We admit it: we are ranch dressing fanatics. We like to put it on our simple salads, spread it across our chicken wings, and dip homemade sweet potato fries in it. Plus, since childhood, neither of us can eat pizza without ranch dressing to accompany it.

It's hard to argue with the notion that wine and pasta are a winning combination. I mean, millions of Italians can't be wrong.

I have came across a lot of members on the forum that didn't have a clear idea of what port forwarding is and what it does. So...Let's get started...

As one of the most popular home screen apps on Android, the Google Now Launcher is used by millions of people across the world. The two main reasons behind this success are its integrated Google Now home page and an elegant, easy-to-use design.

Although lots of the bigger hotel chains are lessening the restrictions they put on their room TVs, some smaller ones are still taking measures to prevent you from plugging in computers or streaming devices into an HDMI port. However, there are a few steps you can take to bypass these restrictions and watch your own media in a hotel that has restricted TVs.

In a letter dated February 16th, Apple CEO Tim Cook responded to the FBI's demand that Apple create a "backdoor" to bypass the encryption on an iPhone used by one of the perpetrators of last year's terrorist attack in San Bernardino, CA. Cook began the letter by stating that Apple has "no sympathy for terrorists" and has cooperated in giving the FBI all of the information that it has available.

So, you want to perform an exploit on a victim, but you're not on the same network as their machine. In this tutorial, I'll be showing you how to set up a meterpreter reverse_tcp attack to work over the internet.

In my last tutorial, I talked about creating a virus inside of a Word Document in the scenario of a mass-mailer attack. In this post, however, I'm going to be covering creating a fake image or screenshot with a meterpreter backdoor hidden inside to be used in a similar scenario. Step 1: Creating the Virus

Obviously this is just a teaser, and who knows how soon we'll see something like this in real life, but just go ahead and watch the video first before you continue reading.

There are a million (okay, slight exaggeration) ways to peel an egg, and countless numbers of tips, tricks, and hacks that are supposed to make that deviled egg appetizer you agreed to make for the party an absolute snap. More often than not, though, experiences vary... and pock-marked, greyish-yolked boiled eggs find their way into your collection whether you like it or not.

When performing something such as a mass mailer attack on a company, sending executables usually isn't the best option. That's why, in this tutorial, I'll be teaching you how to code a VBA script macro into a Word document in order to compromise a system. Combined with a little social engineering, this can be a very effective technique.

There's been a whole lot going on at this year's Consumer Electronics Show, from the latest in virtual reality gear to televisions that continue to slim down while producing higher quality images.

Everyone and his mother (and grandmother) has a chocolate chip cookie recipe that he swears is the absolute best recipe, guaranteed to produce a chocolate chip cookie so good it will make you weep with joy. The problem with that is that everyone—relatives included—has a different idea of exactly what constitutes a perfect chocolate chip cookie.

Welcome back, my novice hackers! One of the most common questions that Null Byte readers ask is: "How can I evade detection by antivirus software on the target?" I have already talked about how AV software works, but to obtain a deeper understanding, what better way is there than opening up and dissecting some AV software?

Winter—or any cold, gray day, for that matter—is the best time for a warm cup of something hot. For me, hot chocolate is my "warm cup" of choice: rich and milky, deliciously sweet, and oh-so-comforting. On super-cold days when I can't feel my face, a nice, large cup of hot chocolate warms my tummy and cheers me up. (And lucky for me, it's pretty healthy for me too!)

Those of you who have been a part of the Null Byte community for even a short while know that I sincerely and firmly believe that hacking is the most important skill set of the future.

Welcome back, curious hackers! In today's tutorial, we will be diving deep into the manipulation of Google Operators, commonly referred to as "Google Dorks" in order to access Surveillance Cameras and other control panels.

Out of the box, your iPhone will not shoot 4K videos. If you want to up your video quality to go beyond 720p or 1080p HD, you'll have to do it manually. However, not all iPhone models can actually film in 4K resolution. If you have an iPhone 6 or below, you're out of luck, but if it's the iPhone 6S or newer, you can rock the 4K no problem.

At night, no matter how dim my Android's screen gets, it never seems to be enough—especially when I'm in bed. In fact, in pure darkness, the lowest brightness setting on my Android devices end up giving me a headache that keeps me up for hours.

Hello all! In this tutorial, I'd like to show you one way of getting root on OS X. Check out this GitHub page for a recent privilege escalation exploit that was recently discovered. I've tested it and it works on both OS X 10.9 Mavericks and OS X 10.10 Yosemite, but appears to have been patched with OS X 10.11 El Capitan. If you check out the file main.m you can see where most of the magic is happening. This source code can very easily be changed to make it do more than just the system("/bin/...

Hello all, this is my first submission to null byte! I noticed something a little strange, particularly that whenever Meterpreter is discussed, it is virtually always in the context of Windows. Granted, the Windows Meterpreter is more powerful than the version that can run on OS X (it has several more commands/options), but I think it is still worth noting how to do it. I've even seen some people mistakenly say that Meterpreter can only be run on Windows, which is not true. Meterpreter can ea...

I have a personal rule when it comes to an app's interface: If it doesn't follow Android's design guidelines, it was probably written with Apple's iOS in mind first and foremost.

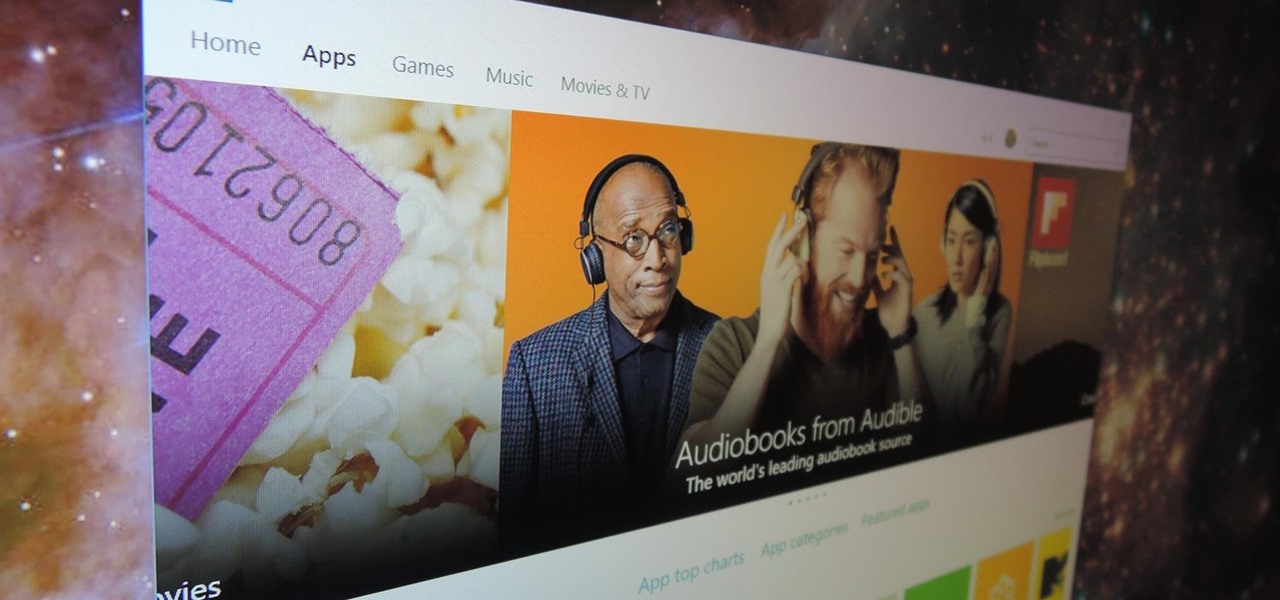
Windows 10 marks a new era for Microsoft with the return of the Start menu, the demise of Internet Explorer, and the introduction of the remodeled Windows Store.

Welcome back, my tenderfoot hackers! In this series, we are exploring the myriad of ways to hack web applications. As you know, web applications are those apps that run the websites of everything from your next door neighbor, to the all-powerful financial institutions that run the world. Each of these applications is vulnerable to attack, but not all in the same way.

I have a lot of favorite kitchen tools. My seven-inch Global chef's knife is my baby. My pasta maker is my dance partner on any given Friday night. My girlfriend's stand mixer is my favorite toy in the apartment.

Other than salt, there's no ingredient that's as big a kitchen staple as olive oil. And just like salt, there are a million little known uses for it.

There are three huge benefits to microwave popcorn: it's quick, it's delicious, and it's cheap. But there's a way to make popcorn that's better, more delicious, and cheaper than the microwave variety. And oh yeah, quite a bit healthier.

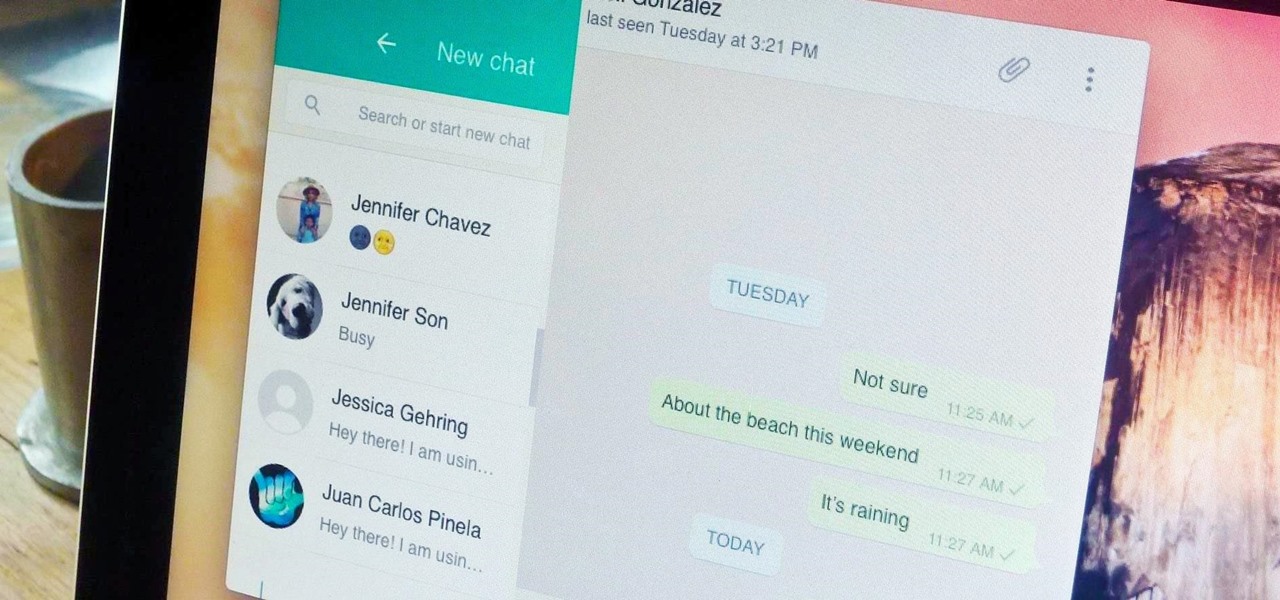
Boasting over 800 million users a month, WhatsApp has quickly become one of the most popular messaging services available today. Thanks to its low price, ease of use, lack of ads, cross-platform functionality, and great features, its popularity is well-deserved.

At its core, grilling is the simplest form of cooking. You create extreme heat, you put a piece of food on top of the heat, and then you sit back and watch the magic happen. Yet despite the inherent simplicity in grilling, there are a million ways to make it more complex, more unique, and, yes, even more flavorful.

It's a basic law of cooking: whenever you're really craving something, you don't have it. All you want is a glass of wine? Chances are you finished the bottle while braising meat last night. Want nothing more than a sandwich right now? Yep, you finished the bread with breakfast. You'd kill for a steak? They're all in the freezer, and you don't want to wait while they thaw; you want your steak now.

At any moment, you can open up Meerkat and start live-streaming a video from your smartphone, available for anyone to watch. Thanks to its popularity at SXSW and the backing of several big Hollywood players, the app just announced that it's receiving $14 million in funding.

Today I am going to teach the various ways that you can use social engineering to hack a system. For those of you that have followed my past tutorials, you know that social engineering can unlock a world of possibilities. This is because no matter how many firewalls, no matter how many patches there are on a server, the password is kept in the minds of people...and people, are not as smart as computers.

Although this century is still young, with little fanfare we may have just witnessed the "Hack of the Century." AV software developer Kaspersky of Russia recently announced that they found that some hackers have stolen over $1 billion from banks around the world!

Welcome back, my tenderfoot hackers! Hacker newbies have an inordinate fixation on password cracking. They believe that cracking the password is the only way to gain access to the target account and its privileges. If what we really want is access to a system or other resources, sometimes we can get it without a password. Good examples of this are replay attacks and MitM attacks. Neither requires us to have passwords to have access to the user's resources.

This past year was a big one for WonderHowTo. Our biggest yet. In 2014 our writers, curators, and community members helped over 100 million people learn over 270 million new things. That's 40% more people than the total number of students enrolled in every single school from elementary through college across the entire United States. That's pretty awesome. I couldn't be more proud of our entire team, and of course you, the community members who've helped us grow to this point.

Blizzard Entertainment, the wildly successful video game developer that brought us World of Warcraft and StarCraft, has finally released their popular trading card game Hearthstone: Heroes of Warcraft to the Android platform.

Hate slogging through pages and pages of weighty books and lengthy work documents? You may not be able to depend on speed-reading apps, but with the right font, you can increase the number of words you scan each second, speeding up your reading pace exponentially.

While most of us don't think twice about dragging a pattern or using Touch ID to open our phones, or entering a password in for our email and bank accounts, these features are there to protect some of our most private information. Only problem is, they don't do a good job of it.

I have never been a morning person, and that's a trait that I don't think is going away. Combine my distaste for early hours with being a heavy sleeper, and it adds up to a lot of alarms being dismissed in a haze, with no real intention of ever waking up.

iPad, iPhone, and iPod touch owners: it's that time again. iOS 8 has been released to the public, and those who have been eager to update since Apple's WWDC announcement won't have to wait any longer. Since iOS 8 promises to pack a bunch of new, really great features, it's time to present your options for getting on the latest and greatest for your Apple device.