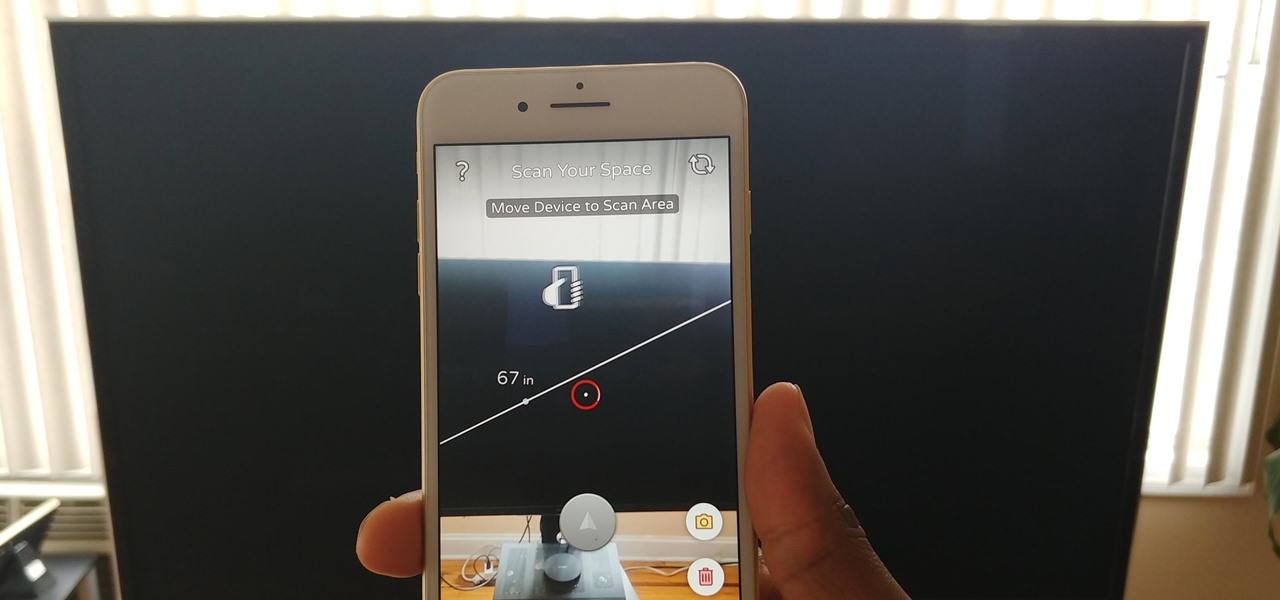
Hello, budding augmented reality developers! My name is Ambuj, and I'll be introducing all of you Next Reality readers to the world ARKit, as I'm developing an ARKit 101 series on using ARKit to create augmented reality apps for iPad and iPhone. My background is in software engineering, and I've been working on iOS apps for the past three years.
Our phones have evolved past a simple pocket computer. They have become more like Swiss Army Knives, opening up possibilities that were previously considered Sci-Fi material. Thanks to the recent push into augmented reality, a new world of tools is becoming available to mobile users.

Accompanying Snapchat's core features, like editing snaps and applying filters to them, is Bitmojis. These are small avatars that you create in your own likeness and use all throughout Snapchat. Formerly, there were two "styles" that you could pick from to make your Bitmoji: Bitstrips style and Bitmoji style. But Snapchat has a third style now that will redefine the way you use Bitmojis.
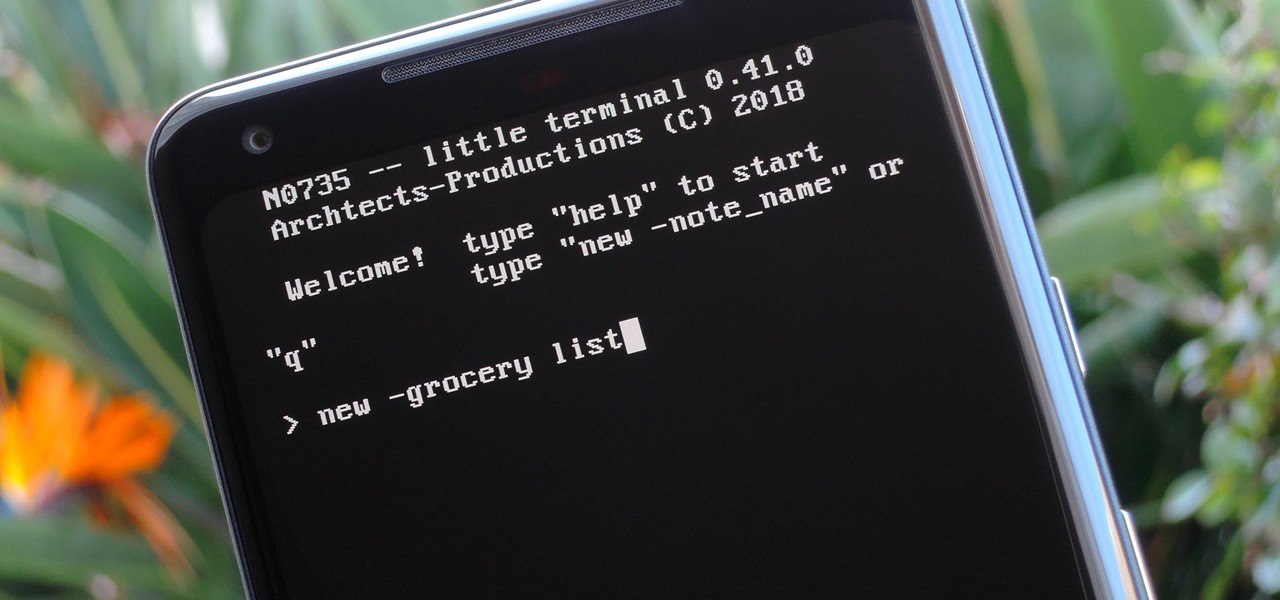
Deep down inside, Android is really just a fork of Linux, the popular open source desktop OS. You can see traces of its roots everywhere, and this lineage still holds a certain appeal with many Android fans. If you're in that boat, you'll love the newest notes app we just found.

When hacking into a network during a penetration test, it can sometimes be useful to create your own wireless AP simply by plugging a Pi into an available Ethernet port. With this setup, you have your own backdoor wireless connection to the network in a matter of seconds. Creating an AP is also helpful while traveling, or needing to share a connection with a group of people.

Not to be outdone by Apple and it's new line of flagship phones, Google has followed suit and finally announced the followup to their highly regarded Pixel line of handsets — the aptly named Pixel 2. Thankfully, the tech giant has also joined in on the trend towards more durable devices, and has engineered both the Pixel 2 and Pixel 2 XL to have a rating of IP67 under the IEC standard 60529.

Virtual private networks, or VPNs, are popular for helping you stay anonymous online by changing your IP address, encrypting traffic, and hiding your location. However, common IoT devices, media players, and smart TVs are hard to connect to a VPN, but we have a solution: Turn a Raspberry Pi into a router running through PIA VPN, which will ensure every connected device gets the VPN treatment.

We started with our system manager in the previous lesson in our series on building dynamic user interfaces, but to get there, aside from the actual transform, rotation, and scaling objects, we need to make objects out of code in multiple ways, establish delegates and events, and use the surface of an object to inform our toolset placement.

The V20 is an amazing phone from LG powered by Android. Packing impressive features such as a removable battery, expandable storage, and the latest Android version straight out of the box, the V20 is a tough phone to beat.

A few months ago, LlabTooFeR leaked a full system dump from Google's then-unreleased Pixel and Pixel XL smartphones. That may not seem like a big deal at first glance, but the system dump contained all of the preinstalled apps and services from Google's new flagships—including the much-anticipated Google Assistant.

This Fourth of July, go beyond cherry pie, strawberry shortcake, and those gimmicky red, white, and blue cupcakes. Instead, wow your friends and family with this delicious, patriotic honeycomb cake made of puff pastry, whipped cream, and fresh fruit — no artificial coloring needed! Don't Miss:

Alright, NB community! Here we go... Bubble Sort. What Is Bubble Sort?

Macs are generally highly power efficient due to, in part, the optimized sleeping schedule with OS X. Yet in certain scenarios, you might not want your Mac to go to sleep: downloading a huge file, reading a book, reviewing a spreadsheet, analyzing some content on the screen... the list goes on. To resolve this, you can go to System Preferences and mess with the settings, but this can be an annoying process if you need to do it often.

Back in the days when June Cleaver was our role model, stay-at-home moms eagerly greeted their offspring's arrival home from school with fresh-baked cookies. But in the current vernacular, "Ain't nobody got time fo' dat!"

Hello fellow gray hat hackers, I wrote a program in python that helps me to fill up my proxychains.conf file, so I don't have to manually enter in the proxies. I figured I will give a little how-to of how I did it and maybe I could help some of you(hackers) out there to stay anonymous.

Vegetables are perhaps the most important part of our diets, but often times they're an absolute pain to prepare. Cleaning every fleck of dirt off of dozens of leafy greens takes ages, and eliminating the more fibrous parts of certain veggies can be extremely tedious.

In this article, we will build a parallel password cracker using the techniques explained in the previous part. As SHA-512 is the digest function that Kali (and most modern Linux distributions) use to store our passwords, we will make a SHA-512 password cracker.

As many of you know, processor's clock frequency improvement got stuck in about 2003, causing the origin of multicore CPU (and other technologies). In this article I'll introduce you on how to run code simultaneously in various processors (I suppose that all of you have a multicore CPU). When you write code without any parallel directive, it only executes in one CPU at the same time (see it below). OpenMP make simple to work with various cores (if not with all of them) , without so much heada...

Welcome back! In the last iteration of how to train your python, we covered loops, today we'll be covering something that I wish I had learned about much earlier in my scripting career, errors. We all run into them, and they can be frustrating, but there is also a silver lining to them. Today, we'll be discussing why some errors are unavoidable, and what we can do when we run into them. Also, this article will be more of a concept and less of writing actual code, but the information is equall...

When I tried to set up an eviltwin for a MitM-constelation in kali 2.0, I couldn't provide internet to the victim. The origin was the brctl bridging. I have read many tutorials but all of them where explained in backtrack and older versions of kali. So i was searching for a solution without using brctl and this solution will be explained now. This will just work on unencrypted wireless-environments.

Heartbleed, move over. There's a new bug in town, and this time it's also affecting Mac and Linux computers. It's called Shellshock (its original official title is CVE-2014-6271), and it's currently got a 10 out of 10 severity rating over at the National Cyber Awareness System. While some updates have been issued to fix this bug, they were incomplete, and your system is probably still vulnerable, as it has been for the last probably 20 years.

The Xposed Framework offers many great customization options for your Galaxy S5. S Health, with its ability to read your heart rate through a built-in monitor, is one of the main selling points of the GS5. Trouble is, the two don't seem to play nice together.

Airports are terrible germ-infested purgatories where people sit around for hours without Wi-Fi while they anxiously await to get wherever they really want to go. Unfortunately, there isn't much we can do about waiting, but this little Wi-Fi hack could help make the waiting a little less boring.

One of the best things about the Nexus line of devices is the ease with which one can achieve root. Plug your phone into your PC, download a couple files, type a few commands, and you can be rooted within 30 minutes. No muss, no fuss, no carrier-locked bootloaders.

Welcome back, my budding hackers! As you know, I firmly believe that to be a true professional hacker, you need to be proficient in Linux. This is for a number of good reasons.

Currently, all Nexus tablets running Jelly Bean or higher can enjoy multiple user accounts. With tablets often migrating between various people in the same household, there’s no reason for Dad’s finances to mingle with little Tammy’s candy crushing. Multiple users, each with separate profiles, just makes sense on an Android tablet.

How to easily build a raised garden bed out of wooden pallets for free! …Well almost free. Building a raised vegetable garden with pallets or reclaimed wood is a really rewarding experience. The garden bed idea out of pallets came about from the fact that l wanted to build a rustic looking raised garden bed. A vegetable garden bed that not only provides delicious food, but looks good at the same time. The recycled wood has come from hardwood timber pallets that have been sourced totally FREE ...

One of the best things about the Samsung Galaxy S3 is the ability to modify the device in countless ways, as with any other Android device.

In this video, we learn how to draw Bruce Lee. Start off by drawing the head, using lines to keep where the eyes, mouth, hair, and nose go. Next, draw in the hair and the outline of the face. Then, draw in the arm making a karate move, and the body, showing the muscular definition. After this, draw the rest of the body, making pants on the bottom of the waist. Draw in more lines to make definition on the body and place circles on the chest for the nipples. To finish this, color the skin in an...

Tired of drawing delicate flowers and ready for something a little darker? You can draw a wicked skull by following the method and including all the qualities you should include to really get your sketch to look like a skull.

This video is about applying eyeliner with your eye closed. Take the pencil, Revlon color-stay in black, and take the hand that is not dominate and pull back the lid to the side giving a smooth canvas. Slowly take the eyeliner and start from the inside corner of the eye and start slowly going all the way across. Slowly start following the natural lash line. Add a wing to it by taking it past the natural lash line. Bring it up just a little bit. To make it last all day, put liquid liner over t...

This video shows you how to write checks, in case you're really dumb. Two girls set up a fake store in which they demonstrate how to write a check. The girl playing the cashier explains the following steps to the other girl playing the customer.

This video shows you how to make monolid eyes look more open and rounded. First, prime your eye. Take a dark green shimmery color and brush that in from your lash line to your eyelid crease. Take a peach shadow and work that in from your crease to below your brow bone. Blend in more green. Blend again. Add vanilla colored shadow on your brow bone to highlight. Now take a lighter shade of green and dab it in the center of the upper lid and highlight with a vanilla color. Line your eyes softly ...

Watch this video to learn how to edit the Windows Experience Index. While it may not be apparent from the video, but it is really quite simple. Browse to C:\Windows\Performance\WinSAT\DataStore

In this how-to video, you will learn how to use a song to read palms. Memorize these lines to music to help you. First, if you have a rich line, you are the rich and you get much money. If you have a sun line, you are popular. Everyone likes you because you are the sunshine. Check your palm. Check your life line. If it is thick, you have a powerful body. If it is thin, you are weak. Check the head line. If you have a short line, you quickly decide and act. If it is long, you need to think fir...

A bouquet of roses is a lovely thought but will quickly wilt and die. Give your loved one a bouquet of roses that will last for years to come and it will only cost you the price of a pencil and paper. They’re quick and easy to sketch.

If your looking for a break from monopoly and checkers, try your hand at the ancient Chinese board game Go. Go is a strategic board game in which you must try to surround a vacant point on the board with your stones and avoid getting your stones tied up by your opponent.