A recent pathogen outbreak in Illinois is just one of many outbreaks of an underappreciated, but serious, viral infection passed from rodents to humans. These hantaviruses have been cropping up more frequently in the last decade or so, giving us more reason to clean out our dusty attics, basements, and garages.

With the height of the flu season ahead, there are some good reasons to keep a flu vaccination in mind.

With folks drawing lines in the sand before the upcoming election this November, it's important to know where you stand on some of the most important issues: the economy, foreign affairs, domestic affairs, and apples—caramel or candy apples, that is.

Seriously, what's with all of the candy corn hate? I don't care what anyone says, candy corn is and always has been the perfect Halloween snack for me. Only recently did I realize that not everyone gets as hype as I do about small, sugary vegetables.

Welcome back, my greenhorn hackers! In many cases when a computer, phone, or mobile device is seized for evidence, the system will have graphic images that might be used as evidence. Obviously, in some cases these graphic images may be the evidence such as in child pornography cases. In other situations, the graphic images may tell us something about where and when the suspect was somewhere specific.

We all know them, and many of us despize them. And some might support them, regardless many have different opinions.

When you look at an Italian flag, what do you see? Green, white, and red? Well, I see a Caprese salad. And no, I do not need to have my vision checked. It simply means that I have the eyes of a chef.

No one ever wants to experience pain, whether it's as small as a stubbed toe or as great as recovering from surgery. Yet so much of our lives causes pain, lasting or brief in its form. With a few mental tricks and unusual home remedies, you can relieve some of the most common aches and ailments that arise painlessly.

Any beer aficionado who's been to Ireland will always talk about how the Guinness there "just tastes different." But save your eye rolls, skeptics: it turns out your favorite lagerhead actually has a valid point.

Tagine is both the name of a cooking vessel and also the dish that is cooked within it. In fact, some might say tagines are the national dish of Morocco. These slow-cooked stews and braises, often combining meat, vegetables, spices, and dried fruits, have a character unlike anything I've ever eaten.

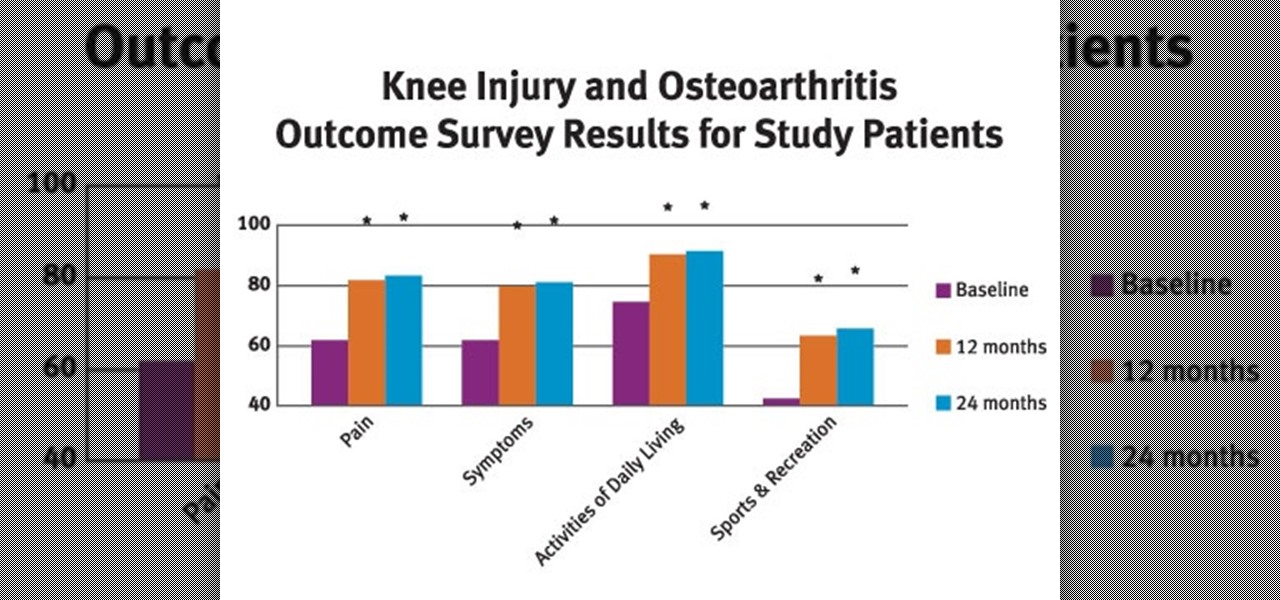
Osteoarthritis can affect every gender and at any age but it commonly occurs in women than in men. In America there are approximately 27 million Americans aged over 25 who live with osteoarthritis.

It's nice to have a drink on an airplane, whether you're taking a flight somewhere fun or for work. However, what's not so nice is the high prices and relatively bad quality of the liquor that's available.

Like Costco's price codes or the tags on your bread, the numerical codes printed on those sticky little fruit and vegetable labels can reveal a lot of information to us consumers. Once you understand the codes, you can look at that little label (also known as PLU, or "price look up" label) and know whether the produce you're about to buy or eat was treated with pesticides, genetically modified, both, or neither. Before we go any further with deciphering the codes on these labels, let's take a...

"Does bottled barbecue sauce even taste that bad?" a friend of mine asked. Well, truthfully, no. But it also doesn't taste that good, especially if you've had truly great barbecue or even your crazy uncle's homemade sauce at a holiday cookout.

When you come home from the grocery store, you probably put away every single fruit and vegetable in the bins and drawers in your refrigerator. Any fifth grader knows that fridges work to preserve food, thus everything should go in there, right? Nope!

Welcome back, my nascent hackers! Earlier, I wrote a guide on finding operating system and application vulnerabilities in Microsoft's own security bulletins/vulnerability database. In this tutorial, I will demonstrate another invaluable resource for finding vulnerabilities and exploits by using the SecurityFocus database.

As practically the entire Steampunk world knows by now, IBM has predicted that Steampunk will be the big new trend from 2013 to 2015. They based this prediction on their computers, which sift through broad swathes of the internet in order to see patterns that may help commercial industries. According to them, Steampunk has been on the rise for the last few years, and they predict that it will explode into peak popularity within the next two years. But what does that mean and how will it impac...

A bouquet of roses is a lovely thought but will quickly wilt and die. Give your loved one a bouquet of roses that will last for years to come and it will only cost you the price of a pencil and paper. They’re quick and easy to sketch.

Treasure may be buried as close as your own backyard. If you have some time to kill, try the art of treasure hunting. You’ll be sure to discover lots of interesting thing after learning how to use a metal detector to look for treasure.

It takes more than a kicky costume to become a professional wrestler. Start young to build up your basic wrestling skills and athleticism. To turn pro you’re going to need some acting flare, love for performing and a little luck.

Summer is almost here and you’re looking forward to that exotic vacation but you are going to need a passport and photos to go in it. There are a few simple ways to get a photo for your application. Find the method that is best for you and get traveling.

Bennett's fracture takes place at the base of the thumb. It typically occurs when an individual falls on an outstretch hand. The force is directed this way; the fracture occurs here. Learn how to diagnose and treat a Bennett's fracture in this medical how-to video.

A dislocated shoulder involves movement of the ball of the humerus away from the ball and socket joint. Ninety-five percent of the time, it will come out anteriorly when an individual's arm is forcefully pushed backwards and rotated in such a way that the ligaments in the front of their shoulder tear and the ball will pop out the front of the shoulder. This is a very common injury seen in contact sports. Learn how to diagnose and treat a dislocated shoulder in this medical how-to video.

Today's cheerleading incorporates difficult stunts and gymnastics into the routines. ESPN even now broadcasts the National High School Cheerleading Competition nationally! Madonna, Paula Abdul, Sandra Bullock and even Ronald Reagan were all cheerleaders! So if you or your children want to crack next year's squad, learn from our expert Shyra Fernandez. Shyra will show you the correct way to perform various advanced jumps and stunts that will get you on your way to being a "crack" cheerleader.

In this online video series, learn judo techniques from 12 time U.S. National Masters Champion Sensei John T. Anderson, as he demonstrates moves such as the compression arm lock, forearm lock, Hadaka Jin rear stranglehold, breakfalling, Juji Gatame cross lock, Kate Te Jume stranglehold, Kisa Katame, straight arm lock, Tai Otosha body throw, passing guard, Ko Uchi Gari major inside reap, leg throw, arm entwining, and Uke Otoshi hand drop.

Valentino Moutafov studied at the National Sports Academy in Sofia, Bulgaria. He has 20+ years teaching & coaching experience, and has competed in mixed pair & men's pair acrobatics.

Sibylle Walters founded Flairs Gymnastics in 1990. She is a former German National Gymnastics Champion.

Richard has been an avid pool player for the past 25 years and has played in competitive team and singles events since 1993. He has finished in the top ten percentile in both BCA national and VNEA international tournaments.

We've all attempted to fold a paper airplane before, right? One we hoped would sail majestically through the air for a good while but just ended up nose-diving into the grass. Paper planes, an invention likely as old as paper, are models of engineering; and they must account for the same dynamics as real planes, from drag force to stability to weight. So what is the perfect design?

If the importance of augmented reality and VR hardware to Facebook's future wasn't already clear enough, a shake-up in the executive ranks at the company has made it as clear as smartglasses lenses.

Linux is a diverse and powerful operating system that virtually every IT professional must learn and know well. Whether you realize it or not, you have likely already used a Linux device, and learning to design things for it is a key step in any Data Science career path.

While there are completely legitimate reasons to use Bitcoin, it's also used by terrorists, drug dealers, and other shady people that need to be investigated. That's where SpiderFoot comes in, which has a command-line interface to search for Bitcoin wallet addresses on a website and query the balances associated with them.

The amount of information we see on a daily basis is overwhelming. Then there's all the data we never even see. If your career depends on making sense of all of this information, you need to understand the programs that do the heavy lifting.

No longer strictly relegated to the realm of science fiction shows and novels, artificial intelligence can be found behind important technologies that are driving innovation throughout the world. From space exploration and self-driving cars to data science and marketing algorithms, AI is the driving force behind many technologies that are moving humanity forward.

It is well documented that what you say and do online is tracked. Yes, private organizations do their best to protect your data from hackers, but those protections don't extend to themselves, advertisers, and law enforcement.

Wi-Fi networks come in two flavors: the more common 2.4 GHz used by most routers and IoT devices, and the 5 GHz one offered as an alternative by newer routers. While it can be frustrating to attack a device that moves out of reach to a 5 GHz Wi-Fi network, we can use an Alfa dual-band adapter to hack Wi-Fi devices on either type of network.

MIT artificial intelligence researcher Lex Fridman recently asked SpaceX and Tesla founder Elon Musk possibly the best question he's ever been asked: What would he ask a hypothetical AGI system (an AI system with human-level intelligence and understanding) if he only had one question?

It's been said time and time again: reconnaissance is perhaps the most critical phase of an attack. It's especially important when preparing an attack against a database since one wrong move can destroy every last bit of data, which usually isn't the desired outcome. Metasploit contains a variety of modules that can be used to enumerate MySQL databases, making it easy to gather valuable information.

The words of three of tech's most important executives in the last 48 hours are providing some valuable insight into the near term future of augmented reality and the cloud infrastructures that support it.