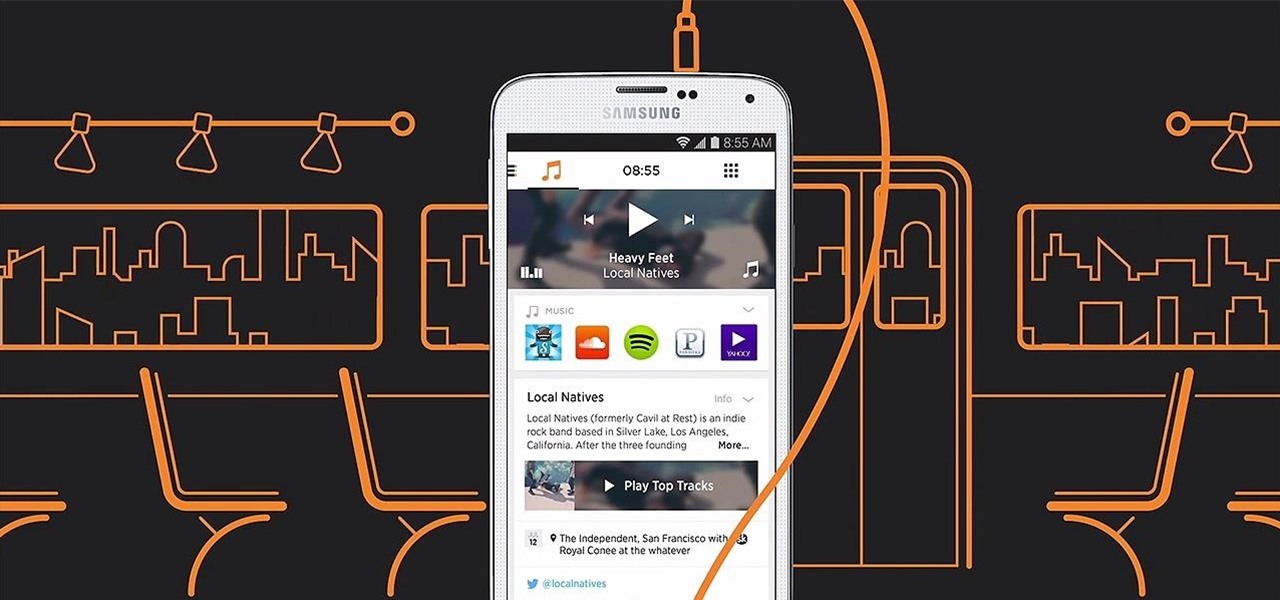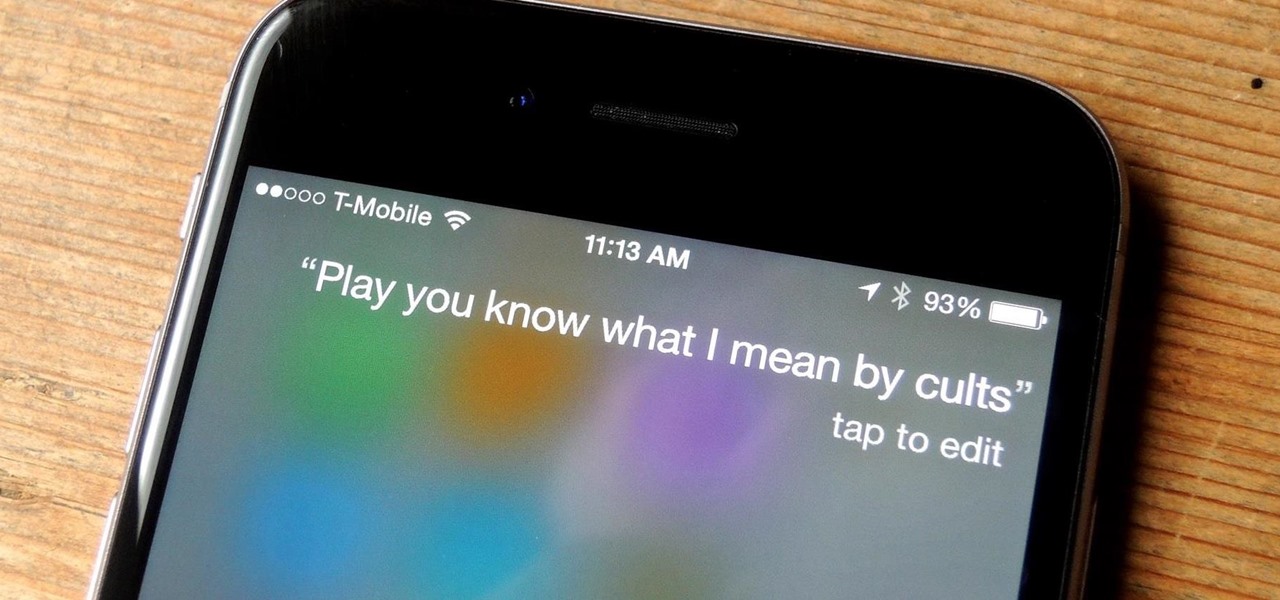
Spotify lets you use Siri commands to play and control music on your iPhone, but it wasn't always like that. It only applies in iOS 13 and later, so if you're on an older iPhone model with an older iOS version, you can use a really complicated workaround in iOS 12 or try a jailbreak tweak on older firmware.
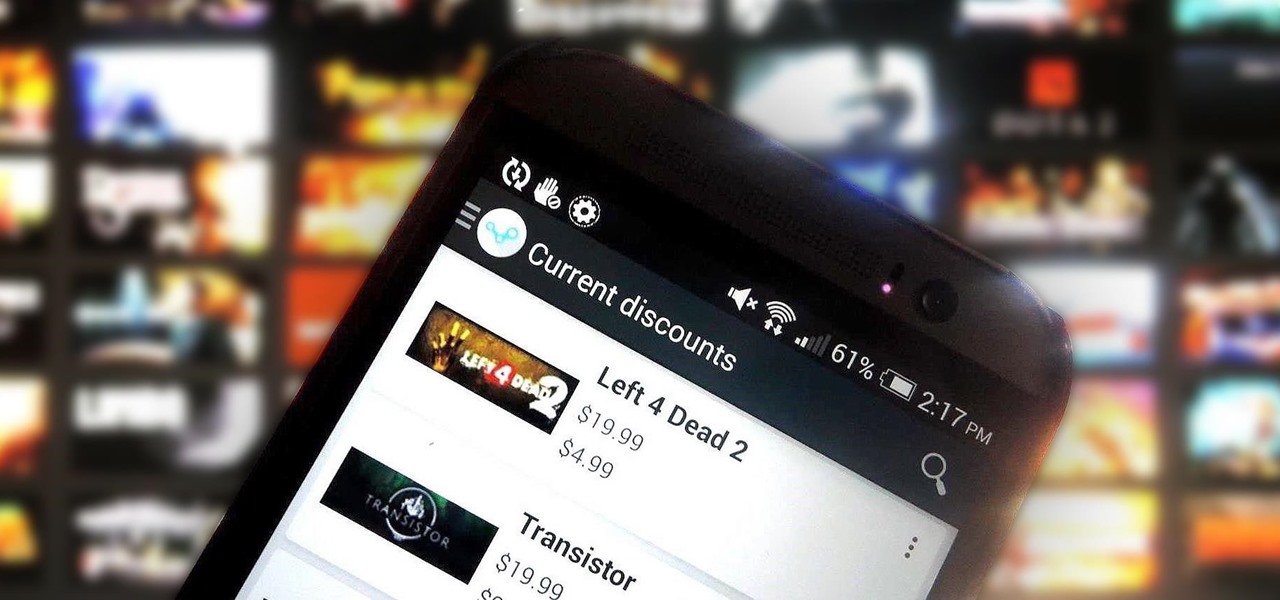
Steam is by far the biggest and best service for getting games on your Linux, Mac, or Windows PC. With their catalog containing everything from the biggest blockbusters to indie games created by one-man development teams, it's no easy task to keep track of their best values—until now.

With developments from tech giants Apple and Samsung being shared throughout the interwebs, the term smartwatch has become increasingly popular over the last year. That being said, smartwatches have been around for a while.

Only scumbags hide their call and message history, right? Wrong. While it may seem like a tactic for the unfaithful, it's still a good thing to do for certain contacts on your phone that you don't want to block outright.

Reddit is home to tons of fun and unique content. A starting point for the various memes and videos that eventually make it into your Facebook feed, you could seriously spend all day just browsing different subreddits and not get bored.

If you're like me, then you've got an incredibly complicated Wi-Fi password with uppercase and lowercase letters, numbers, and special characters.

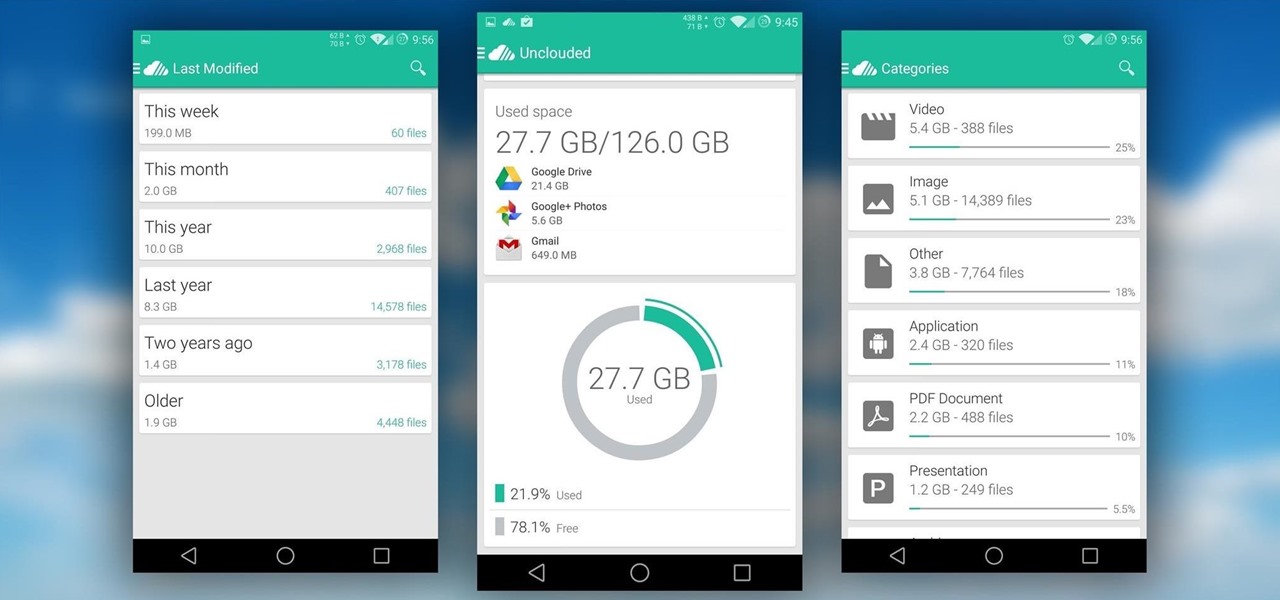
It seems like every cloud service out there is offering tons of upgrade options and free promotions to give people as much space as they need to store their files online. I personally have over 100GB of Google Drive space which is shared between multiple computers, phones, and tablets, so keeping track of everything can be a huge pain in the ass.

When Yahoo! purchased the home screen replacement app Aviate back in January, many were wondering if the internet giant intended to continue development of the launcher or if the transaction was just another acqui-hire.

Now that all variants of the Galaxy S5 have finally been rooted, we can start exploring all of the tweaks and hacks that Superuser privileges open up to us.

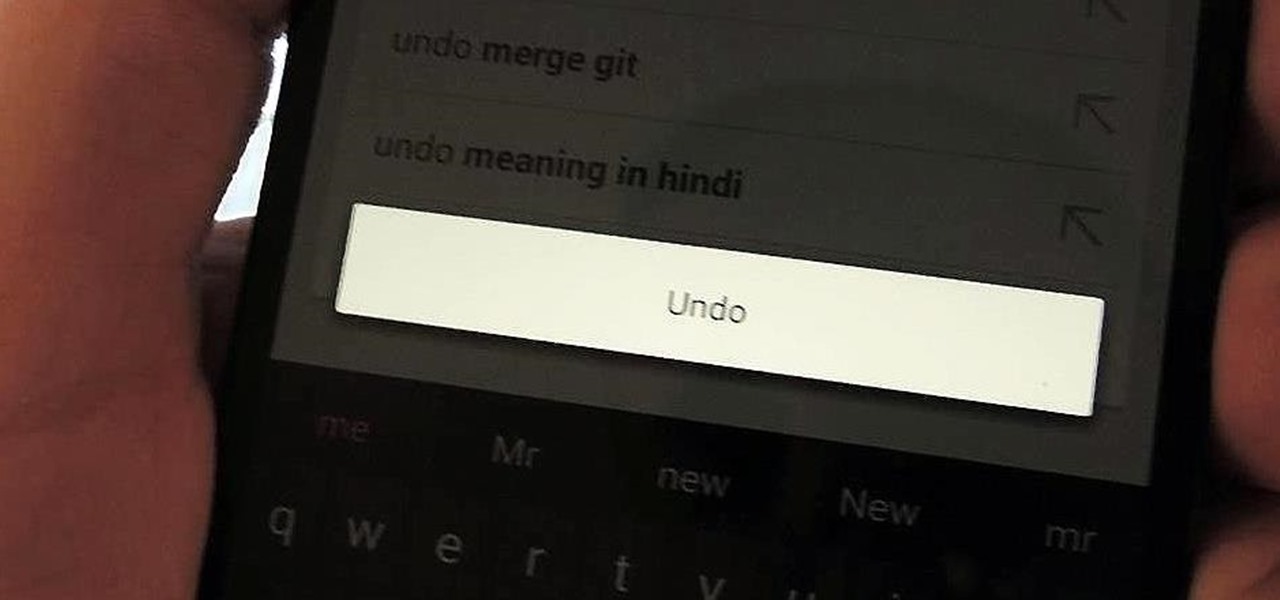
Over the years, we've probably all complained at some point about Android's lack of an "Undo" feature. When you're typing something out, there are times when you might want to go back a step.

Earlier this morning, Twitter announced (through a tweet, naturally) that it has acquired Cover, roughly a minute after Cover made the same announcement. Cover Lock Screen, a lockscreen replacement app, has been vastly popular during its first year. The app places relevant shortcuts on your lockscreen that adapt to your habits, so whether you're at home, work, or in the car, you'll find the apps you use the most in these situations readily available for you. For more information on Cover, inc...

If you lend someone your phone, even if it's just for a second, there's a chance they can enter an app and see something you'd rather they didn't. Whether it's a personal email or a private photo, there are plenty of reasons why you'd want to keep snoops out of certain apps.

Amazon just announced its entry into the set-top streaming content marketplace with its new Fire TV box. Competing directly against Apple TV, Google's Chromecast, and Roku, Amazon is betting on big processing power and voice controls to stand out from the competition. Features include the following.

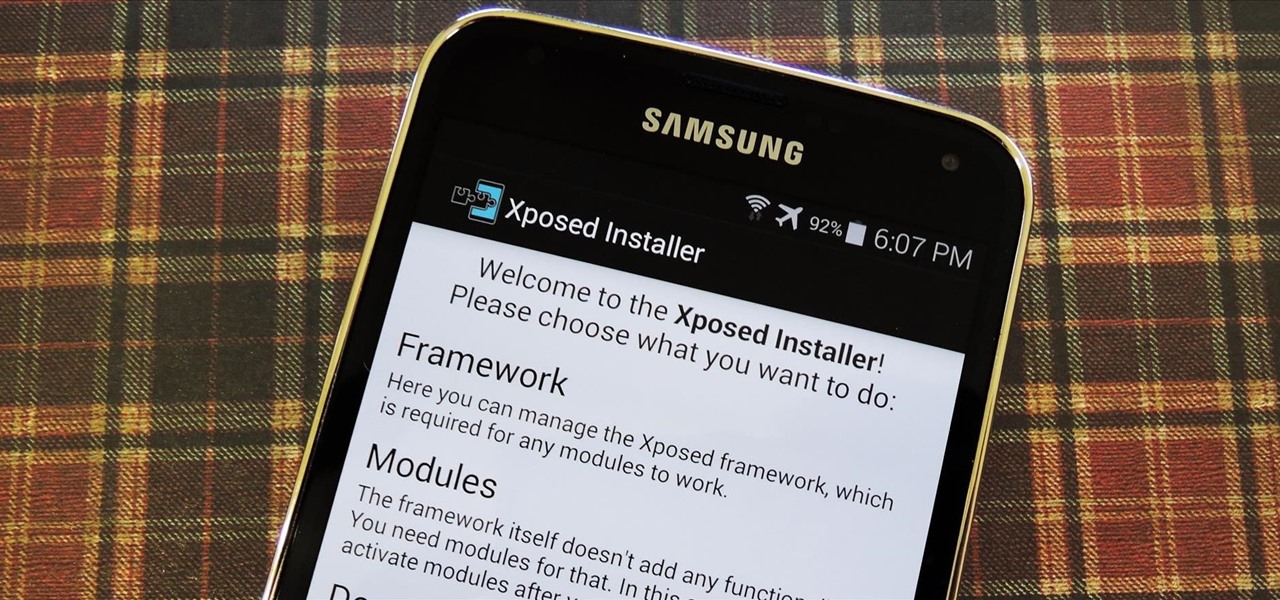
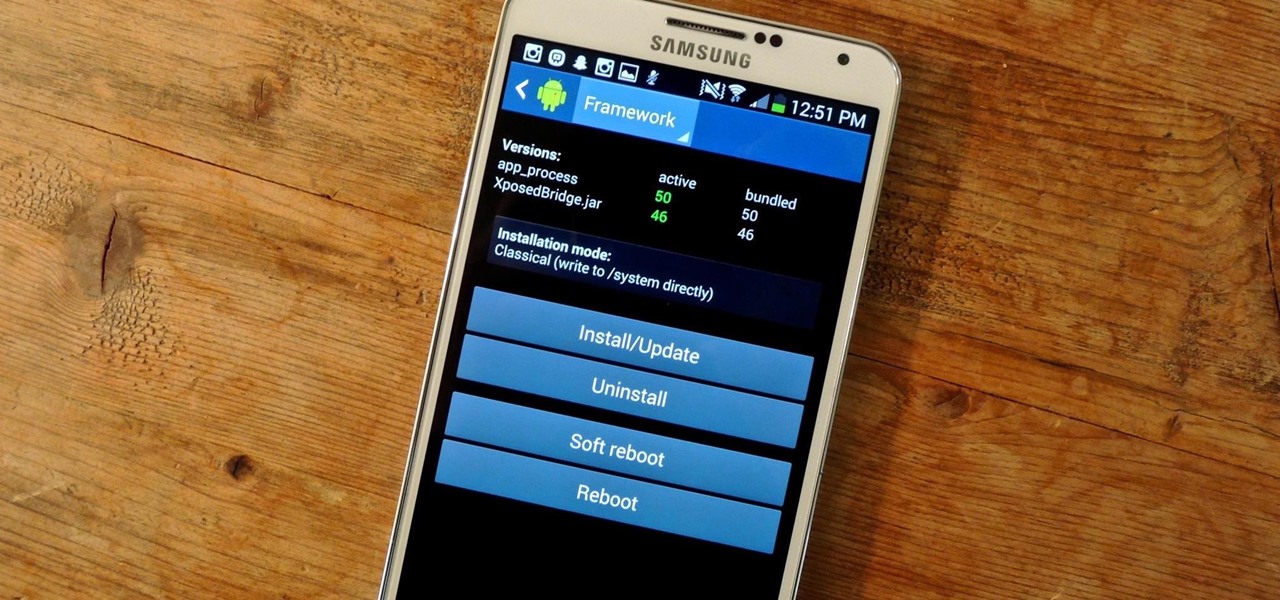
Allowing us to easily get features that would otherwise be available only through flashing mods and custom ROMs, Xposed Installer has been a godsend since its development, simplifying the sometimes tasking and potentially harmful process of changing the core components of Android's operating system.

While browsing the internet on your Samsung Galaxy S4, you've probably scrolled to the bottom of a very long webpage, Twitter feed, or down into the abyss of some other app. Depending just how far down you've scrolled, it can be a test of your patience (and fingertips) scrolling back up to the top.

With over 8 million active users, CyanogenMod is definitely the most popular ROM for Android devices, which explains why venture capitalists invested $7 million last month for future development.

Samsung does a good job of making their devices fairly open, and the Galaxy S3 is no different. There are numerous way to root a device, but sometimes the jargon and steps can be a little intimidating for new rooters, and even pro rooters.

What's the meaning of life? That's the age-old question; but can it ever really be answered? I mean, isn't life just a big game anyway? Perhaps, a game of inches?

Tethering your Android phone basically turns it into a mobile hotspot, allowing you to funnel a 3G or 4G internet connection from your phone into your PC or laptop via USB. As you might expect, phone carriers brought the hammer down in an effort to stop users from getting around the fees they charge to normally allow you to do this.

Assuming everyone knows of the recent "String of attacks" passed between Obama and Romney, I just want to talk about how useless this entire thing is. I'll try to be as un-biased as possible.

WordPress started in 2003 with a single bit of code to enhance the typography of everyday writing and with fewer users than you can count on your fingers and toes. Since then it has grown to be the largest self-hosted blogging tool in the world, used on millions of sites and seen by tens of millions of people every day.

You see people every day, but for some reason drawing them is always so difficult. Have a look at this tutorial for tips on how to draw very easy people. This video is meant for beginners and will show you how to turn a simple stick figure into a lifelike drawing of a person.

Think of your brain like a muscle, if you train it correctly and diligently, it will perform at its top capacity. The retention of information is a skill like any other that can be improved with some practice and even rest when appropriate.

Make sure to get a complete upper body workout and add cable crossovers to your exercise routine. These crossovers can be done at varying angles to work a variety of chest and arm muscles without changing machines. Your pecs will thank you.

Tick bites should be treated immediately, the concern being transmission of Lyme disease. If you've received a tick bite, what you should do is to remove the tick promptly and carefully. Use tweezers to grasp the body of the tick near its head and pull out very gently to remove the tick whole without crushing it. Learn more about tick bites and how to treat them in this medical how-to video.

Yes, you can have your cake and eat it too. There are a lot of light or nutritional alternatives to a lot of the desserts that we commonly use or eat. Saving room for dessert is a must for adding any treat to the end of a healthy meal. Learn some tips for buying dessert foods in this nutrition how-to video.

This fitness how to video demonstrates beginners level cobra poses. Standing poses along with cobra poses are great for opening the muscles in the lower body. Boost your energy level in the morning with a sun salutation that incorporates the cobra pose.

Bosu Ball exercises can increase balance and core muscle strength. Learn Bosu Ball balance exercises with tips on stability and lunges from a fitness trainer in this free exercise video series.

The Lindy Hop is a fusion of many swing dances that preceded it or were popular during its development but is mainly based on jazz, tap, breakaway and Charleston. This 4 part how to video demonstrates of the California lindy routine. These steps are fun and easy to do. Follow the steps in this tutorial and you will be dancing the Lindy Hop in no time.

The Lindy Hop is a fusion of many swing dances that preceded it or were popular during its development but is mainly based on jazz, tap, breakaway and Charleston. This how to video demonstrates the 24 bars of the Big Apple lindy routine. These steps are fun and easy to do. Follow the steps in this tutorial and you will be dancing the Lindy Hop in no time.

SQLite is a small C library that implements a self-contained, embeddable, zero-configuration SQL database engine. SQLite implements a large subset of SQL-92 and stores a complete database in a single disk file. The library footprint is less than 250 KB making is suitable for use in embedded devices and applications where memory space is scarce.

Amid a troubling resurgence in coronavirus cases, led by the new Delta variant, augmented reality is once again moving back into the spotlight as a solution, especially now that the move to return to offices has been stalled.

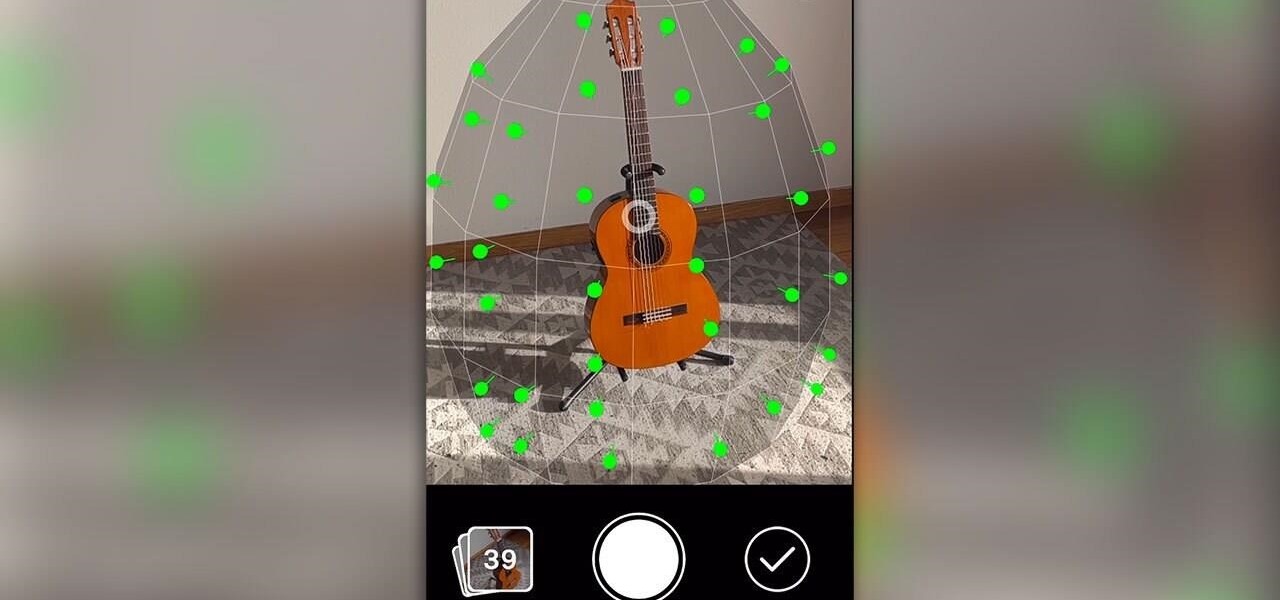
One of the more exciting augmented reality announcements Apple made during its WWDC keynote on Monday came in the form of Object Capture, a new 3D scanning feature coming to macOS Monterey.

In the great smartglasses race, component makers, such as those that supply the crucial waveguide displays that make visualization of virtual content possible, have a vested interest in pushing the industry forward in order to ship units.

For better or for worse, Google started the race towards smartglasses for everyday use with Google Glass before scrapping the Explorer Edition and pivoting towards enterprise customers.

Mobile augmented reality gaming pioneer Niantic is chomping at the bit to get games like Pokémon GO out of smartphones and onto smartglasses, and it appears to be taking matters into its own hands.

Thanks to numerous smartwatch deals this holiday season, many people are receiving their first one. But what exactly can they do? In regards to fitness, quite a lot. With a growing list of sensors and software updates, these small devices can be the very thing you need to ultimately reach your fitness goals.

It's safe to say that we can call the annual ranking of AR investments a holiday tradition at Next Reality.

Smartphones and laptops are constantly sending Wi-Fi radio signals, and many of these signals can be used to track us. In this guide, we'll program a cheap IoT device in Arduino to create hundreds of fake networks with common names; This will cause nearby devices to reveal their real trackable MAC address, and it can even let an attacker take over the phone's data connection with no warning.

Following the launch of the Magic Leap One earlier this month, the device and the company took a few hits from early reviewers. But it turns out those were just love taps compared to the absolute scorched earth acidic screed penned this weekend by someone well credentialed to dissect Magic Leap One: Oculus Rift creator Palmer Luckey.