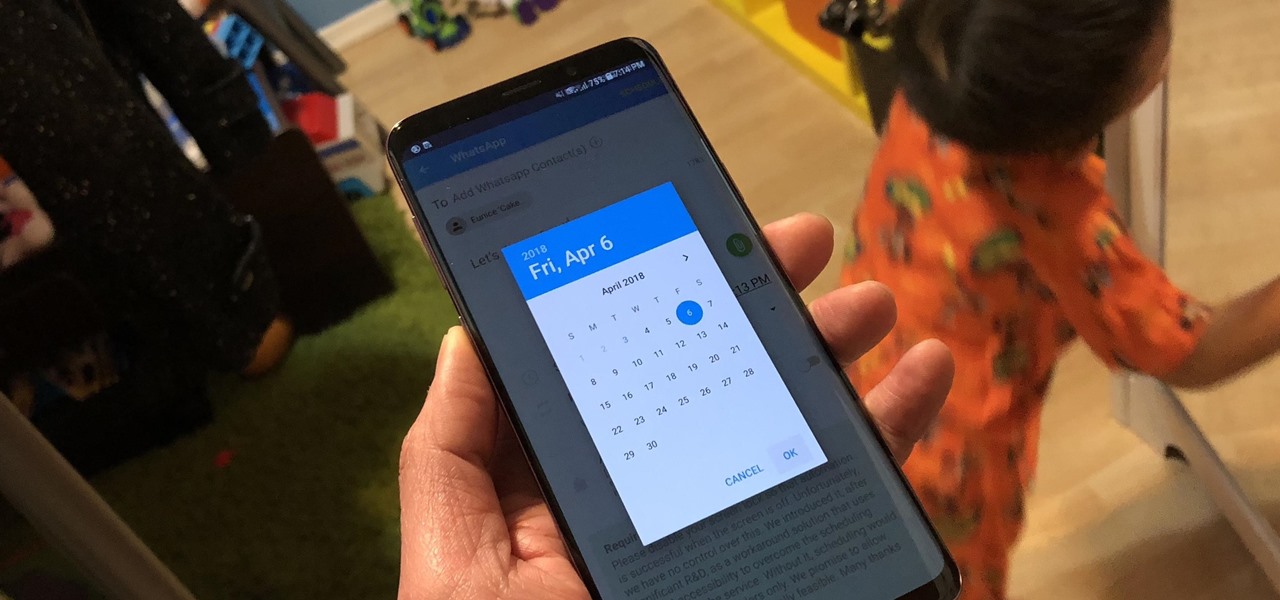
Great ideas often strike at random times, but messaging friends and loved ones at an inopportune hour not only risks their wrath, but also increases the chances of your message not being paid proper attention to. Thankfully, there's an app that lets you create and post WhatsApp messages at the time you wish for maximum effect.

Over the years, the internet has become a dangerous place. As its popularity has increased, it has attracted more hackers looking to make a quick buck. However, as our dependency on the web grows, it becomes increasingly difficult to sever all ties. This means we have to protect one of our weakest points, the password.

There's a new macOS vulnerability that hackers within physical reach of your computer can use to gain root access to your system and accounts. Just by using "root" as the username and a blank password on a privilege escalation prompt, someone can install malware on your computer, access hidden files, reset your passwords, and more. Root access gives them the ability to do anything they want.

Due to the overnight success of smartphones, millions of people are connecting with others. Currently, over 15 million text messages are sent every minute worldwide. Most of this communication is happening in the open where any hacker can intercept and share in the discussion unbeknownst to the participants. However, we don't need to communicate insecurely.

No one is safe anymore, it seems. Google's Project Zero has just uncovered how easy it is for attackers to target your phone's Wi-Fi chip, which is essentially a mini processor for Wi-Fi that detects and processes networks.

As it turns out, your Android apps are pairing together to share your data without asking for your permission first. Researchers from Virginia Tech developed a tool called DIALDroid to monitor exchanges of data between Android apps over the last three years, and what they've found is quite alarming.

If you live with pets, you know where their tongue has been, yet you let them kiss and lick you all they want without even thinking twice about it. I've heard people say that a dog's mouth is very clean, and that their saliva, delivered by licking, can help heal wounds, but is that really true?

Locking individual apps on your Android device gives you an added layer of security by safeguarding app data from unwanted attention. I personally prefer using an app locker over a standard lock screen because my kids play with my phone, and they've completely disabled it after inputting the wrong PIN. So app lockers give me the right balance between giving my children access to my device, and the security of locking down my data from would-be intruders.

If the recent "state sponsored" Yahoo hack wasn't enough motivation for users to stop using their services, the latest news about Yahoo should be. Joseph Menn, a reporter at Reuters, just revealed that Yahoo created a custom email wiretap service for the US government.

CEO's of IT companies doesn't know this because they are not a hacker. Only a true hacker can become a successful Security head officer.

Researchers at the cyber security firm Zimperium have recently uncovered a vulnerability in roughly 95% of Android devices that has the potential to allow hackers to take total control over your phone with a simple picture message (MMS). The gritty details of this exploit have not been made public yet, but hackers now know the general framework for this type of attack, so you can be certain that they'll hammer out the details in no time.

Android Lollipop still doesn't have a simple way to add a custom lock screen wallpaper, so when I came across Corgi For Feedly from developer Stan Dmitriev, I had to check it out. What sets Corgi apart from other lock screen replacements is that it connects directly to your Feedly account to display top stories from your favorite RSS feeds as your background.

Welcome back, my budding hackers! We've spent a lot of time learning to compromise Windows systems, and we've successfully compromised them with Metasploit, cracked their passwords, and hacked their Wi-Fi. However, very little time was spent developing ways to extract the information from the system once inside.

Yesterday, the Free Software Foundation published an article written by Paul Kocialkowski. A software developer for the the Android fork system Replicant, Paul stated that his organization discovered, and later patched, a "backdoor" vulnerability that existed in older Samsung Galaxy devices, including our beloved Galaxy S3s. Only problem is, it's kind of bullshit—but we'll get to that later.

Welcome back, my budding hackers! Previous to this tutorial, we've focused mostly on hacking the target system. If we're successful in owning the target system, we'll then want to make certain that the system administrator doesn't know we were there, and that he or she cannot track us.

David Blaine has made millions off his magic tricks and mind-bending illusions, so why shouldn't we get in on the action, too? Well, your Samsung Galaxy S3 can do all kinds of things, but magic isn't one of them...yet.

If you're anything like me, you probably rinse your mouth out after you brush your teeth. I know technically you're supposed to not rinse your mouth out after brushing, but I just can't stand the feel of the excess toothpaste in my mouth. It's a surefire way to dry it out.

What's the best way to learn how to tie an efficient and sturdy pashmina/shemagh? Why, ask someone who ties one every day, of course. Take a gander at this helpful tutorial to learn how to tie one of these babies on your head quickly from your Middle Eastern instructor.

We get if you don't like clowns that much. After all, with all that white face paint, a snarling too-big mouth, and sinister-looking eyes, they're more creeptastic than jolly. But not all clowns have to be scary.

If you're looking to buy a new used car, then Eric has a great tip for you to avoid getting scammed— look into the horse's mouth. Yes, that sounds cryptic, but it's a very similar process where you look underneath the oil cap. If it looks smooth like it should, go ahead, think about purchasing that vehicle. But if there's a lot of built-up black gunk on the bottom, do yourself a favor and RUN. That engine is destined for failure.

In this video, we learn how to get rid of a double chin with face exercises. This works the chin muscle, known as the metalis. It also works the muscles at the front of your neck. This exercise exerts a gentle pressure on your chin and the front of your neck. It will tone and tighten your neck to make it look youthful and vibrant. It also tones your jaw muscle to define your jaw line and get rid of those jowls. First, stretch out your neck as far as it will go. Then, open your mouth and close...

In this tutorial, we learn how to bleach your teeth for really cheap. First, buy the Plus White teeth whitener kit from a store or online. Once you have the whitening kit, grab plastic teeth molds and see how they fit in your teeth. Once you do this, add some of the whitening gel to the molds, then push them into your mouth on both the top and the bottom. Make sure to rub the gel all the way around your teeth as well so you have a layer of gel all over. Leave this in for the recommended amoun...

In this tutorial, we learn how to make a monkey with Stampin' Up punches. First, you will need to punch out all the appropriate punches that you need to make this. Once you have them, start to assemble by starting with the head. Place the eyes and the mouth on the appropriate spots, then use a black pen to add in further details on the face. As you continue, make sure to glue the different pieces together until you reach the bottom. Once you are done, add any additional details with the black...

If the screenshot for this video isn't enough to tempt you into indulgence, then maybe the description will: This beef casserole is whipped up with a blend of both exotic and familiar ingredients, including an apple, curry powder, mango chutney, and onions.

Health nuts berate creamy sauces because they're too full of fat, carbohydrates, and calories, but who said you couldn't indulge every once in a while? If you love pasta and you love creamy foods then this linguini, topped with a creamy white clam sauce, will be your heaven on earth.

A polymodel head is being mapped. Keep the turbo smooth active to smooth out edges and seams. Use the relax tool to help even out the mesh and areas around the mouth, the ears and the neck as work proceeds. Use the stitch modifier to attach and combine the top and bottom of the head. To get all the seams and areas to match they must be moved, rotated and scaled. Use the weld tool on all the vertices and use the relax tool to get all the seams to match. Use the pelt map for the ears. Use the s...

T.I. is finally out of the joint and back on the hip-hop scene. What better way to celebrate in your own home for free than making an XBox 360 Avatar in his likeness? This video will show you how to use one set of clothing pieces to make a pretty spitting image of the rap star.

Learn Hindi and speak some of the body parts, colors and numbers. So if you say head it will be "sir" in Hindi, Forehead is "matha", cheek is "gaal", tooth is "daant", lip is "honth", mouth is "muh" (you will not hear h clearly

A sleeping prank victim is much easier to deal with than an awake one. They can't prevent the prank, and afterwards are usually too disoriented to respond violently with any effectiveness. This video will show you several pranks to play on sleeping victims, some of which you've probably seen before and a couple we're betting you haven't.