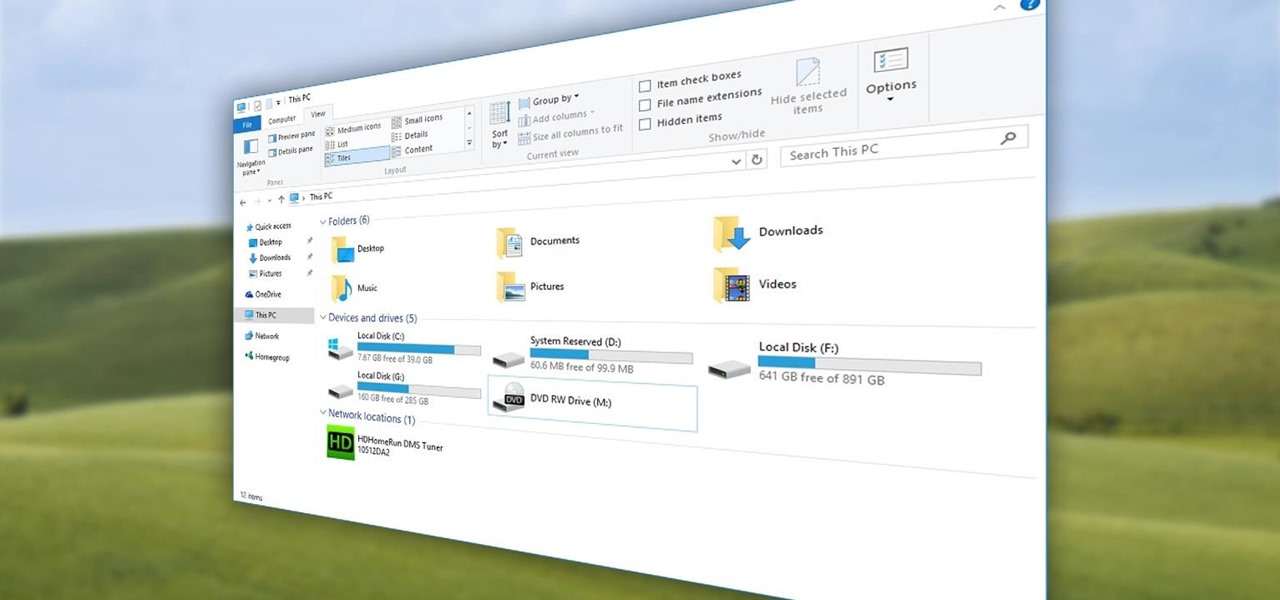
Quite a few things have changed with Windows 10, but one of the more central features that has received a makeover is the old Windows Explorer program, which has been renamed to File Explorer in this version.

One of Android's biggest strengths, when compared to other mobile operating systems is its open file structure. Google introduced a built-in file manager with Marshmallow that provides basic file management, but like with most apps on Android, there are alternatives. Third-party file managers are readily available, providing deeper access and control of all your files.
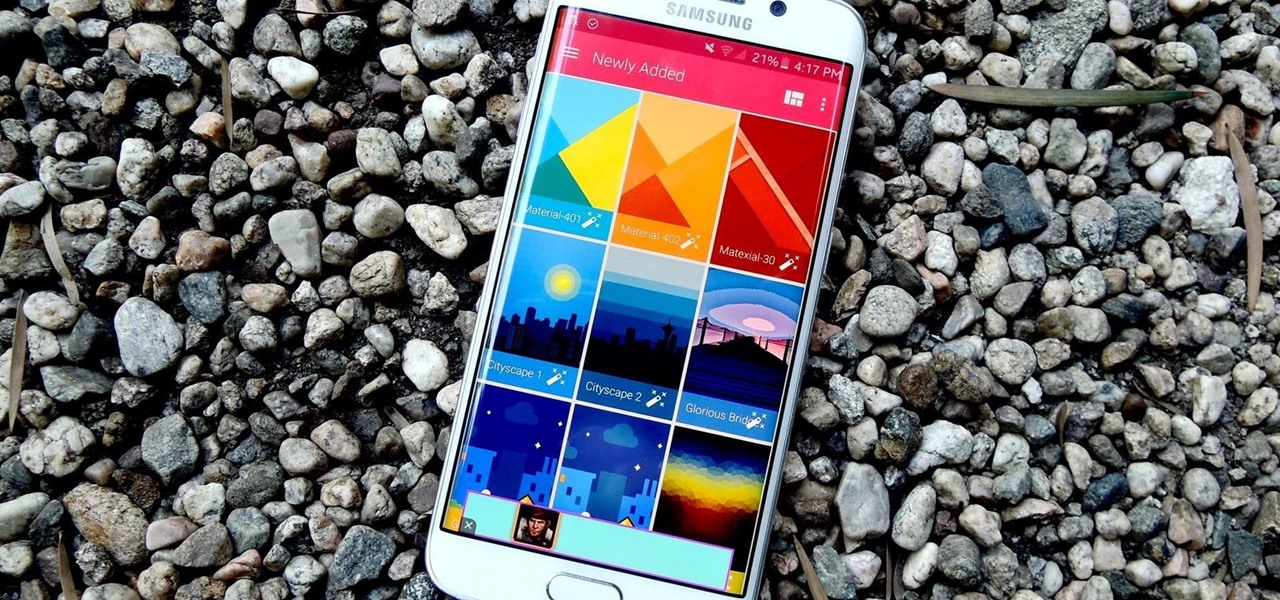
Out of all the questions that we receive from our readers and viewers here at Gadget Hacks, the most frequently asked one is "What wallpaper is that?" On occasion, our wallpapers may be personal or images from the web, but for the most part, they come from dedicated wallpaper apps.

We are visual animals. So when it comes to food, presentation is everything. In deciding what to eat, certain colors and textures instantly turn us off or on. Think of runny sautéed spinach versus a salad of fresh vibrant spinach. Which one would you reach for first?
Android has a system-wide user dictionary file that any third-party keyboard can utilize, if it so chooses. This file contains all of the words that you've added to your keyboard manually, and of the big-name players, Minuum, TouchPal, and the Google Keyboard call on this file to determine their user dictionaries.

With the sheer amount of photos, videos, and miscellaneous files we place on our computers, proper organization becomes necessary. Not only so that we can quickly get to a file when it's needed, but also to declutter folders and keep them from looking like random file dumps.

Welcome back, my nascent hackers! In previous tutorials for my Wi-Fi Hacking series, I have shown you how to crack WEP and WPA2 passwords, break a WPS PIN, and create Evil Twin and Rogue access points. In this continuation of the series, let's look at slightly different approach to attacking wireless.

Like most people who cook in a small kitchen, I'm very wary of adding anything to my drawers and cabinets unless I'm sure it's going to be essential to my cooking arsenal or that it can be used in multiple ways.

First, I want to give credit to the author where I first found how to do this: Astr0baby's Blog. This article was dated, so I took the script on his page and reworked it to make it work today. (I also included the way to make it hide the cmd line popup.) Requirements

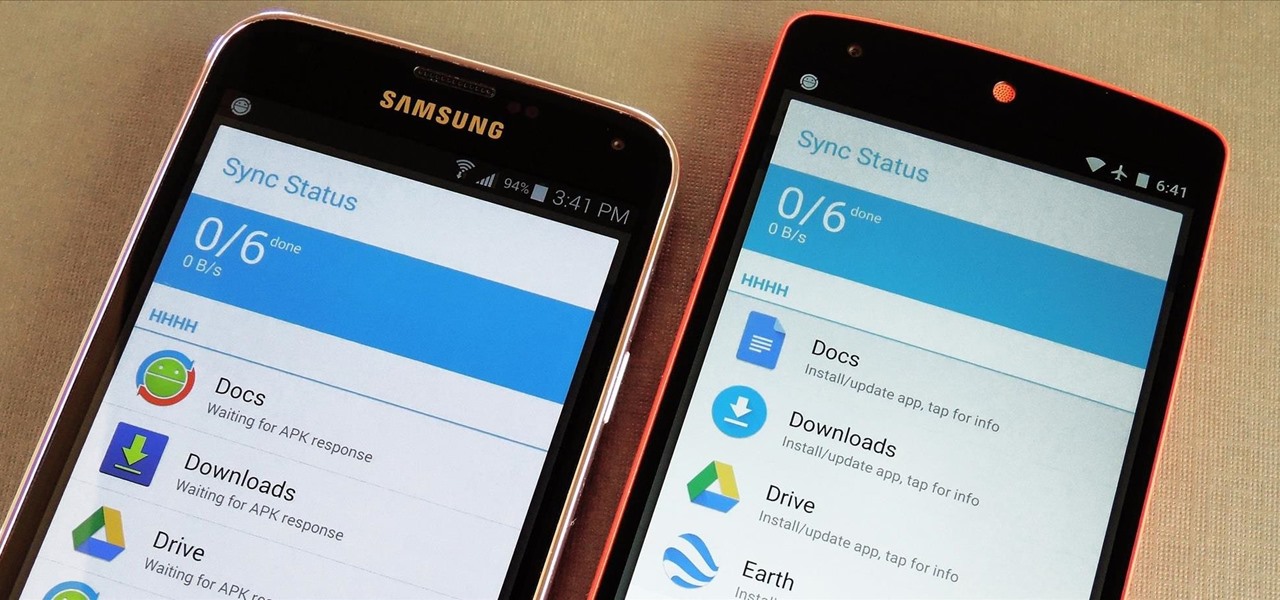
If you own multiple Android devices, you're surely familiar with the struggle of keeping apps and games in sync. While games with proper Google Play Games support will indeed sync progress across your phone and tablet, many developers neglect to include this feature in their wares.

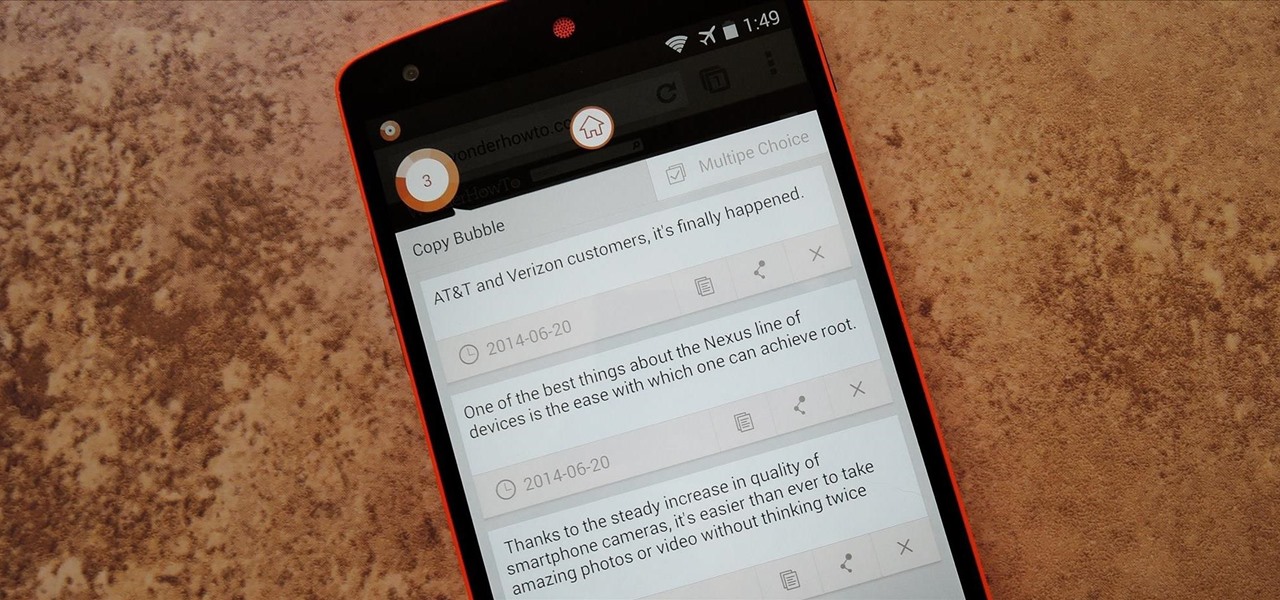
Using a combination of my phone, laptop, and an arsenal of apps and plugins, I can send pretty much anything to my Chromecast. However, nothing is ever perfect, and the file type that was still giving me headaches were torrent and magnet files.

Welcome back, my greenhorn hackers! In previous Wi-Fi hacking tutorials, I have shown you ways to create an Evil Twin, to DoS a wireless AP, and to crack WEP and WPA2 passwords, but in this tutorial, I will show you something a little bit different.

Alas, I have never tasted an authentic cronut (croissant-doughnut hybrid) from Dominique Ansel's NYC bakery, only its Los Angeles knock-offs. Ansel is also the guy who created a chocolate chip cookie shot glass and the flambéed ice cream s'more, so clearly he has some sort of dessert-perfecting gene the rest of us lack.

Welcome back, my novice hackers! Before we try to attack a website, it's worthwhile understanding the structure, directories, and files that the website uses. In this way, we can begin to map an attack strategy that will be most effective.

Can you cook a steak or salmon filet that's straight out of the freezer and get good results? Ordinarily, I would say no. Usually your steak ends up a sad grey mass fit only for the family dog and the fish is burned on the outside with an icy, undercooked center.

Not too long after getting a new device, you probably start installing any and all apps that seem fun and interesting. But after having used the device for a considerable period of time, those extraneous apps begin to take their toll.

Text input on a touchscreen device is constantly evolving. From early beginnings of pecking out each individual character to today's predictive text and gesture keyboards, we've already come a long way.

Old habits die hard. It may be a cliché, but it's undeniably true, especially when it comes to the bad ones. Nail-biting, fidgeting, and overspending can label you as someone who is obsessive-compulsive, overly nervous, and routinely stressed out, but you can make the break less painful with a few simple tweaks to your routine and by understanding how your habits work.

Welcome back, my greenhorn hackers! Lately, much of the discussion here on Null Byte has revolved around evading detection and not getting caught hacking. Several of you have written me asking for a series on evading detection and forensics, and while I began a series 5 months ago on just that, we have changed hacking platforms from BackTrack to Kali, which has a much more highly developed forensic toolset.

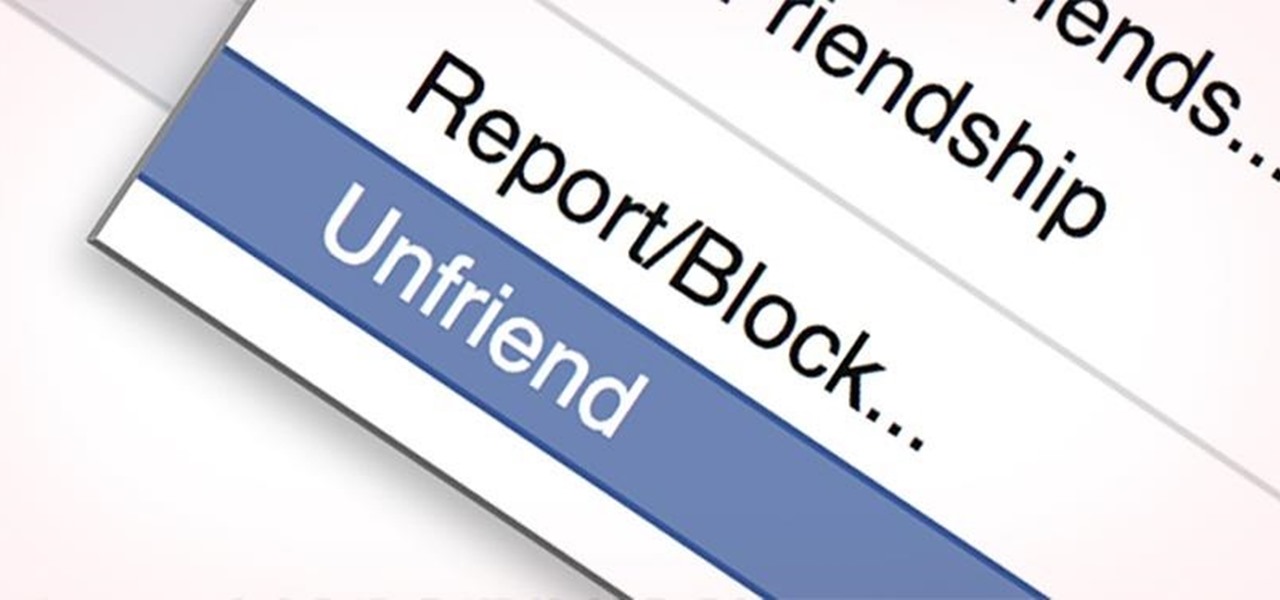
Admit it: you haven't talked to more than 70 percent of your Facebook friends in the last year. Whether you barely know the names crowding your friends list, or have vague memories of high school Spanish class with them, Facebook friends are easy to find and difficult to get rid of.

To flip, or not to flip, that is the real question. When you're nervously standing over the stove or grill, what do you do with that steak before you?

Google's new camera, aptly named Google Camera, has been all the rage since it was released onto Google Play last Friday. The main reason is the amazing Lens Blur feature that adds depth-of-field Lytro effects to photos, without the use of any expensive accessories or extra hardware, like on the new HTC One M8. The camera does this by utilizing a depth map through the processing of multiple images. Frame your photo, move the camera (phone) in an upward tilt or motion, and the software capture...

If you're as bad at locking your Nexus up as I am, you have the "slide" option set for your screen lock. It may not be the most secure option, but it's definitely the easiest way to unlock your device while being able to utilize lock screen widgets.

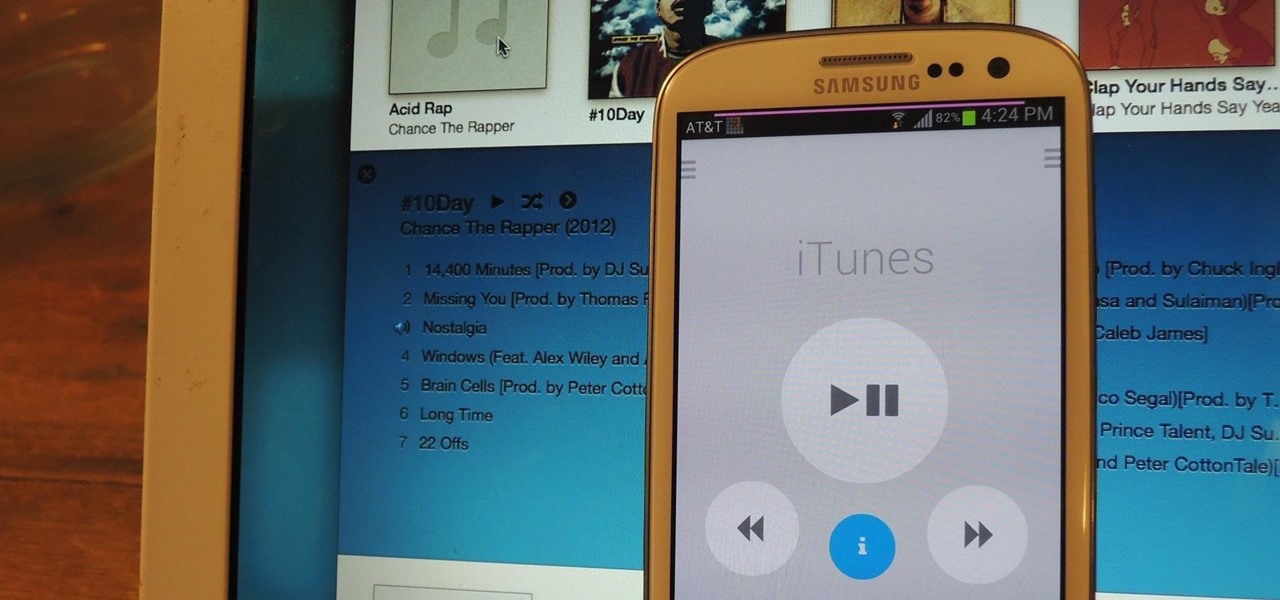
Dropbox, the cloud backup tool that is a mainstay on many of our devices, has added two companion apps to its service. Earlier today, we showed you a glimpse into a new testing version of the Gmail app, with features like pinning and snoozing to keep your inbox in check. Now, Dropbox has released Mailbox for Android, about a year after they purchased the company and its iOS app, with a simple goal: taming your inbox.

I still remember when I had to get up from my comfy spot on the couch to change the channel on my old television. So for me, the remote control may be one of the most underrated inventions of the last century. These days, remotes take on all sorts of shapes, not just the typical brick, but also in the form of watches and cell phones.

Mobile scanning applications are nothing new in the world of Apple, except that the majority of them usually come with pesky in-app purchases that stifle the entire experience and render some features useless until you pay for them.

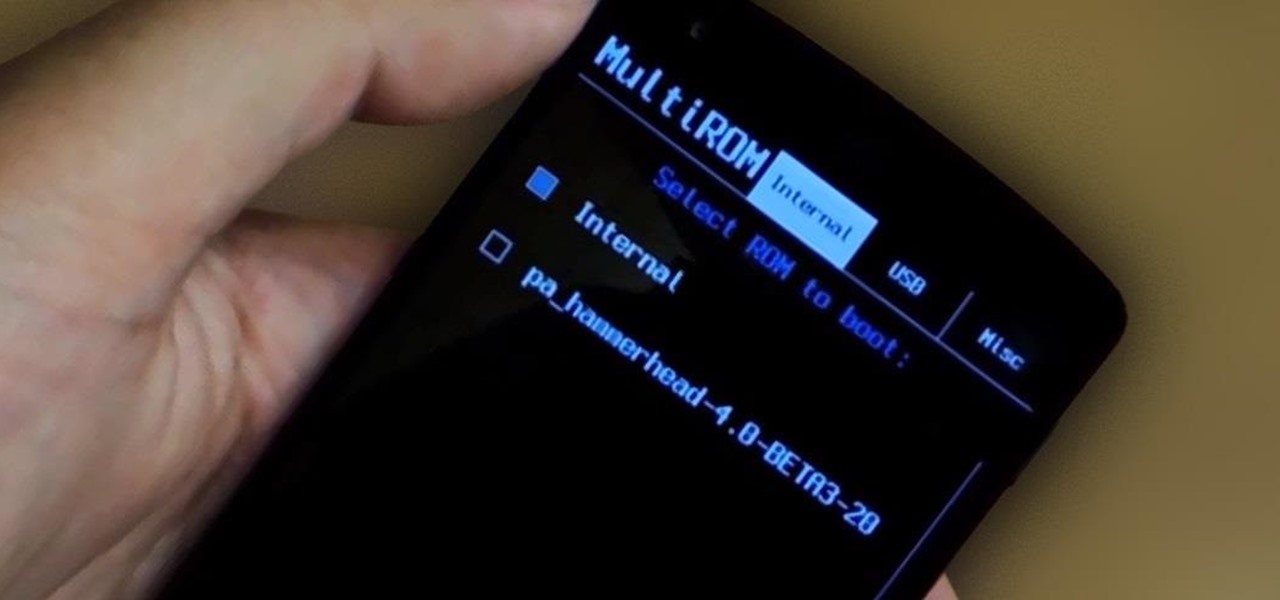
When you enter the softModder realm by rooting your Nexus 5, you open up an exciting world of possibilities and deep customizations for your device. Among other things, it gives you the ability to flash custom ROMs which, individually, act as entirely different operating systems that can vastly alter your user experience.

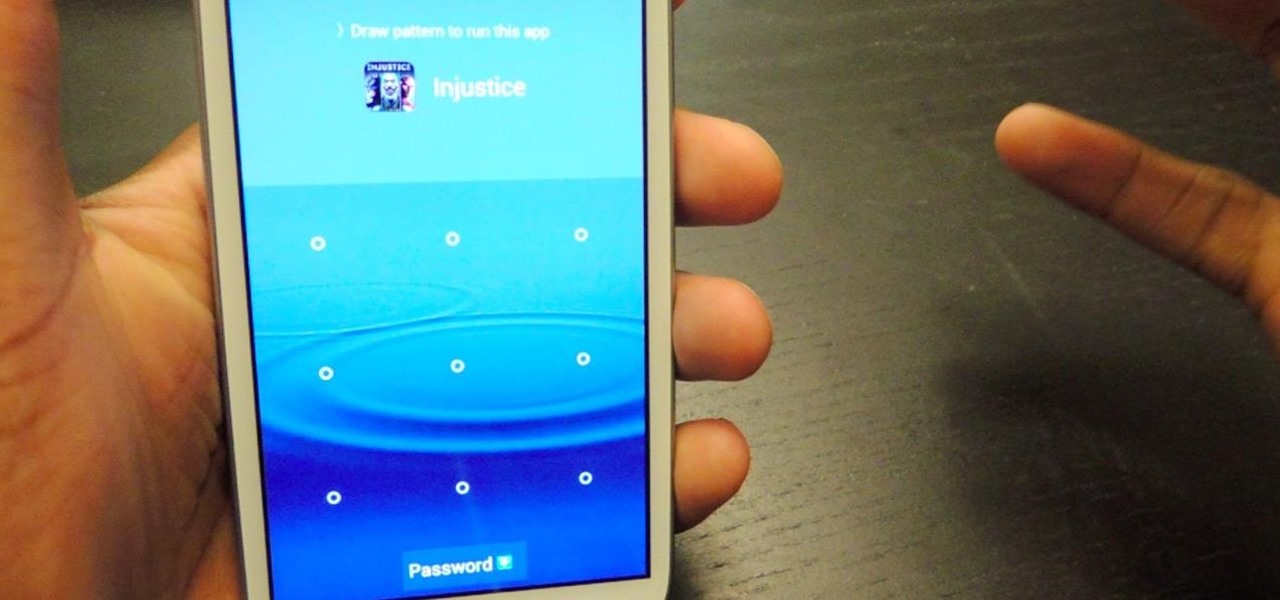
Keeping unwanted clowns off on my Samsung Galaxy S3 is priority number one. I've shown you how to snag a picture of people opening your apps and how to lock your screen for whenever you hand off your phone, allowing them to access only the page you left open.

Automation applications bring the future a little closer. If you've seen Minority Report or other futuristic sci-fi movies, the intrigue of having your electronics work independently is something we can all appreciate.

Welcome back, my fledgling hackers! If you're like most aspiring hackers, at one time or another you've probably spent too much time playing Call of Duty and not enough time preparing for your final exams.

Welcome back, my fledgling hackers! In one of my recent articles, I showed you how to install BackTrack as a dual boot system on a Windows computer. In this tutorial, I will walk you through BackTrack, giving you a tour of the most salient features for the hacker-to-be.

Unwanted advertising is everywhere. Annoying pop-up ads, overly loud late night commercials, spam...it never ends. And before spam, there was junk mail. Junk mail is even worse because unlike TV commercials and internet ads, it's physical. You can't just delete or ignore it—and it's an awful waste of paper. So what can you do about it?

Do you ever wonder how all these celebrities continue to have their private photos spread all over the internet? While celebrities' phones and computers are forever vulnerable to attacks, the common folk must also be wary. No matter how careful you think you were went you sent those "candid" photos to your ex, with a little effort and access to public information, your pictures can be snagged, too. Here's how.

Want to take vibrant photographs like this one? You won't find this filter in Instagram, and that's because it's a little more difficult than just slapping a digital filter on a solo photo. The extra RGB colors are created using a special strip device called the Harris shutter, invented by Robert Harris of Kodak.

Welcome back, hacker novitiates! In the next few hacks, we will be breaking into Windows servers. In this installment, we will learn to add ourselves as a user to a Windows 2003 server. Of course, when we have added ourselves as a user, we can come back any time and simply log into our account without having to hack into the system and risk detection.

Relays are simple redstone devices that allow you to switch between multiple outputs with only one input. They're incredibly useful in the right situation!

Firstly, let me say a few quick things: Once built, this is a lazy (one button) way to harvest melons, but this is going to be a complex and lengthy build.

This article is a guide for making Chainmail Armor from start (simple wire) to finish (a finished chainmail shirt). We will be using the European 4 in 1 weave, as this is the most common weave. This is the weave that you usually see in movies. There are several sections to this guide: Materials, Making the Rings, Weaving the Rings, and Making the shirt.

Remember summer camp? Remember the smell of the log cabins? The feel of the treated wood? Well, you can create something for your home that's perfect for a nostalgic summer camp aesthetic. Meg Allen Cole (recently of Threadbanger) was inspired to make this mid-century modern wall hanging piece made from a small wooden log (or branch) when she was at a relaxing, wooded vacation spot in Maine. And she shows you how to make one, too!

This how to video will give you ideas on how to make a sandwich that looks like a sailboat. Preparing this sailboat sandwich is a fun activity to do with kids. Watch and learn how it done.