The search for the causative agent of colony collapse—the mass die off of honey bees throughout the US and Europe—has escalated with increasing confusion lately. Everything from pesticides and stress to viruses and mites have been implicated, and some researchers think that many of these environmental factors work together to take down hives.

When Kaci Hickox, a Doctors Without Borders nurse, returned to New Jersey from working with Ebola patients in West Africa in 2014, she was surprised by her reception. Instead of a quiet return to her home in Maine after four weeks on the front line of Ebola treatment, she was quarantined by the State of New Jersey in Newark. She later filed a lawsuit in U.S. District Court for violation of her civil rights, false imprisonment, and invasion of privacy.

Bacteria gets a bad rap. Most headlines focus on the danger and discomfort posed by pathogens like bacteria, but many of the bacteria that live on and in us are vital to our health. Many products out there, called probiotics, are sold with the implication that they're supporting these healthy bacteria that share our bodies — but do they actually work?
And so it begins... CES 2017 is upon us! This is a very exciting time for those who are looking out for the newest innovations and releases from the world of technology. I said this was going to be a fun week, and here we start it with a bang from smartglasses developer Osterhout Design Group (ODG).

Google is on a mission to bring a better messaging experience to Android users. We've seen them try and fail over the years with various messenger apps, but this time, they're taking a different approach by working with industry leaders to create a new messaging standard. The result is RCS Universal Profile, or simply Chat, and it's finally catching on.

This is the very first article in my series on setting up a Mac for hacking. In this series, I will be operating under the assumption that you have a clean install of macOS (previously OS X). If you aren't starting with a clean installation, there may be a few differences, but nothing we can't help you out with.

Pokémon GO made waves as the first augmented reality game to gain popular adoption. In fact, it was so popular that it only took a few days to uncover some the benefits and serious issues with combining physical and digital worlds.

New releases of iOS are always pretty exciting. I remember the anticipation buildup of iOS 7 before it was announced at WWDC 2013, as it was expected to be a complete game changer compared to previous versions—and it was.

Starting with the release of Android Lollipop, the process of installing the Xposed Framework got a bit more complicated. Not only are there separate installers for each Android version, but now, you also need to know exactly what type of processor is in your device to make sure you're downloading the right files. In fact, CPU architecture is becoming a factor in more and more scenarios these days, including certain sideloaded app updates and, of course, custom ROMs.

Welcome back to control structures, part two featuring the three types of loops. Here we go! What Is a Loop?

In recent weeks, some people have been shunned from the Null Byte community because they expressed "black hat" aspirations. This is because Null Byte is the "white hat" hacker training/playground. Although most of us think we know what that means, it does beg the question; "Who and what is a white hat hacker?"

In the recent hit movie Furious 7, the storyline revolves around the acquisition of a hacking system known as "God's Eye" that is capable of finding and tracking anyone in real time. Both the U.S. spy agencies and an adversarial spy agency (it's not clear who the adversary is, but the location is "beyond the Caucasus mountains," which could imply Russia?) desperately want their hands on this system.

Welcome back, my fledgling hackers! Over the years, we have examined multiple ways to own, exploit, or compromise a system. On the other hand, we have not spent a lot of time on denial-of-service (DoS) attacks.

Nothing gets me functioning in the morning better than strong coffee. And if I'm going to start my day with a dreaded workout, that steaming cup of caffeine is the exact motivation I need to get going. Although coffee might not seem like the best beverage to drink before hitting the gym, it actually has a few hidden benefits over water that may surprise you.

Welcome back, my rookie hackers!

Welcome back, my hacker novitiates! In the previous two posts in this series, we looked at the basics of buffer overflows. In this post, we will look at one technique for finding buffer overflows. We will try to send random, oversized, and invalid data at a variable to see whether we can make it crash or overflow. This process is known as fuzzing. It is often the first step to developing an exploit, as we need to find some variable that is susceptible to overflowing.

It's been a while when the major web browsers first introduced HTTP Strict Transport Security, which made it more difficult to carry Man In The Middle (MITM) attacks (except IE, as always, which will support HSTS since Windows 10, surprised?).

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Each flavor of sake, the national spirit of Japan, comes with its own fans, not unlike whiskey aficionados here in the States. While sake is often called "rice wine," it is more akin to a malted beverage like beer.

In the aftermath of the unindicted police killings of Michael Brown and Eric Garner, we've been told that the system worked as intended. When our legal system's outcome is at conflict with what a majority of Americans believe is just, it's clear that some changes are needed. But what specifically needs to change? And what can an average citizen with a moral and just cause do to prevent these kinds of tragedies from repeating themselves again and again?

Apple Pay has been available to use in stores, as well as in select apps and websites, ever since its first appearance in iOS 8.1. Now, with iOS 12, there are currently 13 different iPhone models that support Apple Pay functionality without the use of an Apple Watch, and the list of partnered stores that accept Apple Pay has only grown. Here's our always-up-to-date list to keep you in the know.

Cold brewing tea and coffee are all the rage, and for good reason: they're idiot-proof. I, personally, am a total dunce at brewing coffee. It either ends up strong enough to peel paint from a car or so weak that you can see through it. Meanwhile, I have friends who inevitably brew green tea to the point where it's painful to drink it.

Old habits die hard. It may be a cliché, but it's undeniably true, especially when it comes to the bad ones. Nail-biting, fidgeting, and overspending can label you as someone who is obsessive-compulsive, overly nervous, and routinely stressed out, but you can make the break less painful with a few simple tweaks to your routine and by understanding how your habits work.

Update: June 19, 2014 Android 4.4.4 has been released, fixing a small security bug in 4.4.3. The factory images have already been made available to all current-generation Nexus devices, and I've linked them out below. This does not affect the process depicted, you can still use these same steps to bring your device up to date with this latest release.

Welcome back, my fledgling hackers! As nearly everyone has heard, Target Corporation, one of the largest retailers in the U.S. and Canada, was hacked late last year and potentially 100 million credit cards have been compromised. Happening just before Christmas, it severely dampened Target's Christmas sales, reputation, and stock price (the company's value has fallen by $5B).

Autumn is a time of year when everything looks, smells, and tastes good. The scents of cinnamon and spices are everywhere you go, and even the dead leaves that fall off the trees are pretty. In particular, the fruits and vegetables of the season are gorgeous.

Welcome back, my hacker apprentices! Metasploit framework is an incredible hacking and pentesting tool that every hacker worth their salt should be conversant and capable on.

You'd think the ability to block calls from certain numbers would be built in to most phones by now, but that's certainly not the case with the iPhone.

The very first text message was sent on December 3rd, 1992 by Neil Papworth, an engineer for Vodafone, and it simply said "Merry Christmas." He may have jumped the gun on the whole Christmas thing, but you trying coming up with the first text message in history!

UPDATE (February 26, 2014) Yesterday, the U.S. House of Representatives passed H.R. 1123 with a 295-114 vote decision. The ruling repeals the 2012 Library of Congress (LOC) decision that limited the ability to legally "unlock" your smartphone (see below).

OSAGYEFO DR. KWAME NKRUMAH (1909-72) Founder and Father of the Nation Osagyefo Dr. Kwame Nkrumah, the first Prime Minister and President of Ghana, stands out not only among the Big Six but also among the greatest statesmen of history. It was he who canalized the discontent of the people of the Gold Coast Colony into the highly organized movement of protest against British rule, and within a relatively short period won political independence for Ghana on March 6, 1957. With Ghana independent, ...

Today's post is a small go-to guide for beginner programmers in Null Byte. With many of our community members picking up programming from our Community Bytes, it only makes sense to lay out a one-stop guide for your reference. Hopefully this guide will help you make an educated and thoughtful choice on what programming languages you want to learn, and how you want to learn said languages.

This is an overview of gymnastics ant tumbling for beginners. Sibylle is a former German National Gymnastics Champion. Sibylle has coached thousands of students since 1984.

On July 20, 1969, humans set foot on the moon for the first time. But some say our microbes beat us there. With the Space Age came new questions about microscopic invaders from outer space and concern about where we are leaving our microbial footprints. The questions are even more relevant today.

To play in the World Cup, soccer's ultimate tournament, you have to be among the best players on the planet. For the rest of us, Google has a hidden game to simulate the thrill of scoring goals for your favorite team.

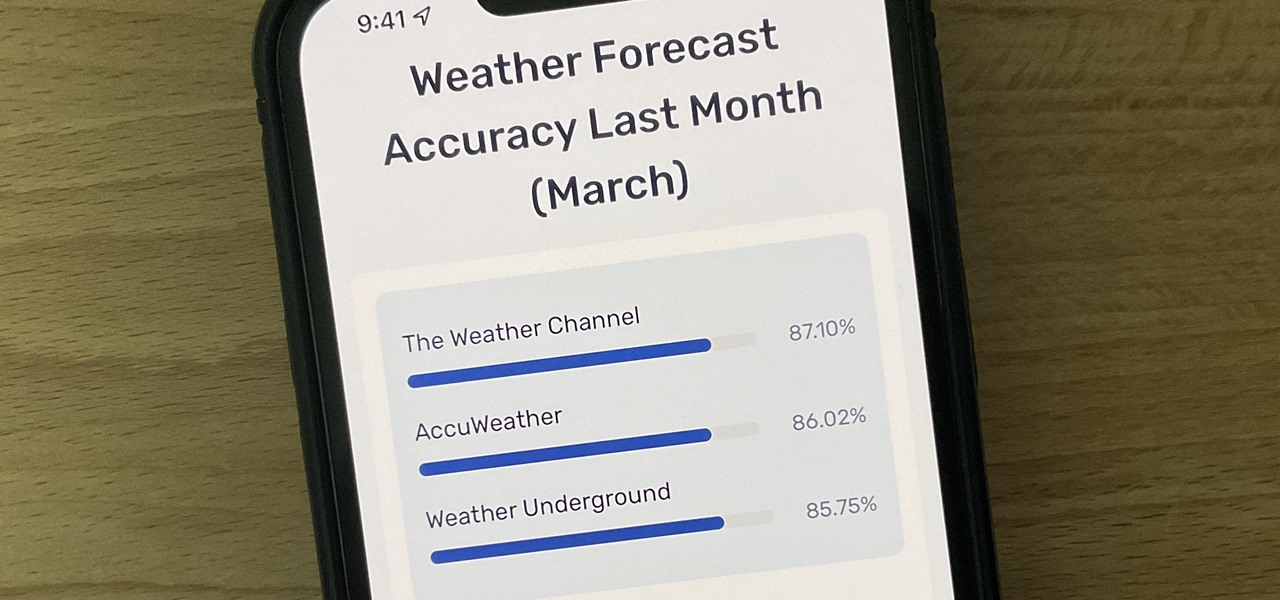
Not all weather sources are equal. When you're looking at the forecast, you hope that it's at least semi-accurate so you can plan the week and days ahead, but many sources are unreliable. And with the famous Dark Sky API shutting down on March 31, 2023, you'll need an alternative source of weather information if you use an app that utilizes that API.

"Unfortunately, no one can be told what the matrix is, you have to see it for yourself." That's the line just before Morpheus gives Thomas Anderson (aka Neo) the red pill, finally opening his eyes to the tapestry of code that has veiled his eyes for his entire life.

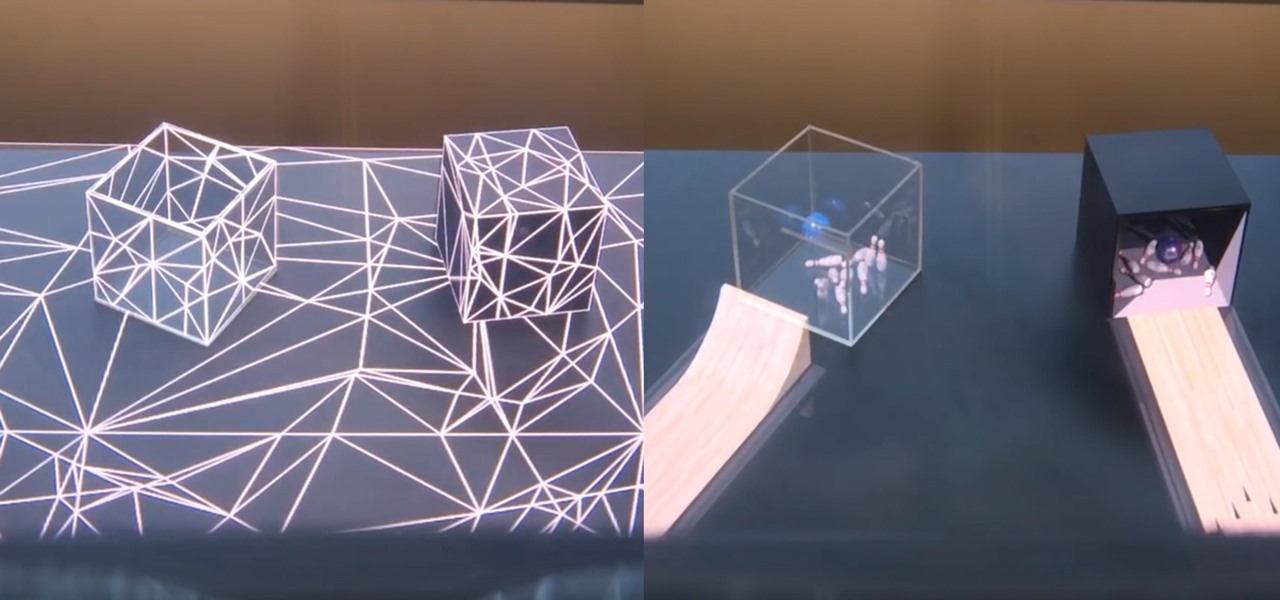
One app is continuing to make a name for itself as the go-to platform for celebrity art that transcends canvas and paint and moves in augmented reality.

While Snap may eventually compete with Apple and Samsung in selling smartglasses to consumers, today it is helping them achieve their business objectives via augmented reality.

After piloting the Nreal Light in South Korea and Japan via carrier partnerships and securing another round of funding, Nreal is now ready to begin selling the consumer edition of the smartglasses to the western world as well as introduce a version for enterprise customers.