This video describes how to edit and delete data in PHP and MYSQL. The video is about twenty minutes long and is perfect for anyone learning how to manage databases and websites with PHP or MYSQL. This video is part of a series on learning PHP and MYSQL. However, this video is not intended for anyone who is technically challenged or not a coder and should only be watched after having a good grasp on PHP syntax.
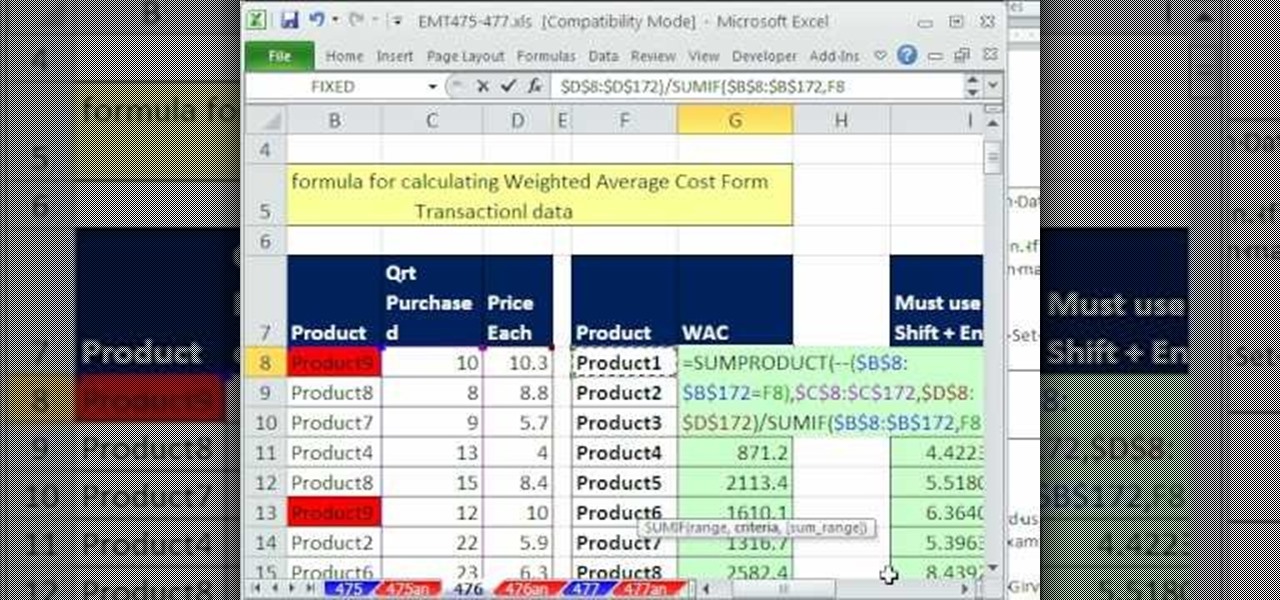
This video shows you how to calculate weighted average cost from a transactional data set using SUMPRODUCT function. It explains things very clearly. If you're working with a very large database transactions the SUMPRODUCT function makes it. It works as text if you do the formatting first and then type the number. We put the number in first and then format as text, then press F2 and ENTER.
OnTime is such a flexible tool and it can be used in a variety of ways, with completely different methodologies. One of the methodologies that works well with OnTime is Scrum. This week we walk through a quick demonstration of setting up a new OnTime database for use with a Scrum methodology.
This first installment from Axosoft's own series of video tutorials on the OnTime Project Management Suite is about Notifications and Alerts—the way OnTime communicates with your employees, your customers, and you about events that occur in your database. Get started using notifications and alerts in your own OnSite projects with this how-to.
If you're new to DreamCoder for MySQL, one of the things you may want to know how to do is create a stored procedure in a remote MySQL database. Happily, this tutorial will walk you, step by step, through the process. For detailed instructions, press play!
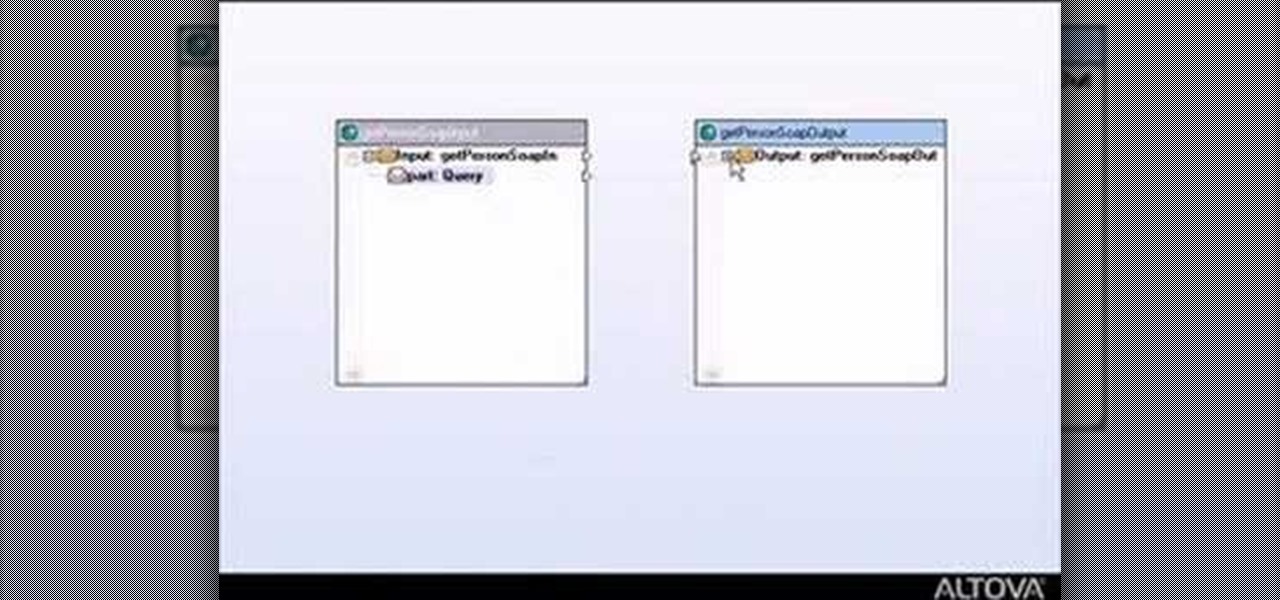
This tutorial shows you how to build web services with MapForce. Load an existing WSDL file and build a complete web service by retrieving data from databases or XML files and using a visual function builder. It's easy to build web services in MapForce as this tutorial shows.

Learn about drag & drop XSLT stylesheet design using Altova StyleVision, a visual style sheet design tool. Learn to publish XML and database data in HTML, PDF, and MS Word in this video.

See how simple it is to create data-driven web sites using ASP.NET 2.0, Visual Web Developer 2005 Express Edition, and SQL Server 2005 Express Edition. Watch this video tutorial to learn how to create a database, add its data, and display that data on a web page.

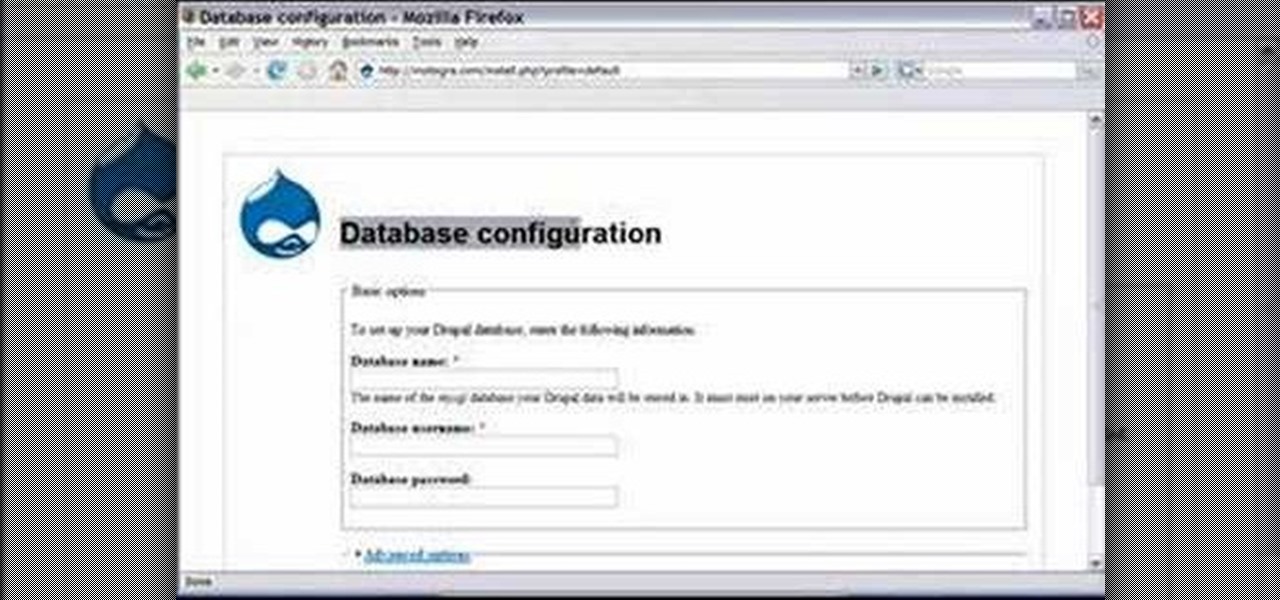
Basic installation of Drupal on a web server from start to finish with good explanations of Drupal's framework. Tutorial assumes viewer knows basic FTP and database configuration.

A quick overview of phpMyAdmin which shows how to view the database information etc from cPanel. This video is provided to you by Scandicsoft.

How to display the data in a MySQL database table in a web page using PHP.

This video demonstrates how to discover the dating history of people by searching on the website www.rateabull.com. The site searches their own dating database, as well as several other social networking sites.

Hello, my web huggers! In today's tutorial we will learn how to use the Google Hacking Database (GHDB) developed by Exploit Database, to find vulnerable web servers and "juicy" information.

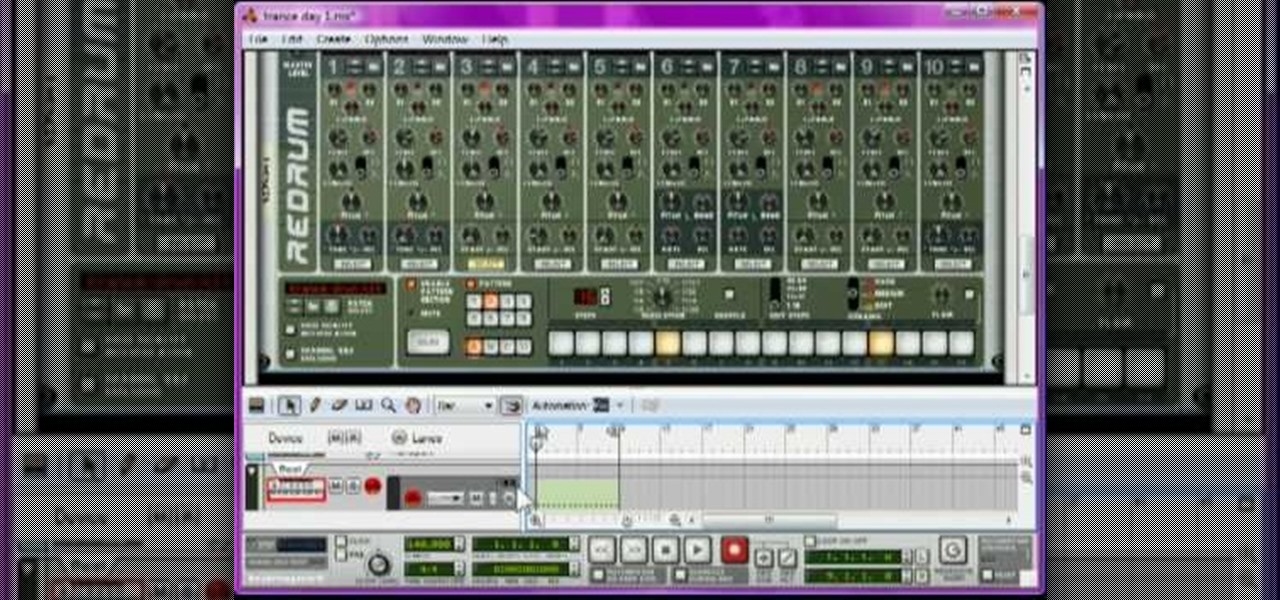
Making trance music has been the point of departure for most of the world's great DJ's, and your career need be no different. If you want to start making your own trance tracks, watch this video. It will teach you how to do it in great detail using Reason 4.

For SQL injection, the next step after performing reconnaissance and gathering information about a database is launching an attack. But something seems off .. in the real world, it's usually not quite as simple as passing in a few fragments of SQL code to an input field and seeing all that glorious data displayed right in the browser. This is when more advanced techniques are needed.

When it comes to streaming services, Google Play Music is one of the best options for both Android and iOS. Perhaps its single greatest feature is the fact that you can upload as many as 50,000 of your own songs to Google's servers, then stream your library to any device without ever paying a dime.

I have been on Null Byte for a long time, a very long time and. I havent always had an account here, ive like many of you also have, been looking and decided to make a profile to contribute.

Lady GaGa and Beyonce blew up the charts early in 2010 with "Telephone" and the music video featured more of the awesome dancing and imagery that has made GaGa videos and concerts famous. Watch this video to learn the choreography and steps to the dance done during the last chorus in the music video for "Telephone".

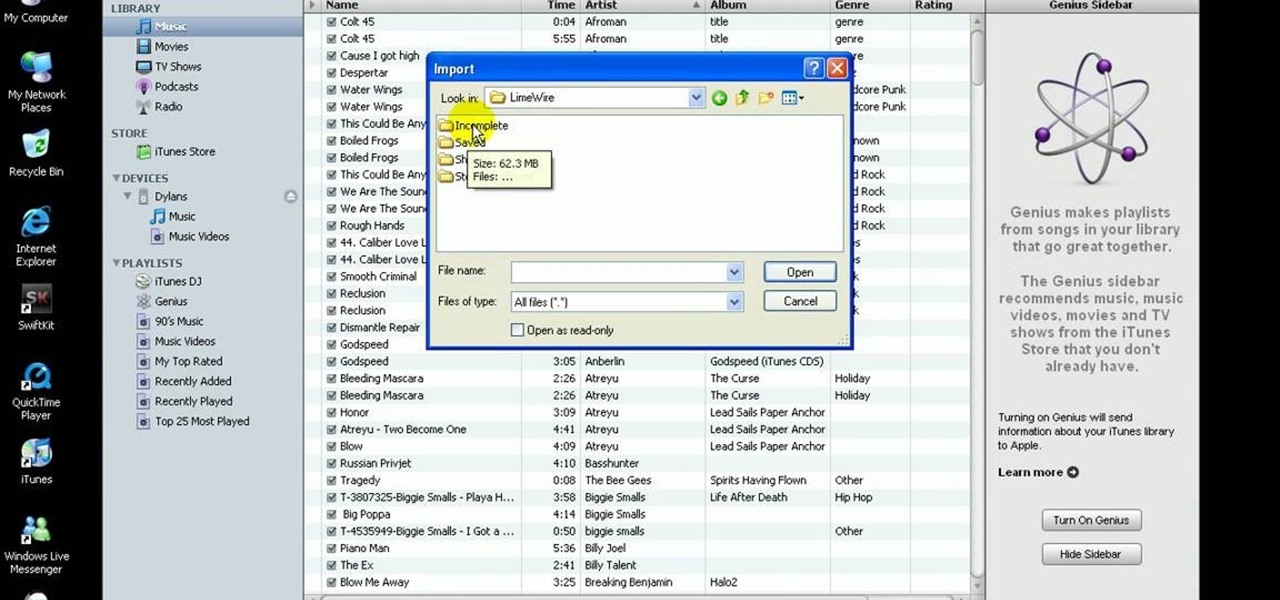
In this quick video, learn how to import music to iTunes from elsewhere on your computer, and then add that music to your iPod or MP3 player. This tutorial contains very useful information that will allow you to take full advantage of your iPod and also help to keep all of your tunes in one place.

First things first: You can't actually recover a Joomla administrator password. That's because Joomla uses a one-way MD5 hash that prevents you from doing so. However, it is possible to reset your password.

Metasploit is an extremely popular pentesting tool capable of enumeration, exploitation, and injecting shell code, and is a part of almost every hacking toolkit. So there's no way I could leave this out of our series on getting your Mac set up for hacking.

INTRODUCTION Hello dear null_byters here we go again with our third part of this serie.

It used to be easy to hack tethering—root your device and install a third-party or modded tethering app. But snuck in amongst the changes in Android 4.3, a new data-monitoring service of sorts made its debut. There used to be a time when your data connection was yours. You paid for it, so you were free to use it for whatever you wanted. Unfortunately, those days are long gone.

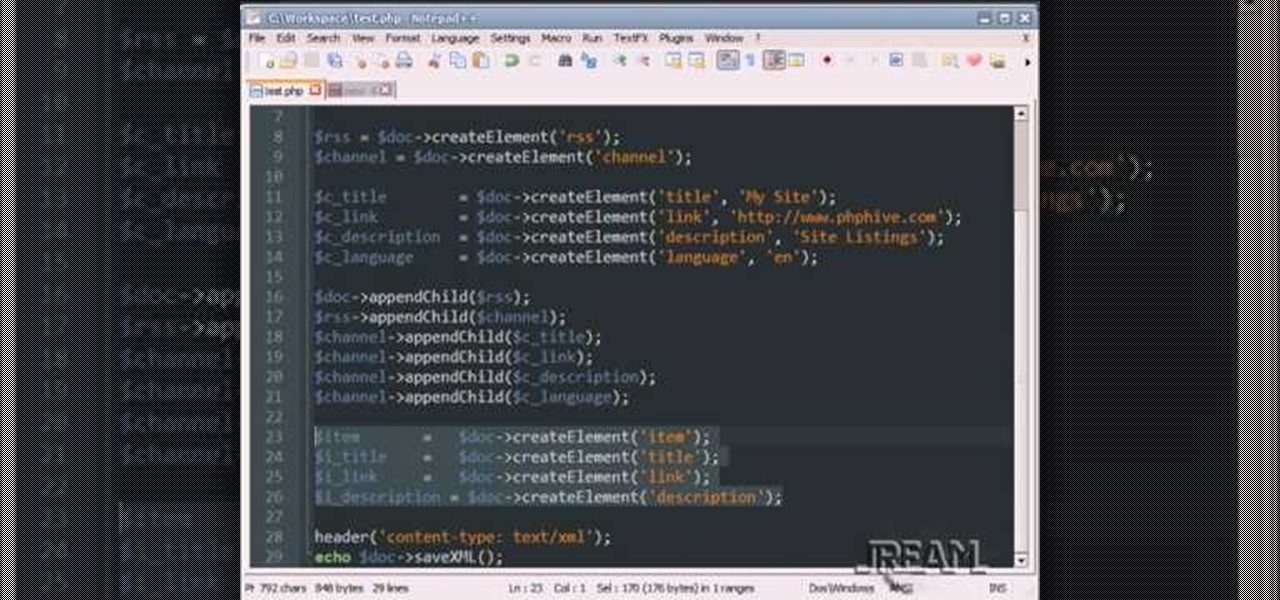
This tutorial teaches you how to create an RSS feed with PHP using DomDocument. You can generate the items with a database loop, and this example uses a very simple array. Take a few minutes and add some more knowledge to your PHP world.

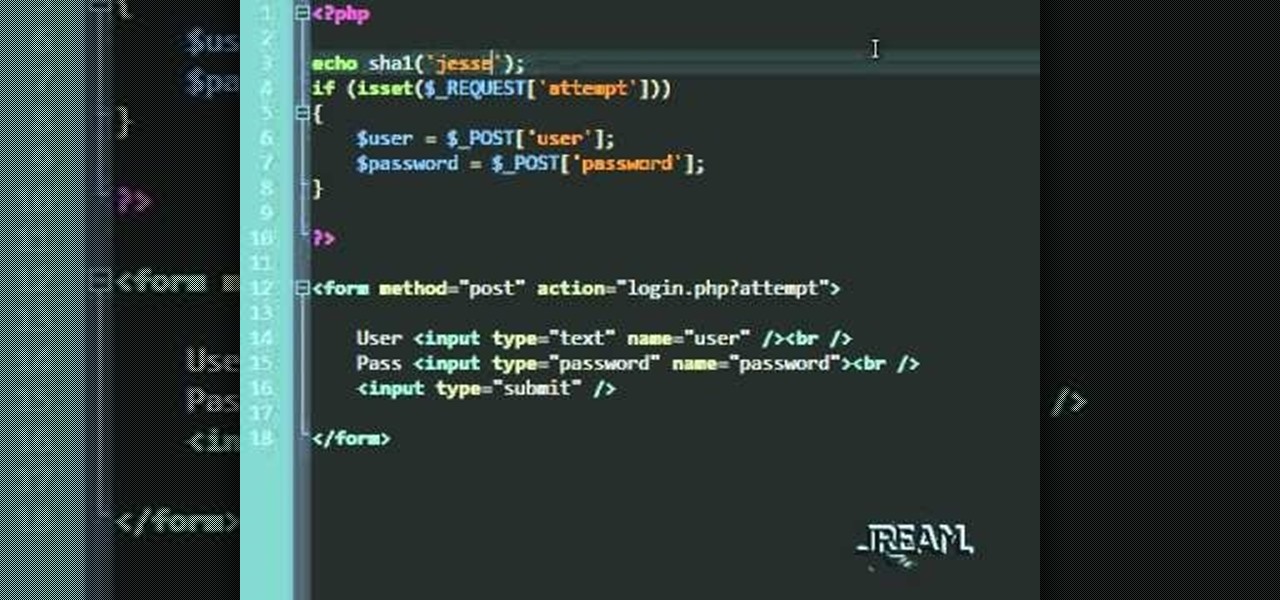
In this tutorial you'll learn about a simple PHP login script that serves to check your MySQL database against a user/password. The code in this video is a quick and dirty procedural code, but it's enough to get you going so you can try it out yourself.

In this clip, you'll learn how to reset or truncate a MySQL DB table directly with script or indirectly through PHPMyAdmin. Whether you're new to the PHP scripting language or a seasoned developer mereley looking to pick up a few new tips and tricks, you're sure to benefit from this video tutorial. Take a look.

MapForce includes support for the two most popular EDI formats, UN/EDIFACT and ANSI X12. In this how-to video, you'll learn how to use MapForce to map and convert data between EDI messages (X12 and UN/EDIFACT) and XML, databases, or text files. Learn to map EDI data with this how-to.

While editing databases with DreamCoder for Oracle, you may find that you want to manipulate master-detail. This minute-long how-to video will walk you through the process in DreamCoder for Oracle. Take a look.

This screencast from Matthew MacDonald, author of Access 2007: The Missing Manual, guides you through creating a custom switchboard in a Microsoft Access database.

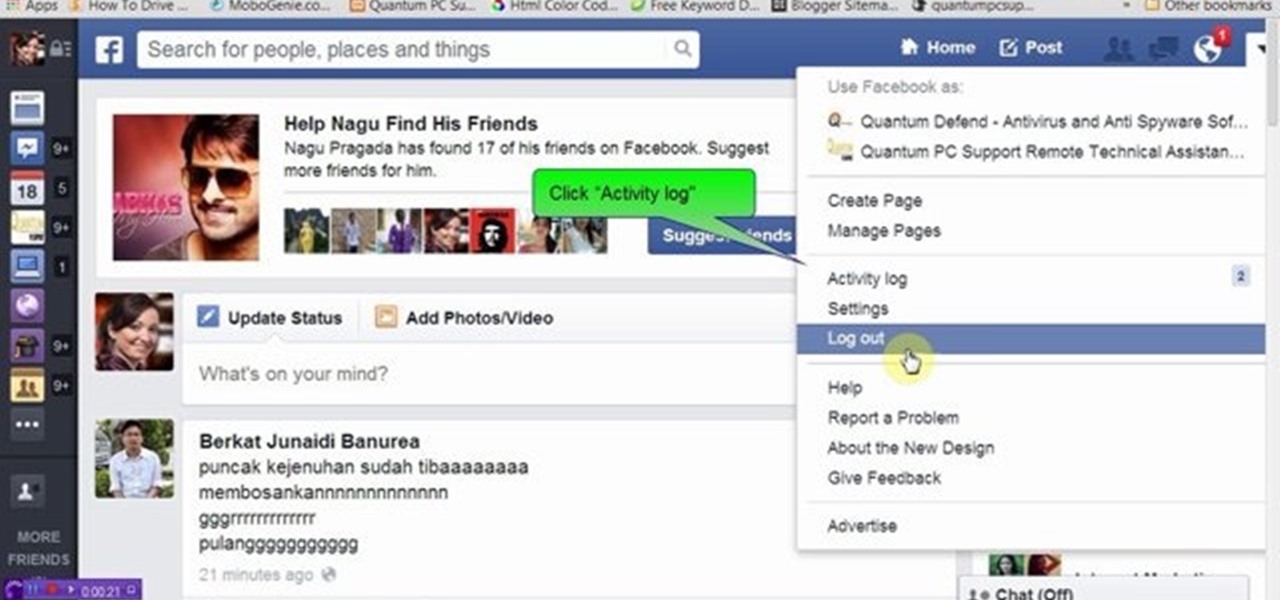
We know that Facebook is a very useful social media site. Facebook keeps your search history in its database. This video will show you how to view or delete history in your Facebook account. Follow the video and try it yourself.

I have made a video to show how we can add an applet into web application. It is shown in two parts. The applet can communicate with database too.

Music today is easily and readily downloaded, and because of that, many of us end up with giant music collections. If you're using iTunes, you can organize your music into specific playlists so that you always have what you want to listen to easily accessible. Take a look at this guide on how to create an iTunes playlist.

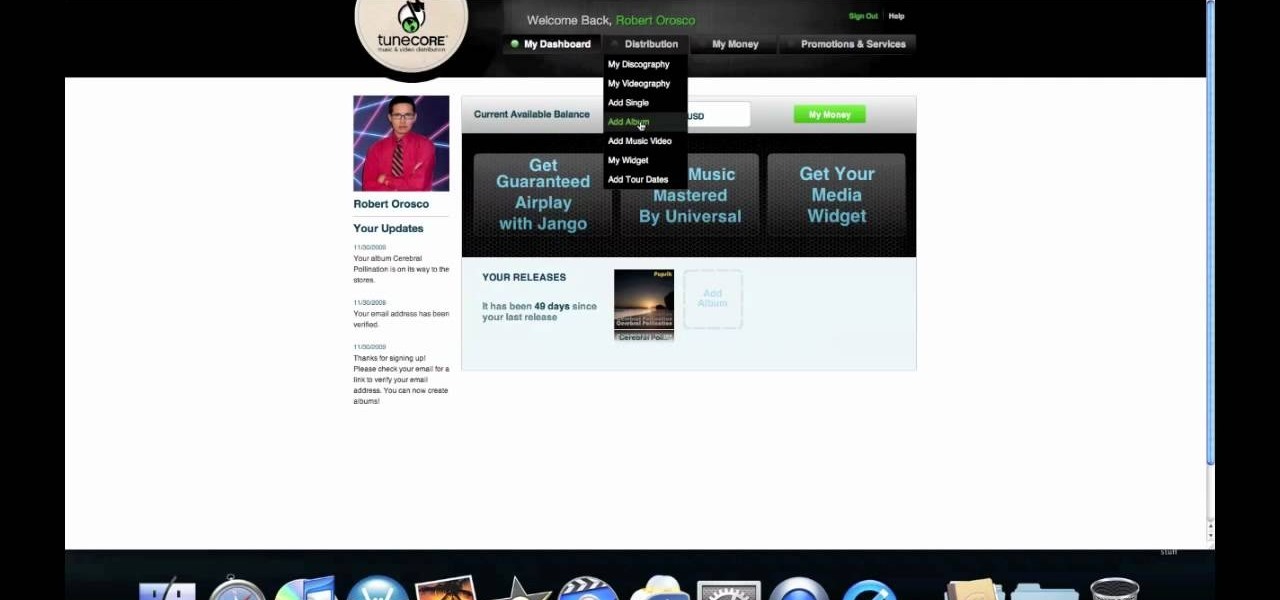
If your band has gotten to the point where you think there is market for your music on iTunes, well done. You're probably wondering how you actually go about selling your music on iTunes. This video will show you one way to submit your music to iTunes using a service called TuneCore.

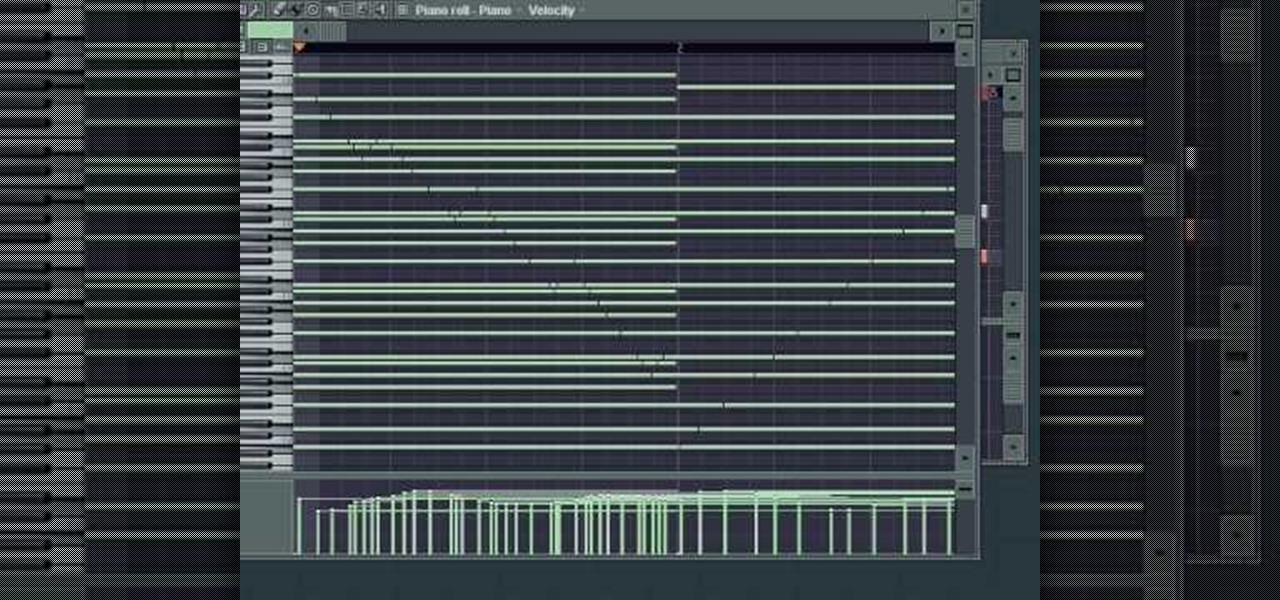
Learn how to cheat like hell to produce realistic sounding piano flourishes, amazing rolls, and perfectly harmonious music in FL Studio. This tutorial uses examples from other FL tutorials on this site so you may have to watch more than just one. Check out this advanced music theory tutorial and get some great cheating tricks to help your music production in FL Studo.

There are many password-cracking tools out there, but one of the mainstays has always been John the Ripper. It's a powerful piece of software that can be configured and used in many different ways. Metasploit actually contains a little-known module version of JTR that can be used to quickly crack weak passwords, so let's explore it in an attempt to save precious time and effort.

No operating system is stricken with as many vulnerabilities as Windows, and it's often a race to release the latest patches to fix things. From an attacker's point of view, knowing which patches are present on a Windows machine can make or break successful exploitation. Today, we will be covering three methods of patch enumeration, using Metasploit, WMIC, and Windows Exploit Suggester.

If you want the best two-factor authentication app out there, our pick is Authy. A close second is LastPass Authenticator. If neither of those is to your liking, try Duo Mobile or Microsoft Authenticator. But if you're fine with missing out on great features, then and only then should you look at using Google Authenticator.

It is often said that the best hackers remain unknown, and the greatest attacks are left undiscovered, but it's hard for an up-and-coming penetration tester or white hat to learn anything unless one of those factors is actually known or discovered. But the end goal here in our SQL injection lessons is to make that statement as true as possible for us when performing our hacks.

GitHub is an extremely popular site that allows developers to store source code and interact with other users about their projects. Anyone can download public, open-source files on GitHub manually or with Git, and anyone can fork off someone's project to expand or improve it into its own project. It's a really great site for programmers, developers, and even inspiring hackers.

Learning how to play guitar, keyboards, bass, even singing, you have to train your ear. Being an intelligent musician and being able to convey ideas is INCREDIBLY important in any professional situation. Learning how to hear various intervals from a root note will open up new avenues of understanding, playing by ear and more! In this video you will get a lesson on intervals as well as some home work to practice with!