This is very tasty and easy to follow cheesecake recipe. - You will need a 20 centimeter spring form pan. You'll also need: 14 grams of sweet biscuit crumbs, 7 grams of butter, cinnamon, 75 grams of cream cheese, 4 eggs, 1 cup of sugar, 1 teaspoon of vanilla essence, 1 tablespoon of grated lemon rind, and 2 teaspoons of lemon juice.

The recipe can be found on www.yesdivascancook.com. An eBook containing this and other cheesecake recipes is also offered.

Learn to tie the triple goddess knot with this video tutorial. First you will need a nice size piece of string. Make a small loop with one side of the string close to the middle. Second, make a second loop with the other side of the string close to the middle. Third,cross the right hanging part of the string over the left string to form a small circle under and between the two bigger loops. Insert the end of the left string into the underside of the left loop to form a split loop. Do the same...

This is a very simple fudge recipe using evaporated milk, marshmallows, and chocolate chips that brings raves. It is a classic candy recipe that is often requested. Instructions are also given for butterscotch and mint flavors.

Artichokes can be a delicious treat with a butter sauce or other dipping sauces. You don’t have to be a blue ribbon chef to prepare artichokes. Just keep these few tips in mind.

Worried about your next drive in the rain? Do you feel you & your car are not prepared? Stay safe in a downpour with these tips to handle slippery, wet pavement and reduced visibility.

Chutney is a term for a class of spicy preparations used as an accompaniment for a main dish such as chicken or fish. Serve this delicious mango chutney with your prepared fish or chicken dish tonight.

Neck pain can be the worst. Be aware of daily habits that may be causing your chronic neck pain and replace them with healthy choices. In this tutorial, learn how to soothe chronic neck pain.

Not sure what skirt length is most flattering on your body? Hemlines rise and fall like the stock market, but you’ll always look great if you heed these tips.

It’s an evening of wining and dining and you want your meal to come out perfect. Whether a side dish or main course, please your crowd with pasta al dente.

Fishing is relaxing, but not if you hook yourself because you couldn’t cast a reel! You Will Need

Think you can beat the bubble-gum bubble record? Follow these steps and learn how to blow the biggest bubble ever!

When faced with the searing pain of brain freeze, use these quick tips to bring sweet relief. You Will Need

Prevent yourself from peeing in your pants with these tricks. You Will Need:

Don't sign any termination papers until you're sure you've made the best deal you can. You Will Need

Watch this cooking how-to video as Tracy cooks some authentic Jamaican festival. What is festival you ask? Jamaican festival is a sweet like bread. Follow along with this Jamaican cooking lesson to learn how to make festival.

Looking for a fancy dessert for tonight? Then try this recipe, it is a specialty from the Cognac region in southwest France. This Souffle a la Cognac is sure to be a hit.

Watch this how to video to learn how to make classic, comforting corn bread for a dinner side dish, afternoon snack or quick breakfast.

Check out this video to learn scoring techniques of joining two pieces of stiff leather-hard clay. Following are some steps you will see demonstrated

Cosmetics maker Coty is hanging an augmented reality Magic Mirror on the wall of its Bourjois boutique in Paris that will tell customers which shade of makeup will make them the fairest of them all.

Everything that has a beginning has an end. This week marked the end of the long wait for the reveal of Magic Leap's first product and the beginning of the wait for more substantive details. Likewise, Google Tango will meet its end in March 2018, when ARCore will officially begin its public rollout.

The ride-sharing company Lyft has managed to secure $500 million in funding, which will certainly help its ongoing competition with Uber. According to recent reports, the cab firm is currently valued somewhere between $6.9 billion and $7.5 billion, but this still pales in comparison to Uber's estimated $70 billion valuation.

There may be no other crustacean with as many names as the crawfish: crayfish, crawdad, crawdaddy, mudbug, Florida lobster, spiny lobster, rock lobster, and freshwater lobster (to name a few). But no matter what you call it, there's no denying that it's a popular delicacy in the South and beyond.

Gatorade and football go hand in hand, from player endorsements to the traditional Gatorade shower that coaches get at each Super Bowl. So, get in the game-day spirit with these Gatorade-infused drinks, desserts, and snacks. The good thing about Gatorade is that it comes in every color of the rainbow—so feel free to make these in your favorite team's colors.

Most of you already know that a zero-day exploit is an exploit that has not yet been revealed to the software vendor or the public. As a result, the vulnerability that enables the exploit hasn't been patched. This means that someone with a zero-day exploit can hack into any system that has that particular configuration or software, giving them free reign to steal information, identities, credit card info, and spy on victims.

Pies and soufflés: these are two dishes that can try even the most experienced cook. Berry pies can be especially challenging, since the high water content of cherries, strawberries, blueberries, and blackberries often leads to a big, leaky mess once you cut into your beautiful pie.

Magic Leap's business strategy for bringing augmented reality to the mainstream has become even clearer via its latest funding round.

If you've ever wanted to barge into Jerry Seinfeld's apartment like Cosmo Kramer, you can now do so without having to book a ride on the Peterman Reality Tour.

The story of Meta and its Meta 2 augmented reality headset isn't over, there's a new development that could impact its ultimate fate.

Although Niantic is already an augmented reality startup unicorn thanks to the success of Pokémon GO, the company has reportedly captured yet another round of funding.

If imitation is the sincerest form of flattery, then Niantic must be blushing constantly, as numerous copies of Pokémon GO have spawned over the past year or so, seeking to capture the same success, often adding the lure of tangible prizes from brand partnerships.

France's Groupe PSA (formerly known as PSA Peugeot Citroën) — one of the world's top-10 carmakers — aggressively seeks to take a lead in the rollout of the industry 's first driverless cars, as it becomes the first mainstream carmaker to announce it will launch a Level 3 self-drive vehicle launch by 2020.

Demand for Tesla's driverless features as well as its ultra-long battery ranges and a reputation for offering the best-in-class electric car driving experience helped Tesla see a 32% surge in its value as a brand, topping out at $5.9 billion in the BrandZ Top 100 Most Valuable Global Brands study, released June 5.

Samsung has some competition as LG may be incorporating OLED panels for their new flagship V30 launching later this year.

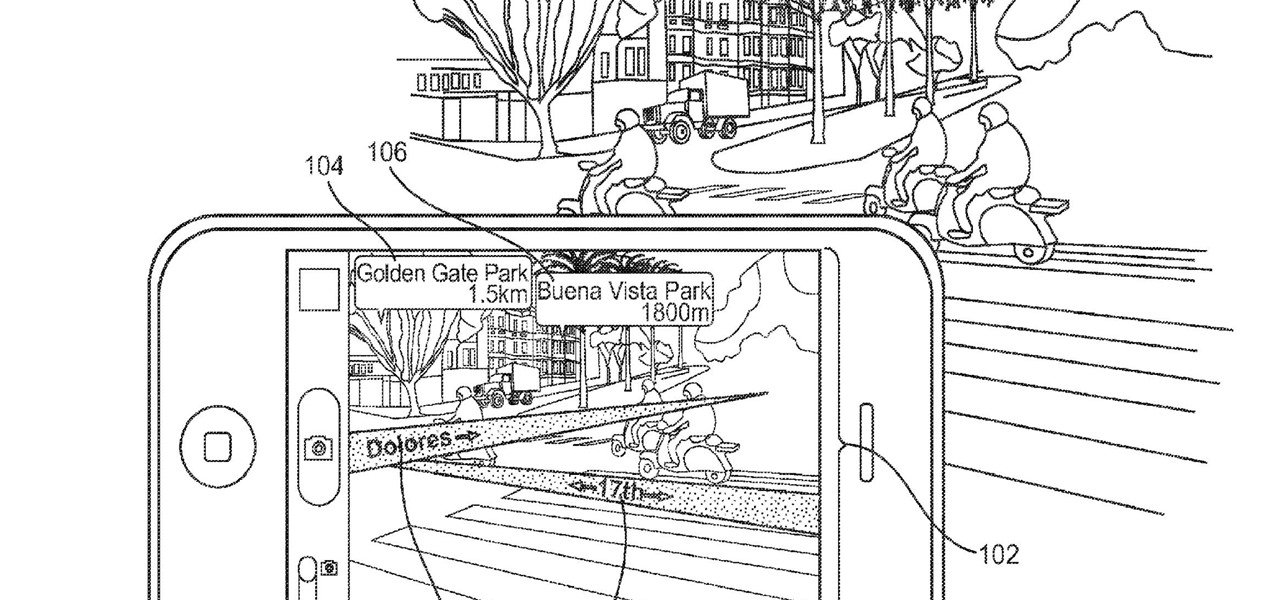
Apple is combining internal and external talent in an effort to give them in edge in the augmented reality market, though we still don't know what form their foray into alternative realities will actually take.

Hello, Null Byters. I'm Barrow, and I'm excited to introduce myself as the new admin here on Null Byte. Just like previous admins have done before me, I will be writing new guides, updating older guides if they need it, and responding to some of your issues in the forum. Before I get started with any of that, though, I wanted to talk a little bit about myself and the future of Null Byte.

Knowing how to cut and slice raw meat is a skill all omnivorous cooks need in their arsenal. However, raw meat's limp and gelatinous character can be challenging to work with, especially when you're trying to slice it into symmetrical, attractive sections for a stir-fry or a stew.

This video demonstrates how to make a funky yarn pom pom. Take a yarn of your choice that matches your scarf. Take one end of the string and start winding it not too tightly around your fingers. Leave back enough string for the pom pom for the other end. Cut the string using a pair of scissors and set it aside taking care not to mess the ball. Cut another piece of string with appropriate length that goes around the ball of string kept aside. Place the cut string over the table and place the b...

Learn how to make delicious sushi like a real chef. You may think sushi is just raw fish, but you’d only be half right. It’s actually the combination of fish and rice – and how it’s combined is an art form in itself.

There are countless ways in which a talented and trained programmer and tech pro can earn a lucrative living in an increasingly data-driven age — from writing and creating apps and games to working for a cybersecurity firm or even the federal government.