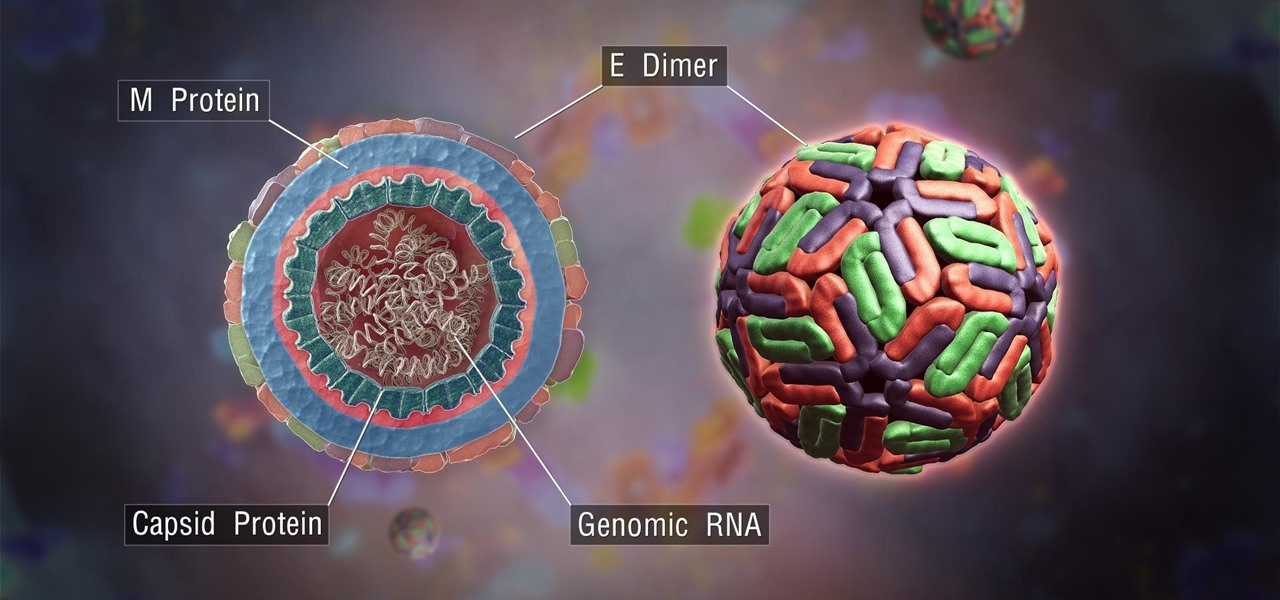
The Centers for Disease Control and Prevention (CDC) just reported some upsettingly high numbers of human papillomavirus (HPV) in adults. In data retrieved from 2013–2014, 22.7% of US adults in the 18–59 range were found to have the types of high-risk genital HPV that cause certain cancers.
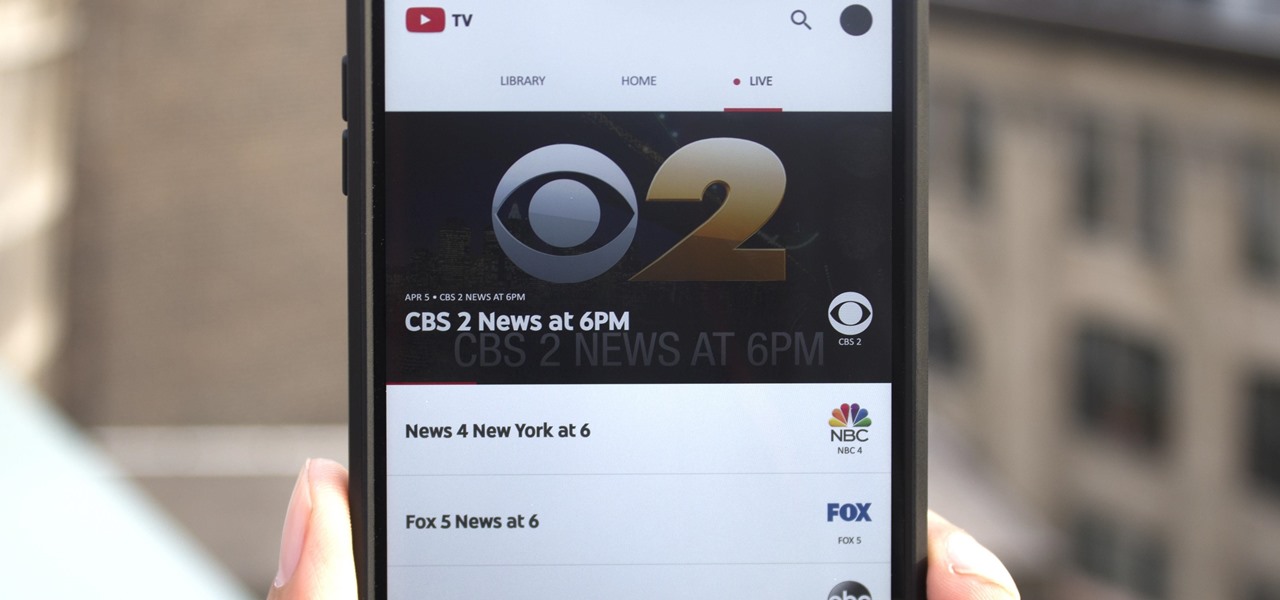
As you may have heard by now, YouTube has launched its own live streaming TV bundle available for users in the select markets of New York, Los Angeles, the Bay Area, Chicago, and Philadelphia. A subscription to the new streaming YouTube TV bundle costs $35 a month, but the service is drawing in users by offering a free 30-day trial.

Lightform might just be the thing to have at your next party. The San Francisco-based company just created the first computer ever able to connect to a projector and instantly scan 3D scenes to mix reality with projected light.

Huawei is making a fresh attempt at launching into the US market to challenge Apple and Samsung's monopoly on premium smartphones. In its latest attempt to break into America, Huawei is trying to get its Chinese mobile chipset accredited by AT&T.

Yes, bubonic plague—the Black Death that killed millions in the Middle Ages— is still out there. It even infects and kills people in the United States. Without treatment, half the people infected die, but the Food and Drug Administration approved ciprofloxacin in 2015 to treat plague, and it has just successfully been used to stop the infection in five people.

Jostled in the airport, someone is coughing in line. The air looks empty but it is loaded with microbes that make their way into your body. You get sick. You give it to your family, and that's pretty much it. But what if you were so contagious that you spread it to your entire community and beyond?

We usually associate Salmonella bacteria with a dangerous type of food poisoning, but they actually are pretty good at seeking out tumors. That trait made the bacteria a great candidate to deliver a protein that would help knock tumors out.

A recent study underscores a connection between climate change and infectious disease, raising concerns about our quickly warming planet.

No one can dispute the evolutionary success of bugs. The oldest insect fossils were found encased in crystallized mineral silica in Scotland in 1926, and they're between 396 and 407 million years old.

The mention of Zika can strike fear in the hearts of pregnant women. With infections increasing around the world, including in the US, researchers are fighting the clock to figure out how the virus can have such horrific effects in some people.

In this episode of Have You Seen This?, we will look at Oriental Museum by 247 Technology Limited, a free application in the Windows Store for HoloLens. Museum exhibits seem to be a popular theme amongst the demonstrations going up, so let's see how this one looks.

Paranoid Android has always been one of the most popular custom ROMs because of the inventive features its developers add to Android. Two of the biggest draws in particular have to be the "Halo" notification bubble, and the "Pie" navigation buttons, which can both fundamentally change the way you interact with your device.

We're almost there to completing the setup of your Mac for hacking! Now that we have Git and Homebrew under our belts, it's time to take on something fairly easy, but very important for our hacking needs.

This morning, Google opened a pop-up showroom where anybody can visit to get a hands-on look at the new Made by Google hardware lineup. At 10 am the line at 96 Spring st, in the SoHo neighborhood of New York City, was growing but still manageable. As we waited to be ushered in, Google representatives came by to offer us coffee drinks prepared by a pair of baristas in the Peddler Coffee cart parked on the curb. "Now that's latte art," said the guy in line next to me when he saw that the foam-t...

A few months ago, LlabTooFeR leaked a full system dump from Google's then-unreleased Pixel and Pixel XL smartphones. That may not seem like a big deal at first glance, but the system dump contained all of the preinstalled apps and services from Google's new flagships—including the much-anticipated Google Assistant.

Guys, this has got to stop. It's not funny anymore. I'll defer to one of my all-time favorite people when it comes to my feelings on this unsavory subject:

Koji is a culture made up of a certain fungus (mold) called Aspergillus oryzae, which has been used to ferment rice and soybeans in Japanese, Chinese, and Korean kitchens for centuries. Koji can actually have other involved fungi, but Aspergillus oryzae is the most common, and therefore the names can be used interchangeably. Its end purpose is to enhance the flavor of items like soy sauce, sake, and miso.

One of Android's biggest strengths is its ability to interact with other operating systems. When you plug your phone into your Windows PC, you instantly see all of the files it holds—and all it takes is a simple syncing app to do the same with Mac. To top that off, apps like Pushbullet and Join bridge the gap even further by allowing you to share links, files, and messages between all of your devices.

Welcome back my, tenderfoot hackers! Many people come to Null Byte looking to hack Facebook without the requisite skills to do so. Facebook is far from unhackable, but to do so, you will need some skills, and skill development is what Null Byte is all about.

Welcome back, my novice hackers! As many of you know, recon is crucial to a successful hack/pentest. In most cases, hackers spend more time doing good reconnaissance than actually hacking. Without proper recon, you are simply guessing at what type of approach or exploit is going to work and, as a result, your time is wasted without any useful outcomes.

Cable TV providers were dealt a pretty significant blow on Thursday, February 18th, 2016, when the Federal Communications Commission decided that customers should have a choice in what type of device they use to watch cable, instead of being forced to rent a set-top box.

For many people, the two main advantages of buying a Nexus device are prompt updates and the ability to root without much hassle. But in a cruel twist of fate, these two features are almost mutually exclusive, since OTA updates will refuse to run on rooted devices.

Home cooks are often quite intimidated when trying to reproduce the delicious ethnic dishes they enjoy at various restaurants. Thankfully, there are definite flavor profiles and spice/seasoning/herb combos that are very specific to various regional cuisines and cultures; with a little guidance, you can create dishes that are tasty homages to the cuisines you love to eat. In this two-part article (second part here), I'll cover both categories and sub-categories of some of the most popular ethn...

Welcome back everyone. As many of you know, reconnaissance is extremely important in any successful hack. Without proper reconnaissance, we won't know what we're about to get into, literally.

School internet filters serve a valid purpose—they keep students from wandering off into the deep corners of the web while still allowing at least some internet access. But a lot of these restrictions are completely ridiculous, to the point where some school districts block access to the educational material in National Geographic or forbid searching terms like "China," "Iran," or "Russia"—because, you know, breasts and commies.

When attempting to compromise a target, we want as much control as possible over the victim. Metasploit's meterpreter allows us to have immense control over the victim, the only issue is that sometimes we can't land a meterpreter. We may only be able to land a standard shell, but fear not, there is a way to upgrade our shell into the all powerful meterpreter!

In response to the success of Apple Pay and an attempt to stave off the appealing Samsung Pay service, Google is completely revamping Android's mobile payments system. Instead of just using Google Wallet as an app to make payments with your phone, a new service called Android Pay, with an extensive underlying framework and API, will soon make its debut—and maybe even sooner than you'd think.

There are plenty of legitimate reasons that you might want to record a phone conversation. Let's say you operate a business and take orders over the phone, and you don't want to miss an item. Or perhaps you need to jot down some notes from a recent conference call, and things were just happening too quickly in real time.

If your Android device wasn't manufactured by Samsung, chances are it uses on-screen navigation buttons. Colloquially referred to as "Soft keys," these have become commonplace due to their flexibility, as well as the fact that manufacturers don't have to include extra hardware buttons with a propensity to fail.

Researchers at the cyber security firm Zimperium have recently uncovered a vulnerability in roughly 95% of Android devices that has the potential to allow hackers to take total control over your phone with a simple picture message (MMS). The gritty details of this exploit have not been made public yet, but hackers now know the general framework for this type of attack, so you can be certain that they'll hammer out the details in no time.

There are many reasons to root Android, but for me, the most important one is to have the Xposed Framework. Xposed gives you access to hundreds of modules, which take away the need to manually modify core system files to add new features and functionality to your Android device.

When it comes to smartphones, the biggest complaint voiced by most users is battery life. Sure, it's unrealistic to expect your Android device to run for weeks without a recharge, but many folks struggle to even make it through the day without having to top off their battery.

Welcome back, my hacker novitiates! Eluding and evading antivirus software and intrusion detection systems is one of the most critical tasks of the hacker. As soon as a new exploit is developed and discovered, the AV and IDS developers build a signature for the attack, which is then likely to be detected and prevented.

Welcome back, my hacker novitiates! As you know by now, the Metasploit Framework is one of my favorite hacking tools. It is capable of embedding code into a remote system and controlling it, scanning systems for recon, and fuzzing systems to find buffer overflows. Plus, all of this can be integrated into Rapid7's excellent vulnerability scanner Nexpose.

Welcome back, my tenderfoot hackers! Those of you who have been reading my posts here for awhile know how much I emphasize good reconnaissance. Novice hackers often jump into a hack/exploit without doing proper recon and either fail or get caught. Experienced and expert hackers know that 70-80 percent of a good and successful hack is dependent upon successful and accurate reconnaissance.

When you're actively using your phone, a certain amount of battery drain is to be expected. But, if your device is just sitting in your pocket draining its battery, that's when you need to take action.

Check it out: you save more dough (ba dum bump) when you order a large pizza than with any other size. Why is this true? NPR reporter Quoctrung Bui's engineer friend pointed out that a medium pizza was twice as big as a small one, yet only cost slightly more.

With all of the personal data that's stored on our smartphones, it's of vital importance that we have some sort of lock screen security enabled. One of the Galaxy S5's killer features is obviously the fingerprint scanner. It makes the process of dealing with a secure lock screen a bit easier than typing in a password or PIN.

One of the best things about the Nexus line of devices is the ease with which one can achieve root. Plug your phone into your PC, download a couple files, type a few commands, and you can be rooted within 30 minutes. No muss, no fuss, no carrier-locked bootloaders.

Back in August, Google introduced Android Device Manager. This new service allowed you to locate, lock, or wipe a lost or stolen Android device from either a companion app or a web interface. Effectively, this is the "kill switch" that legislators are clamoring for.