Identity theft typically occurs when someone uses your personal information such as social security numbers, credit card numbers or account information to perform various misdeeds, and you are left to clean up the mess.
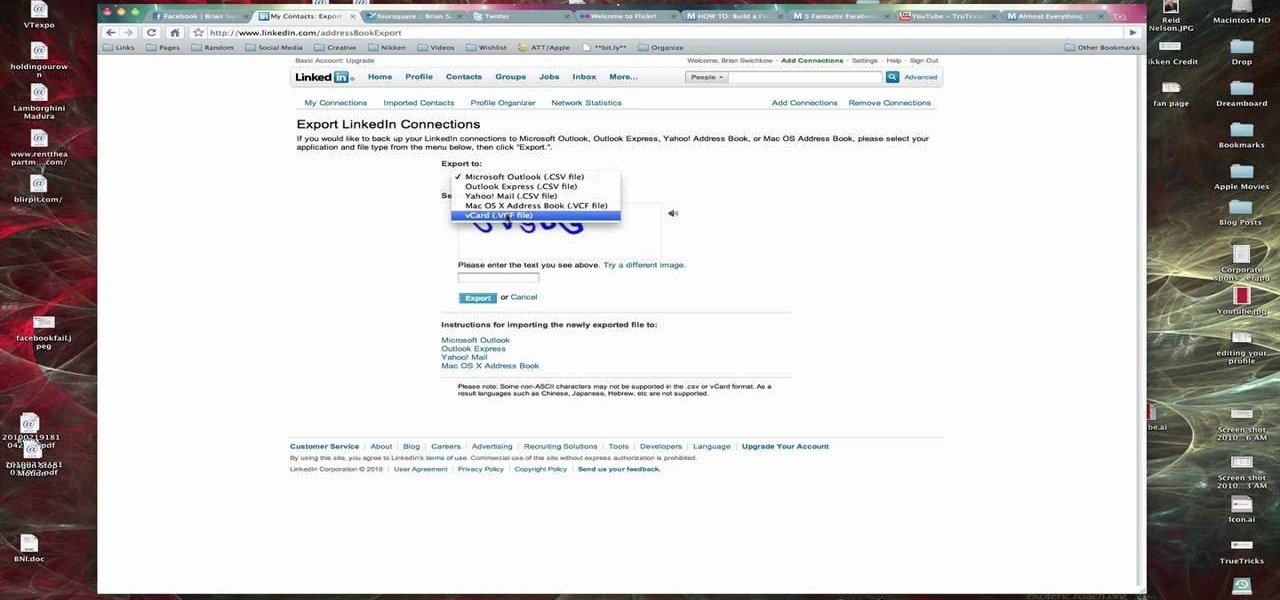
In this Computers & Programming video tutorial you are going to learn how to export LinkedIn contacts to an address book. LinkedIn is great for keeping your contacts in your professional network. To export your contacts go to home page and click on ‘contacts’. Now your full network of contacts will be displayed. On the right hand bottom, click on ‘export contacts’. On the next page select where you want to export the contacts, type in the security code and hit ‘export’ and all the contacts wi...

Installing a peephole in your home's front door can give you and your family a sense of security knowing who comes to your door before they enter. In this video Barbara K will show us exactly how to install a peephole on your door.
When you need a website to showcase your product or service, it can be quite confusing. Follow these easy steps to gather everything you need to have a successful website. Start your search for a domain name in the domain name registrar. (Example: www.companyname.com) Rent space from a hosting company to hold the files for your website. Set up an email account for your company. Create the content for your website (example: products, prices, services, etc). Get internet security to protect sen...

Identity theft is a huge problem and one of he fastest growing crimes in America. A number of credit card companies now issue credit cards with embedded RFIDs (radio frequency ID tags), with promises of enhanced security and speedy transactions.
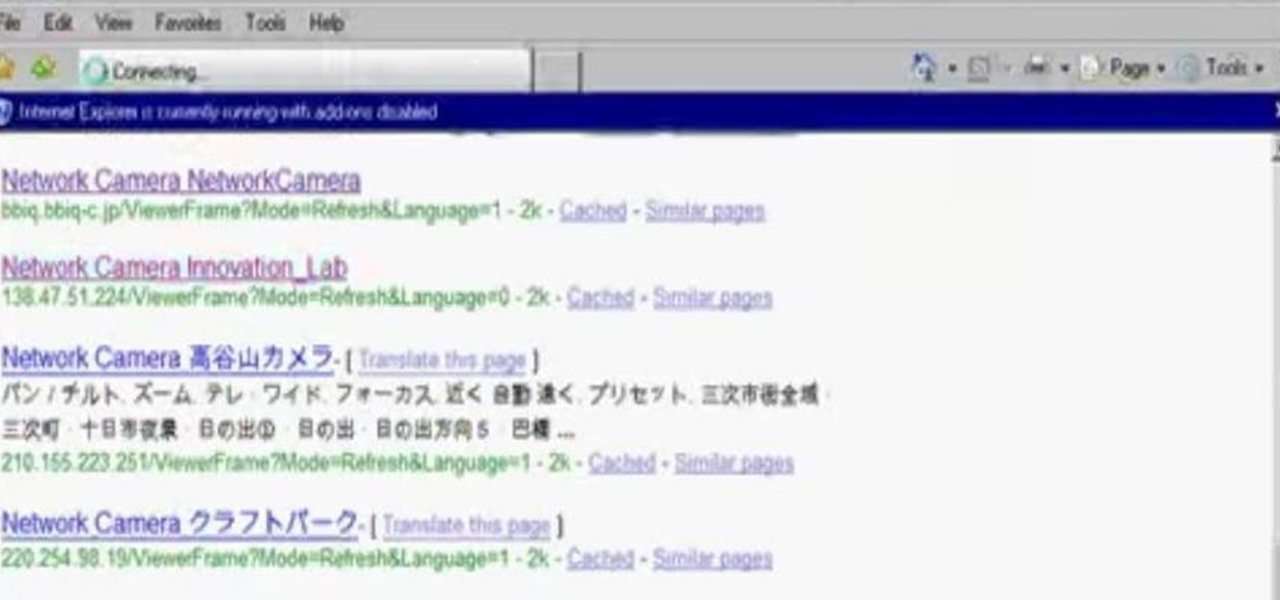
Learn how to hack Google with this amazing video. This video will teach you how to hack Google by using advanced search operators and esoteric search terms to find “hidden” files and mp3s quickly and easily; you'll also learn how to use Google to hack unprotected Internet-controlled devices like webcams and security cameras. For more information on Google hacking, and how to get started using these hacks yourself, take a look at this instructional video!

Commemorate the worst president in history by drawing his face to a lifelike representation and then having a dart throwing contest with your homeboys at the bar! This drawing tutorial, which teaches you how to sketch the face of George W. Bush, or W, is an excellent way to hone your targeting and aiming skills.

Not sure how to enable javascript on your computer? Follow these steps to enable all the functionality javascript provides.

Thanks to the Freedom of Information and Privacy acts, we’re all entitled to see what the FBI has on us. Learn how to get your hands on your FBI file.

Apple just released iOS 14.4.1 for iPhone today, Monday, Mar. 8. The event marks 41 days since Apple released a public update for iPhones, with iOS 14.4 back on Jan. 26.

With everything the last year has thrown at us, the odds are good that you've had to start working from home, complete with all-new challenges both for you and the technology you use.

In a previous guide, I demonstrated how to extract images from a security camera over Wi-Fi using Wireshark, provided you know the password. If you don't know the password, you can always get physical with the Hak5 Plunder Bug. Using this small LAN tap, we can intercept traffic like images from a Wi-Fi or IP security camera if we can get physical access to the Ethernet cable carrying the data.

It's common for IoT devices like Wi-Fi security cameras to host a website for controlling or configuring the camera that uses HTTP instead of the more secure HTTPS. This means anyone with the network password can see traffic to and from the camera, allowing a hacker to intercept security camera footage if anyone is watching the camera's HTTP viewing page.

Unless you're completely new to Instagram, it's likely that you've linked your account with a third-party service at some point and forgotten about it. Those services still have access to data such as your media and profile information, so it's important that you not only know how to find these "authorized" apps, but that you know how to revoke their permissions.

After about 40 days of beta testing, Apple pushed out iOS 11.4.1 to everyone as a stable build on Monday, July 9, exactly one week after the final beta appeared.

There's always an iPhone in our list of top phones for privacy and security, due in large part to advanced security measures like Face ID, consistent iOS updates, and easy ways to prevent unwanted access and excessive data sharing. However, some of those options actually do the opposite and hinder security. It all depends on how you use your iPhone, but you should at least know everything available.

The microphone in a Windows computer is accessible to most applications running on the device at all times and completely without security limitations. Information gathered from recorded audio conversations taking place in the surrounding area of a compromised computer can be used for social engineering, blackmail, or any number of other reasons.

After recently being in the news for collecting PII (personally identifiable information) for analytics and after-sales support, OnePlus has another security problem. An individual going by the name Elliot Alderson discovered an app in OnePlus devices that can enable root access with one command.

Code execution in Microsoft Word is easier than ever, thanks to recent research done by Etienne Stalmans and Saif El-Sherei. Executing code in MS Word can be complicated, in some cases requiring the use of Macros or memory corruption. Fortunately, Microsoft has a built in a feature that we can abuse to have the same effect. The best part, it does so without raising any User Account Control security warnings. Let's look at how it's done.

The iPhone X has a new unlocking mechanism called Face ID, which replaces the old Touch ID system since the phone no longer has a fingerprint sensor. The way it works is simple — you just look at the phone, it recognizes your face, then the system unlocks — so Apple deserves the praise they're getting for it. But did you know you can get almost this exact same feature on any Android device right now?

Last month, it was revealed that Juniper Networks' routers/firewalls were hacked. It was reported that a backdoor was implanted in the operating system of their routers/firewalls and that attackers could listen in on all encrypted communication. There are now fears that all confidential communications by U.S. government agencies and officials could have been compromised over the last three years.

With a root bounty of over $18,000 up for the taking, developers were highly motivated to get the AT&T and Verizon Wireless variants of the Samsung Galaxy S5 rooted. Legendary hacker George Hotz, aka Geohot, has won the race and can now step up to claim his prize.

You've unlocked your bootloader and rooted your HTC One running KitKat, but there's still one lingering aspect of security you've yet to rid yourself of—S-On—the extra security measure HTC implemented into Sense.

Kip "Kipkay" Kedersha is known for his intriguing and clever how-to and prank videos, even when he teams up with MAKE Magazine. He will show you how to tweak, hack, mod, and bend any technology to your hacking needs. No electronic device, gadget, or household item can stand the test of Kipkay's hacks and mods.

WPA-secured wireless networks, or WiFI Protected Access, is a form of internet security that secures your wireless LAN from being accessed by unauthorized users. Safer than WEP, or wireless equivalent privacy, WPA still has weaknesses that are prone to cracking - IF, that is, you know what you're doing.

In this tutorial, we learn how to make a bear pop-up card. First, draw a big bear face on a 4x6 card. After this, fold the card in half so the face is in half. From here, use scissors to cut along the mouth line up until you reach the nose. After this, bend that flap up and down so it's creased and will flip both ways easily. After this, open the card back up and push the nose of the bear into the top. Then, close the card again and the nose will pop up from the page, enjoy!

In this tutorial, we learn how to draw Naruto & Hinata. First, draw the outline of the head and then draw the hair and bangs on the top of the head. After this, draw in the eyebrows, eyes, nose, and mouth. After this, draw in the neck and then the rest of the body. Draw in lines to show the folds for the clothing and then draw the body of the other character around this one. Draw Hinata in the same way as you drew Naruto, just make sure to make their faces and hair different. When done, you w...

In this tutorial, we learn how to draw Demon Realm Pain. To start, you will draw the outline of the character with a pencil. Draw the headband on him first, then draw the eyes, nose, and mouth. After this, draw on the top of the head using a half circle, then draw on the horns on top of the hat. After this, draw on freckles to the character's face and then shade in around the different areas. After this, you will start to draw in additional details around the face and shade in where needed to...

In this video, we learn how to do a quick draw of Sonic the Hedgehog. First, use your pen to draw the nose and the mouth. After this, draw in the eyes and the eyebrows above them. From here, draw in the spiky hair on top of the head, using big spikes. Draw in the ears in the hair and then draw in lines to create more details. Next, draw in the arm and the hand, with a glove on the hand. After this, draw in the details of the clothes, drawing in folds on them. From here, draw in the legs and t...

In this tutorial, we learn how to draw a face using charcoal. Start out using a light touch with your pencil to draw the outline of the pencil. After this, use the darker touch of a charcoal brush to draw in the details of the eyes. Draw the eyeline and the creases in the eye, then draw in the nostrils and the middle of the mouth. Draw in shading around the neck and chin to make a difference between the two. Use a light touch of the brush to create shading throughout the entire face, not usin...

In this tutorial, we learn how to draw the face of an anime young man. Start out by using a pencil on a white piece of paper, drawing spiky hair at the top of the page. After this, draw in additional lines to create more hair around the face, then draw in the sides and the bottom of the face. Next, draw in the features of the face, including the eyes, nose, ears, and mouth. Then, start to draw the clothing and add shading in on the clothing and the top of the hair. Add in more lines to make i...

In this tutorial, we learn how to draw a dragon in profile. Start with a pencil on a white piece of paper and draw out the outline of the profile for the dragon. After this, start to add in the details for the side of the face, this includes the horns, teeth, nostrils, and scales for the dragon. Work your way into the middle of the dragon, drawing in different details, including the eyes and the mouth. Continue to shade and add different lines to the dragon, then finish it off with a horn or ...

Vault Boy has been around for a long time now, and appeared in the few but proud Fallout games as their mascot and skill-demonstrator. Pay homage to this plucky little guy by creating an XBox 360 Avatar in his likeness using the materials below and following the steps in the video. He looks a little skinny to me, but you can change it if you want right?

Sarah teaches us how to do a Dias de las Muerto look for Halloween in this tutorial. First, apply a pure white makeup to the entire face, including the lips. After this, wipe makeup off from around the eyes and draw a circle around them, including the top of the eyebrows down to the top of the cheeks. Next, apply a black flower like shape over the circles you just created. After this, apply a dark green paint to the inside of the eyes, covering everything in them. Next, apply dots at the top ...

If you've ever stuffed a caramel apple into your mouth around Halloween then you know just how delicious the combination of apples and caramel sauce is. The caramel offers a melting, sweet complement to the tart and crisp apple.

In this tutorial, we learn how to draw Goofy. First, draw the nose and then draw in the face. After this, start to extend the face down with the neck and a collar. After this, draw the back of Pluto and then his four legs like he's walking. Next, draw a darker line over the picture, then draw a tongue hanging out of the mouth and eyes and ears. Make sure to draw the tail, then start to color the picture with Pluto's signature colors. Add in any additional details, then save your picture onto ...

In this video, we learn how to draw Neji Hyuga from the Naruto series. Start by drawing the outline of the helmet, then add in a swirl that is on the front of it. After this, draw in the eyebrows and then draw in the eyes as well. Draw in the pupils and lines around the eyes. next, draw in the nose and draw in the mouth as well. Next, you will draw in the shirt and neck for the upper body of the character. To finish the drawing, you will draw in hair on the helmet and down through the face!

If everyone in the world properly secured their email account there would be no spam. But yeah… never going to happen. That's more of a reason to encrypt and digitally sign our emails, but isn't using p2p security really expensive and really hard? Nope. It's actually free and easy with GnuPG. It's demonstrated on Mac OS X, but it's just as easy with Windows.

In this tutorial, we learn how to draw a cartoon figure of a boy. Start out by drawing a large circle for the head, then drawing the arms underneath and a circular body. next, draw the hair onto the boy, and add shoes, a shirt, and pants. Now, color the hair yellow, the body skin color, the shirt green, and the pants blue. Outline the drawing with black ink, then add on the facial features. Start with two circular eyes, a nose, and a small mouth that is a curved line. Add in more hair to the ...

In this tutorial, we learn how to draw a cute and blue cartoon bird. First start out by drawing a circle for the head, an oval for the body, and then an oval wing in between the both of them. After this, trace over the lines to make squiggle marks on the wings and on the rear end of the bird. Add on an eye and pupil to the head, then draw a beak with an open mouth, making it a "v" shape in the middle. Then, color the entire bird blue, leaving the beak orange and the eye outlined in black. To ...