
How To: Peel an Egg in 5 Seconds
This how-to video is about how to peel an egg; many of us are not familiar about this east method of peeling an egg.


This how-to video is about how to peel an egg; many of us are not familiar about this east method of peeling an egg.

To get rid of fleas start by giving your pet a bath every other week. Another good thing to do every other week is to wash all your pet's bedding in hot water. Vacuum all of your carpets once a week to get rid of any flea eggs, baby fleas, and adult fleas that are in the carpet. Flea collars are a problem because they leave a residue on your pets. When you pet your pet you get that residue on your hands and if you put your hands in your mouth you will ingest those chemicals. Natural methods a...

Manga is a popular form of comics and print cartoons that dates as far back as the 1945 U.S. occupation of Japan. This video tutorial shows how to draw a basic anime manga boy using a marker. Start with the eyes making sure to include white circles to imply glossy pupils. Next draw a slight nose and mouth within the shape of a face. Add the left ear and include spiky disheveled hair. After including a slight neckline, base the head in a collared shirt.

Learn Arabic words using the Learn Arabic with Pictures series from ArabicPod101.com. Beautiful images clearly show Arabic vocabulary divided into units by topic.

Not a great lock picker? Well, get some help figuring out how to break into padlocks and high security locks -- check out this video tutorial on how to open locks with comb picks. Comb picks are one of the best ways to hack into these common everyday padlocks. It's not a foolproof way to pick locks, but it's great when it works.

A gin based recipe with a bit of cointreau, pineapple juice and some grenadine. This drink is a bombardment of flavors all exploding in your mouth at the same time.

Does someone at work not have an indoor voice? Before you stuff a sock in her mouth, try this. Check out this Howcast video tutorial on how to deal with a loud coworker.

This is Brian Brushwood with Scam School. The trick is called 'In the bank'. This week we've got another puzzle with a setup that sounds absolutely impossible.

Hummingbirds are just as pretty as flowers—and a lot more interesting to watch. Here’s how to bring these tiny miracles within view.

How to create the puppy dog pumpkin, Good Boy. It's not very difficult, just saw off the top gourd stem and turn the bottom pumpkin upside down. I used some toothpicks to help level the bottom pumpkin. Carve out the eyes, mouth and legs. Gouge the rind off but leave the rest of the flesh on the dog's chest, eyes and tongue. Paint areas if desired. I used a button nose held by straight pins and funny eyes glued on. The ears are attached by toothpicks into the head pumpkin. Just look for unusua...

The spy camera shown in this how-to video has a 60 foot cable, and is full color and has audio. This spy cam can be used as a security device, or to feed paranoid delusions or stalking urges. Watch this video tutorial and learn how to set up an X10 spy camera.

Korean style grilled beef is served with green onion salad, a mixture of bean paste and hot pepper paste called "Ssam Jaang". You wrap it all up into a leaf of lettuce and pop it into your mouth. You can dip some pieces of cucumber and carrot into the spicy paste. Watch this how to video to learn how to cook Korean style marinated beef.

Installing a home security system can be expensive, but it doesn't have to be. This how to video shows you some easy practices that keep your home well protected. All you need is a few inexpensive items such as flood lights, signs, and light timers.

Your home security systems may not work for you if you don't turn it on. To top it off some of your bad habits can invite thieves in to your home. This how to video reviews some common sense steps to protect your home from burglars.
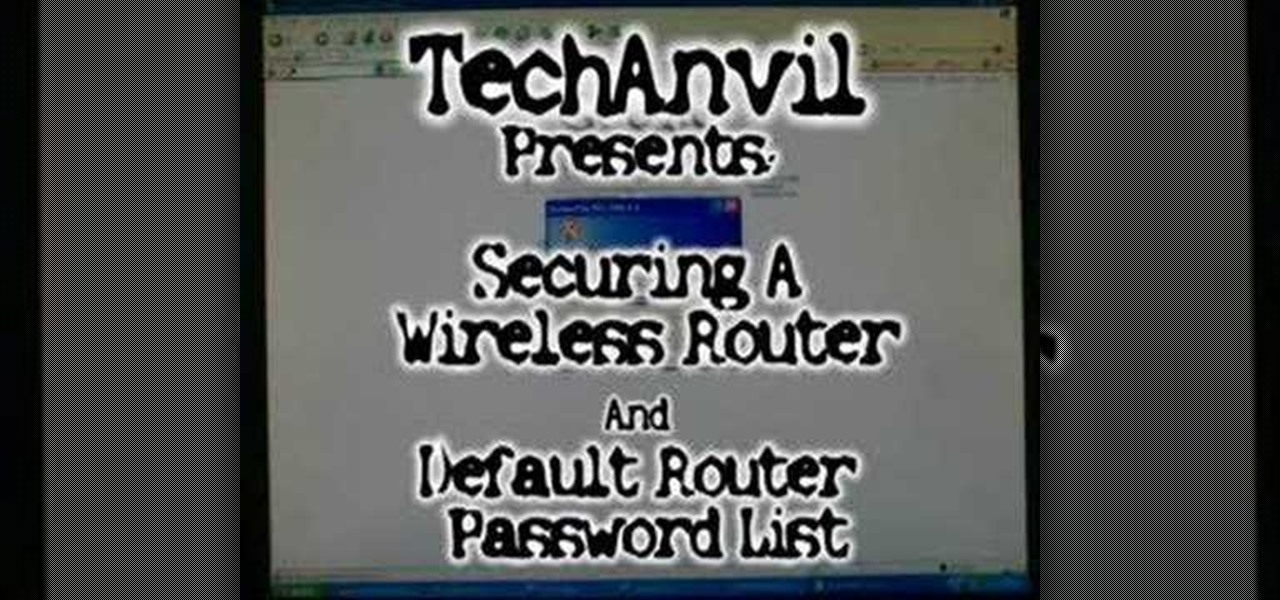
This video walks through basic security configuration for a WRT54G Wireless Router. Also provides a default password list.

This how to video will show you how to make a Mediterranean tuna salad that will melt in your mouth. Watch and learn how to make this classic sandwich with a modern twist.

Watch this how to vidoe and learn how to make mouth-watering southern-style power slaw. This slaw recipe goes great with chicken.

Kids say the darndest things. They also eat the darndest things - from toys to pet food to grass, growing kids want to try it all. But stuffing so much stuff into their mouths can be very unsafe.

This dish was originally made either with all vegetables, or with the addition of Italian sausage. Growing up, Chef John remembers this being made with sweet Italian sausage occasionally, but most of the time it was hot dogs. Hot dogs were simply the least expensive sausage available, and so our grandparents, needing to feed many mouths without many dollars, chose this lower cost alternative. The strange thing is, it really works! It tastes wonderful no matter what sausage you chose

Are you worried about how your bathroom cleaning supplies are damaging the environment and your own air? Use these recipes to create non-toxic, homemade bathroom cleaners instead. Never mix homemade cleaners with commercial cleaners, because when mixed, they can produce toxic gases. Use the same safety precautions as you would with store bought cleaners- keep them out of reach of children and pets, and out of your eyes and mouth. Always work in a well-ventilated area. Store your cleaning ingr...
Numerous potential exploits are found for every operating system each month, and Android is no exception. Trouble is, lots of Android devices don't receive timely updates — but many are now getting regular monthly security patches to at least shore up these vulnerabilities.

When it comes to digital security, one of the best ways to protect yourself is to use two-factor authentication. Most apps these days support it, including Facebook, a site where the more privacy you can muster, the better. However, of the two 2FA options available for Facebook, only one should be used as the other will share your phone number with the world, a huge privacy concern.

Electronic warfare tactics work by jamming, disrupting, or disabling the technology a target uses to perform a critical function, and IoT devices are especially vulnerable to attacks. Wireless security cameras like the Nest Cam are frequently used to secure critical locations, but a hacker can surgically disable a webcam or other Wi-Fi connected device without disturbing the rest of the network.

After years of struggling, it appears BlackBerry has finally figured out how to update its iconic design for modern times. The BlackBerry KEY2 pays homage to past devices such as the Bold 9000 while adapting to modern times with the Android OS. The result is a device that might be the best BlackBerry to date.

As with most social media platforms, Instagram can be a double-edged sword. On one hand, it's a great way to share and express yourself — but on the other, it can be just as effective at compromising your privacy. Thankfully, there are a few things you can do to protect yourself.

As the third-largest smartphone manufacturer in the world, Apple devices are a constant target for hackers everywhere. While iOS has seen fewer common vulnerabilities and exploits (CVEs) in recent years, iPhones still aren't hack-proof. Fortunately, you can strengthen your security with the help of a few apps.

Because of the way Google Play works, Android has a "bad app" problem. Google allows any developer to upload an app to the Play Store, regardless of if it works, how it looks, or whether or not it can harm users. Malware scanning happens primarily after apps are uploaded, and though Google has recently taken steps to safeguard users with its Play Protect program, you don't have to depend on them.

After numerous scandals like the Equifax data breach and the 2016 US election, cybersecurity has become a significant issue for Americans. Unfortunately, anytime we use our devices, we're open to a cyber attack — especially when we browse the web. However, there are ways that we can make it harder for hackers and data miners.

In my previous article, I discussed installing and configuring OpenVAS on Kali Linux. Now it's time to start using OpenVAS with the Greenbone Security Assistant to audit networks for security issues. This can be extremely helpful when you are looking for vulnerabilities or misconfigurations in a large number of hosts.

When you first set up an iPhone, you'll be prompted to create a six-digit passcode to unlock your screen and access certain system settings. If you skip this step, you can always go back and create one, which we highly recommend. Without a passcode, everything on your iPhone is accessible by anyone who gets their hands on it — nosey friends, hackers, thieves, local law enforcement, the FBI — and you don't want that, do you?

Incredibly tiny in size, splinters can be frustratingly difficult to remove from your skin. If large and not completely embedded, a splinter can usually be extracted using tweezers, tape, or glue, but if it's small and in there pretty good, you'll have to get more creative.

This video talks about how one can make a doraemon character with the help of playdoh. This tutorial is for all the ones who loves Doraemon and playdoh.

I don't know anyone that likes going to the dentist—few things are more uncomfortable than having someone else's hands in your mouth. But outside of that, not only can the pain of certain procedures be unnerving, the drugs used to numb those pains can be just as uncomfortable. Not being able to feel your mouth for hours on end is a disconcerting feeling. But all that could soon be a thing of the past, thanks to virtual reality.
This video will show you how to protect others from accessing saved password on Google Chrome. Saving account passwords in browsers are useful for time saving as well as threatening for malicious activity. This is dangerous for security. So you must protect your accounts detail from others to secure your browsing. Watch the video and follow all the steps carefully.
This video will guide you how to blur faces in YouTube video. Many times it’s needed to blur the faces of people in videos. In many sensitive cases faces are blur due to security or confidentiality reasons.

You know that guy who does the cheesy card trick to get the attention of all the girls at the party? Well, we kinda hate that guy don't we? But, if we could be that guy, it might not be so bad.

Video: . Video: .

This how to demonstrates how to use your Apple iphone as a spy camera to spy on others. If you're suspicious, paranoid or just downright creepy, this video can show you how to convert your Apple smart phone into a device for surveillance on others.
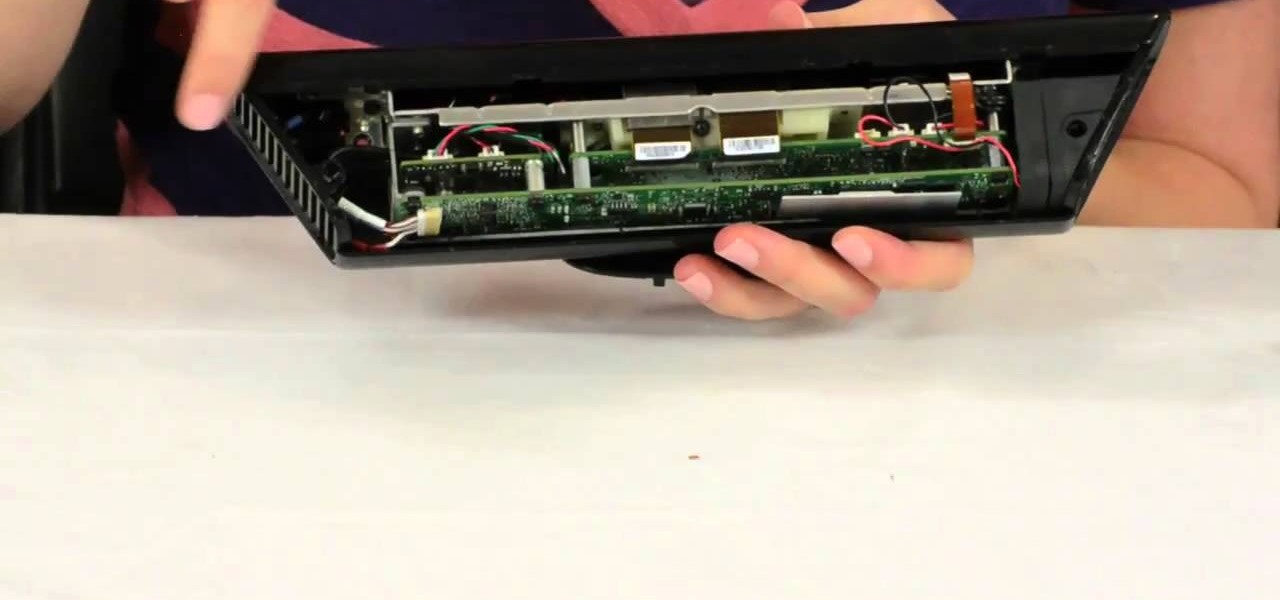
Microsoft's Kinect is gaining popularity with Xbox 360 owners, but what's really more fun? Playing games with this revolutionary hands-free gaming device or gutting the sucker to see what it's all about? We'll take the latter choice.
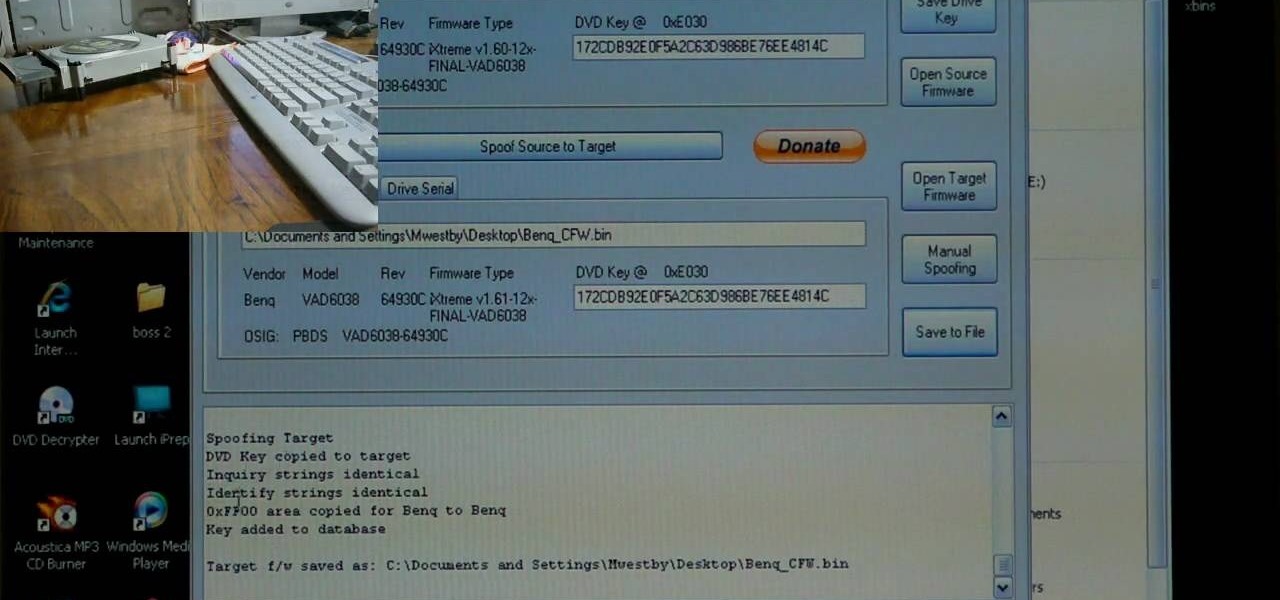
If you've already flashed your XBox 360's disc drive, then congratulations, you've accomplished the most challenging step involved in hacking you XBox. You aren't done though. As Microsoft keeps updating it's firmware to try and fend off hackers, you must keep updating your custom firmware to thwart their efforts. This video will show you how to upgrade your flashed BenQ XBox 360 disc drive's firmware to IXtreme 1.61 using Jungle Flasher 1.61. NOw you can play your burned games with a greater...