Intel, the company which is mostly known for creating computer processors, once again showed off their Project Alloy "merged reality" experience, this time during their CES 2017 press conference. Intel's Chief Executive Officer, Brian Krzanich, stated that they will be "productizing" this tech with their partners in the fourth quarter of 2017.

For some time now, there has been quite a bit of speculation as to when the selection of augmented and mixed reality head-mounted displays would begin to trickle out to the public. Pricing, availability, and software selection are all issues that will have to be addressed before widespread adoption will start.

Cyanogen, Inc., the for-profit company that spun off from its CyanogenMod roots several years ago, has announced that they're shutting down all of their services. The company's impending demise shouldn't directly impact many Android users, but the announcement does have one major repercussion: The servers that used to host the popular CyanogenMod custom ROM have now been shut down.

Bluetooth 5 was announced and made officially available on December 7, 2016. It comes with a handful of improvements to speed, range, maximum device connectivity, and anti-interference from other nearby devices. While this might be great for those special few who use Bluetooth on a daily basis to send and receive (or steal) data, what about the average Joe?

Selecting text on a touchscreen device has always been a major pain point. Those tiny little arrows that let you adjust the selection area are always too hard to actually adjust, making precision all but impossible. Then there's the issue of some apps not even allowing text selection in the first place, so the entire experience is basically a big mess.

Before the iPhone 7 models were released, there were many rumors pointing to the inclusion of wireless charging, which obviously didn't happen. Now the rumor mill is back at it again for Apple's next smartphone, most likely being called the iPhone 8, and the possibility of wireless charging is more certain this time.

Starting with Marshmallow, Android added a built-in theme engine called "Runtime Resource Overlay," or RRO. This theme engine was intended to be used only by smartphone manufacturers, not end-users, so unlike Cyanogen's CM Theme Engine, owners can't use it to change the look and feel of their phones.

Forget headphone jacks and "Courage." Look past the shiny Jet Black finish and beyond the minimized antenna lines. Sure, quad-LED flash and dual cameras are nice—but dual-SIM would've been much better.

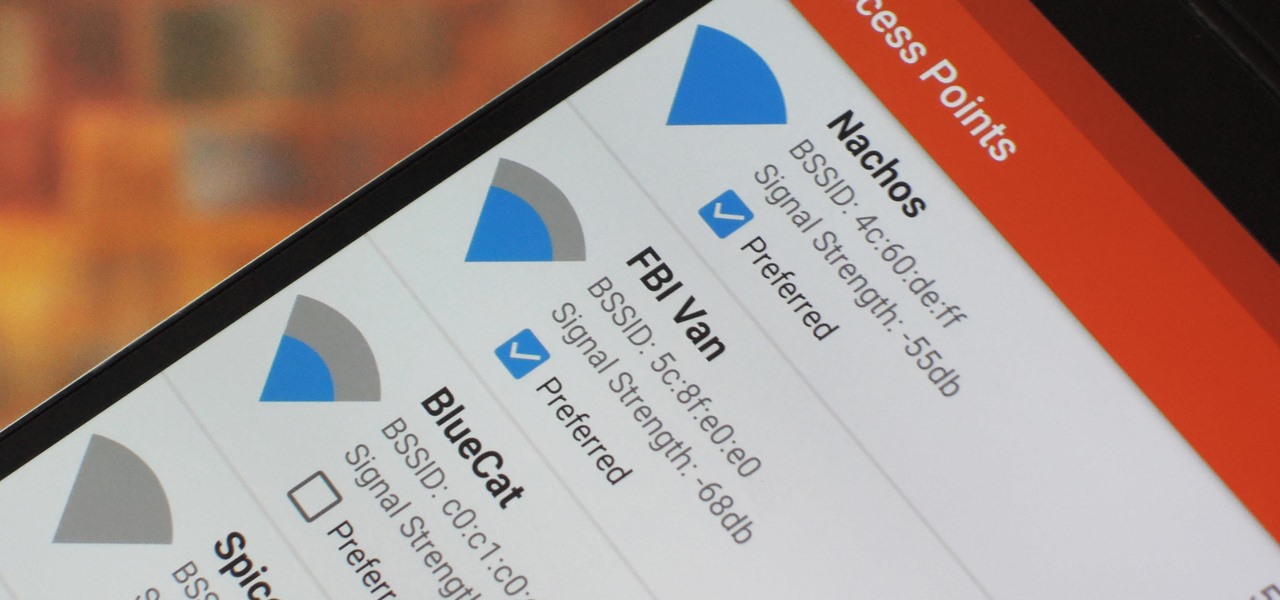
Wi-Fi signals have limited range, so if you live in a two-story house or work in a larger office, you may have set up multiple routers or repeaters to ensure full wireless coverage. Sadly, Android handles the transition between networks pretty poorly.

Things are definitely starting to shape up with iOS 10. After three developer betas of the upcoming operating system, Apple has begun rolling out the developer beta 4 release for iPhone, iPad, and iPod touch, which focuses mostly on refining some of the cool new features.

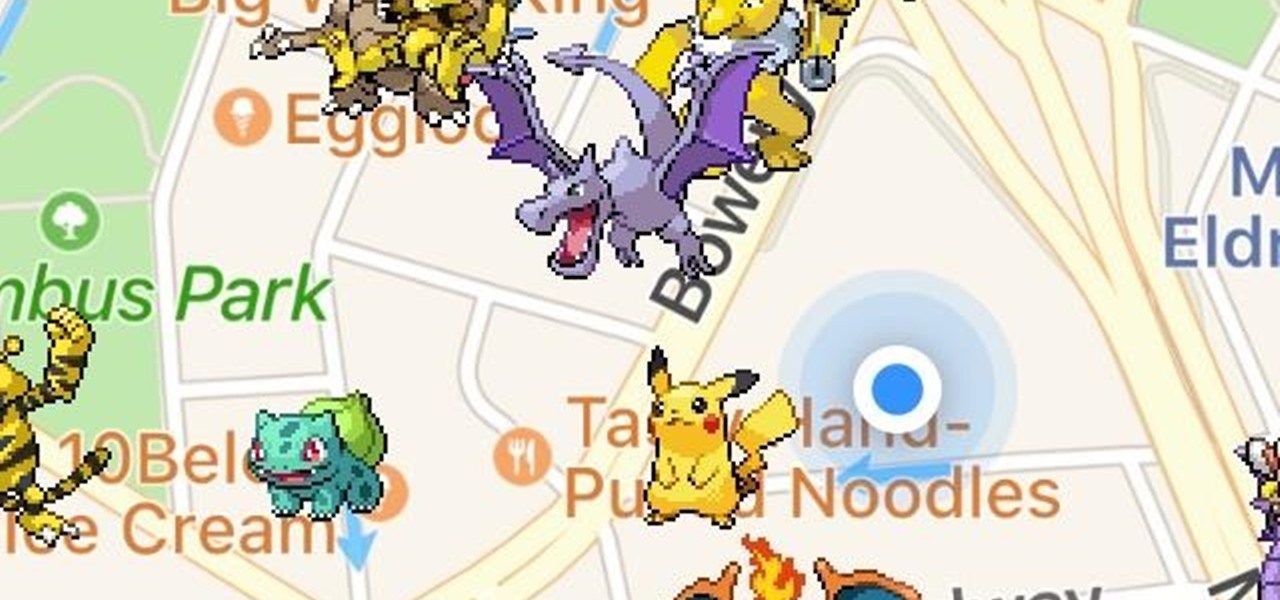
The only way to know which Pokémon are in your area in Pokémon GO is the cryptic "nearby" list, which sometimes doesn't work—and also doesn't tell you which direction to head off to hunt that Pokémon you're looking for.

Hash browns are a breakfast staple and for good reason: they're simple, salty, and crispy, and so delicious that you can easily down several servings of them in one sitting. Basically, they're the French fries of breakfast.

Not content with bringing the first untethered mixed reality headset to market, Microsoft wants to expand their Windows Holographic operating system beyond HoloLens into vastly more robust technologies.

Eggs bring life to almost any dish. Toast with avocado? Put an egg on it. The same old salad you eat for lunch everyday? Put an egg on it. Stir fry leftovers? Put an egg on it.

My first time opening a coconut was a confusing and frustrating experience. I remember the loud echoing noise as I hit it with a knife, a hammer, and my countertop. It took multiple tools, YouTube videos, and plenty of angry sighs for me to get it open.

When a craving for crunchy tacos hits, it's undeniable. Don't Miss:

If history holds true, we'll see the iPhone 7 arrive this September, and just like many times before, there are already a ton of rumors about its features. As usual, many claims are pure speculation, but there are some trustworthy reports and lots of good information we can use to make some educated guesses regarding Apple's upcoming flagship.

Welcome back, my budding hackers! In this series, I have been trying to familiarize you with the many features of the world's best framework for exploitation, hacking, and pentesting, Metasploit. There are so many features, and techniques for using those features, that few pentesters/hackers are aware of all of them.

When it comes to proper tomato storage, conventional kitchen wisdom (and Alton Brown) state that tomatoes are best stored at room temperature—not in the refrigerator. Supposedly, refrigerated tomatoes develop a mealy texture and lose their flavor if they are exposed to cooler temperatures over time.

You can use the F1 key to notably dim your Mac's display, but sometimes that just isn't dark enough. If you're working in pitch black conditions, have a migraine or tired eyes, or just want a more comfortable environment, you might want your screen even darker—without making it pitch black.

This is a how to to change any user password on a windows 7 computer. If you forgot your password you can change any account password even if you are locked out of your account.

Now is the time to act if you've been in the market for some must-have Android apps but felt like the price was a little out of your range. The Google Play Store is running a sale so you can pick up some high-quality paid apps—including the popular Nova Launcher Prime and Poweramp Music Player, among many others—for just $0.99 each. While there are quite a few solid apps here you should try—and with a two-hour refund window, why not try them all—here are our favorites you should seriously con...

Although lots of the bigger hotel chains are lessening the restrictions they put on their room TVs, some smaller ones are still taking measures to prevent you from plugging in computers or streaming devices into an HDMI port. However, there are a few steps you can take to bypass these restrictions and watch your own media in a hotel that has restricted TVs.

Many of us are guilty of sacrificing a delicious breakfast for a few extra minutes of sleep in the morning during the busy work week. Grab-and-go breakfasts are definitely timesavers, but granola bars and other packaged items often lack the fresh breakfast feel that makes the first meal of the day so great.

How much you've actually spent and how much you think you've spent are usually two completely different results, and is especially true on Amazon when it's so easy to click and buy. You might think you've given Amazon a couple thousand over your lifetime, when the fact is that it's three or four times that amount.

In my household, we are frugal and somewhat picky eaters, so we have to be a little creative with the things we buy. We like to purchase items that can be used in multiple dishes to reduce cost—and because it's just more practical. Pancake mix is a favorite because it can be used in various dishes where any type of breading may be involved. To help inspire you, here are some of my favorite ways to use pancake batter at home.

A crick is a sudden, spasmodic pain and stiffness in the neck caused by tight muscles that can absolutely ruin your entire day. It can last for more than one day and can be triggered by the smallest movement of the neck, such as a simple pandiculation, aka a yawn-stretch. Although you can't always prevent them, there are many natural ways to lessen a painful stiff feeling in the neck.

Welcome back, my hacker novitiates! Often, to hack a website, we need to connect to and exploit a particular object within said website. It might be an admin panel or a subdirectory that is vulnerable to attack. The key, of course, is to find these objects, as they may be hidden.

Welcome my aspiring hackers and programmers! Today i will introduce you to a programming language that as a hacker you should have in your set of hacking/programming skills (except if you're only interested in web hacking/programming...then you should go learn some html or PHP instead of C#).

How's it goin'? In this tutorial, we will learn about the security issues of the popen and system functions. I've seen a few people attempting to run command line utilities or whatever it is they require with calls to these two functions but may not know the security implications which come along with it. I will show you using an example from the wargame IO Smash The Stack.

Hello again! In this tutorial, we are going to go over something called "operators" which will help us build upon conditions of control structures and also some variable manipulation. Without further ado, let's dive in!

Welcome back to another C tutorial, this post covering the first part of control structures, if statements. Let's get right into it.

The morning started out like most of them do: I was hungry, and it was time to chow down on some breakfast. However, this particular morning had me craving something besides the usual milk and cereal.

Microsoft's "Fall Update" to Windows 10, code named Threshold 2, has a lot of new tricks up its sleeve. It's the biggest update we've seen since Windows 10 was released this summer, and it's rolling out to all users right now.

It might be difficult to admit, but a lot of us are probably guilty of lurking on Instagram profiles, whether it be an ex you've been keeping tabs on or someone cute you literally just met.

Greetings dear null byters, today we start a new series, we will start to attack users using social networking that are popular such as Facebook, Skype, and much more, and in part 1 of the series will engage users of Skype.

With new messaging services being pushed out constantly, it can be a pain trying to keep track of them all on your Android device. We had previously shown how to stay on top of them all with a unified "inbox" app, but that still requires you to have each individual app installed. While looking for a true one-stop messenger, I came across Disa.

Roughly four years ago, Adobe decided to abandon development of the mobile version of their popular Flash Player browser plugin. Their excuse at the time was that this move would enable them to focus more on HTML5 development for mobile devices and allow them to put more effort into maintaining the fluidity and security of their desktop Flash plugin.

Welcome back, curious hackers! In today's tutorial, we will be diving deep into the manipulation of Google Operators, commonly referred to as "Google Dorks" in order to access Surveillance Cameras and other control panels.

Since the release of Windows 8, Microsoft has been heavily encouraging users to use Windows with a Microsoft account. According to Microsoft, the main benefit of using a Microsoft account is the ability to sign in and sync your information across various Microsoft devices and services. Furthermore, you have access to a singular cloud storage solution which can contain documents, pictures, settings, and more on whatever system you're using with the Microsoft account.