
News: Magically swap water with whiskey
Properly produced, a pointless bar trick is as much a how-to as a Mario Batali cooking instructional. We are non-discriminatory in that regard. While curating, we focus primarily on the INTENT of the video.


Properly produced, a pointless bar trick is as much a how-to as a Mario Batali cooking instructional. We are non-discriminatory in that regard. While curating, we focus primarily on the INTENT of the video.

In case anybody's been under a Beyoncé-proof rock for the last month, the (internet) world is forever changed by the Single Ladies... and in many ways, me.

Ahhh. Obsession. Specifically, Stephen. When the market dove 700 points last week, he was watching this video, on repeat, mumbling something entirely incoherent.

Coolio slammed onto the music scene with Fantastic Voyage and Gangster's Paradise in the mid 1990's. His persona has ever been an iconoclastic combination of Compton hood and class clown.

This guy from the east coast of Scotland has successfully mated the classic procedural tutorial with stop motion film making. 25 years old. Composed the music to boot. None of the visual techniques are new. But that does not make the video any less satisfying.

Upload up to 4000 songs from a computer onto an LG Rumor cell phone. No need to get a separate mp3 player or iPod as long as you've got your mobile phone. Watch this video cell phone tutorial and learn how to listen to music on an LG Rumor. Listen to music on an LG Rumor cell phone.

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server. You may know that Minecraft is an excellent creative tool, but perhaps less well known are the fascinating array of redstone powered games that have been made by players like you.

This Week's Workshop: Music To My Ears The heart of WonderHowTo's Minecraft World is, naturally, “How-To” and so in the spirit of all things tutorial and DIY we will be hosting a weekly workshop showcasing the best and newest tutorials, builds, and inspiring ideas. We hope to inspire creativity and create a place where the community can share ideas and practice skills, right here on our server.

Have you been thinking about joining a local Belly Dance Class? Many people are curious about Belly Dance but are unsure of what to expect in a class, or may be worried about not being the "right" body type, weight, or age.

As a USC student with limited funds, I'm always trying to figure out how to make the most out of my night when I go out. LA is great because there is so much going on for little to no cash if you know where to look. Echo Park/Silver Lake definitely has the most options, see below for my breakdown.

Go to http://yourguitarsage.com/ to find out how to order my ebook containing charts for over 170 tunes and constantly updating.
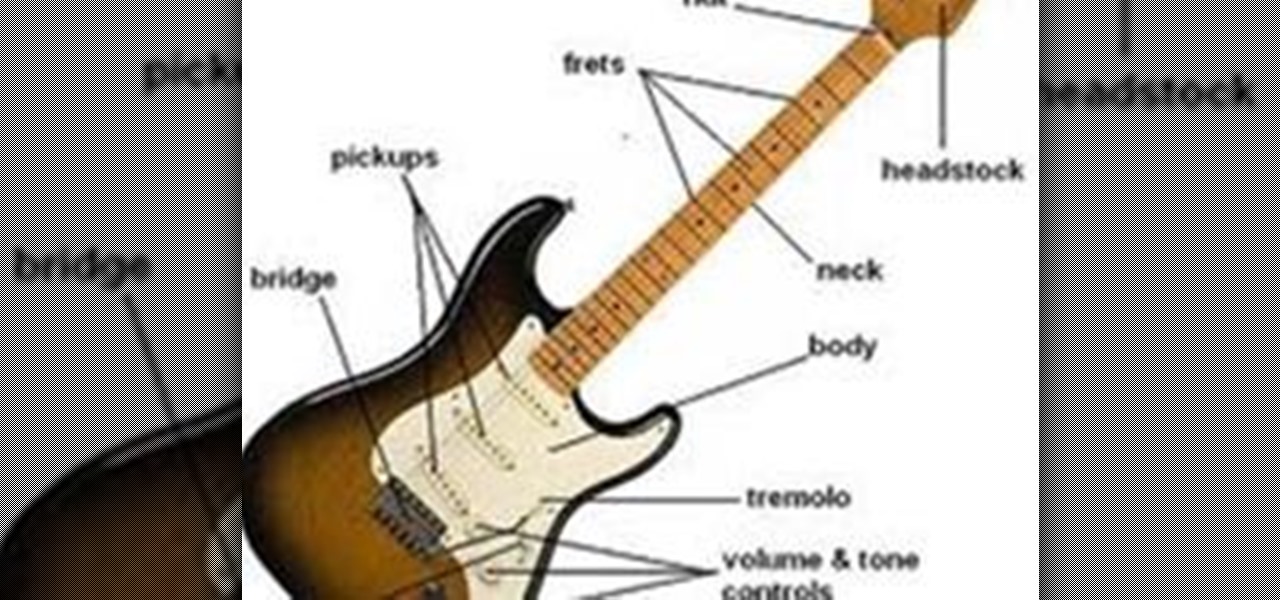
How to be a better guitarist

Tim Hawkinson is an artist who truly inspires. The Los Angeles based artist creates complex, whimsical sculptures with simple mechanics and basic materials. One of his most notable pieces is the art-world-renowned "Uberorgan", a giant football field sized, fully-automated bagpipe, cleverly constructed with plastic sheeting and pieces of electrical hardware.

According to Wikipedia, to be called "the Stradivari" of any field is to be deemed the finest there is...

The Ubuntu CD does not contain much in terms of software applications. So how can we incorporate other programs that would be made available after booting from a live CD?
You can also use Nokia Multimedia Transfer to fill up the memory on your Nokia device to a desired percentage with a random selection of tracks. Nokia Multimedia Transfer will first transfer any photos you may have added to the device folder in iPhoto and music in the device folder in iTunes. If there is still space in your Nokia device memory, Nokia Multimedia Transfer will fill the memory up to the desired remaining percentage.

Oh Data, You so Awesome! We are going to use Node.JS to gather us some data. Given nodes plethora of well abstracted network abilities and it's deep evened nature, it will make quick work of plugging into various data sources and gathering / making good use of said data.

This morning, I received a message from a friend who was reading a hack log, and she had some questions about the commands used. This got me thinking, as Linux has a ton of commands and some can be archaic, yet useful. We are going to go over everything you need to know to read a hack log and hopefully implant the steps in your head for future use.

For a moment, picture a situation where you want to host some files or images, but you do not want it traced back to you. Perhaps you're working on a project with others and need secure data storage. Anonymity is the new shield of the 21st century—and you best protect yourself. As always here at Null Byte, we are trying to make that happen. Before someone can learn how to root a box, they need to learn how not to be found. I can not stress that point enough.

With the plethora of programming that we promote at Null Byte, I figured a lot of you newbies that stop by IRC will need a big boost in the right direction to make your dive into programming a lot easier. A hot question that has been thrown around in IRC a lot when making the initial dive is, "How do I write code?". People who do not know much about computers can't understand how code is written. Code that we write here is usually scripted and written in Python, so we will use it as our examp...

File recovery on Linux is a bit different than Windows. It requires different software than the Windows counterparts because every OS has their own file system. Windows uses NTFS, or FAT file systems, while on the other hand, Linux uses ext-based file systems. I personally use ext4 file system because it's the latest and greatest ext-journaling system and supports a large level of directory recursion and file sizes, but most installations still use ext2 or ext3. When files are deleted from a ...

Welcome to part two in a series about steganography, the art of hiding things in plain sight. We are practicing steganography because it can be a useful skill if you don't have access to encryption software, or need a quick solution to make sure the sender and recipient are the only ones who are able to read your message.

Leaving your wireless router at its default settings is a bad idea. The sad thing is, most people still do it. Once they've penetrated your network, hackers will change your router settings so they'll have an easy way back in. This allows them to change your network into a shell or proxy so they can forward their traffic anonymously through you when committing other dirty deeds.
Type: Digital, Landscapes Theme: Incredible Landscapes, "Beyond the Mundane"
Type: Digital, avian Theme: Bird portraits, "The Avian Persona", wild or in captivity

This article is about how to play triplet strums like Spanish tocaores (guitar players) on a ukulele. This technique is commonly used among flamenco guitar players, and it is portable to the ukulele. This technique is also portable to all kinds of music, and it's a nice way to end a song with some kind of drumming fireworks.

Humming while beatboxing is one of the most important techniques to pick up if you're planning to cover popular songs. It's also a key element for singing and beatboxing, but that's for another tutorial. Here, I'll teach you how to hum while beatboxing by explaining exactly how it works.

If he were still alive, today would be Elvis Presley's 76th birthday. And if you're not planning a huge celebration for the King of Rock and Roll, then try out a smaller one. Learn some of his songs and eat some of Elvis's favorite food today, to commemorate the King.

This video teaches the bare basic sounds for beatboxing and gives you some simple beats to start practicing with. To help you out with timing, use the online metronome at http://www.metronomeonline.com/.

Did you play Cat's Cradle as a kid? Well, there's more to string figure art than just Cat's Cradle or Jacob's Ladder. This string art video demonstrates how to make a string figure Crow's Feet. Song: Stuzz (DJ Deep Jr.) - Punk's Life

Did you play Cat's Cradle as a kid? Well, there's more to string figure art than just Cat's Cradle or Jacob's Ladder. This string art video demonstrates how to make a string figure Horned Star. Song: Europe - The Final Countdown

Did you play Cat's Cradle as a kid? Well, there's more to string figure art than just Cat's Cradle or Jacob's Ladder. This string art video demonstrates how to make a string figure North Star. Song: Laurent Wolf - No Stress

Did you play Cat's Cradle as a kid? Well, there's more to string figure art than just Cat's Cradle or Jacob's Ladder. This string art video demonstrates how to make a string figure Super LIghtning. Song: The Beatles - I Want You (She's so Heavy)

Did you play Cat's Cradle as a kid? Well, there's more to string figure art than just Cat's Cradle or Jacob's Ladder. This string art video demonstrates how to make a string figure Dragonfly. Song: Buckethead - Jump Man

Did you play Cat's Cradle as a kid? Well, there's more to string figure art than just Cat's Cradle or Jacob's Ladder. This string art video demonstrates how to make a string figure Cup and Saucer. Song: Rihanna - Disturbia

Did you play Cat's Cradle as a kid? Well, there's more to string figure art than just Cat's Cradle or Jacob's Ladder. This string art video demonstrates how to make a string figure Super Apache Door. Song: Osibisa - Rabiatu

Did you play Cat's Cradle as a kid? Well, there's more to string figure art than just Cat's Cradle or Jacob's Ladder. This string art video demonstrates how to make a string figure King's Throne. Song: Fabri Fibra / Gianna Nannini - In Italia

Did you play Cat's Cradle as a kid? Well, there's more to string figure art than just Cat's Cradle or Jacob's Ladder. This string art video demonstrates how to make a string figure volcano island. Song: Aphex Twin - Pop Corn

Did you play Cat's Cradle as a kid? Well, there's more to string figure art than just Cat's Cradle or Jacob's Ladder. This string art video demonstrates how to make a parachute / tent. Song: Miles Davis - So What.

Did you play Cat's Cradle as a kid? Well, there's more to string figure art than just Cat's Cradle or Jacob's Ladder. This string art video demonstrates how to make a string figure titled Pillars of the Sun. Song: Megadeth - Holy War.