The video shows us how to use a proxy to bypass the Internet Filters. Most of the times in our schools and colleges most of the websites including the social networking ones will be blocked for security reasons and makes us unable to log into those websites. In such cases even the ones from the YouTube, several videos will be blocked. So in this video, we will be shown how to bypass those filters and log into those sites. Firstly go to the website Proxapp and over there you will be asked the ...

RAID, or Redundant Array of Independent Disks, lets you divide and replicate data among multiple hard disk drives for information storage security. This video tutorial demonstrates how to install Ubuntu in a RAID 0 array. Before starting, you'll need at least 2 hard drives and an Ubuntu alternate installation CD. RAID 0, or striped disks, let's you install an operating system, such as Ubuntu, on a partition, while using others for data storage, as illustrated in this instructional segment.
In this video you will learn how to update your version of Windows 7 and how to check the system settings for automatic updates. In order to do this you need to go in the Start Menu and then in the Control Panel. Then you need to click System and Security. The next step is to click Windows Update. A new window will pop-up and you will see two types of updates: Important Updates and Optional Updates. To install them just click on the blue link and then check the boxes. To check for updates you...
In order to secure a PDF with a password when opened in Adobe Acrobat 9 Pro, press the secure button and go into password security settings. Here you can change on what versions of this software the file will run on, the next option asks which portion of the document is to be encrypted when a password is placed. Further below here is where you actually choose the password, this ensures that only people who know the password will be able to see the contents of the document. Below this is the d...

Check out this Mahalo video walkthrough of Marshlands in Resident Evil 5. Resident Evil 5 (RE 5) is the sequel to 2005's Resident Evil 4. This game guide shows you BSAA emblem locations, treasures, and includes strategies for all 6 missions and boss fights.
VNC stands for Virtual Network Computing. It is remote control software which allows you to view and fully interact with one computer desktop (the "VNC server") using a simple program (the "VNC viewer") on another computer desktop anywhere on the Internet. The two computers don't even have to be the same type, so for example you can use VNC to view a Windows Vista desktop at the office on a Linux or Mac computer at home. For ultimate simplicity, there is even a Java viewer, so that any deskto...

In this tutorial, Mike Lively of Northern Kentucky University gets you started in getting the Adobe Air Content Management System up and going.

For Infinity Exists Full Disclosure's first Website Hacking episode, we demonstrate how to exploit a security vulnerability occurring in a website's database to extract password hashes. Sql (Structured Query Language) is a computer language designed for the retrieval and management of data in a system's database. The Attack, known as Sql Injection, manipulates Sql statements before they are sent to the Sql Server, allowing the Attacker to create, change, or retrieve data stored in the database.

Whether you are sharing an internet connection, working together or just playing group video games, you will need to network your computers. Check out this tutorial and learn just how easy it is to create a home network.

While most iOS updates will only improve the experience on your iPhone, some can cause more havoc than good. If an update unexpectedly breaks or degrades certain functions on your iPhone, you may be able to roll it back to the previous software.

The first step to getting your life together? Getting your online security together. After all, security when you're shopping, video calling, and more means more than ever in a digital age when anyone can copy your info or try to pose as you on the web. This Premium Privacy Bundle featuring Zenmate and StartMail will give you a secure VPN and encrypt your emails, all at a bundled price. The security duo is on sale for 60% off for a limited time, which means it's just $44.99 (regularly $113).

If you're an avid programmer or developer, your time is likely spent creating apps and perhaps the occasional website. And while these go-to coding endeavors are exciting and occasionally lucrative, more and more coding pros are turning to careers in cybersecurity and ethical hacking — thanks to the high pay, flexibility, and unparalleled opportunities.

Since its founding in 1984, Cisco Systems has been a global leader in information technology. From networking hardware and software to domain security and energy management, the company dominates the IT field.

If you've tossed around the idea of turning your interest in white hat hacking into a career in cybersecurity or IT, now's as good as time as ever to invest some time and energy into improving your skill set.

Determining the antivirus and firewall software installed on a Windows computer is crucial to an attacker preparing to create a targeted stager or payload. With covert deep packet inspection, that information is easily identified.

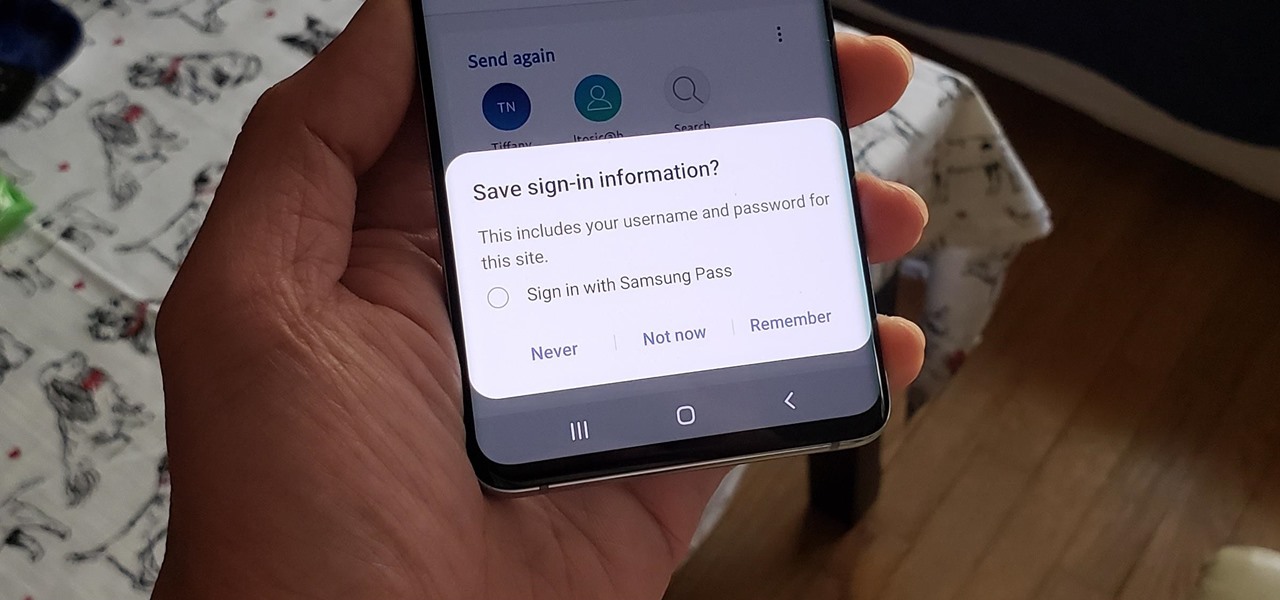
If you use Google Chrome on your computer, you've undoubtedly saved a ton of passwords since the browser always prompts you to. But Samsung uses their own password service on their phones by default, so you'll have to change a setting if you want to use your Chrome passwords to log into apps and sites on your Galaxy.

Using a strong password is critical to the security of your online accounts. However, according to Dashlane, US users hold an average of 130 different accounts. Memorizing strong passwords for that many accounts is impractical. Fortunately, password managers solve the problem.

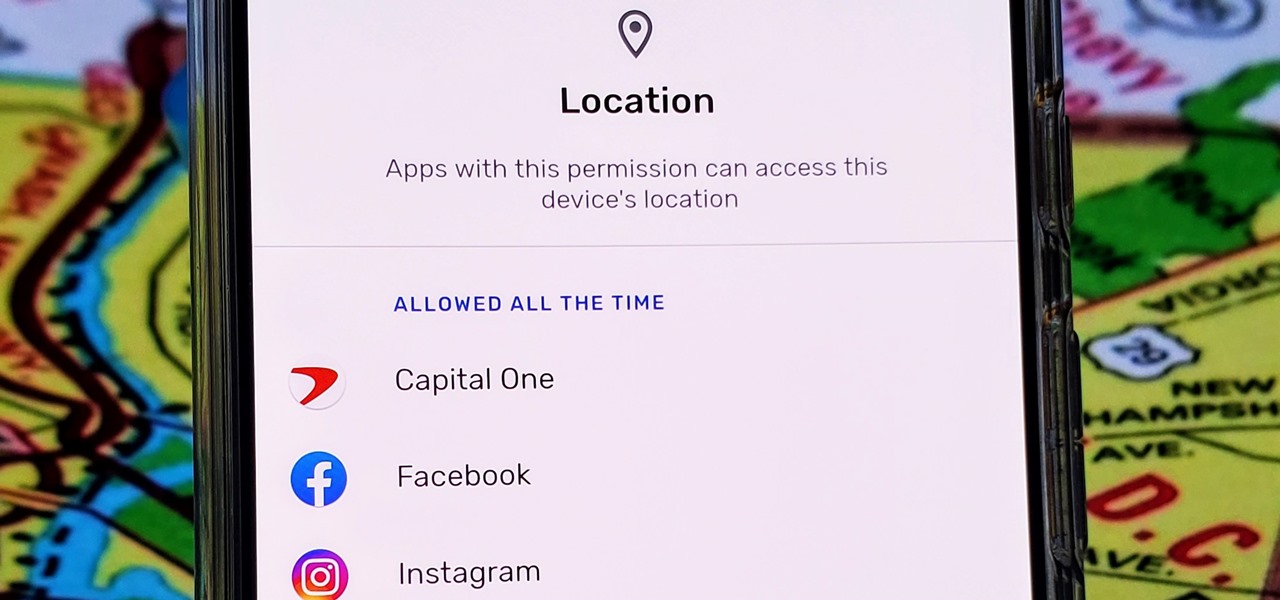
With Android 10, there are now three options when an app asks to access your location: Allow, Deny, and Allow While In Use. That last one prevents apps from seeing your location unless you're actively using them, and it's the default now. But when you first update, most of your apps will still be allowed to access your location in the background — at least, until you do something about it.

During the recent Augmented World Expo (AWE), we had a chance to try out the Lenovo ThinkReality A6 AR headset. Unfortunately, the experience was all downhill from there.

For lack of a better word, a missing iPhone sucks. Not only do you lose a physical device that cost you a small fortune, but there's also the probability you'll never see your precious data again. Hackers and thieves might, just not you. To keep this from ever happening, there are preventative measures you should take, and the sooner you do them the better.

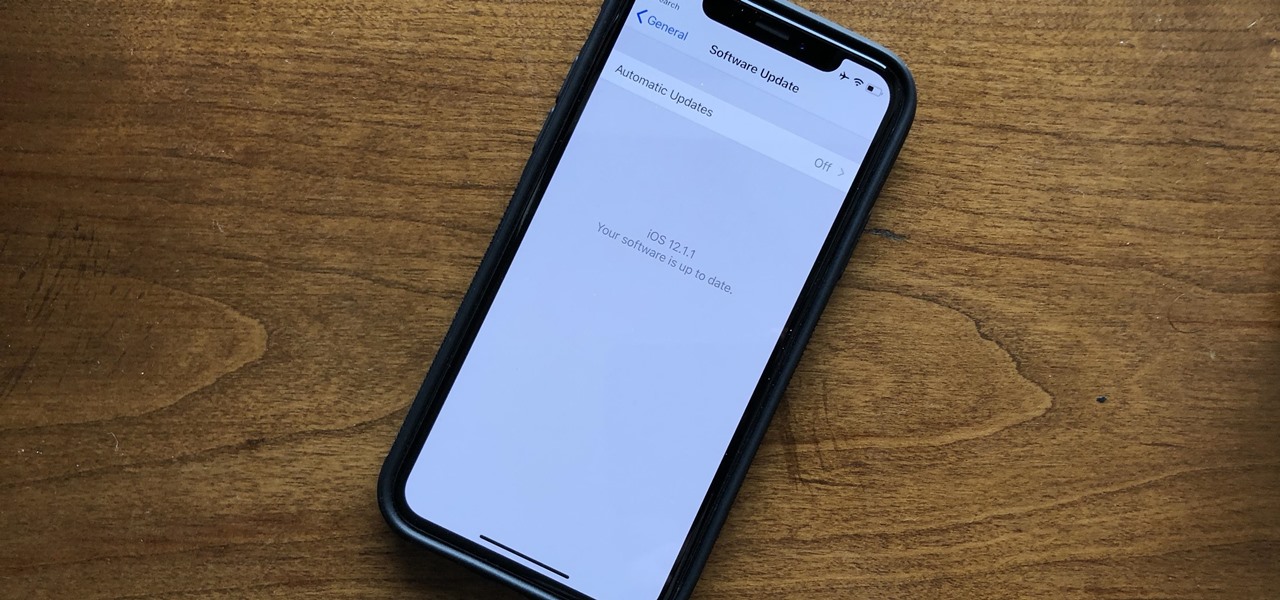
Apple released the latest update for iPhones, iOS 12.1.1, on Wednesday, Dec. 5. It introduces a few new features to iOS 12 as a whole. The software has been in beta testing since Halloween of this year, spending just over one month in the hands of beta testers.

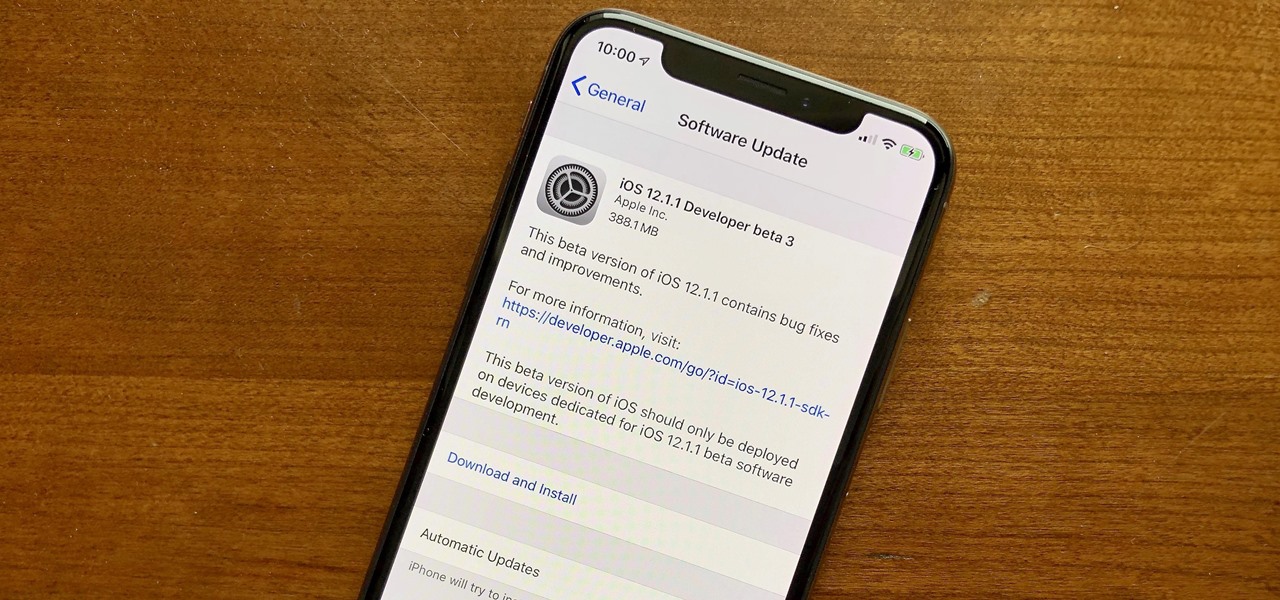
It seems Apple will keep with recent tradition — the third iOS 12.1.1 public beta released to software testers Thursday, Nov. 15, just hours after the 10 a.m. PDT (1 p.m. EDT) release of dev beta 3. Apple likes to take a short time after a developer release to ensure the beta is good enough to release as a whole, as seen with the entire iOS 12 dev beta 7 debacle.

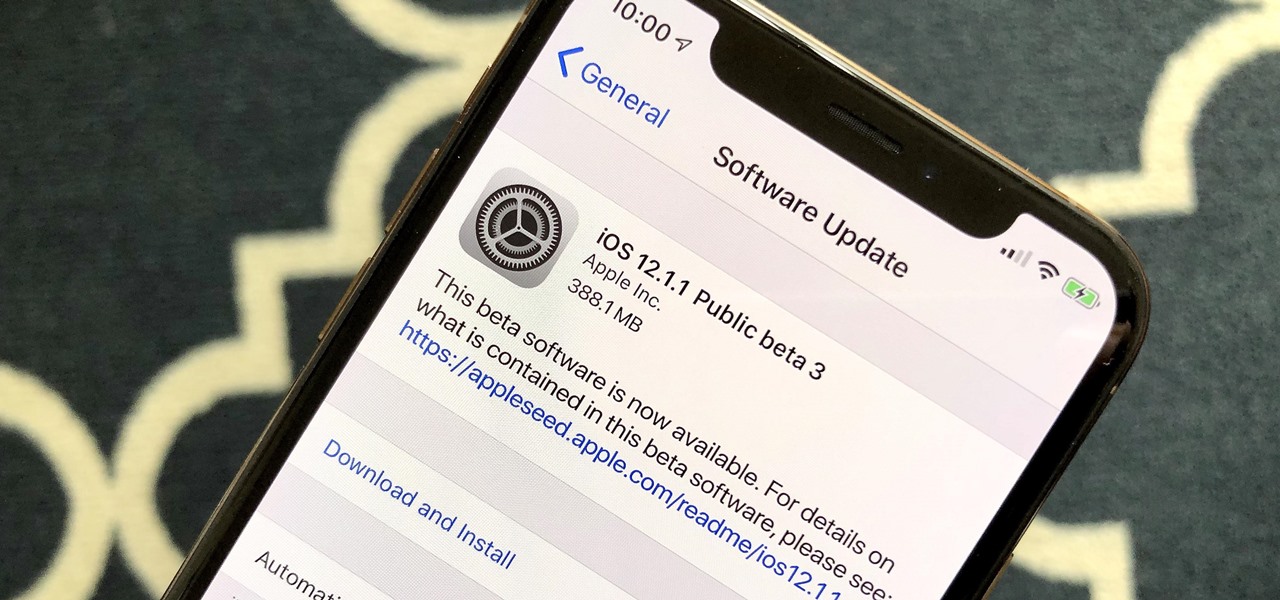
Apple released the third beta for iOS 12.1.1 on Thursday, Nov. 15. This update is not much of a surprise, as it comes just a little over one week after the release of dev beta 2. As with that beta, we expect Apple to release the 12.1.1 public beta shortly, possibly as soon as this afternoon.

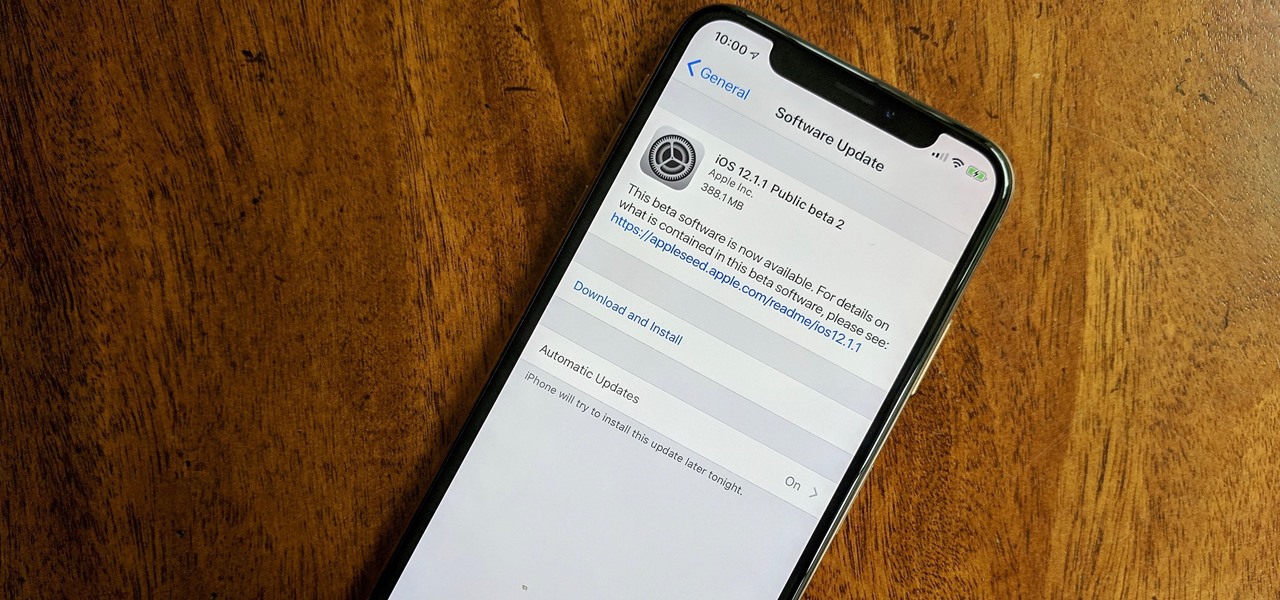
Registered iOS developers received their first taste of 12.1.1 dev beta 2 on Wednesday, Nov. 7, and public beta testers received the iOS 12.1.1 public beta 2 shortly thereafter.

Developers opened their iPhones on Wednesday, Nov. 7, to find an update to the iOS 12.1.1 beta. Apple seeded developers the first 12.1.1 beta on Halloween, marking one week between it and the second beta. It's a quick update turnaround but in line with trends as Apple typically waits at least a week in between beta releases.

The macOS 10.14 security update tried to make parts of the operating system difficult for hackers to access. Let's take a closer look at how its new feature works and what we can do to spoof the origin of an application attempting to access protected data.

Smartphones are still "phones," which means communicating with others is usually a primary use. Ranging from a simple "hi" to a more personal conversation and even sharing passwords, our messages should remain private so that only the intended recipient sees their content. While many apps tout end-to-end encryption, not all apps prioritize security and privacy.

We know Android 9.0 will have the formal designation of Pie, following Google's age-old tradition of naming their OS after items you'd normally find on a dessert menu. And thanks to a slew of new features that centers around your overall security, P could also stand for Privacy.

Flying under the radar during Magic Leap's big week at the Game Developers Conference, the company settled a potentially ugly lawsuit with a former employee.

It's often the smallest details that determine your overall experience with a smartphone. Unlocking your device with a PIN is an example — and iPhones have had a leg up over Android thanks to their automatic unlocking. Thankfully, this era has finally come to an end with the arrival of the Galaxy S9.

One unique feature of Firefox Mobile is extensions. Extensions allow users to add in features that didn't originally come with the browser. These add-ons provide an array of features, including improvement to privacy and security.

Unlike many browsers, Firefox gives a lot of control to the user. By default, Firefox does a great job of balancing security and performance. However, within the app's settings, you can modify options to shift this balance in one direction or another. For those looking to shift it toward security, here are few suggestions.

When traversing the web, you'll regularly come across websites that require you to create an account. With the majority of these accounts, protection is limited to a simple password. Despite this, many people are still using weak passwords such "123456." For these reasons, you really need a password manager, and our research has shown that LastPass is still your best bet.

OpenVAS is a powerful vulnerability assessment tool. Forked from Nessus after Nessus became a proprietary product, OpenVAS stepped in to fill the niche. OpenVAS really shines for information gathering in large networks where manual scanning to establish a foothold can be time-consuming. OpenVAS is also helpful for administrators who need to identify potential security issues on a network.

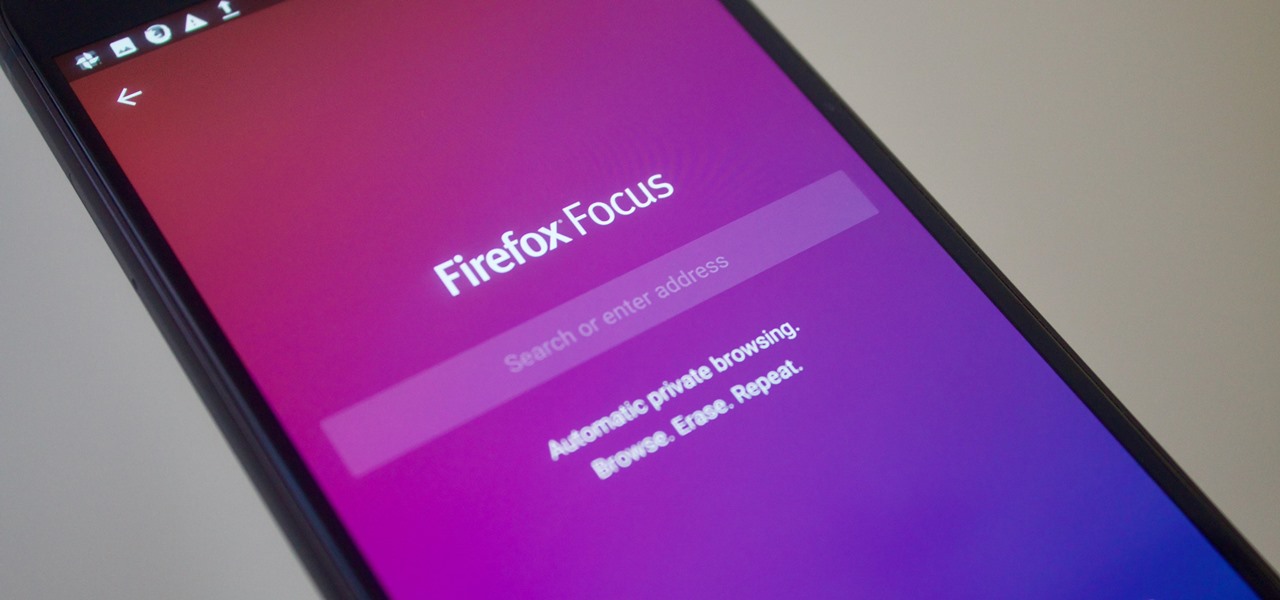
Firefox Focus is Mozilla's effort to make your internet experience a little more secure. Originally released in November 2016 for iOS, Focus blocks internet trackers, search history, anything that gets in the way of a clean, private browsing experience.

New updates to the journaling app Day One include more security for journal writers' data. For example, users can now enable end-to-end encryption. The encryption does not happen automatically; however, users must go to Settings — within Journals — then select each journal they want encrypted.

Maybe you thought sitting behind a Mac gives you special protection when it comes to getting hacked. Thanks to a a new report from Check Point, you can kiss that theory goodbye. The cyber security company just uncovered the latest strain of malware — OSX/Dok — infecting all versions of macOS (previously Mac OS X).

The Snapdragon 820 and 821 were met with praise last year, receiving almost no complaints compared to their overheating predecessor, the Snapdragon 810. But now, all eyes are on Qualcomm to see what goodies they have in store for us this year, as their new SoC, the Snapdragon 835, will be revealed this week at CES 2017.

This is the very first article in my series on setting up a Mac for hacking. In this series, I will be operating under the assumption that you have a clean install of macOS (previously OS X). If you aren't starting with a clean installation, there may be a few differences, but nothing we can't help you out with.

Samy Kamkar, security researcher and friend of WonderHowTo, just had one of his devices featured in Mr. Robot.