
How To: Organize your computer desktop
Keeping a computer desktop organized is tough, but clutter can quickly and easily become a thing of the past. Learn how to organize your computer desktop with this how to video.


Keeping a computer desktop organized is tough, but clutter can quickly and easily become a thing of the past. Learn how to organize your computer desktop with this how to video.

This video will show you how to tune your nitro engine on the LSN, HSN, MSN and other methods. Not sure if it is a idle or lean issue? We will help you!

Check out this home repair tutorial video that demonstrates how to fix and diagnose your appliance. These videos are for information purposes only. A qualified and proficient engineer should be employed to replace any faulty parts on your domestic appliance.

Watch this instructional magic card trick tutorial to learn how to perform the binary routine. This is an original series of user-created moves. There are 9 phases of the Binary Routine, 6 of which are false, and the other 3 are closers that involve a color card change at the end. This video provides instruction on 2 false cuts and 1 closer, along with some possible variations. Just keep in mind, there is room for adjustment with these phases. If you find a better way to do a certain move, th...

This dance tutorial teaches you how to do swing dance routines from great classic films. The moves in this tutorial are based on the 1929 film short "After Seben." Footage is of Shorty George Snowden and his partner, sometimes credited as Pauline Morse, at other times identified as Big Bea. The music is by Chick Webb and his orchestra.

Swing dancing dates back to the 1920's, where the African American community, discovered the Charleston and the Lindy Hop, while dancing to contemporary Jazz music. The term "Swing dancing" is used to refer to one or all of the following swing era dances: Lindy Hop, Charleston, Shag, Balboa and Blues and extends to include West Coast Swing, East Coast Swing, Hand Dancing, Jive, Rock and Roll, Modern Jive, and other dances developing in the 1940s and later.
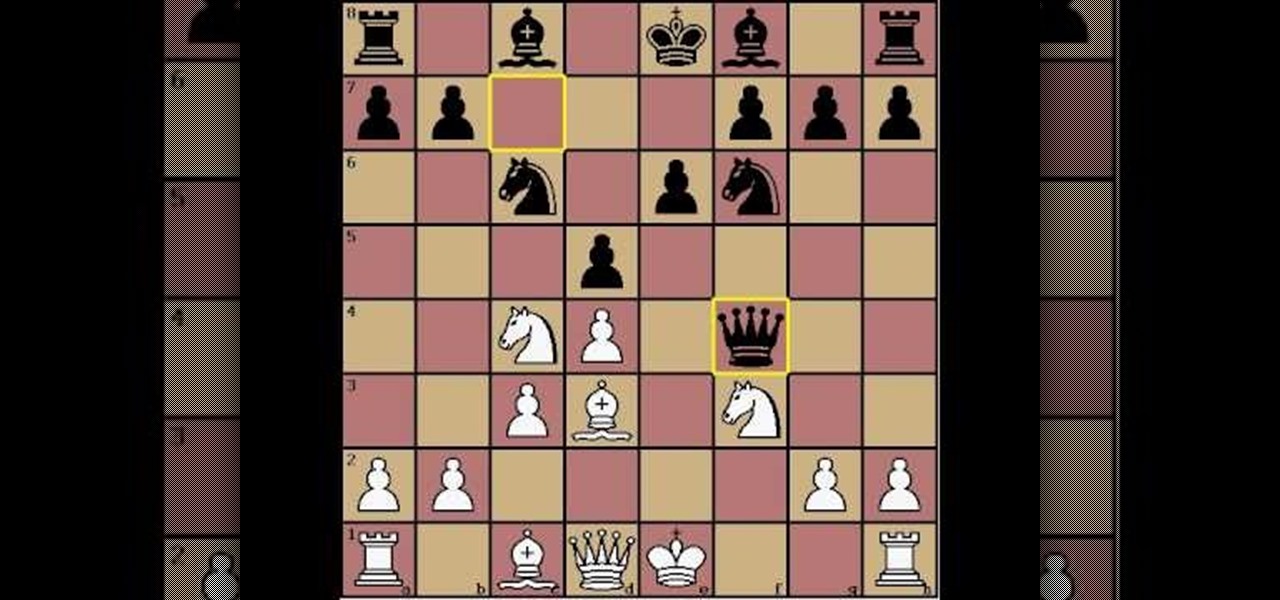
This video features 6...Qc7 in the mainline of the Stonewall, a good move since after the obvious 7.Ngf3, White turns out worse in all lines. Matt suggests an alternate development of pieces including Nh3 and Qf3.

A stager is a small piece of software that's typically used by malware to hide what's happening in the early stages of infection and to download a larger payload later.

Sniffing packets over a network is an easy way for hackers to gather information on a target without needing to do much work. But doing so can be risky if sniffing packets on an untrusted network because a payload within the packets being captured could be executed on your system. To prevent that, Sniffglue sandboxes packet sniffing to provide an extra layer of security.

Navigating and editing text is an essential part of any operating system, and with iOS 13, Apple has made some significant changes. Some things remain the same when working with text, but there are many updates to moving the cursor, scrolling, and selecting, cutting, copying, pasting, undoing, and redoing text.

If cameras are a priority, one of the first specs to check on a new phone is the image stabilization. You've probably been told optical image stabilization (OIS) reigns supreme, but this isn't the case if you're taking a lot of videos. Instead, we would argue, electronic image stabilization (EIS) actually works better for video.

There are many reasons to use Filmic Pro if you're a mobile videographer. Chief among them is its automated controls, called "pull-to-point" sliders. These pull-to-point controls not only allow you to manually adjust focus, zoom, exposure, ISO, and shutter speed before and during the action, they also let you set start and end points to automate each function, leaving you free to focus on filming.

One of the most powerful features when editing videos with Enlight Videoleap is the keyframe tool, which allows you to add custom transitions, animate text, granularly adjust audio, move video clips across the frame, supplement effects, and more. If you want your video to change color over time or for captions to move across the screen, use keyframes in combination with Videoleap's other tools.

Websites are often misconfigured in ways that allow an attacker to view directories that are not ordinarily meant to be seen. These directories can contain sensitive information such as private credentials or configuration files that can be used to devise an attack against the server. With a tool called Websploit, hackers can scan targets for these hidden directories without difficulty.

Before attacking any website, a hacker or penetration tester will first compile a list of target surfaces. After they've used some good recon and found the right places to point their scope at, they'll use a web server scanning tool such as Nikto for hunting down vulnerabilities that could be potential attack vectors.

It's easier than you might think to hack into Wi-Fi routers using just one unrooted Android phone. This method doesn't require brute-forcing the password, a Windows OS for converting PowerShell scripts into EXE format, a reliable VPS for intercepting hacked Wi-Fi passwords, or Metasploit for post-exploitation tricks.

If you transition to an Apple Watch from another wearable like Fitbit, you might be a bit confused by the new calorie burn counter. Instead of ending your day with thousands of calories burned, your watch says you've burned just hundreds. Could it be you're less active with your Apple Watch? Probably not. It's more likely because of the different way the watch counts your calories.

Reconnaissance is the phase of an attack where a red team or hacker designs a strategy based on the information they can learn about the target, as well as what the available attack surface looks like. These scans can take time to discover relationships, but Raccoon OSINT scanner coordinates multiple automated scans to produce invasively detailed reports on a target with a single command.

Traditional subdomain enumeration techniques create a lot of noise on the target server and may alert intrusion detection systems to an attacker's intentions. For a stealthier approach, there's a tool with the capability of finding hundreds of subdomains related to the target website without alarming the server administrators.

The microphone in a Windows computer is accessible to most applications running on the device at all times and completely without security limitations. Information gathered from recorded audio conversations taking place in the surrounding area of a compromised computer can be used for social engineering, blackmail, or any number of other reasons.

Using Hydra, Ncrack, and other brute-forcing tools to crack passwords for the first time can be frustrating and confusing. To ease into the process, let's discuss automating and optimizing brute-force attacks for potentially vulnerable services such as SMTP, SSH, IMAP, and FTP discovered by Nmap, a popular network scanning utility.

Using just a small sticky note, we can trigger a chain of events that ultimately results in complete access to someone's entire digital and personal life.

With Virtual Network Computing, you don't need to carry a spare keyboard, mouse, or monitor to use your headless computer's full graphical user interface (GUI). Instead, you can connect remotely to it through any available computer or smartphone.

The future is here with a new demo made with Apple's ARKit and LeapMotion. Typically, since ARKit works through your iPhone, in order to move augmented reality objects that are appearing on your screen, you have to drag them with your finger. However, developer Arthur Schiller is now playing around with how you can move augmented reality objects on your phone with gesture recognition, rather than by touching.

GitHub is an extremely popular site that allows developers to store source code and interact with other users about their projects. Anyone can download public, open-source files on GitHub manually or with Git, and anyone can fork off someone's project to expand or improve it into its own project. It's a really great site for programmers, developers, and even inspiring hackers.

In this tutorial I am going to show you how to create an undetectable Meterpreter Trojan using a Domain name. I have taken a few guides/tutorials and built it into one. The first part is creating the DNS Payload. The second part is creating the Executable file. Part 3 is using both in Shellter to create your undetectable Trojan. Part 4 is setting up your listener using Armitage.

Very often we have processes in Linux that we want to always run in the background at startup. These would be processes that we need to start at bootup and always be available to us.

Welcome back, my greenhorn hackers! The Holy Grail of any hacker is to develop a zero-day exploit—an exploit that has never been seen by antivirus (AV) and other software developers, as well as intrusion detection system (IDS) developers. In that way, you can exploit systems with your newly discovered vulnerability with impunity!

Welcome back, my novice hackers! More and more, the world is turning to and adopting the smartphone platform as the digital device of choice. People are not only using smartphones for voice communication, but also web services, email, SMS, chatting, social networking, photography, payment services, and so on.

One of the most exciting things about a major iOS update is the discovery of new glitches, or even just finding ways to replicated the old ones that we've come to love so much. One of these is the glitch that lets you nest folders within folders on the home screen, which can save some major screen real estate. While this glitch was available in both iOS 7 and iOS 8, the process is slightly different in iOS 9, but you still have a couple options to choose from.

When I tried to set up an eviltwin for a MitM-constelation in kali 2.0, I couldn't provide internet to the victim. The origin was the brctl bridging. I have read many tutorials but all of them where explained in backtrack and older versions of kali. So i was searching for a solution without using brctl and this solution will be explained now. This will just work on unencrypted wireless-environments.

With each day that dawns, there is a new, major hack that makes the news headlines. If you are paying attention, there are usually numerous hacks each day and far more that never make the news or are kept private by the victims. Every so often, a hack is so important that I feel compelled to comment on it here to help us learn something about the nature of hacking and IT security. This is one of those cases. Last week, the U.S. Office of Personnel Management (OPM) revealed that they had been ...

It's been a while when the major web browsers first introduced HTTP Strict Transport Security, which made it more difficult to carry Man In The Middle (MITM) attacks (except IE, as always, which will support HSTS since Windows 10, surprised?).

Presented by Apartments.com When looking for a new apartment, it's hard not to notice the improvements (on large and small scale) needed prior to moving in. While your landlord may be taking care of new carpeting, cleaning the central air vents, and fresh paint on the walls, there may be some additional improvements on your list that you can take care of on your own. Here are five quick improvements you can check off your list before the big move.

With smartphone screens getting bigger by the generation, one-handed mode mods are becoming rather prevalent. Most of these function by shrinking the screen to a more manageable size, but this is actually kind of boring when you think about it.

Welcome back, my hacker novitiates! As you know by now, the Metasploit Framework is one of my favorite hacking tools. It is capable of embedding code into a remote system and controlling it, scanning systems for recon, and fuzzing systems to find buffer overflows. Plus, all of this can be integrated into Rapid7's excellent vulnerability scanner Nexpose.

Welcome back, my greenhorn hackers! In previous Wi-Fi hacking tutorials, I have shown you ways to create an Evil Twin, to DoS a wireless AP, and to crack WEP and WPA2 passwords, but in this tutorial, I will show you something a little bit different.

The latest software update to the Amazon Fire Phone packed a lot of new and enhanced features, one of which makes the Carousel (a favorite feature of mine) much more useful.

Fast moving cars, strangers in the background, and even birds flying by can all ruin a great shot. Thankfully, TouchWiz provides the tools to remove unwanted objects, right in the stock camera application.

The way you use your camera just got a bit more interesting. Phogy, a brand new camera app for Android, allows you to capture pictures with a 3D effect that comes alive when shifting your phone from side to side.