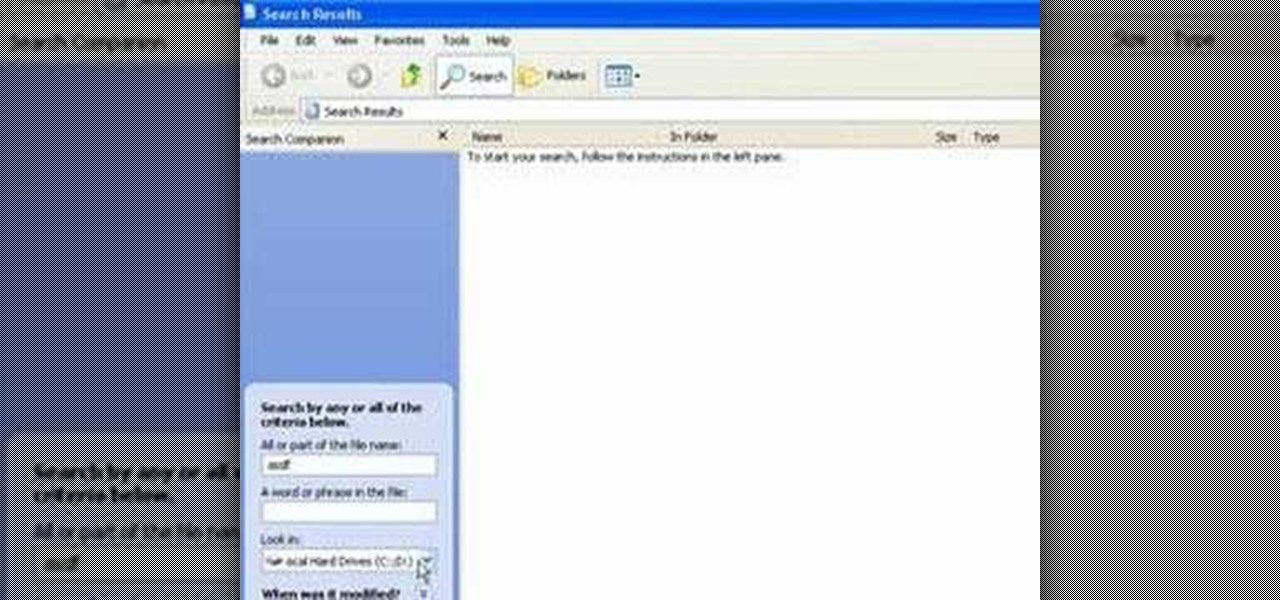
In this video tutorial, Mike shows how to find a missing file in Windows XP and Vista with three different options. In the first option, open Windows Explorer or My Computer. Then open the recycle bin to check for your missing files. If you don't see your file there, close the recycle bin and go to Start and then Search. Look for your file by searching for the file by name to find the location of your missing file. You don't have to know the entire file name to do a search. If that does not w...

In this economy being competitive for a job means your application must stand out above the rest. Here's how to write a cover letter to successfully introduce your resume. Make sure your cover letter follows business letter format. Your name and address must be written at the top left corner. The employer's name and address are written just below. The letter should be addressed to a specific person within the company. Paragraphs in a business letter are not indented, but instead are left just...

What are the names of basic picks? How do you use them? Check out this instructional con video that provides an overview of the basic pins used in lock picking. All picks can be put into two basic categories, raking picks and single pin picking picks. Learn the names of the various picks and how to use them with this tutorial video. Learn the basics and start lock picking like a pro!

Learn how to apply a makeup look inspired by Keira Knightley from the premier of Pirates of the Carribean: Dead Man's Chest. The products used for this look are Dark Brown Shadow (the palette's so old, the name's rubbed off... any dark brown shadow will do), Gold Shadow from the Profound Palette, Champagne Shadow from the Profound Palette, Maybelline Define-A-Line eyeliner in Ebony, MAX Factor Volume Couture Waterproof Mascara in Rich Black, Sonia Kashuk blush in Royal Rush, and Covergirl Lip...

Hello, my name is Nicole Valentine and on behalf of Expert Village, I'm here to talk to you about how to coordinate birthday games for a birthday party. We're going to now talk about how to play the game think fast. This is a very simple game. Just use a ball that you have at home, go to your kids room, go to the toy box and choose an easy ball and you would like to line the guest of the party in a circle. Choose a theme. If it's a boy's party, you might want to go with Power Rangers, or spor...

Hello, my name is Nicole Valentine and on behalf of Expert Village, I'm here to talk to you about how to coordinate birthday games for a birthday party. Now we're going to discuss another birthday game and this one also happens to be an oldie but goodie. And this game is called connect the dot. This is a perfect game if you want the kids in your birthday party to kind of calm down. Let's say after they've eaten, or even the birthday cake. But you want to draw about 4 lines of dots containing ...

Directing a message at a specific person in a group conversation, or to a select few people in the group, can be difficult if you're in a particularly active or hectic chat. Notifications and badges on your iPhone can help you keep track of important messages, but it's still easy to miss one meant for you and not the entire group — which is why you can now mention contacts, or get tagged, in Messages on iOS 14.

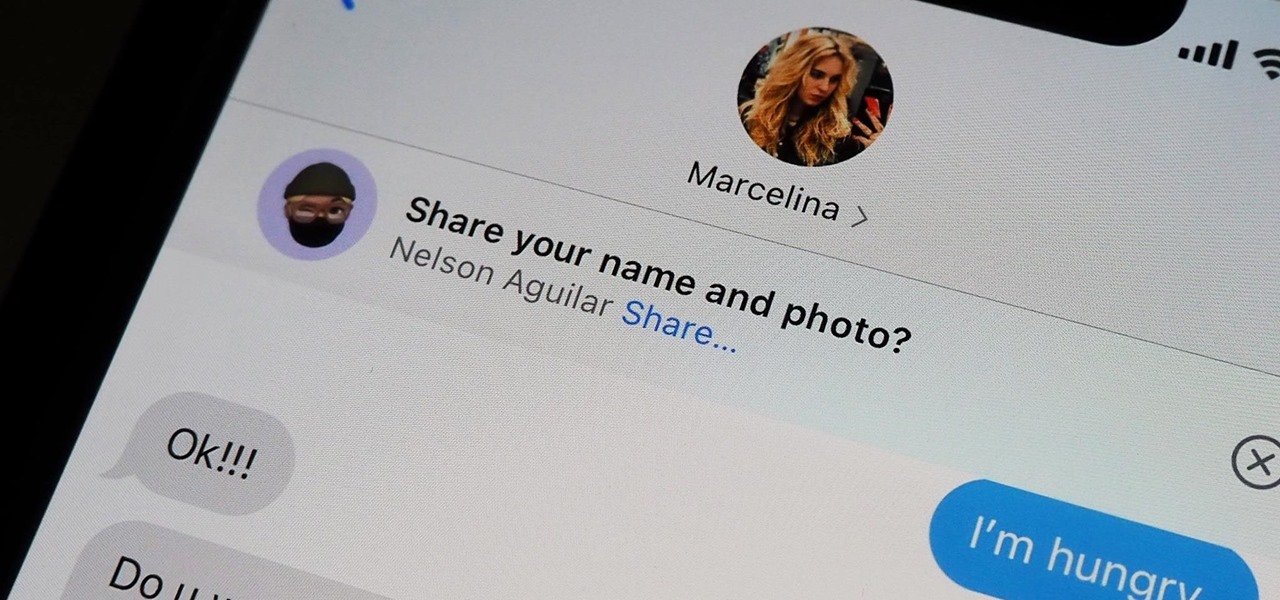
Your iPhone comes with a feature that allows you to share your name and photo with anyone you iMessage in Messages. It's a useful feature if you want people to see a customized name or fun image that you pick, but seeing all those "Share your name and photo" alerts in conversations can get real annoying quickly. There's a way to stop that from happening, thankfully.

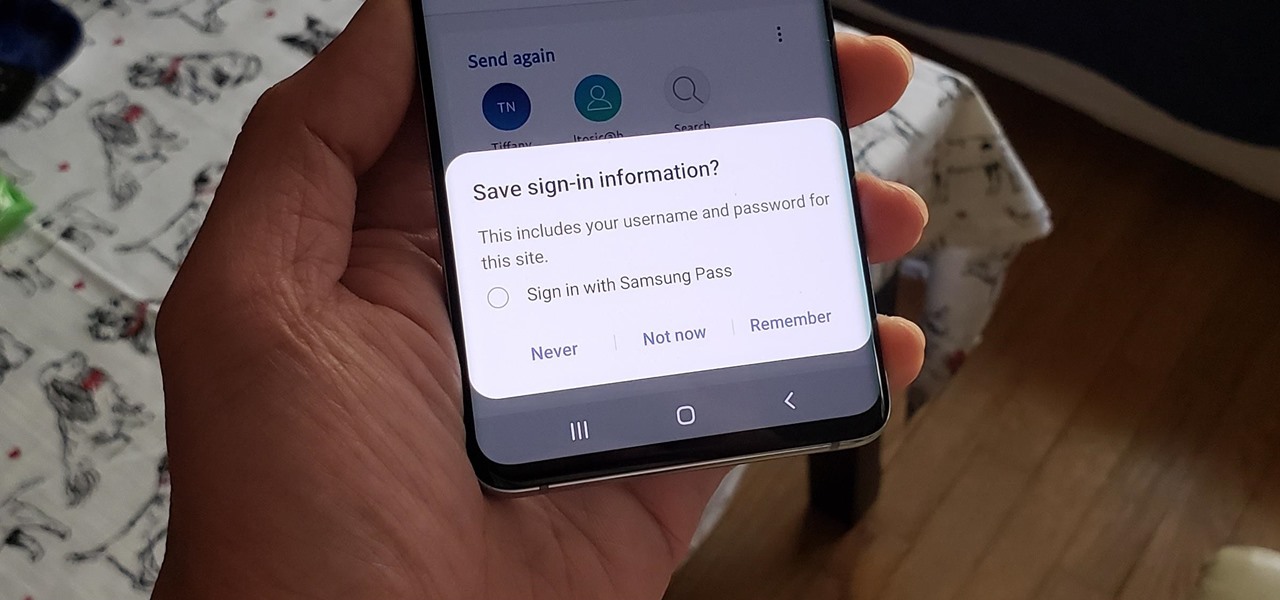
If you use Google Chrome on your computer, you've undoubtedly saved a ton of passwords since the browser always prompts you to. But Samsung uses their own password service on their phones by default, so you'll have to change a setting if you want to use your Chrome passwords to log into apps and sites on your Galaxy.

When you have a personal Instagram account but also manage other profiles — like ones for work, your entrepreneurial startup, an alter ego, or your famous pet, to name just a few examples — how do you manage them all from the same device?

When watching stories in your Instagram feed, there's a high probability that you'll come across an AR filter that you'll want to try out for yourself. A quick browse and search in the Effect Gallery will bring up nothing in most cases. But all of that unproductive work isn't necessary because there's a faster and simpler way to get the AR effect in Instagram Stories, and it works all of the time.

As we predicted this time last year, Magic Leap is finally moving from consumer entertainment hype to making a firm commitment to enterprise customers.

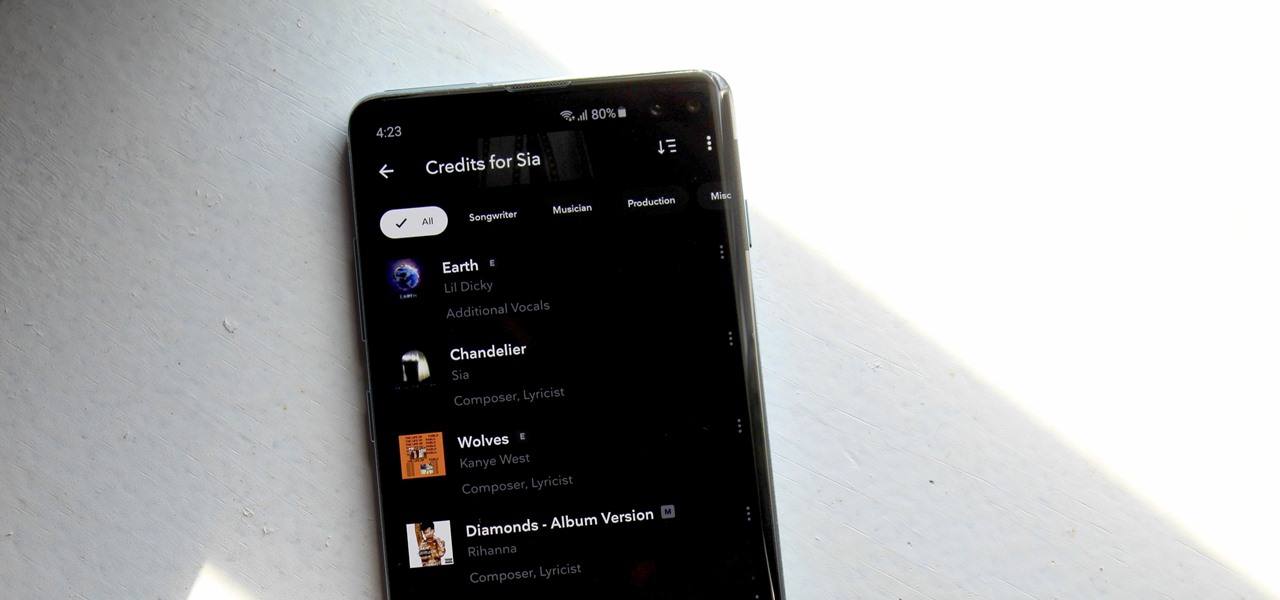
Contrary to popular belief, it takes more than just one artist to create the sound, lyrics, and vocals of a song. With most music being enjoyed digitally nowadays, it's harder to know all of a track's collaborators, as this info used to be in the CD booklet. Well with Tidal, you can now easily find this information and more.

Phone numbers often contain clues to the owner's identity and can bring up a lot of data during an OSINT investigation. Starting with a phone number, we can search through a large number of online databases with only a few clicks to discover information about a phone number. It can include the carrier, the owner's name and address, and even connected online accounts.

Smartphones and laptops are constantly sending Wi-Fi radio signals, and many of these signals can be used to track us. In this guide, we'll program a cheap IoT device in Arduino to create hundreds of fake networks with common names; This will cause nearby devices to reveal their real trackable MAC address, and it can even let an attacker take over the phone's data connection with no warning.

Front and center for iOS 12 this year is Group FaceTime, which allows users to chat with up to 31 additional people at once. While that ambitious feature is sadly delayed, don't cast away FaceTime just yet — you can always pick up your iPhone and start a call with any single contact directly from the Messages app.

Samsung has kept us busy with their Android 8.0 Oreo beta testing program for the Galaxy S8, and most recently, the Galaxy Note 8. As the beta continues to receive new updates, stability has improved continuously, and new features keep on creeping in for both devices.

Playlists are a vital feature for any music streaming service. For many, the ability to add and organize songs into the perfect order is a deciding factor in which streaming service to choose. The folks at Tidal (including owner Jay-Z) certainly recognize this, as they've provided users with the tools to not only create perfect playlists, but edit them as well.

Sophisticated hackers have been exploiting vulnerabilities in Chrome and Firefox to trick even the most careful internet users into logging into fake domains for sites like Apple, Google, and Amazon.

Ever since the update that turned Google Keyboard into Gboard rolled out, a lot of people have been noticing that word suggestions and auto-correct features are downright slow. The issue seems to affect users with multiple languages installed more than anyone, though it can also happen if you have a midrange phone or older device with only one language installed.

Welcome back, my budding hackers! In this series, I have been trying to familiarize you with the many features of the world's best framework for exploitation, hacking, and pentesting, Metasploit. There are so many features, and techniques for using those features, that few pentesters/hackers are aware of all of them.

Hello Friends … My name is Suresh Senarathna and this is my first “How-To” post,

John Oliver sunk his teeth into Republican presidential candidate Donald Trump during the long segment on the latest Last Week Tonight. The whole 21-minute video is definitely worth a watch, but the real fun starts around the 18-minute mark.

Android's Google Play Games app has let you track your feats and accomplishments in the games you play for quite a while now, but for some, the immersion experience might be broken after you finish dominating a game only to see your regular-ass name from your Google account on the leaderboard.

Welcome to the first coding tutorial on SQL here on Null Byte. Typo:

What's up, peeps? In this quick tutorial, we will be looking at structs, a special kind of data type.

Hello everybody Joe here. Today I will be demonstrating how you can find XSS vulnerabilities in a website and what you can do with them

I spend a lot of time helping friends and family with their tech problems, like clearing a browser's cache, scanning a Windows computer for malware, and speeding up a Mac. However, the issue I deal with most frequently revolves around forgotten network passwords.

Doxing is the act of finding one's personal information through research and discovery, with little to no information to start with. You may have seen doxing in the news, for instance when not so long ago, hacker team Anonymous doxed and reported thousands of twitter accounts related to ISIS. Doxing can be useful for finding the address of a coworker, or simply investigating people on the internet. The tutorial I will provide to you now will teach you the basics of doxing and how you can prot...

When you press the "Call" button on most Bluetooth headsets, the majority of Android devices will launch a built-in Voice Dialer app. This app has been around since the dawn of Android, and has received very few interface or functionality updates.

If you've haven't had your fill of Apple's security issues in recent weeks, Siri is now the latest to join the slew of problems with the most recent version of iOS (7.1.1).

Now that the Chromecast development kit has been out for over a month, more and more Android apps are being released or updated to work with the Chromecast.

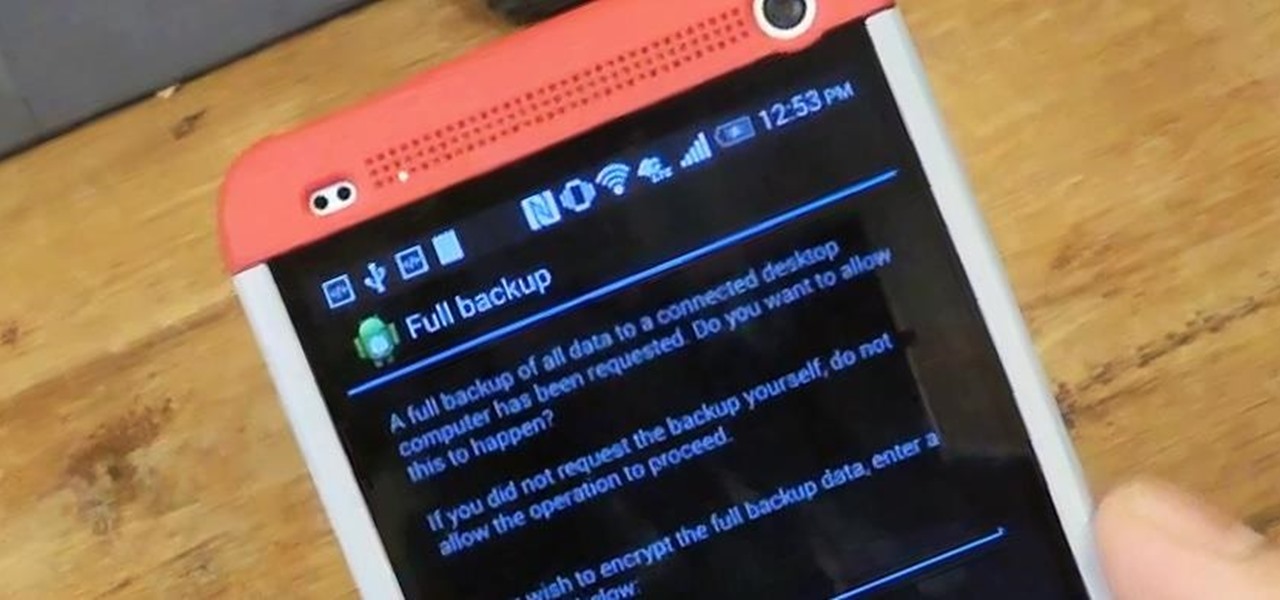
Today, I'm going show you how to back up all of your apps and their data using Android Debug Bridge (ADB)—an essential function for all softModders. These commands will be especially useful when you are updating your version of Android, since they don't require a third-party program to run on your device.

Gmail is a free, advertising-supported email service provided by Google. Users may access Gmail as secure webmail, as well as via POP3 or IMAP4 protocols. Gmail initially started as an invitation-only beta release on April 1, 2004 and it became available to the general public on February 7, 2007, though still in beta status at that time. The service was upgraded from beta status on July 7, 2009, along with the rest of the Google Apps suite.

Every iPhone, iPad, and iPod Touch owner has that one folder which contains those never used apps. You know what I am talking about, the folder that contain Stocks, Voice Memos, Game Center, Compass, Newsstand (That's right, iOS 7 allows Newsstand to be placed in a folder!!). What do you call that folder? "Junk," "Hardly Used," "CrApple?" Why not call it nothing at all.
This how to will show you how to program a fairly simple Hacking bat file. First open notepad.

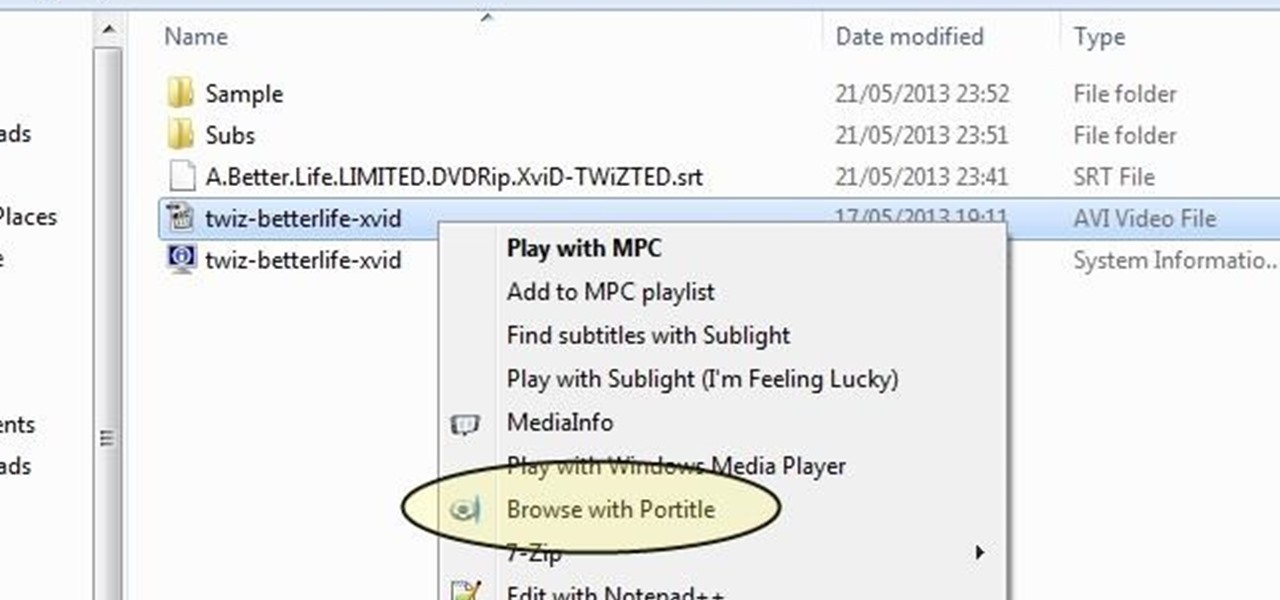
Understand the Problem of Couch Potatoes I have a lot of movies stored on my PC and when I have to finally have the time to watch something, I do not always remember which movie is which. So now I have to google for each movie with the keyboard or search in IMDB.

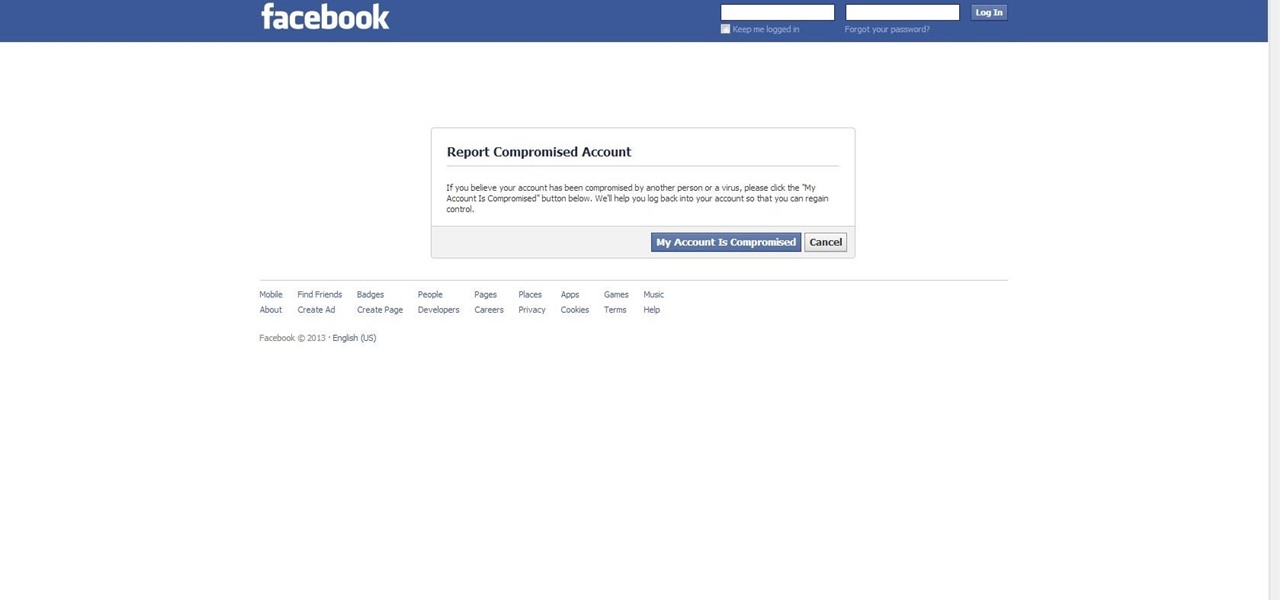
If your facebook account was hacked by someone and you really want it back this tutorial would help you get it back.

ATTN: HUMOUR ALERT Jules Verne was an author of immense imagination, who had a profound effect on speculative fiction, whereas Victoria was a stodgy & pampered royal who led a sheltered and traditional existence. Boring, frumpy, grumpy royal! (Photo from The Guardian, UK)

Have you ever wanted to be famous? Of course you have! Now you can make your Twitter profile look like it's verified, just like professional skater Lil' Wayne. With Twitter's new header, you can now upload a cover photo onto your profile to be seen online and on mobile devices. Just click here and change your header with the images below to get "verified" in seconds! Note that this will not work on the newer Twitter profile designs, since the verified symbol is located outside of all images.