The largest and arguably most widely known event of its type, especially in the US, the Sundance Film Festival is an annual celebration of independent film—ones made outside the Hollywood system. This year, a new type of experience appeared at the Sundance Film Festival in an installation called "The Journey to the Center of the Natural Machine." This mixed reality presentation offered the user the newest type of storytelling in a long and important line—continuation of the species kind of im...
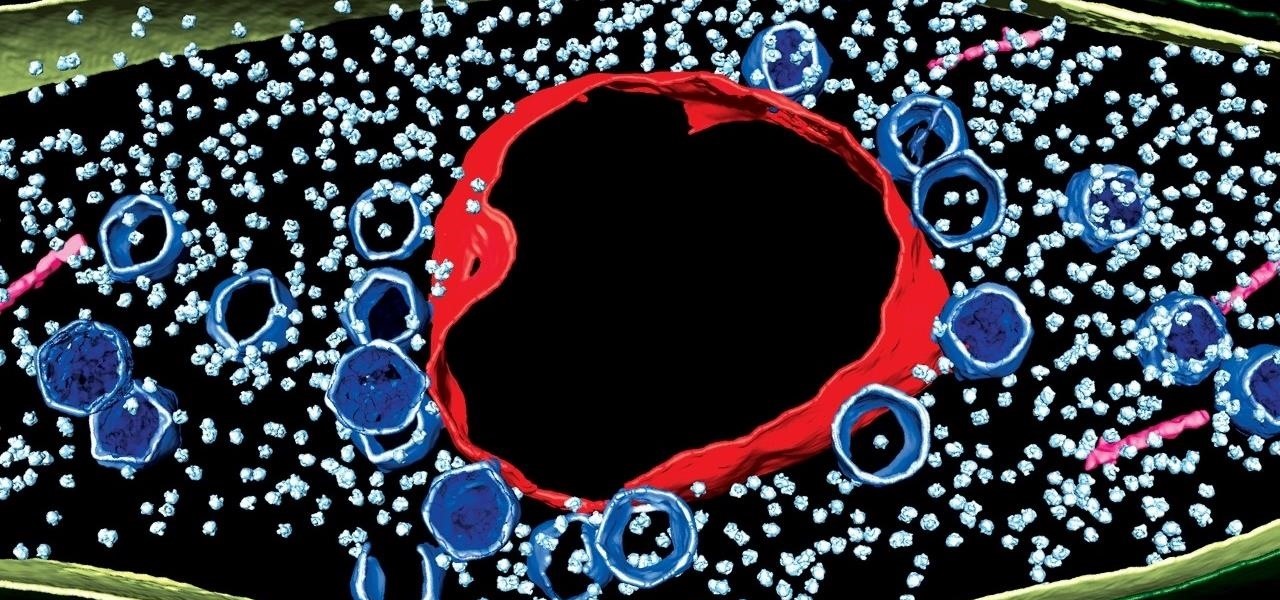
Using extreme time-lapse microscopy, scientists watched a virus take over a bacteria to create a cell that looked and functioned more like a plant or animal cell. True story.

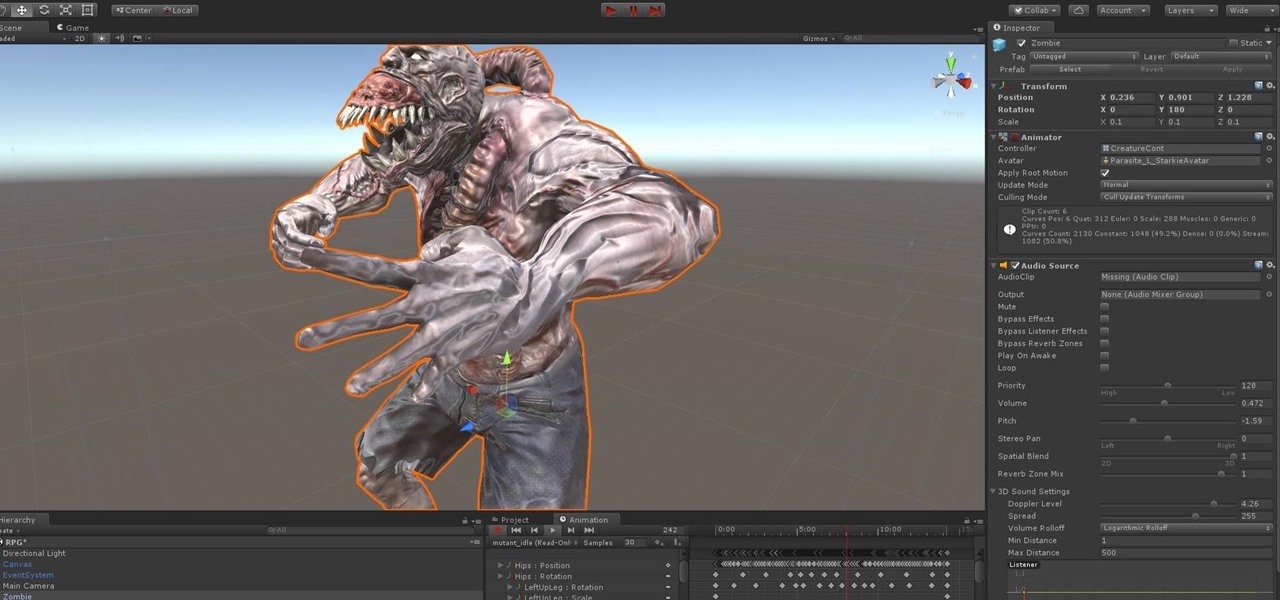
Welcome back to this series on making physical objects come to life on HoloLens with Vuforia. Now that we've set up Vuforia and readied our ImageTarget and camera system, we can see our work come to life. Because in the end, is that not one of the main driving forces when developing—that Frankenstein-like sensation of bringing something to life that was not there before?
We live in a computer world full of file formats. Whether we are talking about images, videos, or text documents, there are dozens of file types for each, and there are new ones added every year to applications. Keeping in mind that many of these formats were created before the internet was widely available (at least, in infant form), the primary reason for this glut of often complex choices is competition.

Breaking off a piece of that Kit Kat bar gets a lot more difficult when the whole thing weighs 13 pounds.

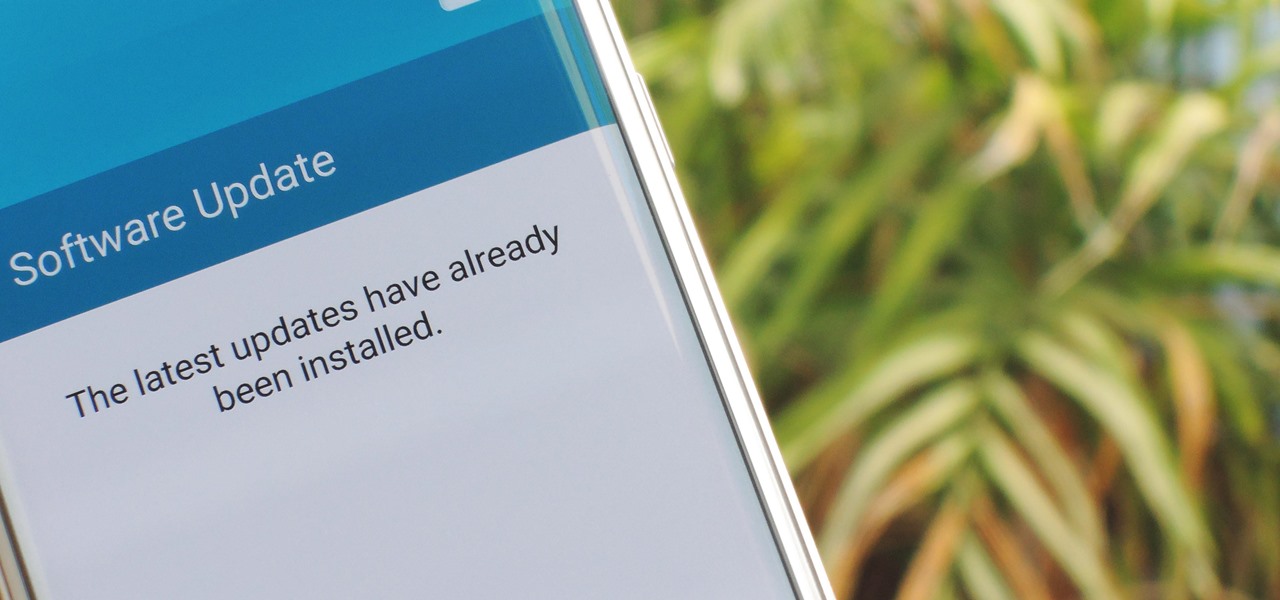
While it hasn't gotten as much attention as iOS 10, Apple's big 10.12 update to their Mac operating system is finally out for all to enjoy—and you can download it for free from the Mac App Store right now.

Smartphones have been around for nearly a decade now, so we've had plenty of time to develop preconceptions and bias. People that have never owned an iPhone will tell you that Apple devices are restrictive and bland, while others might say that stock Android is boring compared to manufacturer skins like HTC's Sense, despite never having owned a Nexus or Pixel.

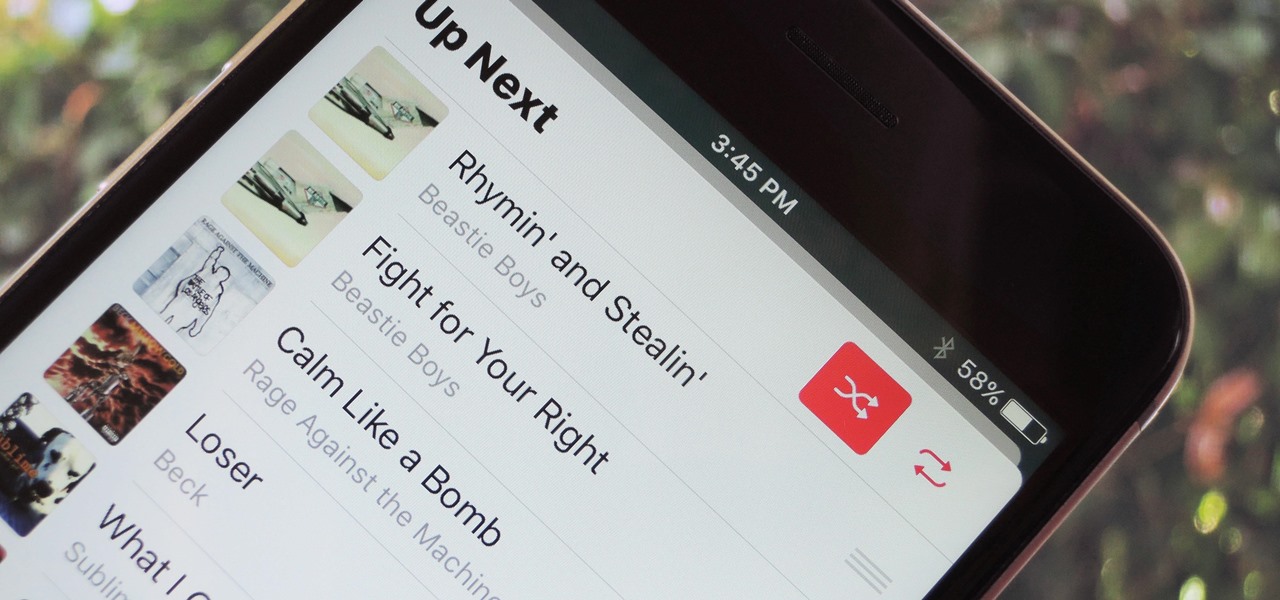
With each update, Apple Music continues to become a bigger part of iOS. It's gotten to the point where you have to fend off multiple requests to subscribe to the streaming music service before you can listen to your own songs on an iPad or iPhone, but as it stands in iOS 10, maintaining your own MP3 library is still possible. Just barely.

You can put spices in a scramble or fry an egg in bacon fat, so why poach eggs in just plain water? Water doesn't add any flavor whatsoever, so you're wasting a valuable opportunity to give your poached eggs more oomph—an extra important step if you're not frying your poached eggs afterward.

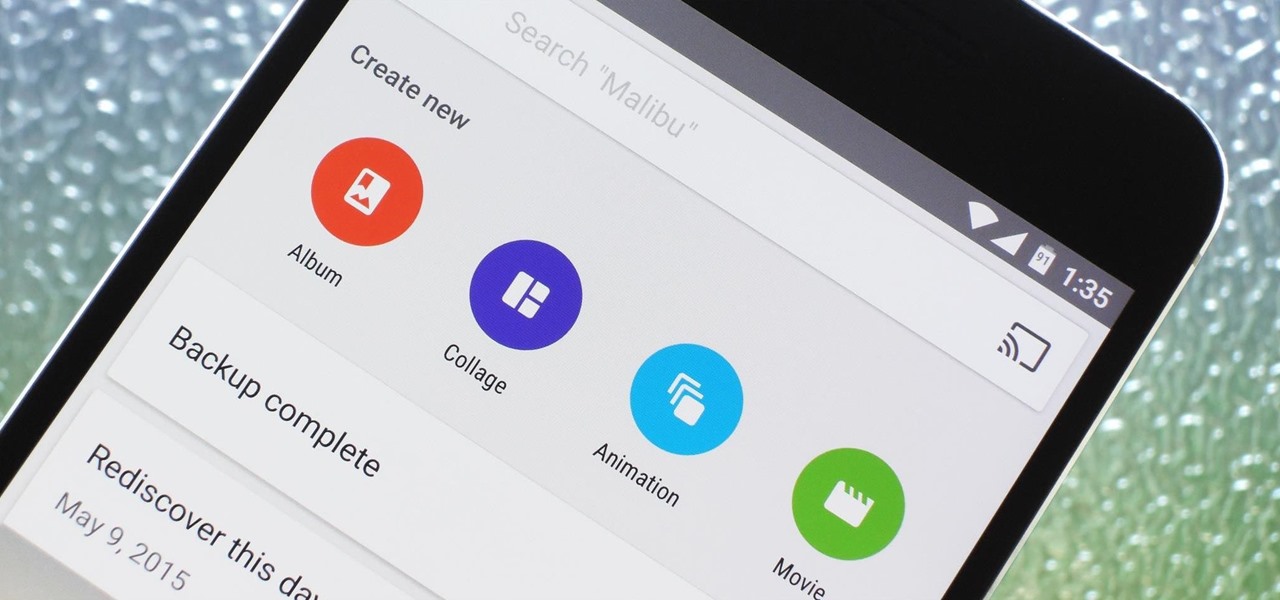
Google Photos is one of the best photo management services out there. It allows you to back up an unlimited amount of high-quality images without ever paying a dime, the photos and videos sync flawlessly across all of your devices, and its neural network-powered visual search feature seems like something that was pulled directly out of a Sci-Fi movie.

You've probably noticed artichokes at the front and center of your local grocery store or farmer's market recently, as spring is artichoke season; They may look like strange, complicated vegetables if you've never cooked them before.

When given the choice between canned and dried beans, many of us are guilty of reaching for cans. They're much more convenient than investing 5-6 hours of your time to make dried beans edible.

Welcome back, my rookie hackers! The Golden Fleece of hackers is to develop a zero-day exploit, an exploit that has not been seen by antivirus (AV) software or and intrusion detection system (IDS). A zero-day exploit is capable of skating right past these defenses as they do not contain a signature or another way of detecting them.

If you use a wireless mouse or keyboard, you could be leaving yourself open to attacks from hackers. Researchers at Bastille had discovered in January 2016 that attackers could make use of a cheap $15 antenna to sneak into your computer through a wireless mouse or keyboard dongle (receiver).

Very often we have processes in Linux that we want to always run in the background at startup. These would be processes that we need to start at bootup and always be available to us.

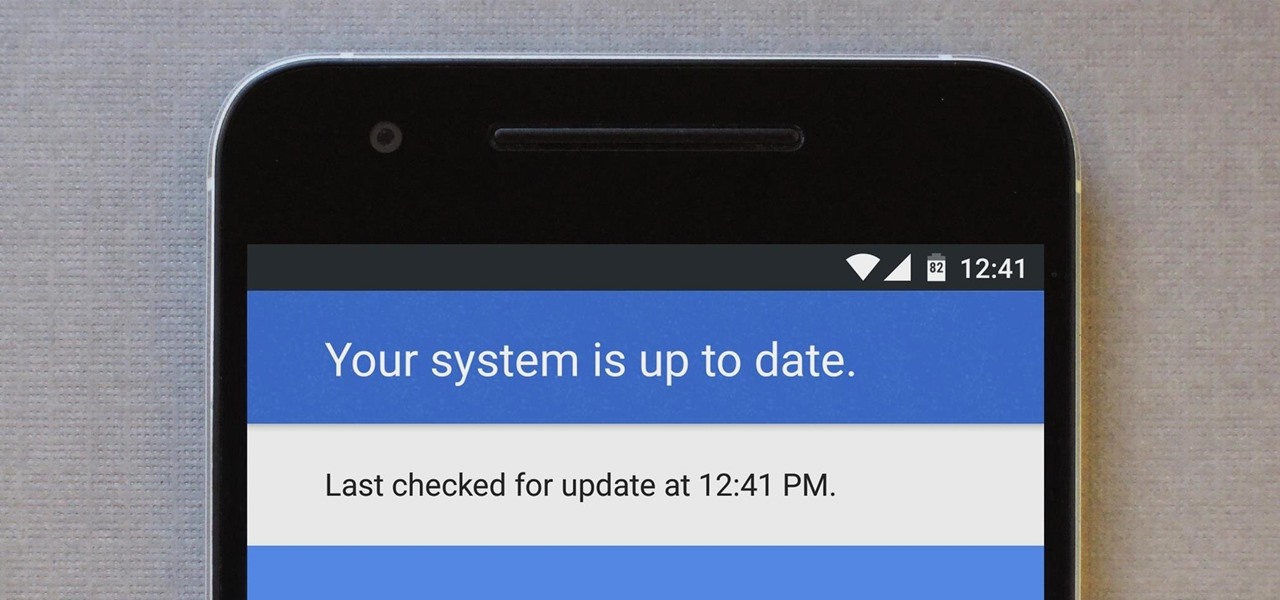
For many people, the two main advantages of buying a Nexus device are prompt updates and the ability to root without much hassle. But in a cruel twist of fate, these two features are almost mutually exclusive, since OTA updates will refuse to run on rooted devices.

I mentioned in one of my earlier articles something about ghost hackers, and very shortly stated a thing or two of what they do.

Welcome back! Sorry I've been gone for so long, but if anyone has been keeping up with these articles, you'll know that when I get quiet, something is cooking under the surface. In other words, I've been working on a project lately, so I haven't had much time!

First of all, I would like to apologize for a week long absents for the tutorials of this newly series, Raspberry Pi. But obviously I'm back and I present all you guys a article on turning your Raspberry Pi into a hacking platform. I'm gonna use the platform Kali Linux for the Raspberry Pi. I should note that I'm not gonna go into detail on how to install Kali Linux since OTW already has done a tutorial on how to turn your Raspberry Pi into a Hacking Pi. The point of this particular tutorial ...

Welcome back to a tutorial on malware. We'll be discovering a method to beef up our little trooper. Without further ado, let's jump right in!

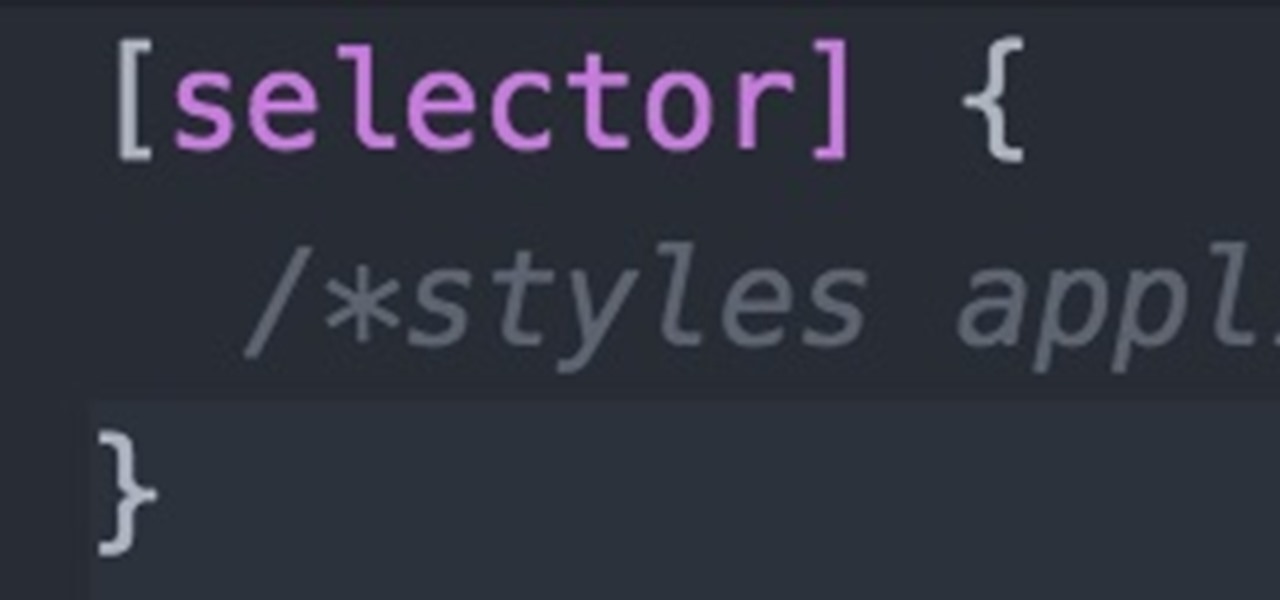
Welcome back Null-Byters! You finally have the pre-basics of CSS and we can begin with styling our web page. If you did not read our last adventure, I suggest you go and read it.

This is my first how-to for this site so feel free to let me know if I can somehow improve! Inspired by the great Jailbroken iDevice and Rooted Android PenTesting tutorials I decided to share how I use my Toshiba Chromebook 2 with Kali Sana.

Welcome back, my fledgling hackers! Over the years, we have examined multiple ways to own, exploit, or compromise a system. On the other hand, we have not spent a lot of time on denial-of-service (DoS) attacks.

Hello, everyone! Many of you don't even know about my existence here on Null Byte, so I thought of contributing something rather interesting. Recently, someone asked how to make your own "Bad USB," and I promised to make a how-to on this topic. In addition, it would be nice to have something related on our WonderHowTo world. So here it is!

Not too long ago, Sony was looking to create a method for theming the interface of their Xperia smartphones and came up with a framework called Runtime Resource Overlay (RRO). They then contributed this framework to Android's main code base, and Google has since taken over the development of RRO as a way for manufacturers to implement themes in their skinned versions of Android.

Reddit, the self-proclaimed "front page of the internet," continues to take a big bite of my free time each and every day, as well as millions of its other users'. The clicking and scrolling through page after page never gets old, but you could speed things up with a few browser extensions and double your Reddit knowledge in half the time. Here are my favorite extensions you can try out for the Chrome, Firefox, and Safari web browsers.

Preparing and serving seafood can be a daunting task. Fish is so delicate that one extra minute of heat can turn a juicy, flaky filet into a dried-out disaster. But that same fragility also allows us to use unconventional methods to chemically transform the fish into its cooked consistency.

Often, despite your favorite makeup mecca's rows and rows of endless colors, applicators, and brands, it's hard to find the perfect shade of lipstick—especially one at the price you want. Rather than resorting to what's available in stores, turn to your stovetop and a box of crayons.

Depending on your child's age, their first smartphone may be a little too open for them, or you, to handle. With essentially a world of information—both good and bad—available at their fingertips, it can seem like a huge hurdle to instill parental controls on their device.

You can beef up the security on your Mac all you want, but all the firewalls and antivirus apps in the world mean nothing when that can of soda tips over on your Macbook, destroying your laptop and all its data forever.

Google's Chromecast is quite literally one of my favorite inventions of the past five years, allowing me to kick back, relax, and enjoy the various forms of streaming entertainment it has up for grabs.

Heads up! We've done a new, more thorough review of the best Android file-sharing apps. You can check that out here. Our old file-sharing app roundup can still be viewed below for posterity.

The right music can spur you to pick up the pace during an intense workout, pep you up before you hit the treadmill or walking path, and even encourage you to lift for just a few extra reps. Although we all have our favorite workout playlists, scientists have discovered what it is, exactly, that makes you workout harder when certain songs begin.

Welcome back, my tenderfoot hackers! One of the issues we often encounter with Metasploit is how to add new modules. Although Rapid7 (Metasploit's owner and developer) periodically updates Metasploit with new exploits, payloads, and other modules, at times, new modules appear that are not added to the Metasploit repository.

Apple's latest update to Mac OS X, 10.11 El Capitan, is currently available in the Mac App Store for everyone to download and install at no cost. The new OS features Split View mode for better multitasking, a cleaner Mission Control, smarter Spotlight, a way to mute Safari tabs playing audio, enhanced Mail and Notes apps, and more.

With each day that dawns, there is a new, major hack that makes the news headlines. If you are paying attention, there are usually numerous hacks each day and far more that never make the news or are kept private by the victims. Every so often, a hack is so important that I feel compelled to comment on it here to help us learn something about the nature of hacking and IT security. This is one of those cases. Last week, the U.S. Office of Personnel Management (OPM) revealed that they had been ...

Due to the way Android works, you normally need to be rooted to uninstall the pre-loaded system apps, aka bloatware, that came with your device. This is because the underlying files for these apps are stored on your system partition, which can only be modified with root-level access.

We are visual animals. So when it comes to food, presentation is everything. In deciding what to eat, certain colors and textures instantly turn us off or on. Think of runny sautéed spinach versus a salad of fresh vibrant spinach. Which one would you reach for first?

OR rather How to make the Backdoor Persistent: Hello, my Cold and Merciless Hackers,