The Cloud Security Alliance (CSA), a leading IT trade association, has published its first report on risks and recommendations for connected-vehicle security, ahead of when driverless cars are about to see volume production in the near future.

Google released its "Android Security: 2016 Year in Review" report last month, and to no one's surprise, included its own flagship phones. However, one surprise on the list was the BlackBerry PRIV, which Google named one of the best Android devices for privacy.

A human rights activist from the United Arab Emirates recently stumbled upon three gaping security loopholes in iOS that work by enticing you to tap a link sent to your iPhone. Ahmed Mansoor received a text message from an unknown number roughly two weeks ago, but instead of following the link it included, he sent the message over to a security researcher at Citizen Lab.

With all of the personal data that's stored on our smartphones, it's of vital importance that we have some sort of lock screen security enabled. One of the Galaxy S5's killer features is obviously the fingerprint scanner. It makes the process of dealing with a secure lock screen a bit easier than typing in a password or PIN.

We haven't met - or rather, our tongues haven't met yet - a French onion soup that we haven't liked. Just thinking about this oily soup dish makes our mouth water: Creamy cheese floating on top, delicious, drenched kernels of onions, and of course the rich amber-hued soup.
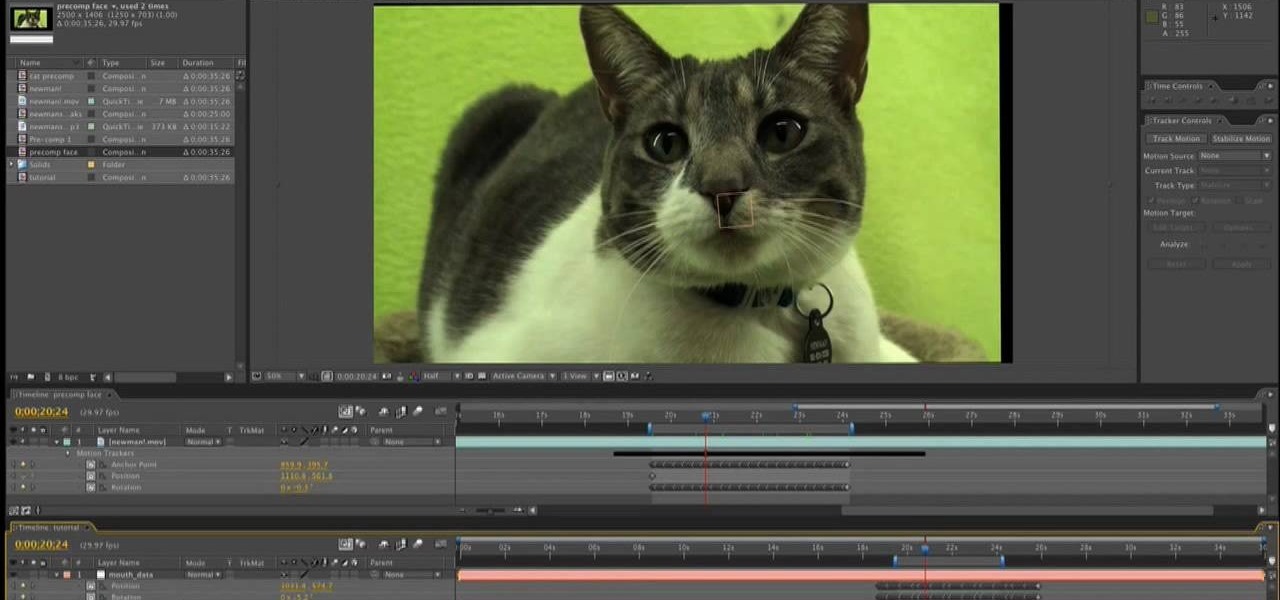
A LOT of movies have featured talking animals. Especially now that the technology is readily available to even low-budget filmmakers to make animals appear to be talking very realistically. If you've wanted to make your own talking-animal film, this video is here to help. It wills show you how to make animals talk using After Effects, creating and syncing mouth movements to fit your sound and leaving you with one charismatic cat, dog, fish, or marmoset.

Twitter is a very powerful way to create word-of-mouth buzz for your website if you can utilize it properly. One way to do that is creating a Tweet This link on your website, which allows your users to tweet about how awesome your website is without going back to Twitter. This video will show you how to create a Tweet This link and put it on your website using Dreamweaver CS4.

This may/will take some practice to do but the risk makes the glory. You simply put a match in your mouth and inhale. Yes, that simple...or so you think.

Everyone should know how to perform basic first aid, especially for choking victims. This video will help deaf people and those with hearing impairment learn how to deal with choking, using sign language. Choking is serious life-threatening problem that need immediate attention. It could result in such problems as hypoxia or even death.

You will be shown how to use rice water to nourish and fortify your skin. You will be using just the rice water.

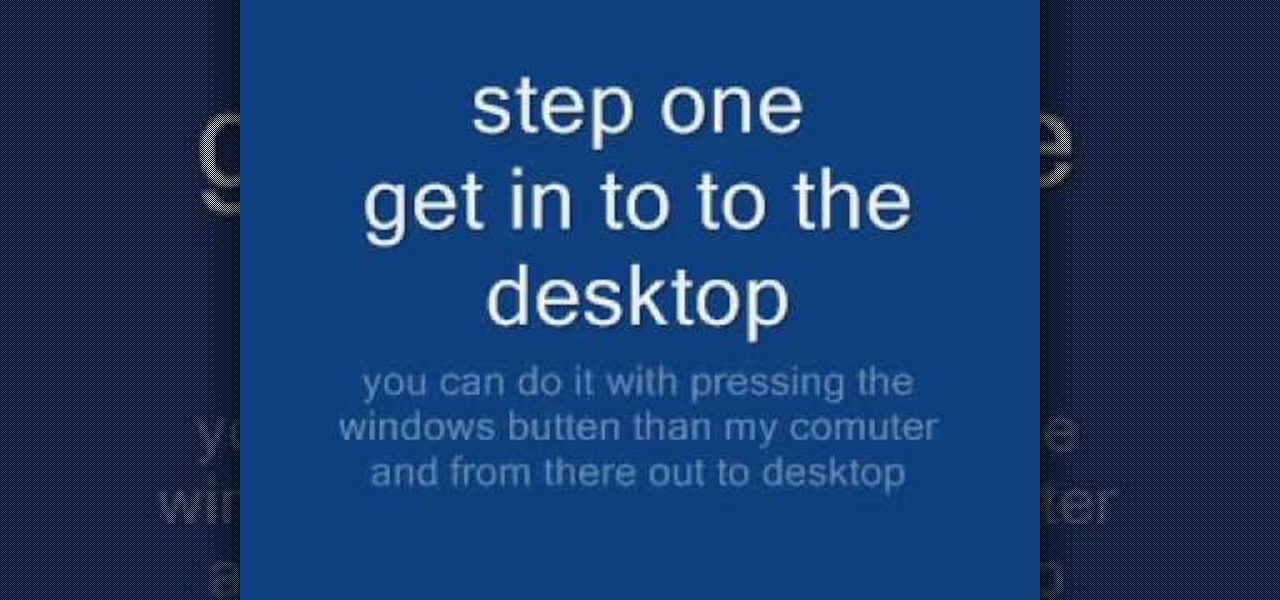
In this video, we learn how to remove Security Tool the simple way. Most ways will not remove this from your computer, but this way will. To start, you will need to restart your computer. After this, press ctrl+alt+del the moment Windows shows up. Then, go to the Task Manager and look through the programs that are open. When your security tool opens, press the same buttons to get the mouse free. Then close the security tool from the Task Manager. Now, go to your desktop and press on the icon ...

When it comes to your security, you want the best of the best. Why settle for mediocre service with something as valuable as your protection? Malware continues to make its way onto the Play Store, leaving millions of devices vulnerable. You need an app that will shield your devices from both the latest malware threats and threats nearby. And when it comes to antivirus apps, there is only one choice.

In an article published in early-2015 by Peninsula Press, it was reported that the demand and the salaries for cyber security professionals are exploding! They cite that 209,000 cyber security jobs were unfilled last year, and that job postings have increased over 74% in the last 5 years. Job opening are expected to grow by another 53% over the next 3 years. You are definitely in the right field, my tenderfoot hackers! Some researchers are expecting information security jobs to continue to gr...

While we now know that iCloud was not exploited by hackers to steal private celebrity photos, Apple did admit that guessed (aka brute-forced) passwords and/or iCloud security questions were to blame for the breach.

In order to draw a meerkat, you will need the following: a pen, an eraser, and a pencil.

Halloween is the holiday of goblins, ghouls and witchcraft, and also death. So, what better way to celebrate the spooky season than with a skeleton drawing? More specifically, a human skull? Merrill K has you covered with this drawing tutorial. He'll show you the trick to sketching out a human skull (frontal view) in step-by-step instructions. Make sure to pause the video after each step and look at the screen every few seconds while you are drawing.

There's nothing more tedious, yet exciting, than watching surveillance cameras at work. They prey on the innocent and the unknowing. They protect businesses, workplaces, and homes. They catch criminals in the act, find hilarious anomalies, and are just darn cool when you're not the one that's supposed to be eavesdropping with them.

Watch this tutorial to learn how to draw a screaming angry mouth. Make sure to pause the video after each step and look at the screen every few seconds while you are drawing.

Google recently released a new mesh router known as Nest Wifi. The updated and rebranded Google Wifi brought many improvements, such as faster processing power and an increased level of wireless security called WPA3. But while it's not enabled by default, you can still get the new WPA3 security on your original Google Wifi.

If you've ever received an email from a sketchy address purporting to be Uber, asking you to sign in with your credentials, you might be a phishing target. Hackers use a fake login page from real-looking domains to trick you into giving up your account information, and while it's been an issue in the past, Uber is making it more difficult on cyber thieves with the addition of two-step verification.

Hundreds of Windows 10, macOS, and Linux vulnerabilities are disclosed every single week, many of which elude mainstream attention. Most users aren't even aware that newly found exploits and vulnerabilities exist, nor that CVEs can be located by anyone in just a few clicks from a selection of websites online.

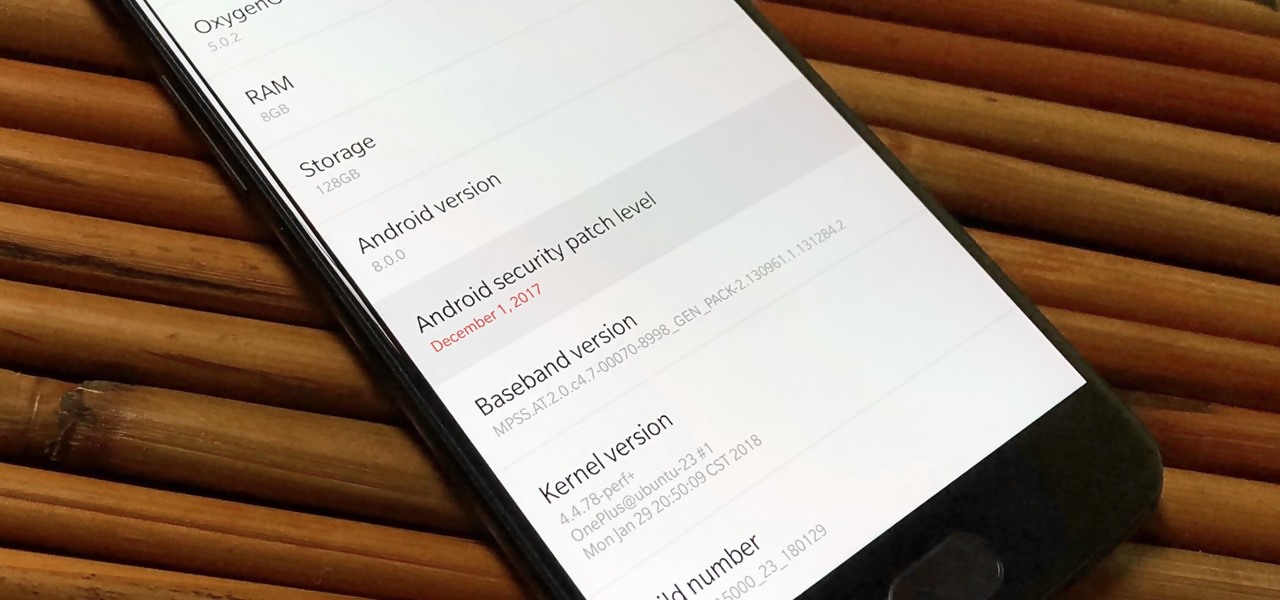
As far as overall security updates are concerned, we all know that iOS reigns supreme over Android. But just how bad do Android devices fare against Apple in general? A recent report will have you second guessing some companies the next time you're in the market for a handset.

You may have seen news reports over the last two days detailing a major security flaw in virtually all smartphones. The devices that are at risk are not limited to either iPhone or Android — all of us are affected. If you want to make sure your smartphone and its data stay secure, there are a few steps you can take.

Many people think antivirus apps are useless — why pay a subscription fee when most malware can be avoided with common sense? But the thing is, there were an estimated 3.5 million malicious Android apps discovered last year, with many of them making their way onto the Play Store. As this number continues to rise, can you truly depend on common sense to protect you?

Samsung's 2016 line of smartphones has a new update, at least for the devices on AT&T. The update brings the Galaxy S7 to version G930AUCS4BQL1 and the Galaxy S7 Edge to version G935AUCS4BQL1. Here's what's on the table.

The Play Store hasn't been the most secure place for apps lately. A quick Google search for "Play Store malware" will give you a taste of some of the malicious apps that snuck their way onto Android's official app store. Google is aware of the problem and they're tying to fix it, but their new Play Protect program doesn't have a great track record, so you might want to look elsewhere.

Kali Linux is the obvious first choice of an operating system for most new hackers, coming bundled with a curated collection of tools organized into easy-to-navigate menus and a live boot option that is very newbie-friendly. But Kali isn't the only distribution targeted at pentesters, and many exciting alternatives may better fit your use-case. We've already covered BlackArch Linux, now it's time to talk about Parrot Security OS.

WhatsApp sneakily made some security changes to iCloud backups without your knowledge, ladies and gents. Not that strengthening security is a bad thing, but still!

Who likes security? I like security. I lock my doors at night, and so should you! That's why it's exciting to me that Samsung has just announced its May security update. It's like getting a brand new, top-of-the-line lock for free, but for your phone.

In previous posts here, I have pointed out that hackers are in high demand around the world and in nearly every industry. Every military and espionage unit of every country is trying to hire high-quality, experienced hackers as fast as they can to hack their adversaries' computer systems in order to gain a strategic advantage and to spy.

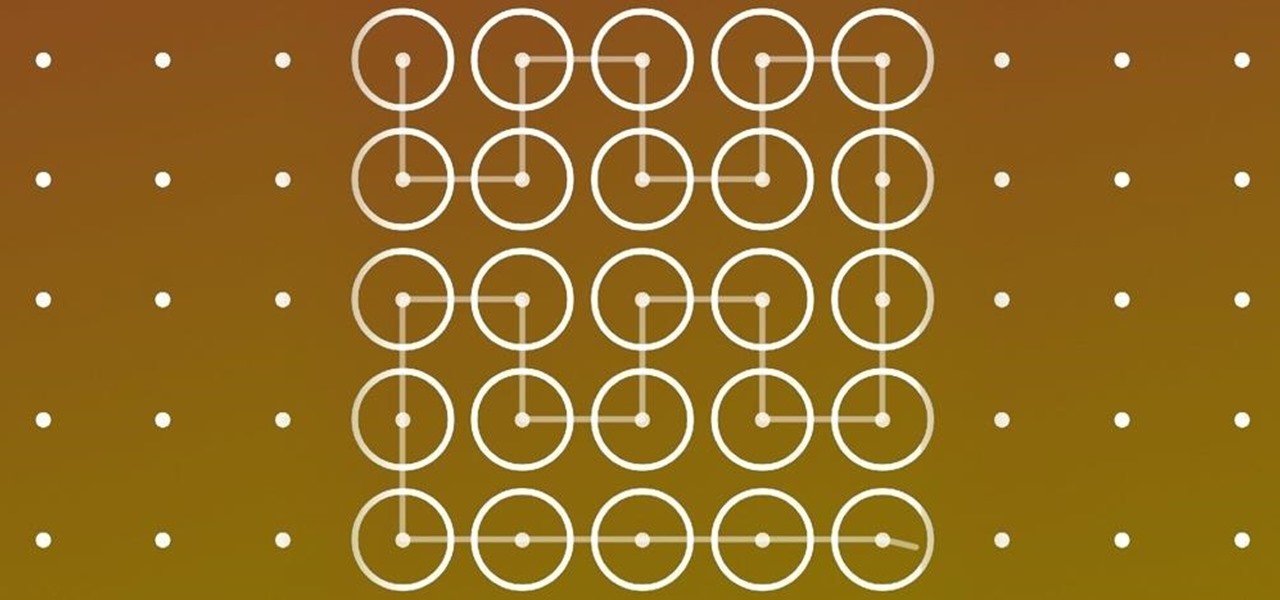
While most of us don't think twice about dragging a pattern or using Touch ID to open our phones, or entering a password in for our email and bank accounts, these features are there to protect some of our most private information. Only problem is, they don't do a good job of it.

These days, our smartphones carry some very sensitive data. From banking app passwords to personal photos, there are many things on your Nexus 5 that you might not want other people to have access to.

Snapchat has had more than its fair share of security failures and mishaps. The photo-sharing company is looking to better address some of these security gaps by adding new features, and today its most recent addition is live: the Captcha. New users will be asked to verify their "humanness" by selecting the infamous Snapchat ghost out of a selection of images. The feature is supposed to help block hacker-made bots from creating fake accounts or accessing existing ones. But rather than using t...

In order to make a tiger mask with makeup for Halloween, you will need the following: moisturizer, white and black liner pencils, black liquid liner, eye shadows, blush, and lipstick.

In this how to video, you will learn how to draw Calumon from Digimon. First, start off with two circles for the head and body. Next, add the ears and oval shapes for the feet. From here, you can trace these shapes to create a more accurate depiction of Calumon. Go into the face and two ovals for the eyes. Draw two ovals inside the ovals for the pupils. Fill it in with black. You can also add a circle at the top of each eye to create a highlight. Next, draw a border in the interior of the ear...

Barbara Wilson of BarbraEllin Cakes demonstrates how to make an edible Teddy Bear out of flour paste icing. You will need some edible glue, spaghetti, a knife tool, a small brush, a sharp craft knife, a mouth tool and a stitch tool.

Not sure how to properly warm up your voice before belting a tune? Learn the right way to warm up your voice so you can surprise friends without setting off the neighborhood dogs.

The most basic and most important aspect of first aid is CPR. It's the one thing that is most likely to save a life. It's stands for cardiopulmonary resuscitation, which is the emergency medical procedure for restoring a person's normal heartbeat and breathing when experiencing heart failure or breathing impairment. But there's a different approach when dealing with and chest massages for babies under one year old.

Choking is serious life-threatening problem that need immediate attention. If waiting too long, it could result in such problems as hypoxia or even death. Being able to respond to a choking victim could save someone's life, and everyone should know this first aid procedure.

Um, okay, the question here is why WOULDN'T you want to decorate a cake shaped like a hamburger? If you've got a guy friend who can't get enough of his Double Doubles at In-n-Out, then this burger-shaped cake is going to knock his socks off.