Welcome back, my novice hackers! As we saw in my first tutorial on Facebook hacking, it is not a simple task. However, with the right skills and tools, as well as persistence and ingenuity, nothing is beyond our capabilities.

Welcome back, my tenderfoot hackers! Hacker newbies have an inordinate fixation on password cracking. They believe that cracking the password is the only way to gain access to the target account and its privileges. If what we really want is access to a system or other resources, sometimes we can get it without a password. Good examples of this are replay attacks and MitM attacks. Neither requires us to have passwords to have access to the user's resources.

The kawasaki rose, named after famous origami folder and theorist Toshikazu Kawasaki, is known for its innovative geometric folds and mirror-symmetric crease patterns.

This video shows us the method to find the percent sign on Blackberry. The first step involves going to a place on the Blackberry where text can be inserted. This place is ideal for inserting a % sign. Look in the keypad carefully. There are various keys in it. Search for the key named 'SYM'. SYM stands for symbol. This key is helpful in typing various symbols in the text to be entered through the keypad. When the 'SYM' key is pressed, it opens a window containing various symbols. The % sign ...

In this dance how to video, Larry Payne demonstrates the sissone a la seconde ferme (to the second position closed), then en avant (in front), finishing with a "changement." The step sissone is named for the person who invented it. ballet move. This is a basic move for the beginning ballet dancer. Follow along with this dance tutorial and you can do the sissone a la seconde ferme ballet move.

This tutorial cooking video will teach you to make Japanese Kaisendon, a Japanese Sashimi rice bowl.

This tutorial video will teach you how to make Bukkake Udon, also known as Japanese cold udon noodles.

This tutorial video will teach you to make Zenzai and Anko, two Japanese red bean sweet treats. Ingredients for Zenzai and Anko

Well, it's up to interpretation as to whether this video shows you how to solve the Rubik's cube the easiest way. Use the set of Rubik's cube algorithms shown to you in this how-to video:

Directory traversal, or path traversal, is an HTTP attack which allows attackers to access restricted directories by using the ../ characters to backtrack into files or directories outside the root folder. If a web app is vulnerable to this, an attacker can potentially access restricted files that contain info about all registered users on the system, their permissions, and encrypted passwords.

Analysis of photographs and social connections can be a huge component of social engineering. Understanding who a person is, as well as who they know, can establish links within a company. This information could be used by hackers to execute elaborate social engineering attacks.

Your home has walls for privacy, but Wi-Fi signals passing through them and can be detected up to a mile away with a directional Wi-Fi antenna and a direct line of sight. An amazing amount of information can be learned from this data, including when residents come and go, the manufacturer of all nearby wireless devices, and what on the network is in use at any given time.

An attacker with shell access to a Linux server can manipulate, or perhaps even ruin, anything they have access to. While many more subtle attacks could provide significant value to a hacker, most attacks also leave traces. These traces, of course, can also be manipulated and avoided through methods such as shell scripting.

The Watch Dogs video game series came out in 2014, enamoring audiences with the idea of a seemingly magical smartphone that could change traffic signals, hack web cameras, and even remotely control forklifts. This may sound like science fiction, but The Sonic uses a customized flavor of Kali Linux to allow you to unleash the power of Kali from any smartphone — all without the need to create a hotspot to control it.

When Stardew Valley launched back in 2016 on Steam for PC, it was instantly deemed a success for steering the RPG farming simulator genre back on the right track. Before its release, we hadn't seen too much in this particular field of games that caught the eye of the general public. Since then, the mega-hit Stardew Valley has made its way to the mobile world of Android and iOS.

With an ordinary birthday card, we can introduce a physical device which contains malicious files into someone's home and deceive them into inserting the device into a computer.

Long admired for their active and cooperative community behavior, some types of ants also wear a gardening hat. Nurturing underground fungus gardens, these ants have a win-win relationship that provides food for both ants and fungi. If we humans understand it better, it may just help us out, too.

Our quest to find novel compounds in nature that we can use against human diseases —a process called bioprospecting — has led a research team to a small frog found in India. From the skin slime of the colorful Hydrophylax bahuvistara, researchers reported finding a peptide — a small piece of protein — that can destroy many strains of human flu and can even protect mice against the flu.

Welcome back to this series on making physical objects come to life on HoloLens with Vuforia. Now that we've set up Vuforia and readied our ImageTarget and camera system, we can see our work come to life. Because in the end, is that not one of the main driving forces when developing—that Frankenstein-like sensation of bringing something to life that was not there before?

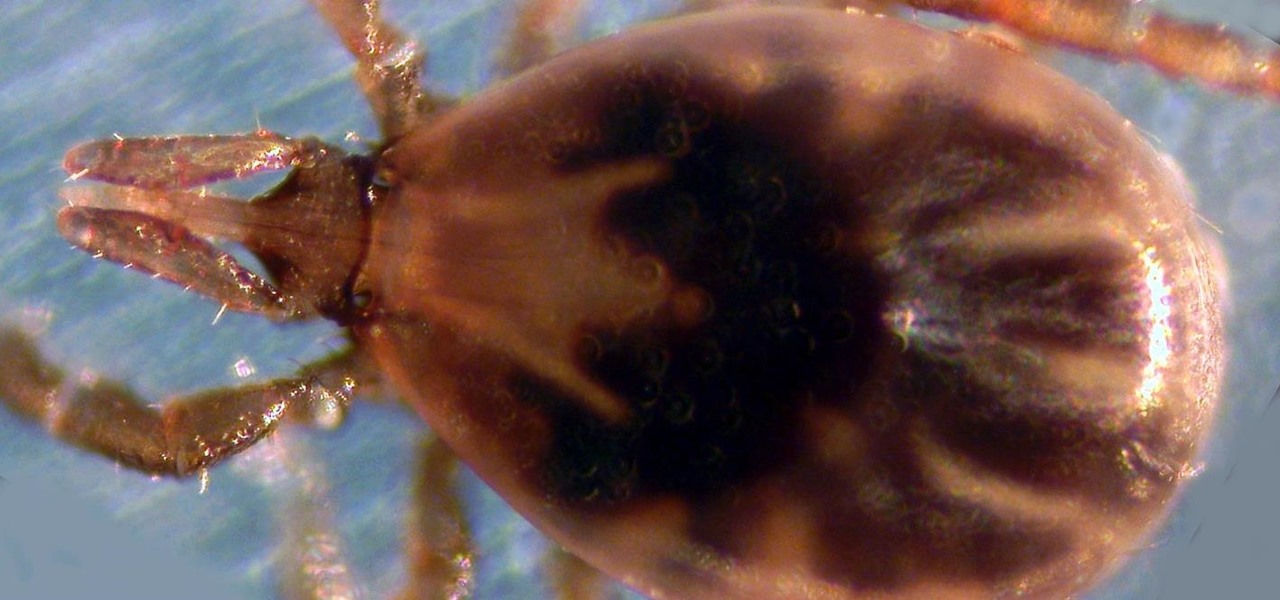
Transmitted by ticks, Lyme disease is a serious infection that is probably headed your way. A recent study confirms the pathogen that causes Lyme disease is now established in nine national parks in the East, including Acadia and Shenandoah National Parks.

With folks drawing lines in the sand before the upcoming election this November, it's important to know where you stand on some of the most important issues: the economy, foreign affairs, domestic affairs, and apples—caramel or candy apples, that is.

Counter-Strike is one of the most popular first-person shooters of all time, and deservedly so. What originally started out as a third-party Half-Life mod garnered such a cult following that Valve had to hire the developers and purchase the intellectual property to make it an official standalone release.

Welcome back! Sorry for the dry spell, but I've been rather busy setting up some side projects! If you remember back to a few training sessions ago, we covered basic file I/O. This is a very important step in making our scripts applicable in a real life scenario, and today we're going to further these concepts.

Welcome back, my budding hackers! One of the most basic skills the forensic investigator must master is the acquisition of data in a forensically sound manner. If data is not captured in a forensically sound manner, it may not be admissible in court. In my Kali Forensics series, I showed you how to acquire a forensically sound, bit-by-bit image of a storage device such as a hard drive or flash drive, but now let's dive into live memory.

Welcome back to another tutorial on functions. Last time, we looked inside memory to see what functions looked like in the flesh and all that Assembly was pretty nasty. At least you have some exposure to it. This time, we will be examining how functions work with the stack.

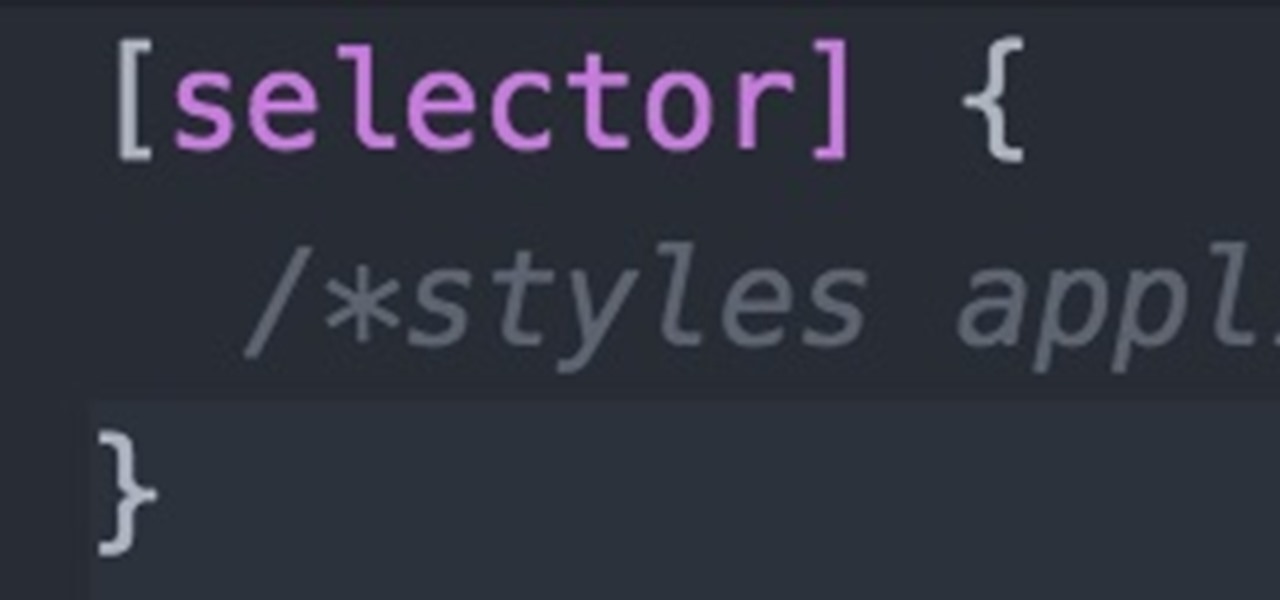
Welcome back Null-Byters! You finally have the pre-basics of CSS and we can begin with styling our web page. If you did not read our last adventure, I suggest you go and read it.

Hello fellow Null-Byters! In this "tutorial" we will be going basics of HTML. In the next tutorial, we will be going over CSS and then apply JavaScript.

Welcome back, my greenhorn hackers! Throughout this series on Metasploit, and in most of my hacking tutorials here on Null Byte that use Metasploit (there are many; type "metasploit" into the search bar and you will find dozens), I have focused primarily on just two types of modules: exploits and payloads. Remember, Metasploit has six types of modules:

Hi all, Pro Hackers/Crackers, Let's see how we can use batch for our own Protection instead of exploiting someone with it.

Welcome back, my aspiring hackers! Those of you who use Windows in a LAN environment understand that Windows machines can share directories, files, printers, etc. using "shares." This protocol dates back to the 1980s when the then dominant computer firm, IBM, developed a way for computers to communicate over the LAN by just using computer names rather than MAC or IP addresses.

Welcome to the first chapter of Excel is Simple, a place where we will burst all myths around excel and try to make it simpler and fun to use.

This is for people who are already proficient at doing basic pull-ups and chin-ups and want to take their training to the next level. It's also pretty funny for anyone who enjoys a bit of gym humor.

Learn how to make a paper origami teo flower instructions. This origami flower is my improvisation, and I haven't seen any similar flower from the nature. I named the flower to my wife Teofila (Teo) because i gave to her the first model of a complete paper flower :). The model is easy and the stamens make the flower looks one idea more beautiful :)

On June 5th, robotics firm Aldebaran and SoftBank Corp., the Japanese giant that owns Sprint (and possibly T-Mobile), unveiled an emotion-sensing robot named Pepper.

We Nexus users are fairly spoiled. There's a ton of third-party development for our phones, which translates to a virtually endless stream of custom ROMs being made available to us.

Welcome back, my rookie hackers! A short while back, I began a new series on database hacking, and now it's time to continue and extend your education in that field. As you know, the database contains all of the most valuable info for the hacker, including personally identifiable information, credit card numbers, intellectual property, etc. So, it's the ultimate goal of cybercrime and the APT hacker.

Welcome back, my rookie hackers! Several of you have written me asking about where they can find the latest hacks, exploits, and vulnerabilities. In response, I offer you this first in a series of tutorials on finding hacks, exploits, and vulnerabilities. First up: Microsoft Security Bulletins.

Welcome back , my fledgling hackers! Lately, I've been focusing more on client-side hacks. While web servers, database servers, and file servers have garnered increased protection, the client-side remains extremely vulnerable, and there is much to teach. This time, we'll look at inserting a listener (rootkit) inside a PDF file, exploiting a vulnerability in Adobe's Reader.

Video: . Steel wool fire Photography

Pythagoras was a smart man, so smart that his mathematical theory is named after him and still used today, more than 2,000 years later: the Pythagorean theorem. It implies that the square of the hypotenuse of a right triangle is equal to the sum of the squares of the other two sides. The Pythagorean theorem is a cornerstone of geometry. Here’s how to use it.