When it comes to the sub-$250 price range, the new Nokia 5.1 might be the perfect phone. Of all the new models announced at Nokia's event in Moscow, the Nokia 5.1 offers the most with the least compromises. For a third of the cost of a flagship, you get a phone with a premium build, solid specs, and good battery life.
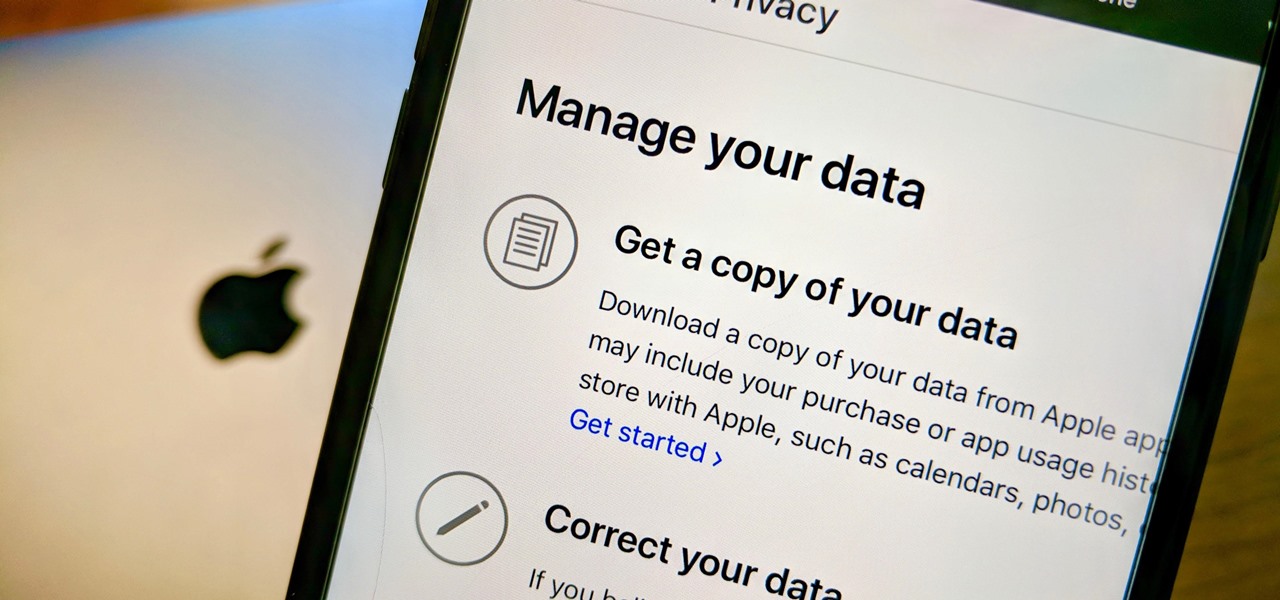
Personal data is a hot topic right now, and for good reason. Never before has the public been so on edge about how companies use their information. Services like Facebook and Google now allow you to download all of the data each has on file. Soon, you'll be able to see exactly the same for Apple as well.
HBO is only a couple of episodes into the second season of Westworld, the television version of the classic science fiction movie about a robot resort gone awry, and the fan theories about the show are already reaching Season 1 levels of weirdness.

With the Masters, one of professional golfing's four most prestigious annual tournaments, now in full swing, Snapchat is giving users the ability to commemorate the moment in augmented reality.

OnePlus has now officially upgraded both the 5 and 5T to Android 8.1 Oreo. As implied by the version number, this isn't a huge update from Android 8.0 Oreo. However, OnePlus has included a few of their own features as well.

With Nokia's relaunch, the iconic company attempted to reimagine the budget phone market. The series of phones they introduced last year challenged the idea that good phones can't be cheap. This year, Nokia introduced the Nokia 7 Plus, a phone which offers perhaps the best balance of specs, software, and price.

Chances are, you just point, shoot, and share photos and videos on your iPhone without a second thought about how your privacy is affected. It's fairly easy to do so since the Camera and Photos apps that Apple provides seem so innocent. But there are a few things you need to know when it comes to shooting media, sharing it, and even deleting it.

Facebook may have shamelessly copied Snapchat and its camera effects for faces (as well as its World Lenses), but it might beat its social media competitor to virtual body augmentation.

Nmap is possibly the most widely used security scanner of its kind, in part because of its appearances in films such as The Matrix Reloaded and Live Free or Die Hard. Still, most of Nmap's best features are under-appreciated by hackers and pentesters, one of which will improve one's abilities to quickly identify exploits and vulnerabilities when scanning servers.

Augmented reality developers are rapidly bringing science fiction tropes into the real world, with the latest example leveraging the TrueDepth camera on the iPhone X to emulate the cloaking technology made famous by movies like Predator and Marvel's The Avengers.

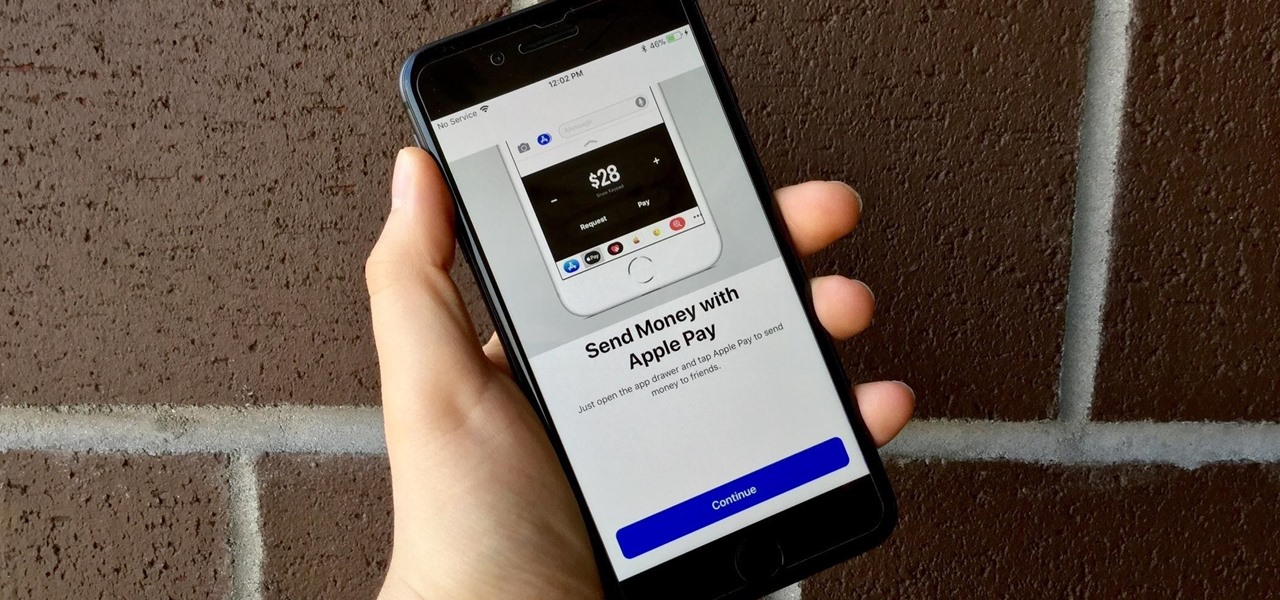
Move over Venmo, Apple Pay Cash is here, and it's built right into iMessage. If you're like us, you've been eagerly waiting to give this new feature a try on your iPhone ever since Apple announced it during WWDC 2017 back in June. While it was never released in the main iOS 11 update, it finally showed up in iOS 11.2.

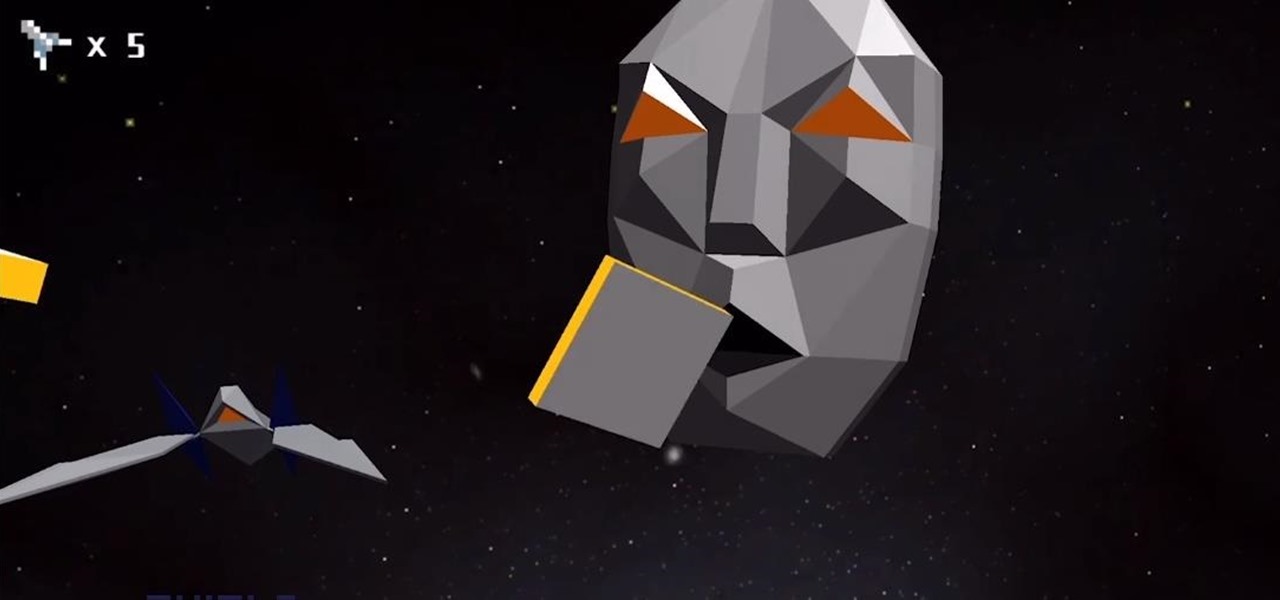
An AR/VR developer has managed to use the iPhone X to transport players into an emulation of the classic '90s video game Star Fox as the game's antagonist.

While it's easy enough to ask websites not to track your browsing activity in Safari, they do not have to honor your request. Plus, some of the third-party content providers that websites use can actually invasively track you across other websites. Thankfully, iOS 11 includes a way to minimize companies from tracking you across the web on your iPhone.

Who knew the HomePod would stir up so much excitement? Apple's soon-to-be home speaker is an intriguing product, if not a "must-have." I know I'm excited to compare it to the other big-name Bluetooth speakers out there to see if Apple is putting their money where their mouth is. But there's more important news to discuss — the HomePod's firmware has revealed some pretty big secrets about Apple's highly anticipated phone, most notably its bezel-less design, and facial recognition technology.

A vulnerability in the design of LiDAR components in driverless cars is far worse than anything we've seen yet outside of the CAN bus sphere — with a potentially deadly consequence if exploited.

The Raspberry Pi loads an operating system from whatever SD card you insert, allowing you to keep different operating systems on separate SD cards depending on which OS you wish to run. A tool called BerryBoot cuts down on the number of SD cards needed by providing the ability to boot multiple operating systems from a single SD card, similar to Boot Camp for Mac computers.

The race for the future of the automative world has never been tighter, with reports earlier this week that Tesla is now almost as valuable as Ford. The neck-in-neck companies are focused on the same next big step for automobiles: the driverless car.

Princess Cruises' Coral Princess voyage disembarked in Fort Lauderdale on Saturday, March 18, after a 10-day cruise in which 182 people were sickened with symptoms of vomiting and diarrhea. According to federal health officials, a norovirus is suspected for the outbreak.

According to the National Safety Federation (NSF), pet bowls and toys carry coliform bacteria, including Staph bacteria, yeast, and mold. Additionally, an (unscientific) survey from Petco found that almost one-third of pet owners do not know the extent of contamination that their pet toys contain.

Phuket, the island in Thailand typically associated with paradise and most recently, illegally-run hotels, now has a different problem—a stray cat with the claws of death.

It seems like a new, dangerous Android exploit is uncovered every month or two. The latest headliners are NightMonkey and Chronos from the list of CIA hacks reported by Wikileaks, which have been billed as gaping security holes in the world's biggest mobile operating system.

This is the very first article in my series on setting up a Mac for hacking. In this series, I will be operating under the assumption that you have a clean install of macOS (previously OS X). If you aren't starting with a clean installation, there may be a few differences, but nothing we can't help you out with.

Considering how much smartphones cost in the first place, we're understandably reluctant to throw them out when we've bought a newer model. And this is probably the best practice, too, as there are many great uses for an old Android device.

When it comes to security, Android generally takes an all-or-nothing approach—once someone has your PIN, they're free to do just about anything, up to and including wiping your device. This is why you have to be extra careful to ensure that neither strangers nor friends are looking over your shoulder while you're entering your PIN.

Welcome back, my novice hackers! As many of you know, recon is crucial to a successful hack/pentest. In most cases, hackers spend more time doing good reconnaissance than actually hacking. Without proper recon, you are simply guessing at what type of approach or exploit is going to work and, as a result, your time is wasted without any useful outcomes.

Welcome back, my tenderfoot hackers! One key area on the minds of all hackers is how to evade security devices such as an intrusion detection system (IDS) or antivirus (AV) software. This is not an issue if you create your own zero-day exploit, or capture someone else's zero-day. However, if you are using someone else's exploit or payload, such as one from Metasploit or Exploit-DB, the security devices are likely to detect it and spoil all your fun.

Welcome back, my tenderfoot hackers! Web apps are often the best vector to an organization's server/database, an entry point to their entire internal network. By definition, the web app is designed to take an input from the user and send that input back to the server or database. In this way, the attacker can send their malicious input back to the servers and network if the web app is not properly secured.

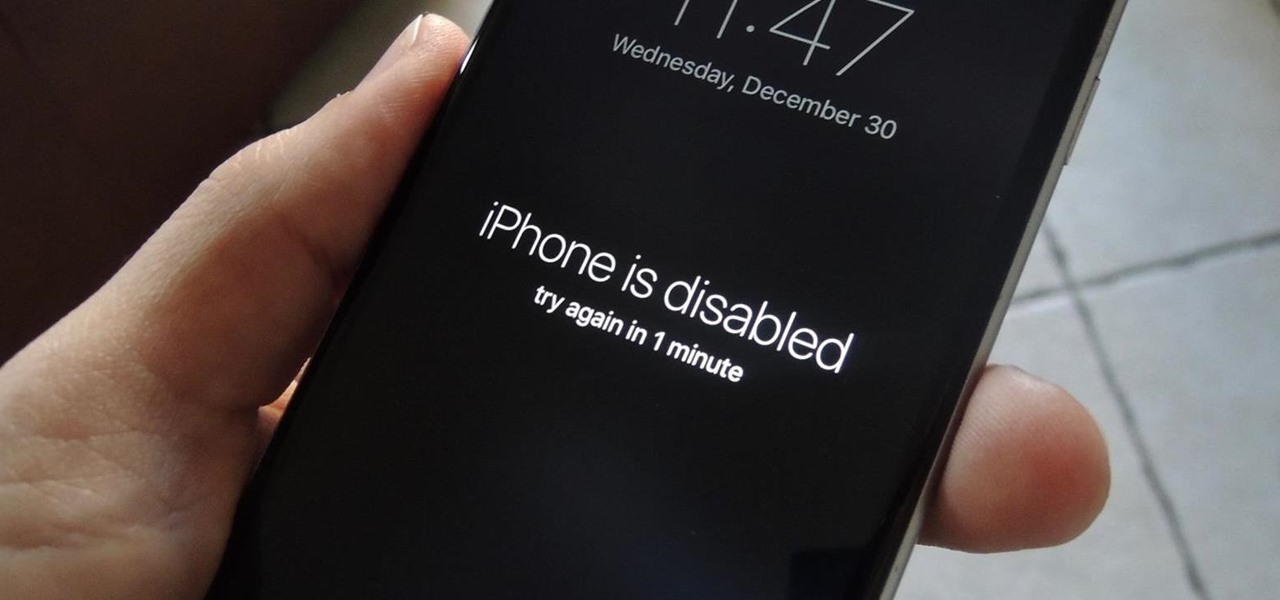
With Touch ID on iOS devices, it's a little more difficult to lock yourself out. However, it can still happen if you don't use it, have a busted fingerprint scanner, or use an older device that doesn't have Touch ID, which means you're passcode dependent (unless you have zero lock screen security).

Hey there, reader! In this tutorial we are going to explain how values are stored in variables as either signed or unsigned. Try to not get lost!

INTRODUCTION Hello dear null_byters here we go again with our third part of this serie.

If you don't have the time or patience to build a complete Ant-Man suit from scratch, there's another way to make a Ant-Man costume for Halloween. If you're more skilled with brushes and makeup rather than drills and cardboard, this is the Halloween DIY for you—especially if you're a fan of the Marvel universe.
I see many people posting the same thing on the internet. "How do I become a hacker? Where do I commence?"

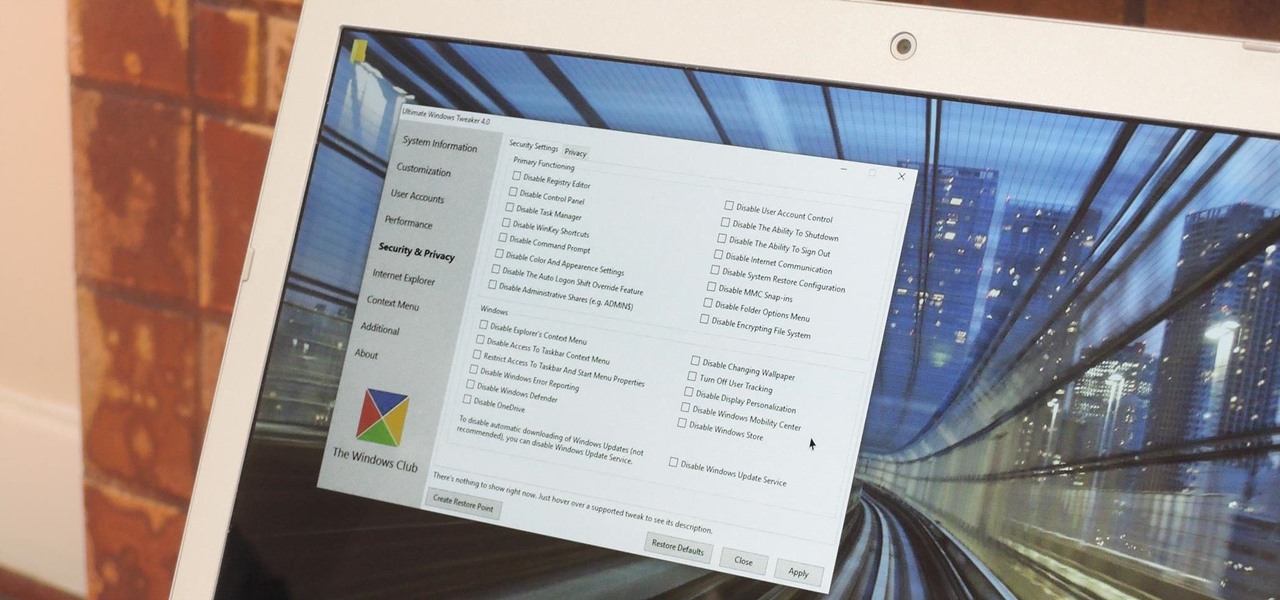
Every time Windows gets a significant update, the vast majority of existing tweaking utilities become obsolete. For every option that you fine-tuned with one of these tools on Windows 7 or 8, there's a change in the registry or system settings that cause your tweaks to now point to a dead end. This was definitely the case with Windows 10, since there were so many sweeping changes that very few existing options carried over.

When it comes to security, there are usually only a handful of things that you want protected from prying eyes on your iPhone—private photos, scandalous videos, and important text, such as credit card and social security numbers.

Hi all, Pro Hackers/Crackers, Let's see how we can use batch for our own Protection instead of exploiting someone with it.

As many of you know, I firmly believe that hacking is THE skill of the future. Although the term "hacking" often conjures up the image of a pimple-faced script kiddie in their mother's basement transfixed by a computer screen, the modern image of the hacker in 2015 is that of a professional in a modern, well-lit office, hacking and attempting to development exploits for national security purposes. As the world becomes more and more digitally-dependent and controlled, those that can find their...

While you may not have loads of secret files hiding on your computer, there might be one or two items that need a little extra security, like a file of website logins or a folder of risqué photos.

Welcome back, my hacker novitiates! Eluding and evading antivirus software and intrusion detection systems is one of the most critical tasks of the hacker. As soon as a new exploit is developed and discovered, the AV and IDS developers build a signature for the attack, which is then likely to be detected and prevented.

Welcome back, my tenderfoot hackers! Those of you who have been reading my posts here for awhile know how much I emphasize good reconnaissance. Novice hackers often jump into a hack/exploit without doing proper recon and either fail or get caught. Experienced and expert hackers know that 70-80 percent of a good and successful hack is dependent upon successful and accurate reconnaissance.

Welcome back, my novice hackers! New hackers often ask me the same question: "What is the easiest platform to hack?" My response is always the same—it is not a platform, but rather a particular piece of software that is easiest to hack, which is on nearly every client-side system. That software is Adobe Flash Player.