
How To: Change the Windows password without the current one
How to change a Windows password in CMD without having to know the current password. Change the Windows password without the current one.


How to change a Windows password in CMD without having to know the current password. Change the Windows password without the current one.
This tutorial shows you how to download bittorents with uTorrent without risking having your IP address get exposed or traced. You will need to find a proxy server for this to work. Download torrents safely.

How to change the login password on Windows XP without having to know the existing password. Change the Windows XP login password.

We hang flags to proclaim our patriotic spirit. This is especially true for retired veterans or those who have loved ones serving in the military. Others hang flags representing the seasons, important events, favorite teams or just a cute and whimsical design as decoration. An American flag can be particularly tricky to wash. Red, white and blue all lying together in one inseparable panel can cause the blue or red dye to bleed onto the white. This is not just a problem with an American flag; ...
In terms of internet, faster = better. We all want faster internet, but how exactly do you get a fast wireless connection? Believe it or not, the answer is quite simple.
FV Extender for Chrome This is an extension you can download for your the Chrome browser. At this time the extension only accepts and sends back gifts but may do more in the future. See developer's site for more information, and a quick video showing this feature in action.

So your washing machine is on the blink? Dirty clothes piling up? You're embarrassed of your smalls and can't face the launderette? Watch this video tutorial to save your blushes and get your machine up and running again in no time...

The following are the response I gather from a therapist (is her opinion). Alejandro, Jessica

Search engine optimization (SEO) is now one of the most important topics for website owners to understand. Anyone that depends on their website to bring them business needs to know the ins and outs of SEO in order to maximize their website’s potential. And if you want your website to have a high Google rank then SEO is essential.

Sometimes, paying for the whole Xbox LIVE service might seem like a waste of money. You're constantly experiencing lag, you've got people modding and cheating, kids are being loud and obnoxious over the mic, and your kill-to-death ratio is getting dumped on. Basically, the whole multiplayer experience just isn't cutting it anymore—you want to go back to the classic world of single player. Well, there's always downloadable content—simply known as DLC.

National Ignition Facility
In my early life I was deeply impacted by the work of physician and psychoanalyst John C. Lilly. I still have my dog-eared copies of The Mind of the Dolphin (1967) and Programming and Metaprogramming in the Human Biocomputer (1968). Lilly's work, with dolphins and the development of the sensory deprivation tank, has formed the basis of movies, music and television productions.

There was a huge ban wave recently on Xbox Live. In the unfortunate event that you decided to do something against Microsoft policy, and have consequently gotten yourself banned from Xbox Live, you may have come to the realization that doing whatever got you banned from Xbox Live in the first place was not worth the risk.

Cars require maintenance no doubt, but it needs pampering even with the change of weather. Like in summer rainy and winter your vehicle is suppose to be looked after differently. It’s always wise to take measures before the onset of the winter season, to save you from the perils. Car owners can follow regular maintenance schedule to have a perfect care of car and it will help them to have hassle free car drive in all sort of weather circumstances even in mercury boiling temperature or spine c...

A silhouette is an outline of a person or an object, usually dark or having little detail, against a brighter, more well-lit background. For this week's Phone Snap Challenge, we've asked you to capture your own silhouette photo with your cell phone for a chance to win a SuperHeadz Ultra Wide and Slim 35mm Camera.

Most people have had the unfortunate experience of not having a washer and dryer at some point. Apartments in my area tend to charge at least one hundred dollars extra for the units with washer and dryer hookups, and even more if you want a unit with an actual washer and dryer installed already. If you are young and just starting out, this may be hard for you to manage with your current salary. If you have no washer and dryer, the only alternative is the laundromat.

Skyrim is a time consuming game. I know I'm not alone in saying I constantly find myself looking for more time in the day. There is never enough time to read the books I want to read, or learn what I want to learn, or play the games that I want to play.

Looking for last-minute Christmas gifts? Give the gift of mobile gaming! Electronic Arts (EA) and Gameloft are having their annual holiday sales just in time for Christmas. If you've got a gamer on your shopping list with an iPad, iPhone or iPod touch, a mobile game will make the perfect last minute present. Games that are usually anywhere from $2 to $10 are now on sale for just $0.99, and there's lots to choose from.

How to Crack Passwords Faster by Putting Your GPU to Work with HashcatSecurity on the internet is always changing. Not too long ago, having a 10 character password meant that you were safe from all forms of hash cracking. Hash cracking is when you take a string of characters that have been passed through a cryptographic hash and try to reverse them. The normal processors that are housed inside of our computer cases are general purpose. The processors are not meant for handling complex math an...

Welcome to another Community Byte announcement! For the past few Community Bytes, we coded an IRC bot, and hacked it. Then, we created a web-based login bruteforcer! This week we are going to start something a bit different. We are going to start going through the missions at HackThisSite one-by-one each week, starting with the basic missions.
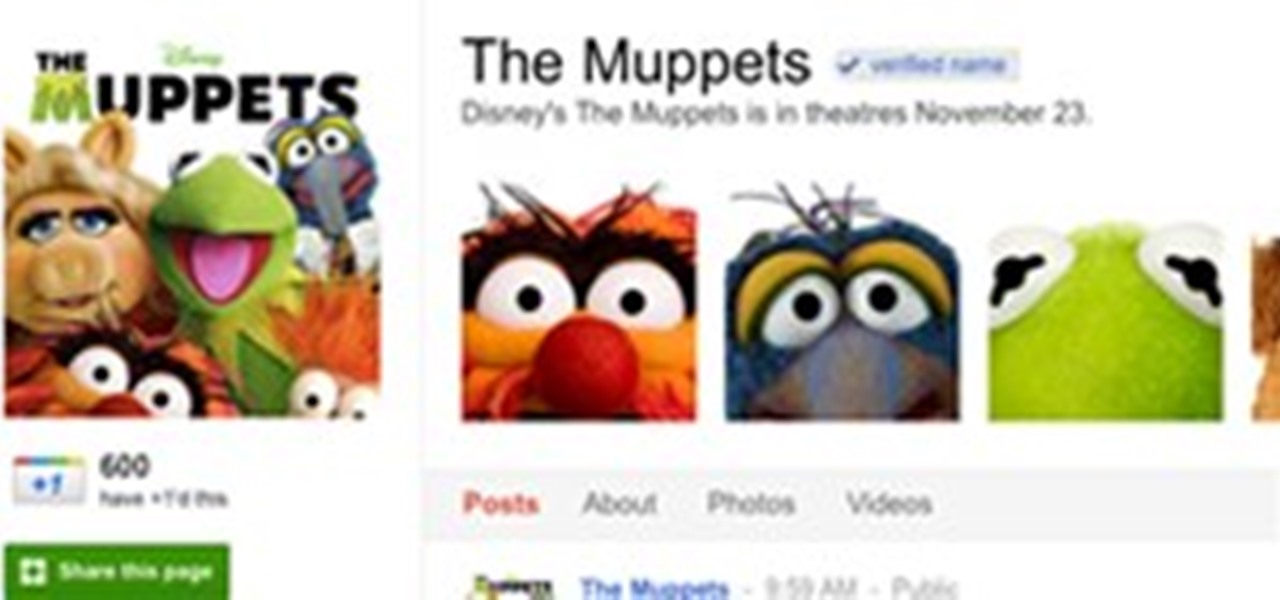
Many companies were disappointed when Google+ rolled out and banned the creation of accounts specifically for businesses and brands. Fortunately, today, Google began rolling out Google+ pages, for them to start connecting with customers and followers. For an example of what a Google+ Page looks like, check out the one for the +The Muppets:

This is Null Byte's fourth part in a series about fully securing our computers (Part 1, Part 2, Part 3). In our last Null Byte, we went over how to encrypt an entire operating system to protect our data, however, this doesn't fully protect us. In the case of legal extortion, the government can actually make you give up your cryptographic key to your computer so that they can look through it.

Learning the basics of SEO In this tutorial I will go over the basics of Search Engine Optimisation. The "white-hat-way" ("black-hat" SEO is tricking Google and other search engine providers, this will get you into trouble quick!).

Permanently deleting files is something that a lot of people aren't aware of. Actually, most people think that once a file is deleted, it is gone forever. This is not the case. Hard drives write to the disk via magnetic charges, positive and negative correlate to 1s and 0s for binary. This is then interpreted into information for the computer to use and access.

PLASTRUM n pl. -S plastron 62 points (12 points without the bingo)

Often times when staying at a hotel or anywhere for that matter, you'll whip out your laptop and check the local area for Wi-Fi. I know you've all been in my shoes when you find an unsecured network that appears to be public Wi-Fi belonging to the hotel or airport, and you connect to it. You connect fast and perfectly, only to find that when you open your browser, it says you don't have an account, and are filtered from accessing the web. This is because the owners of the network want to keep...

The internet is a scary place, and if you're like me, you don't want anyone tracking you or learning your search habits. It's a blatant invasion of privacy for companies to do this, but at least we have methods of fighting back—one of which is Tor.

Bitcoin is a new currency built off "Satoshi Nakamoto's" (alias) 2008 Bitcoin white-paper. Bitcoin provides its users with a way to make peer-to-peer (P2P) transactions without having to use a bank as a mediator. There is no middle man, no corporation backing it, and no one has access to your money, except you. It's decentralized from government, run by the people, for the people.

MOCA's Art in The Street gallery was one of the first large scale street art related museum shows ever. It's not a point of debate whether this did or did not bring street art to a much wider audience, it most certainly did. It united the old graffiti artist of the seventies with the new street artists of the last twenty years. It was a big night with many famous artists attending the opening, including but certainly not limited to, L.A. native Shepard Fairey and the ever exciting Mr. Brainwa...

Dead Island is known for having the most successful trailer of any game ever. It was a beautiful cinematic experience. But sadly, as details of the game itself emerged, and after it was shown at conventions around the world, doubt began to set in about whether this five-year-long project would live up to the hype.

Deus Ex: Human Revolution (DX:HR) was the biggest AAA release two weeks ago, which has drawn rave reviews and sold well across the entire world. But if you've actually played the game, then you've seen something annoying that it and many other games share. It happens at the beginning of the game—every time you turn it on.

Danish developer Playdead has made only one game, a little indie, side-scrolling, puzzle platformer called Limbo. It just happens to be far and away the best video game of that prominent genre (and perhaps the best indie game period) on the Xbox 360, and quite possibly for PlayStation 3 and PC, too. Critical and financial success has followed in droves, and today... Playdead has taken advantage of that success and indie-fied themselves even further by purchasing back the portion of the compan...

These days, I keep multiple browsers open so I can keep track of all my work and personal items. As a staff member of WonderHowTo, a lot of my work is done through our Google Account, which is separate from my personal Google Account.

Crysis 2 is the current standard for high-quality graphics in video games. No other game looks so smooth, so colorful, so... ultra-real. German developer Crytek has built their reputation on PC game technology to the limit, and the CryENGINE 3 graphics engine they used to make Crysis 2 might be the most powerful tool for creating 3D video game graphics on Earth. As of yesterday, it's also free for anyone, yourself included, to download from Crytek's website here.

Children under the age of 13 possess insight that can blow the minds of their elders, but not the wherewithal to make important life choices for themselves. This is exactly why there are strict rules against marketing cigarettes to them. In 2000, a law went into effect called the Children's Online Privacy Protection Act that institutes similar consumer protections for our youth's online identities, prohibiting companies from soliciting personal information from children under 13 years of age ...

+Eric Cattell, the Social Graph Technical Lead of Google+, announced a lot of improvements and added features this morning, most of them having to do with circle management and blocking people.

Hard drive space is one of the cheapest things you can add to your computer. But people take it for granted, thus game developers have given up any efforts in keeping games compact. With all of its expansion packs, World of Warcraft takes up more than 60 GB of hard drive space, and almost any AAA game consumes a gig or two.

Google started culling Google+ accounts. There are two main targets: businesses and those who are using pseudonyms. For businesses, Google is promising to provide their own version of Facebook Pages, which will be released later this year. For those who use pseudonyms, they aren't so lucky. According to Google+'s community standards, users must "use the name your friends, family, or co-workers usually call you". The purpose of this rule is ostensibly to discourage spammers and people from set...

With Microsoft's release of the Kinect SDK, things seem to have slowed down a bit in the world of Kinect development. Have developers exhausted the uses of Kinect already? No way! Four researchers at Cornell University have created an AI-based system on the Kinect that can recognize what you're doing, and maybe even who is doing it.

Tower defense games have covered a lot of creative ground over the last five years. They've gone from simple desktop amusements to a staple of the indie game scene, having been integreated into nearly every other type of game and released on every platform. They have taken place in ancient times, the far future, and on alien planets. But one place they (and most other types of video games) have never taken place is the real world. Not a virtual recreation of the world, but on the very terra f...