Reddit, the self-proclaimed "front page of the internet," continues to take a big bite of my free time each and every day, as well as millions of its other users'. The clicking and scrolling through page after page never gets old, but you could speed things up with a few browser extensions and double your Reddit knowledge in half the time. Here are my favorite extensions you can try out for the Chrome, Firefox, and Safari web browsers.

Preparing and serving seafood can be a daunting task. Fish is so delicate that one extra minute of heat can turn a juicy, flaky filet into a dried-out disaster. But that same fragility also allows us to use unconventional methods to chemically transform the fish into its cooked consistency.

Often, despite your favorite makeup mecca's rows and rows of endless colors, applicators, and brands, it's hard to find the perfect shade of lipstick—especially one at the price you want. Rather than resorting to what's available in stores, turn to your stovetop and a box of crayons.

Depending on your child's age, their first smartphone may be a little too open for them, or you, to handle. With essentially a world of information—both good and bad—available at their fingertips, it can seem like a huge hurdle to instill parental controls on their device.

You can beef up the security on your Mac all you want, but all the firewalls and antivirus apps in the world mean nothing when that can of soda tips over on your Macbook, destroying your laptop and all its data forever.

Google's Chromecast is quite literally one of my favorite inventions of the past five years, allowing me to kick back, relax, and enjoy the various forms of streaming entertainment it has up for grabs.

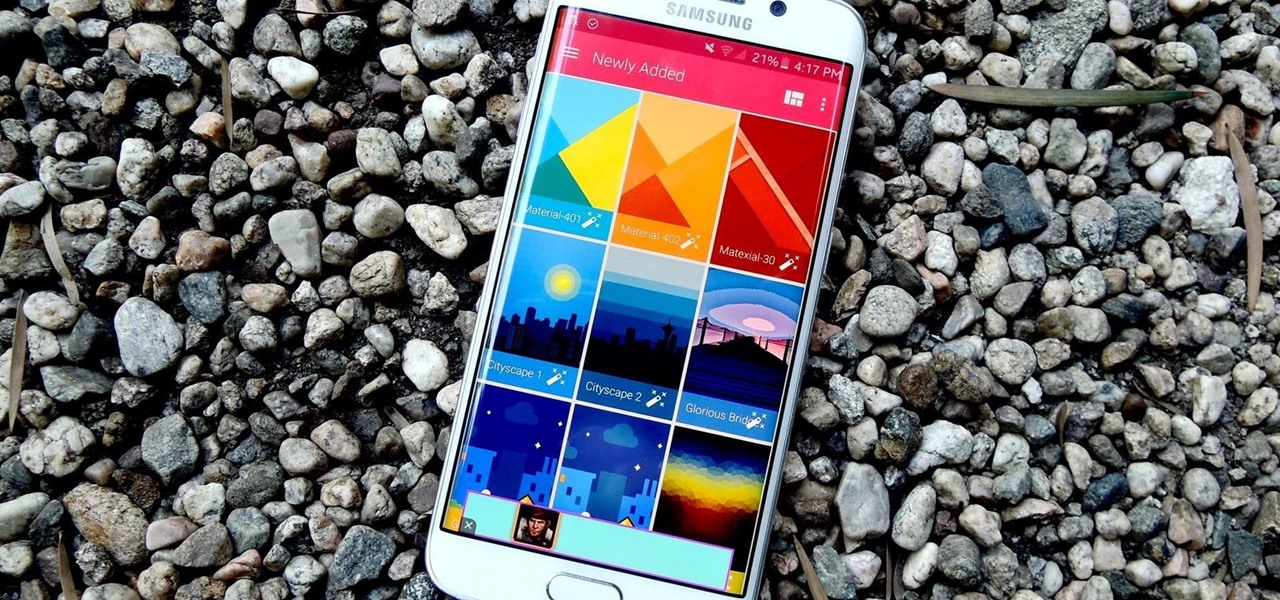
Out of all the questions that we receive from our readers and viewers here at Gadget Hacks, the most frequently asked one is "What wallpaper is that?" On occasion, our wallpapers may be personal or images from the web, but for the most part, they come from dedicated wallpaper apps.

Heads up! We've done a new, more thorough review of the best Android file-sharing apps. You can check that out here. Our old file-sharing app roundup can still be viewed below for posterity.

The right music can spur you to pick up the pace during an intense workout, pep you up before you hit the treadmill or walking path, and even encourage you to lift for just a few extra reps. Although we all have our favorite workout playlists, scientists have discovered what it is, exactly, that makes you workout harder when certain songs begin.

Welcome back, my tenderfoot hackers! One of the issues we often encounter with Metasploit is how to add new modules. Although Rapid7 (Metasploit's owner and developer) periodically updates Metasploit with new exploits, payloads, and other modules, at times, new modules appear that are not added to the Metasploit repository.

Apple's latest update to Mac OS X, 10.11 El Capitan, is currently available in the Mac App Store for everyone to download and install at no cost. The new OS features Split View mode for better multitasking, a cleaner Mission Control, smarter Spotlight, a way to mute Safari tabs playing audio, enhanced Mail and Notes apps, and more.

With each day that dawns, there is a new, major hack that makes the news headlines. If you are paying attention, there are usually numerous hacks each day and far more that never make the news or are kept private by the victims. Every so often, a hack is so important that I feel compelled to comment on it here to help us learn something about the nature of hacking and IT security. This is one of those cases. Last week, the U.S. Office of Personnel Management (OPM) revealed that they had been ...

Due to the way Android works, you normally need to be rooted to uninstall the pre-loaded system apps, aka bloatware, that came with your device. This is because the underlying files for these apps are stored on your system partition, which can only be modified with root-level access.

We are visual animals. So when it comes to food, presentation is everything. In deciding what to eat, certain colors and textures instantly turn us off or on. Think of runny sautéed spinach versus a salad of fresh vibrant spinach. Which one would you reach for first?

OR rather How to make the Backdoor Persistent: Hello, my Cold and Merciless Hackers,

There's nothing in this life that we love more than making one ingredient or one food tool do multiple things. It saves money! It saves time! It makes us look smart at cocktail parties!

Welcome back, my nascent hackers! In previous tutorials for my Wi-Fi Hacking series, I have shown you how to crack WEP and WPA2 passwords, break a WPS PIN, and create Evil Twin and Rogue access points. In this continuation of the series, let's look at slightly different approach to attacking wireless.

Welcome back, my greenhorn hackers, and happy New Year! Now that your heads have recovered from your New Year's Eve regaling, I'd like to grab your attention for just a moment to preview 2015 here at Null Byte. I hope you will add your comments as to what you would like to see, and I'll try to honor as many requests as I can.

The ability to make a meal for yourself used to be one of those life skills you had to learn or otherwise you would starve, but the rise of convenience foods, takeout, and other aspects of modern living have made it entirely possible to be a grown person and not know what to do in the kitchen.

We always want to find more ways to help brilliantly lazy cooks make great-tasting food and save money and time in the process. Luckily, our Facebook fans are invaluable sources of information when it comes to getting cool tips, behind-the-scenes info, and more.

Welcome back, my nascent hackers! Like anything in life, there are multiple ways of getting a hack done. In fact, good hackers usually have many tricks up their sleeve to hack into a system. If they didn't, they would not usually be successful. No hack works on every system and no hack works all of the time.

I've previously shown a few ways to make your iPhone a little more unique by customizing app icons on the home screen, and while those processes did not require a jailbreak, they were a pain in the ass. Thankfully, there's a better way to customize app and shortcut icons that's a lot less convoluted.

We've already seen the visual changes that Android 5.0 Lollipop has brought to the table, but Google spent just as much time altering things under the hood. Awesome new functionality and hardware capabilities have been added left and right, and with the OS already out now, it's high time we had a look at some of these tweaks.

Welcome back, my greenhorn hackers! In previous Wi-Fi hacking tutorials, I have shown you ways to create an Evil Twin, to DoS a wireless AP, and to crack WEP and WPA2 passwords, but in this tutorial, I will show you something a little bit different.

Google's Android L developer preview has given Android a more refined look, with developers excited to update their apps with the new Material Design UI. While some apps are slowly getting updated, QKSMS (QK for quick) is a 3rd-party text messaging app that was built with Material Design in mind.

Welcome back, my novice hackers! Before we try to attack a website, it's worthwhile understanding the structure, directories, and files that the website uses. In this way, we can begin to map an attack strategy that will be most effective.

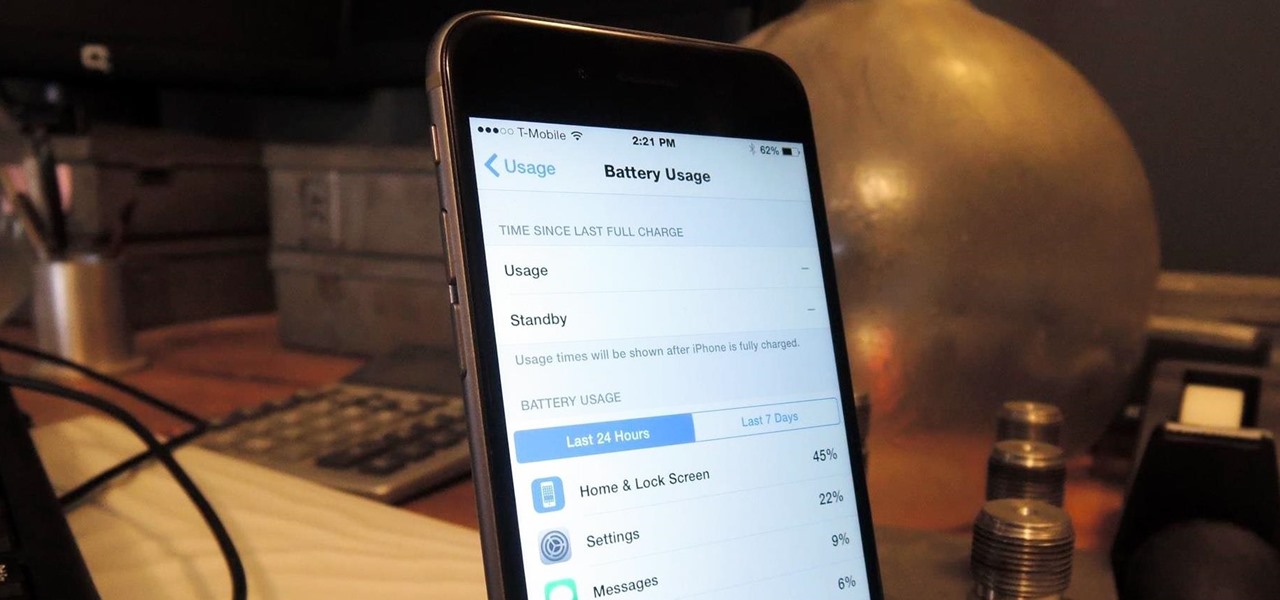
The new iPhone 6 and 6 Plus are supposed to last a lot longer in your pocket with improved battery life, but that doesn't mean that iOS 8 will be that friendly on your older iPhone model. All of those awesome new features could be killing your battery, but with some simple tweaking, your battery life concerns will be a mere afterthought.

Because of Android's massive array of supported smartphones that carry vastly different display sizes and resolutions, the operating system uses a value known as DPI to determine the size of icons and visual assets that will best suit a given screen.

Can you cook a steak or salmon filet that's straight out of the freezer and get good results? Ordinarily, I would say no. Usually your steak ends up a sad grey mass fit only for the family dog and the fish is burned on the outside with an icy, undercooked center.

Welcome back, my hacker apprentices! Last week, I started off my password cracking series with an introduction on the principles and technologies involved in the art of cracking passwords. In past guides, I showed some specific tools and techniques for cracking Windows, online, Wi-Fi, Linux, and even SNMP passwords. This series is intended to help you hone your skills in each of these areas and expand into some, as yet, untouched areas.

Welcome back, my budding hackers! When we are looking for ways to hack a system, we need a specific exploit to take advantage of a certain vulnerability in the operating system, service, or application. Although I have shown you multiple ways to exploit systems here in Null Byte, there are still many more exploits available that I have not yet shown you.

With all of the personal data that's stored on our smartphones, it's of vital importance that we have some sort of lock screen security enabled. One of the Galaxy S5's killer features is obviously the fingerprint scanner. It makes the process of dealing with a secure lock screen a bit easier than typing in a password or PIN.

There are over 60-something Android apps cluttering my app drawer. While I'm constantly on the look out for new mods and apps to install, the default way of managing them is cumbersome and just feels unintuitive. I mean, who on Earth would wants to individually manage each app on their device?

If you're like me, you spend a lot of time on your computer, which can be damaging to your eyes in the long run. Studies have shown that staring at a computer screen or television up close for extended periods of time can have harmful effects on your vision.

Welcome back, my novice hackers! In a recent tutorial, I showed you how to use shikata_ga_nai to change the signature of a payload to evade detection by security devices (firewalls, IDS, etc.) and AV software.

Welcome back, my greenhorn hackers! My preference for Linux as a hacking platform is well documented, and I have even created a series of tutorials to train new hackers. Without being proficient in Linux, you can't really call yourself a hacker.

The late, great writer Laurie Colwin once wrote that if she were allowed to have only one fruit in her kitchen, she would always choose lemons (or limes, since they can often be used interchangeably).

I own two aprons—a cute one for company, and another for the hard-core cooking duties, like cutting up chicken and making stock. The sad truth is that I almost never remember to wear either of them. So, much of my clothing ends up spattered with grease, liquid, and bits of fruit and vegetable. While stain-removing sprays, sticks, and pens are all effective to a certain extent, they have two drawbacks—they're expensive and sometimes I need to use them in large quantity, like when a piece of eg...