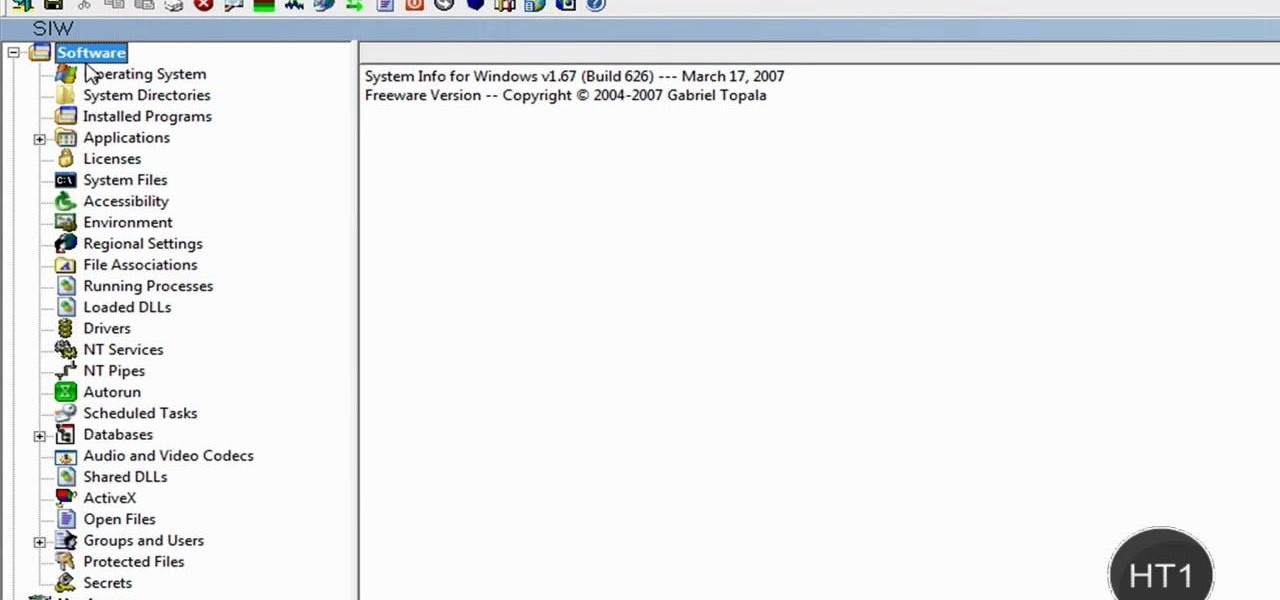
How to find out information / details about your computer? To find out the information about your computer, you need to download software from the website PC World. The following are the steps to download the software:

Bridge is one of the most popular games in the world. The rules may seem overwhelming, but all you need are a few easy steps to learn the basics.

Got ballet tickets? Learn to appreciate and enjoy the performance with these steps. You Will Need

Othello, also known as Reversi, is played with two players, each representing a color on the board. The rules are simple, but strategy is what will help you win. Watch this video to learn how to play Othello or Reversi.

Learn how to 50-50 grind with a skateboard. After you've mastered some skateboarding fundamentals, try moving on to the 50-50 grind.

It's the coolest pool party game ever named after a 13th-century explorer. Marco Polo is a perfect way to cool down and have fun.

This video includes instructions on how to get your PlayStation Portable (PSP) onto the BGSU wireless network.

Apple's annual iPhone launch is set for Sept. 10 and iOS 13 is expected to be released soon thereafter, but it appears that the likelihood of a "one more thing" reveal just got a big boost.

Scientists are constantly on the search for new organisms, species, and other types of life. A special group of these researchers, calling themselves "bioprospectors," dive deep into mines to find unique lifeforms with special properties not found anywhere else.

You might feel the bite, you might not, but an infected mosquito has injected you with a parasite named Plasmodium falciparum, a single-cell protozoa that quickly takes up residence in your body.

Well hello dear readers of Null byte, let me start off stating english is not my first language and they will be some grammar mistakes. This also is my first tutorial so don't hesitate to give me feedback :)

Welcome back, my budding hackers! In my continuing effort to build your basic Linux skills for hacking, I want to show you how to build a secure "tunnel" to MySQL.

Learn How to draw Zero no Louise of Zero no Tsukaima Zero no Tsukaima, or The Familiar of Zero as it is popularly known in the west, is a fantasy comedy-romance anime that tells the story of a young female mage named Louise. For the full tutorial with step by step & speed control visit: how to draw.

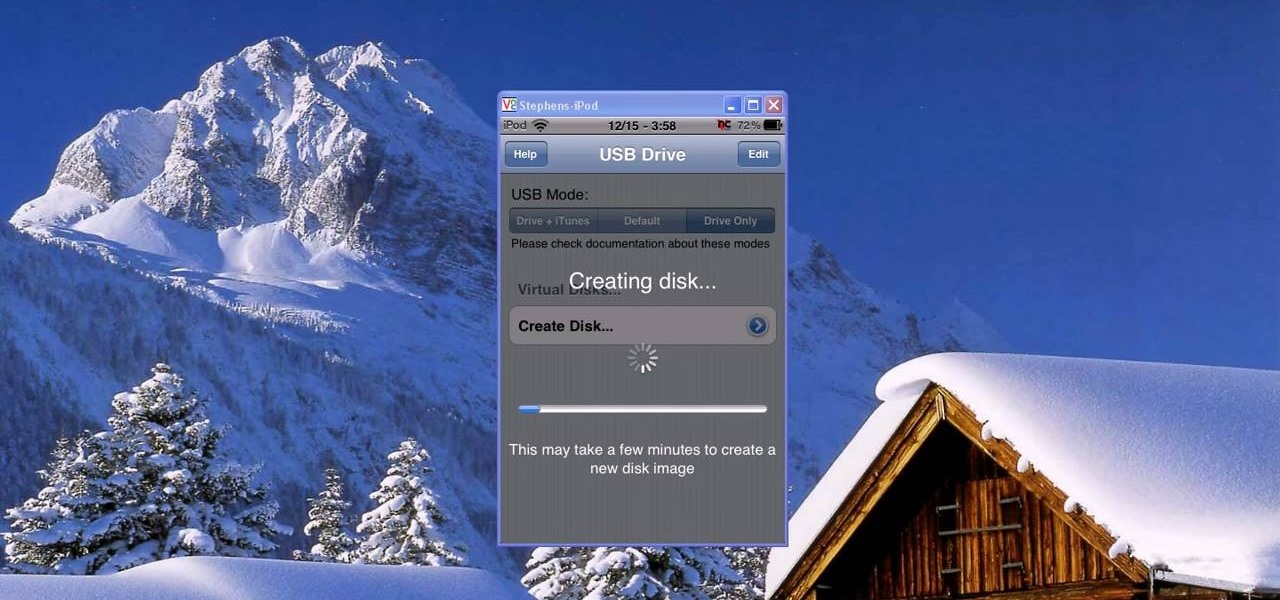
Did your USB just bite the storage drive dust, but you have a paper you have to print out within an hour for English class? Tap your technie magic wand on your iPod Touch or iPhone to turn it into a USB jumpdrive.

You're probably wondering why this handstand video is categorized for beginners. Well, it probably isn't actually for yoga newbies, but it will give those with basic yoga expertise an easy to follow way to perform an impressive handstand.

Watch this dance how to video and learn the Charleston Variation: Savoy Kicks. The Charleston is a dance named after Charleston, South Carolina. The dance became popular in the USA after the swing jazz 1923 song "The Charleston" by composer/pianist James P. Johnson came out. The Charleston soon became one of the most popular hits of the time period.

The cobra footwork is a straight line footwork speed skating technique. This trick was named after the "Cobra" snake for its snake like movement, or slither across the ice. Skate like a cobra. Fast and furious!

According to Japanese legend, folding 1,000 paper cranes in one year will guarantee your wish will come true. A young girl named Sadako did just that in 1955 and wished for world peace—the origami crane has been an international symbol of peace ever since.

A young Maori woman named Migoto (the name is Japanese takes the time to teach Nick (and you) some traditional Maori poi dancing.

Follow along with an overeager young magician named Dergen Brown as he teaches you how to do a classic pass card move. If you can ignore the comedy effort in the beginning, you'll learn this basic technique.

Format strings are a handy way for programmers to whip up a string from several variables. They are designed to save the programmer time and allow their code to look much cleaner. Unbeknownst to some programmers, format strings can also be used by an attacker to compromise their entire program. In this guide, we are going to look at just how we can use a format string to exploit a running program.

In iOS 13, Apple finally took the built in Files app from an extremely rudimentary file browser to a full featured app that can serve the needs of most any user. Among the new features is the ability to compress a file or series of files into a standard ZIP archive right from your iPhone.

Most users don't realize how much valuable data is in their network traffic. With a few simple tools, an attacker can quickly pick out cookies, passwords, and DNS queries from a macOS device as it covertly streams the victim's network traffic to the attacker's system. Here, we will cover two methods for analyzing packets flowing from a Mac.

HTC is working on another flagship device that's expected to be released in mid-April. After the disastrous reception of the recently released HTC U Ultra and HTC U Play, this new model could be the true HTC 10 successor we've all been waiting for.

Welcome back, everyone. In the previous part of this rapid-fire miniseries, we built the victim portion of the shell. Today, we'll be building the attacker portion. This script will initialize interaction with the victim portion of the shell, send commands, and receive the output.

Sideloading apps on Android is incredibly easy—you just have to enable "Unknown sources" in your device's Security settings, then you're free to run an APK installer file to get the app installed.

Welcome back, my greenhorn hackers! I recently began a series on scripting and have received such positive feedback that I'm going to keep this series going. As I've said before, to graduate from the script kiddie to the pro hacker, you'll need to have some scripting skills. The better you are at scripting, the more advanced your hacking. Ultimately, we are leading up to developing the skills to build your own zero day exploits.

When learning Wi-Fi hacking, picking a compatible Wi-Fi network adapter is the first step to learning to crack Wi-Fi passwords.

As we aim for a wireless world, technology's reliance on cloud computing services is becoming more apparent every day. As 5G begins rolling out later this year and network communications become even faster and more reliable, so grows our dependency on the services offered in the cloud.

Using just a small sticky note, we can trigger a chain of events that ultimately results in complete access to someone's entire digital and personal life.

It looks like Chris Urmson has spent the six months since he left Google's Self Driving Car Project trying to build a get-rich-quick self-driving unicorn, along with Sterling Anderson, formerly with Tesla Motors. At least that is one of several scandalous accusations in a Tesla lawsuit aimed at the pair, and their secretive startup Aurora Innovation, LLC.

Apple released the new Mac OS X 10.10 Yosemite in the Mac App Store for everyone to download and install for free on October 16th, 2014, but downloading a 5+ GB file for each of your computers will take some serious time. The best thing to do is download it once and create a bootable install USB drive from the file for all of your Macs.

Welcome back, my greenhorn hackers! Recently, I asked the Null Byte community what subject they would most like me to cover in future tutorials. Many of you cited scripting, and I decided it's best to cover this subject soon, so here goes.

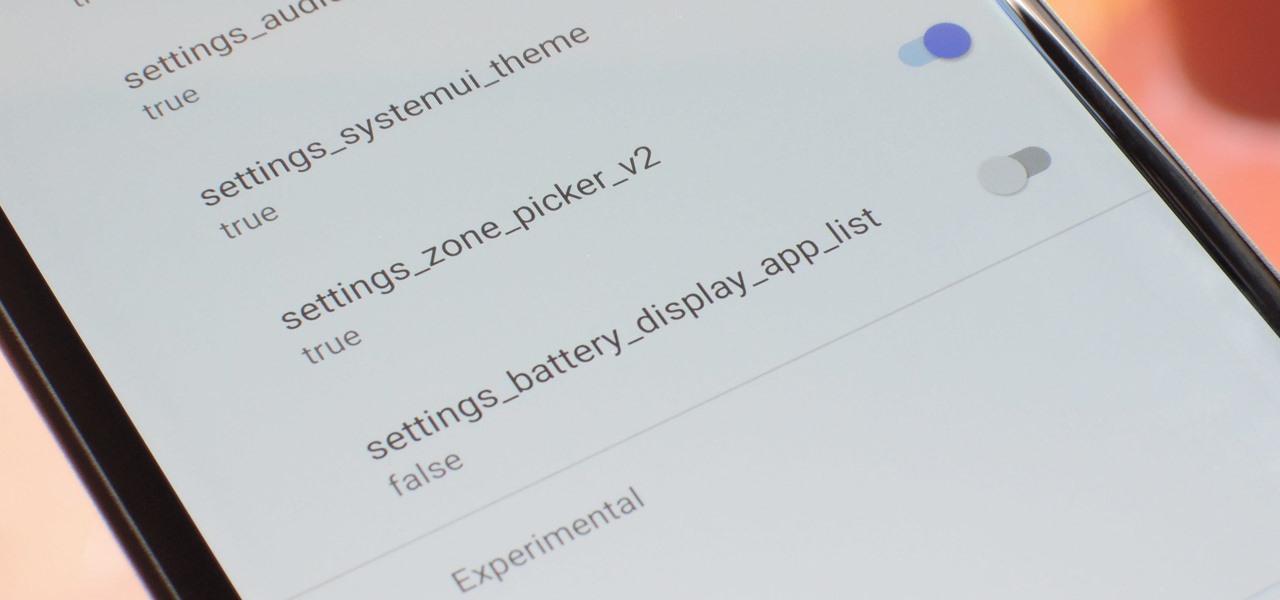
With every new Android update, hidden features are lurking under the surface. Google hides these options to prevent unnecessary tinkering by average users, leaving them in place for power users to discover. These secrets range from silly to really useful, with the latter opening up new ways to manage your phone.

Results of an early-stage clinical trial of an HIV vaccine could mean a hoped-for breakthrough in the battle against AIDS.

For some time now, there has been quite a bit of speculation as to when the selection of augmented and mixed reality head-mounted displays would begin to trickle out to the public. Pricing, availability, and software selection are all issues that will have to be addressed before widespread adoption will start.

You're all kale-d out, you've had it up to here with golden milk, and you're on the prowl for the next superfood. Well, get ready for some unicellular goodness: the next superfood is an algae named Spirulina, also known as Blue Majik. (Kudos to the marketing exec that came up with that, am I right?)

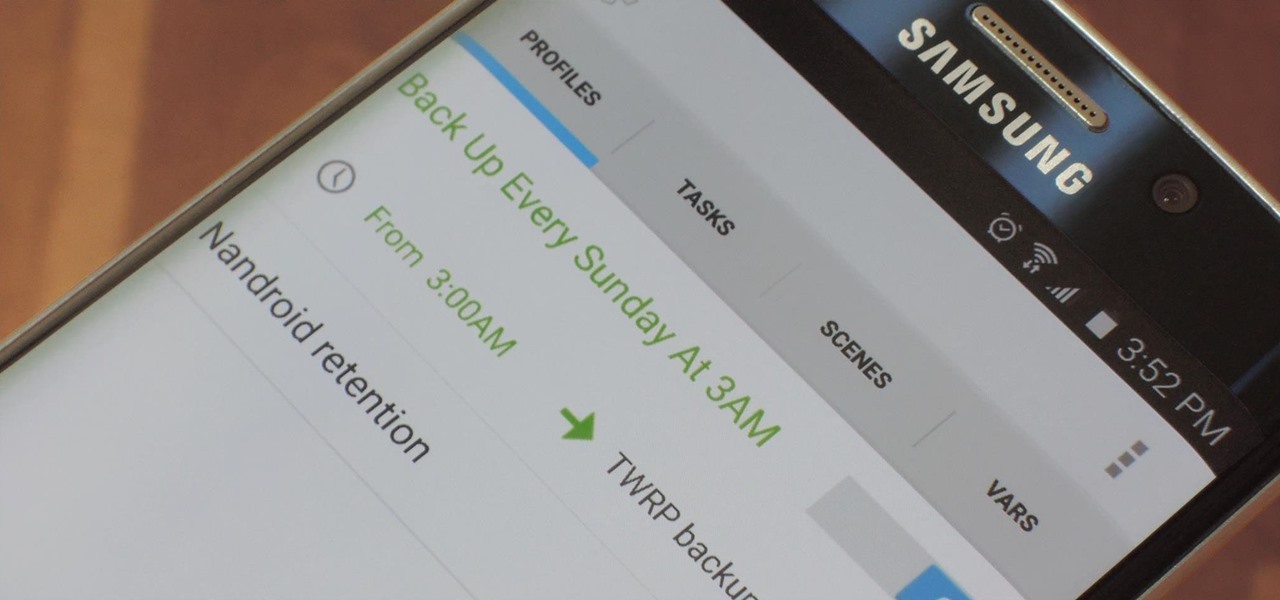
NANDroid backups are one of the best reasons to root your Android device and install a custom recovery. They're essentially a snapshot of your phone's entire operating system and all installed apps, so if you ever screw something up when installing a flashable ZIP or custom ROM, you can restore your NANDroid backup to get everything back to normal.

If you've switched ROMs before or flashed quick mods on your Android device, you've probably used TWRP or another custom recovery to install them. But another great purpose for flashing through a recovery is to install your own custom .zip file filled with everything a fresh ROM needs—namely, all your apps.