As we get closer to the release of the iPhone 7 this September, more and more details are emerging about the features the new smartphone could have. The well-regarded analyst Ming Chi-Kuo of KGI Securities, who has an uncanny ability to predict new Apple features, has reported another detail involving a dual-lens camera on the upcoming iPhone 7 Plus model.

Once you connect all of your devices to your Wi-Fi router at home, you'll never need that long, complicated Wi-Fi password ever again, right?

Welcome back, my greenhorn hackers! Throughout this series on Metasploit, and in most of my hacking tutorials here on Null Byte that use Metasploit (there are many; type "metasploit" into the search bar and you will find dozens), I have focused primarily on just two types of modules: exploits and payloads. Remember, Metasploit has six types of modules:

Welcome back, my nascent hackers! Although my favorite TV show, Mr. Robot, had completed its first season already, I have not completed demonstrating the hacks that Elliot used in the show. (By the way, I can't wait for season 2!)

One more business has decided that rewarding hackers to find flaws in their computer systems is a wise investment! As you know, a number of software companies offer bug bounties, and some of these can be quite lucrative. Google, for instance, offers a bounty of $150,000 for anyone who can hack their Chrome operating system, and many other companies are offering similar bounties, although, not quite as lucrative. Now, United Airlines has decided to offer frequent flyer miles to hackers who fin...

In addition to the fingerprint scanner, the Samsung Galaxy S6 has all of the basic lock screen options that other Android phones have: swipe, pattern, PIN, and password. There also just happens to be a secret sixth option called "Direction lock" that protects the device with a series of customizable directional swipes—only it's hidden in an unsuspecting settings menu.

Technology has progressed by leaps and bounds and has blessed people in a number of ways, but at the same time, it has troubled them also. Computers are now used in every aspect of life. No matter if you are a businessman, an employee, a student, or even a housewife, a computer can assist you in your routine work. You save your personal information, documents, and other similar sensitive stuff on your computer that can hurt you if they get compromised.

Not too long ago I showcased ReCam, a free app that lets you schedule recordings and use your Android device as a security or spy camera of sorts. While useful, this app required you to schedule when to record in advance, resulting in you possibly missing the footage you intended to record (assuming your scheduling wasn't as on-point as you wished).

Android 5.0 has a killer new feature that should make securing your device easier than ever. It's called Smart Lock, and it essentially lets you bypass your secure lock screen when you're in a "trusted environment." This means that if you're connected to a known Bluetooth device or near a pre-programmed NFC card, you don't have to bother entering your pattern, PIN, or password.

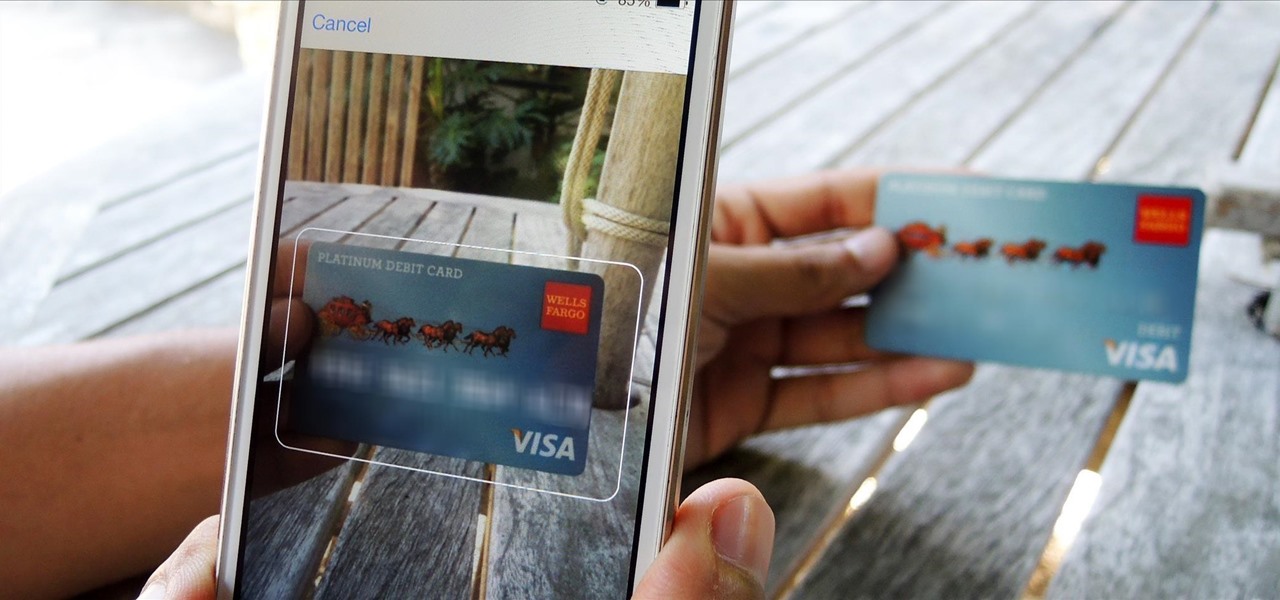
There's a feature that debuted in iOS 7 that lets you to save your credit or debit card information in Safari so that you can auto-fill text boxes when purchasing something online. Unfortunately, you still had to manually fill in your card info the first time, and if you wanted to disable the feature for security concerns, it was entirely useless.

Welcome back, my budding hackers! People often ask me, "Why are you training hackers? Isn't that illegal?" Although I usually give them a short version of this post, there are MANY reasons why YOU should be studying hacking.

A security analyst has discovered a flaw in Chromecast's initial setup process that allows would-be hackers to assume full control over the online streaming device.

Update: June 2nd, 2014 Over the weekend, someone snuck in to Apple's presentation dry run, and grabbed a quick video of the new iPhone will look like.

Adding to the recent recent slew of bugs and issues within iOS 7, it now seems that emails sent with attachments are not encrypted, despite Apple's claims that they are.

Lock screen security provides a means of safety when it comes to keeping others from breaking into our smartphones and snooping around on or stealing private information like documents, emails, photos, and videos.

Welcome back, my apprentice hackers! As many of you know, I have been hesitant to adopt the new Kali hacking system from Offensive Security. This hesitancy has been based upon a number of bugs in the original release back in March of 2013 and my belief that BackTrack was easier for the novice to work with.

February may be the shortest month of the year, but for iOS softModders, there were plenty of apps and tweaks to fill up those days. Whether patching major security holes or just a tweak to make speed dialing more efficient, there was a plethora of great mods for our jailbroken iOS 7 devices. These are our favorites from the month.

There are countless mods and apps for Android devices that give them an iOS-style look, but maybe it's about time we take some notes from Android, especially when it comes to the iOS 7 lock screen.

Welcome back, my hackers novitiates! As you read my various hacking tutorials, you're probably asking yourself, "What are the chances that this hack will be detected and that I'll land behind bars, disappointing my dear mother who already thinks I'm a loser?"

Starbucks' app is the most used mobile payment app in the U.S. because it's well-designed and convenient. But if you use the iOS version on your iPhone, your username, email address, password and location data could be compromised because the app stores them in plain text.

Ways to Blocking a Website on a PC Open the “Control Panel” by click “My Computer” on your PC

About a year ago, Abode decided to discontinue support for Flash on the Android platform. With its security concerns, it's understandable why some people would want to disable Flash on their devices, but there are still some things you can't do without it. Amazon Instant Videos is one thing you can't do, giving you nothing but a "Flash Player is not installed" warning.

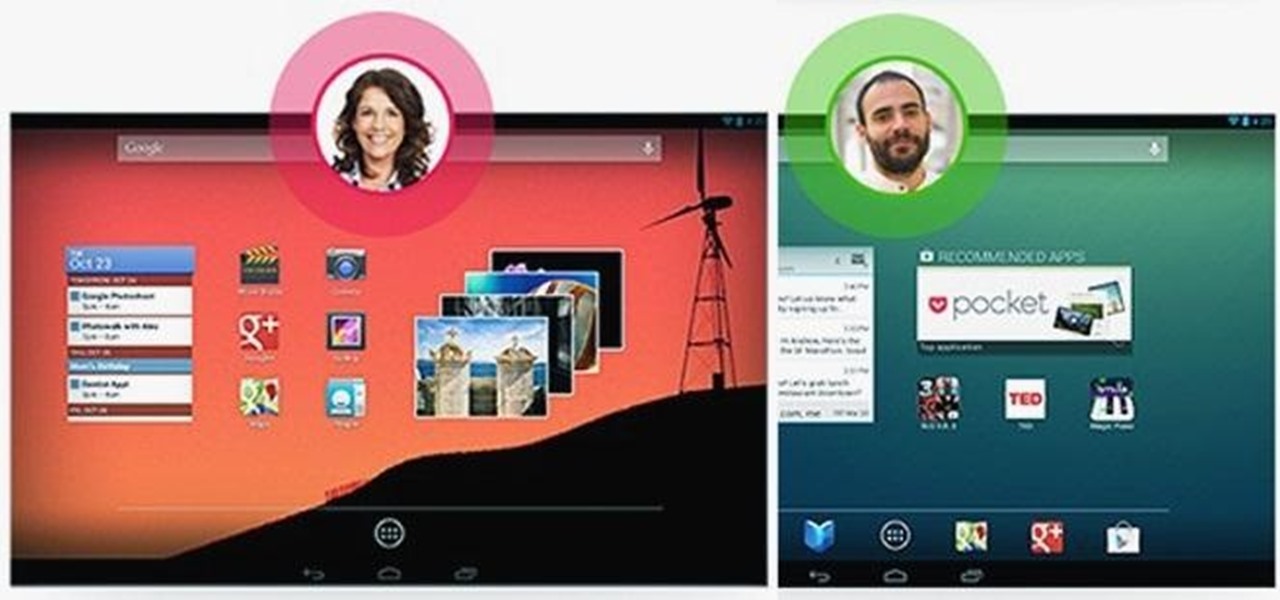
The most recent update for Android's Jelly Bean has some pretty cool new features, like better panoramic photos, gesture typing, and wireless sharing. From a security standpoint, though, the best new feature is the ability to add multiple users to one device. You can create up to 8 different accounts on Android tablets like the Nexus 7 or Nexus 10, so besides saving time hiding or protecting sensitive data, it could also save you some money. You can share a device with your family, kids, or s...

Back in 2010, iOS developer Daniel Amitay developed a camera security app for iPhones that used an unlock screen almost identical to that of the iPhone.

Security researcher and iPhone hacker pod2g has brought attention to a flaw in Apple's iOS that allows the user to change the reply address of an SMS message. This bug has been a part of the iPhone's SMS since the first iPhone in 2007, but Apple has yet to address it. Basically, there's a section in the text payload called User Data Heading (UDH) that controls some advanced features, one of which is the reply address. By changing the reply address of a text message, you can make someone send ...

Consider this reason 1,001 why we love the internet: Using Google, you can hack into almost any webcam or security cam, in any part of the world and even control the webcam to move around so you can get your full panoramic shot. Don't believe us? Then check out this video tutorial to learn the steps you need to take.

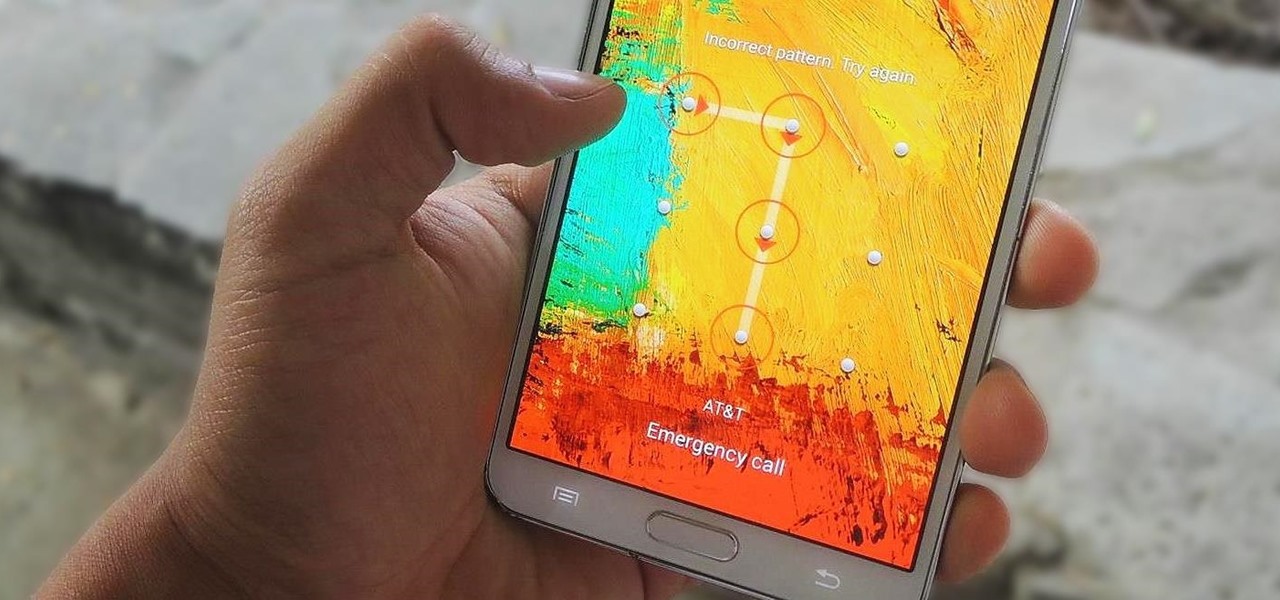
The passcode, or the four-digit code you enter in order to access an iPhone or iPod touch, was created to ensure security and prevent hacking. But what if you haven't touched your iPhone in a month and you simply don't remember what your passcode is anymore?

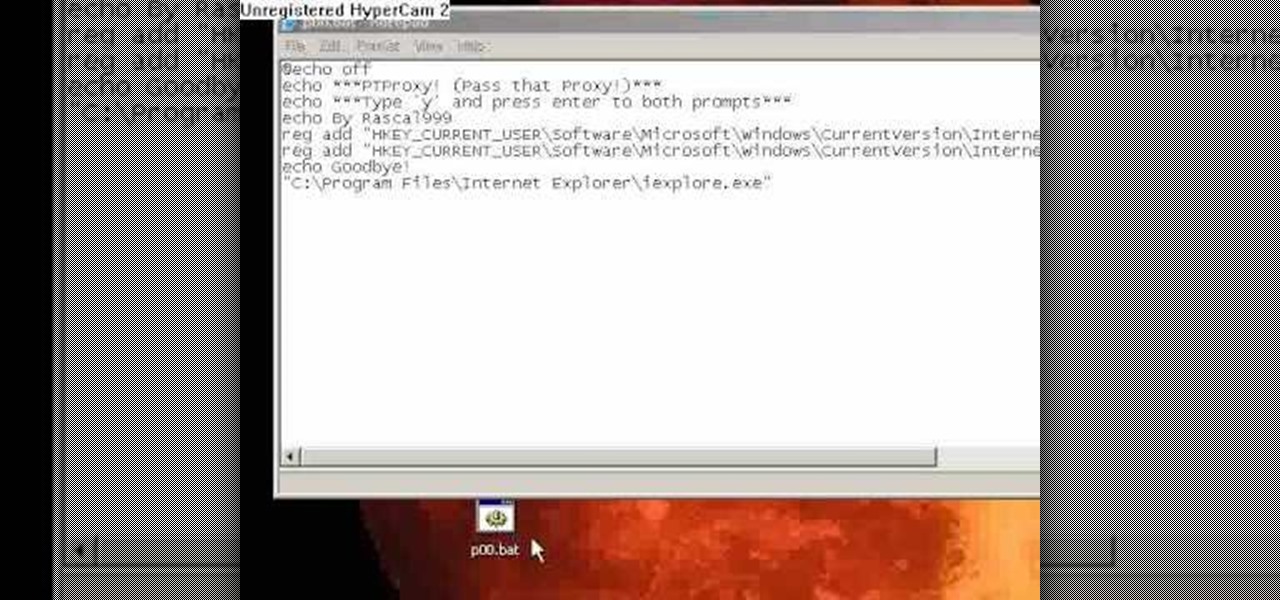
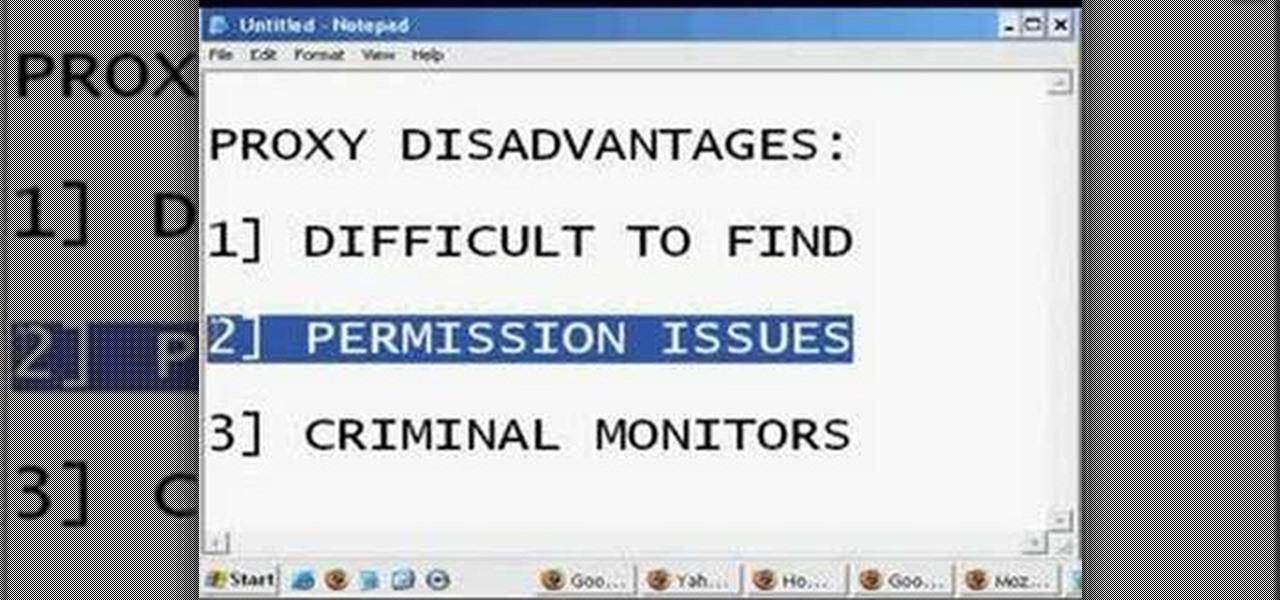
Different ways of using a proxy bypass to access blocks sites is shown with ease in this video. Many places explained to be blocked with internet security such as libraries and schools. Using a search engine such as Google you need to search for a proxy site. After a proxy site has been found you will use it to access the blocked websites through another servers internet provider. The narrator explains that proxies are just a way to bypass internet blocks by avoiding using the blocked compute...

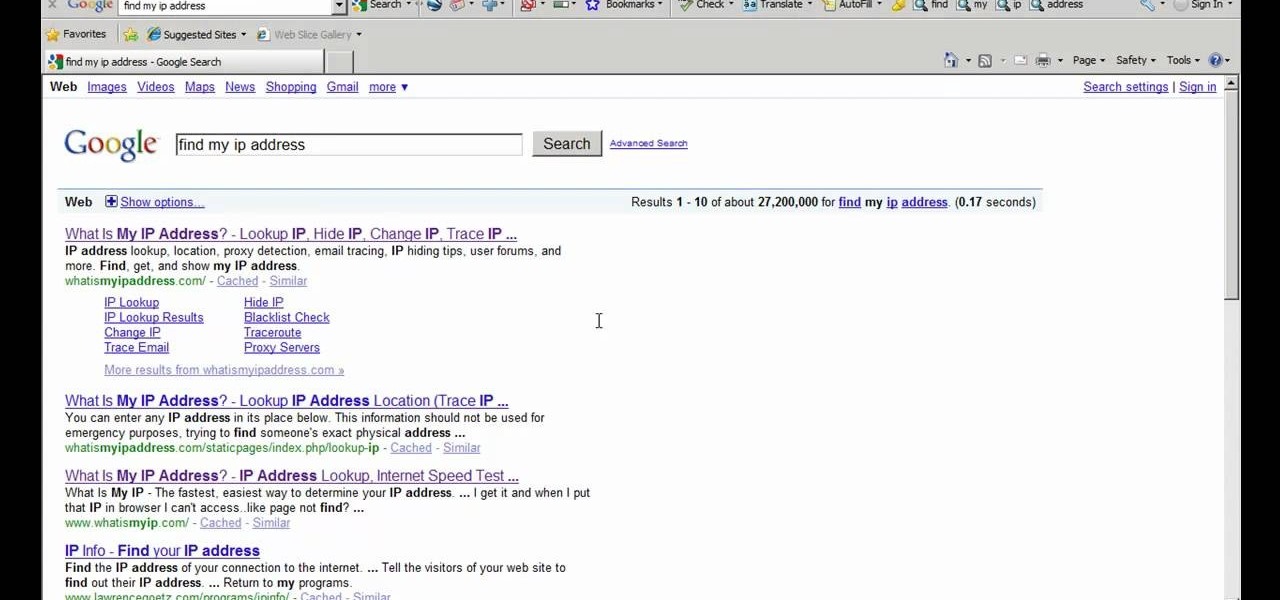
In this video from apexcctv we learn how to find your public IP address and then use dynamic DNS to keep it updated in regards to your security needs. If you go to Whatismyip.com you will see your IP address. You can also go to Google and search for "find my IP address." A service called Dynamic DNS keeps track of your customers IP address. It will map a name to an IP address. Static DNS entries do not change. To set up DNS you can go to CCTV tutorials on the ApexCCTV website. You should set ...

This video tutorial is in the Computers & Programming category which will show you how to hack a wireless network with WEP encryption. This video is intended only as a means of testing the security of your own network. Go to Backtrack Linux, download the backtrack4 and burn it to a DVD. Now put it in a computer with a wireless card and restart the computer so that it boots to the DVD. When it boots up, type "startx" to start the interface. Bring up the command prompt and type in "/etc/init.d/...

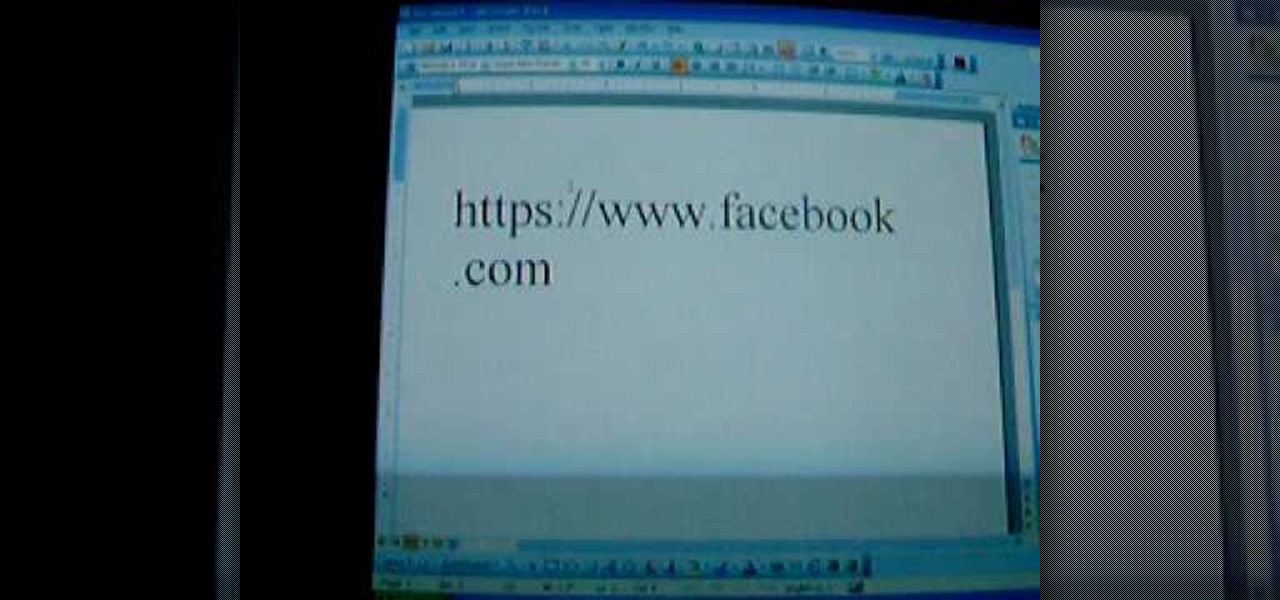
In this video, we learn how to access Facebook at school using "https". You don't have to go to any website to do this, it's simple and easy. All you have to do is type in "https" into your browser before you type in the website you want to visit. Make sure you type in this extra "s" or the website will not work. This should bypass the security settings your school has set so you can access your Facebook account. If you happen to end up on a page when it doesn't work, just make sure the "s" i...

In this tutorial, we learn how to sync iPhoto albums with Facebook. First, open up iPhoto on your computer and highlight all of the pictures that you want to import into Facebook. Once you've done this, go to the top of the window and click on "share". Next, click on "share with Facebook" and then choose who you want the pictures viewable to. After this, click on the "publish" button and wait for the program to load the pictures. After this, go to your Facebook account and see the pictures th...

In this tutorial, we learn how to change your IP address in five different ways. First, go to your security settings and clear all cookies, then start to browse the internet with private browsing from your internet browser. You can change your IP address by going onto your internet browser and changing the LAN settings. Type in your address and port, then bypass the proxy server. Next, go to options and then advanced on your browser. Type in the proxy and port, then click where it says no pro...

In this tutorial, we learn how to perform a master hand reset on your Blackberry Pearl. First you will need to go to the options menu on your phone, then click on security options. Next, you will go to general settings, and then hit the Blackberry menu button and click on "wipe handheld". A prompt will show up and tell you to enter in a confirmation word, then enter that and your phone will now start to go through the process of wiping out all information. When this is finished, your phone wi...

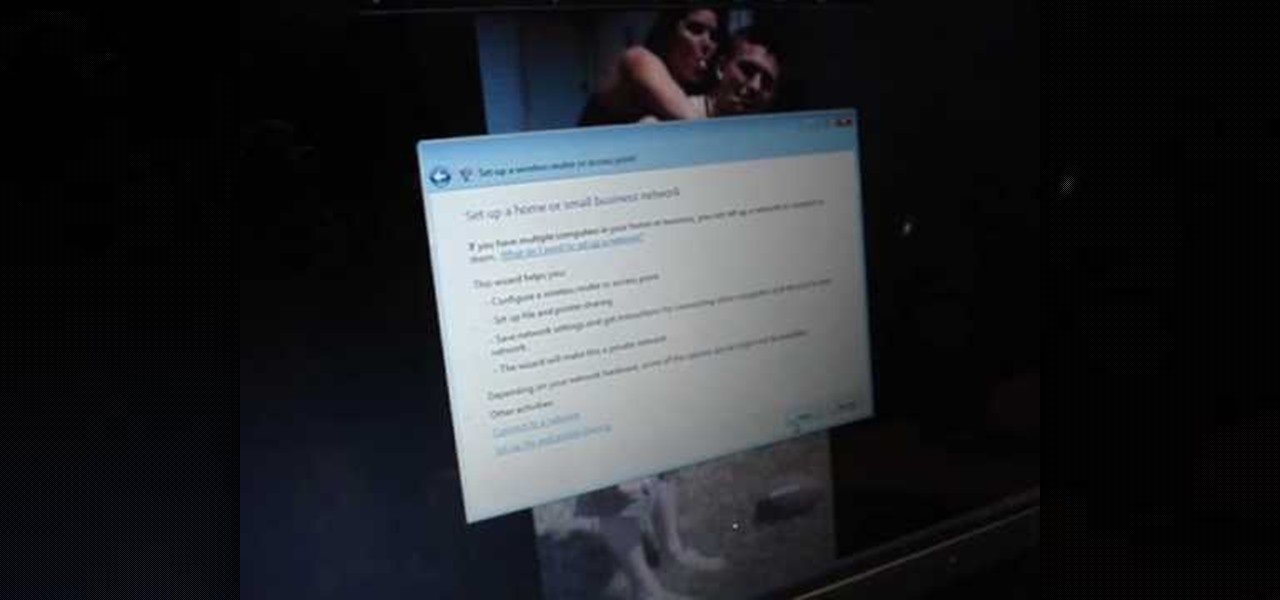
In this tutorial, we learn how to set up and secure a wireless router. First, take your cable and plug it into your modem from your computer. After this, plug in an Ethernet cable into your modem to a wireless router. Now, plug the wireless router and modem into the wall. Now, look for the icon on your computer that says you have connected a new device to it. Go through the set up wizard to make a new wireless network, once it doesn't find one, connect a USB to the computer. Now, click on the...

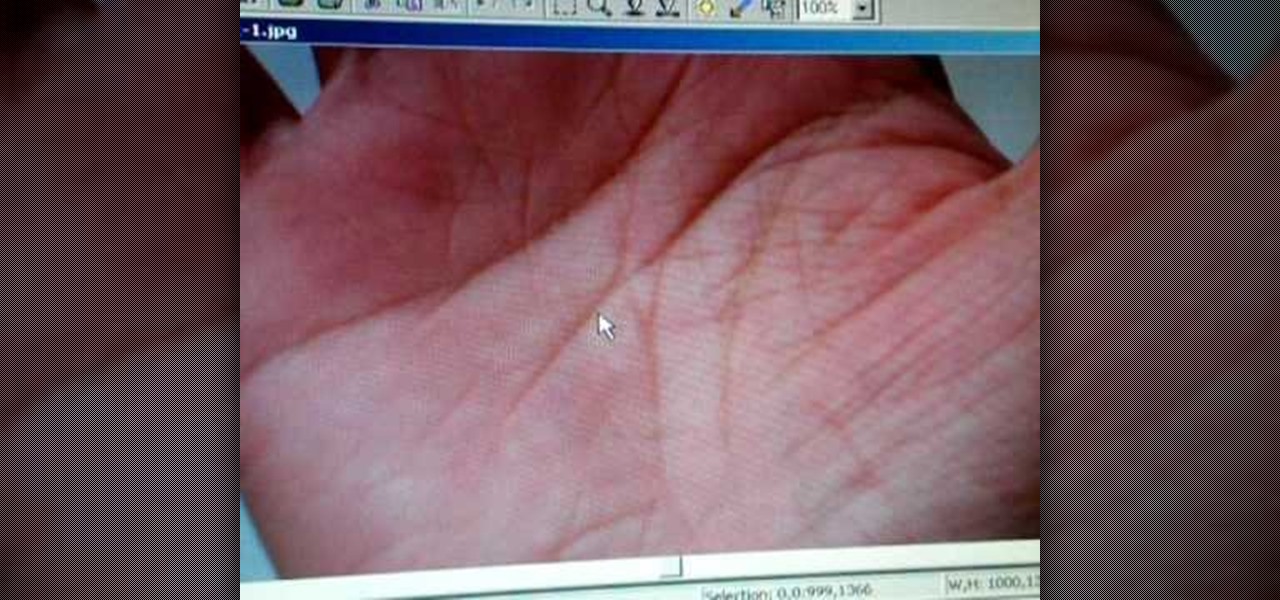
In this video, we learn how to understand the triangles on the lines while palm reading. The triangle on the lifeline shows that any obstacles the person goes through will be in their thirties. It will also say that they can get back onto their feet quite easily. Any set backs or accidents are minor and they won't have distress for too long. If the triangle is on the heart line, it will show that the person has a certain mount of security in friendships and/or relationships, that can help the...

In this video, we learn how to work with Stretch Magic. This is a beading technique that is very easy to use. It's great for making bracelets, because no clasp is required. First, cut a piece of Stretch Magic 4-5 inches longer than you want it. Now, string your favorite beads onto the Stretch Magic. When you are finished with this, connect the ends with a square not and add a drop of super glue for added security. After this, cut off the excess strings from the end and you will be able to wea...

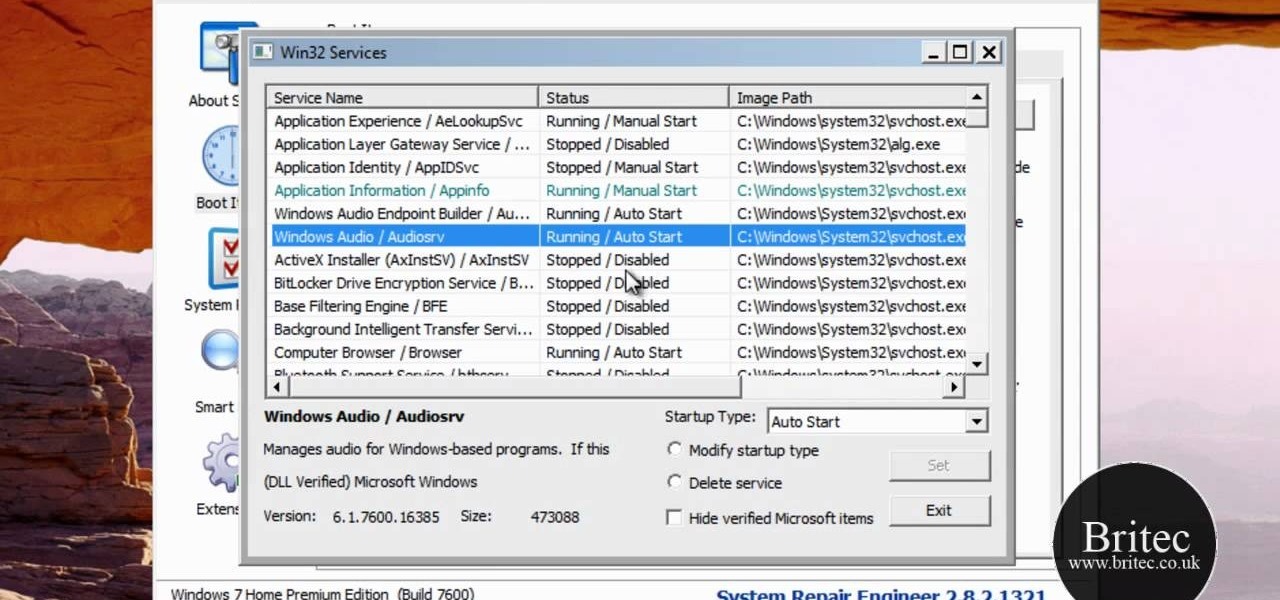
Your Windows computer may be experiencing some issues, and those issues may be a direct result of computer viruses and malicious software from the internet. One of the simplest ways to find these issues and repair them is by using a freeware program called System Repair Engineer (SREng). But that's not all it can do… check out the video to see a basic overview for using SREng.

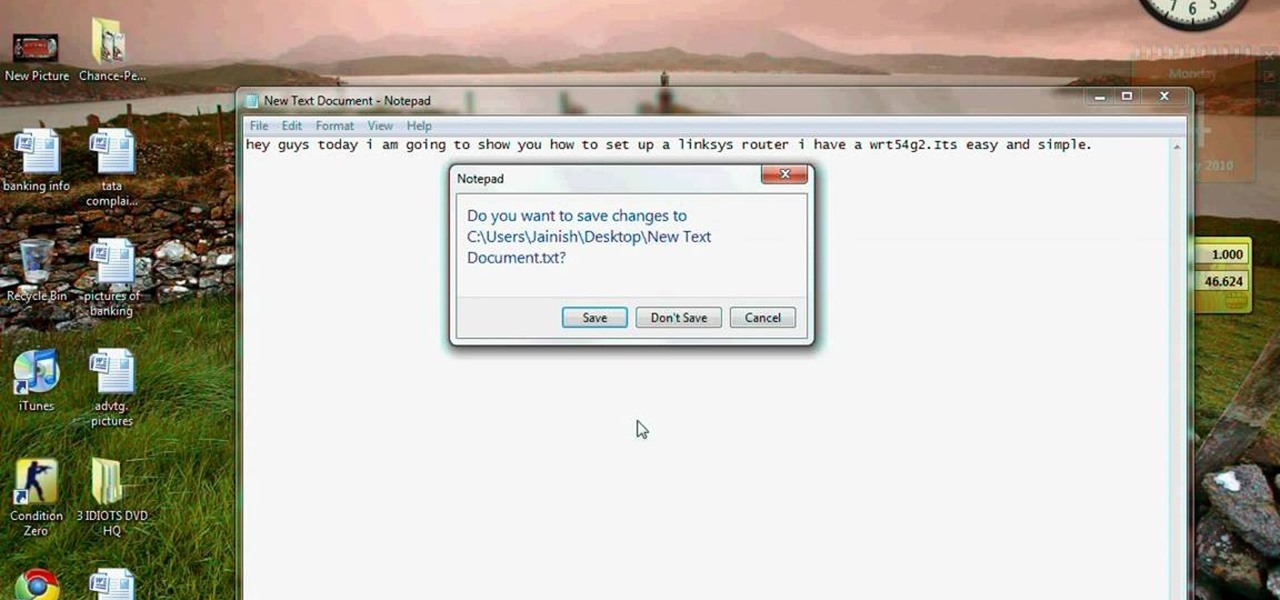
This video tutorial is in the Computers & Programming category which will show you how to set up a Linksys WR54g or WRT54g2 wireless router. First you connect to your Linksys router. Then go to http://192.168.1.1 and type in "admin' as your password in to log in window and click "log in'. then go to the "wireless' tab and enter your wireless network name. In the wireless channel select '11 2.462GHz' and click save. Next go to "wireless security' and type in the wireless network key. This is t...

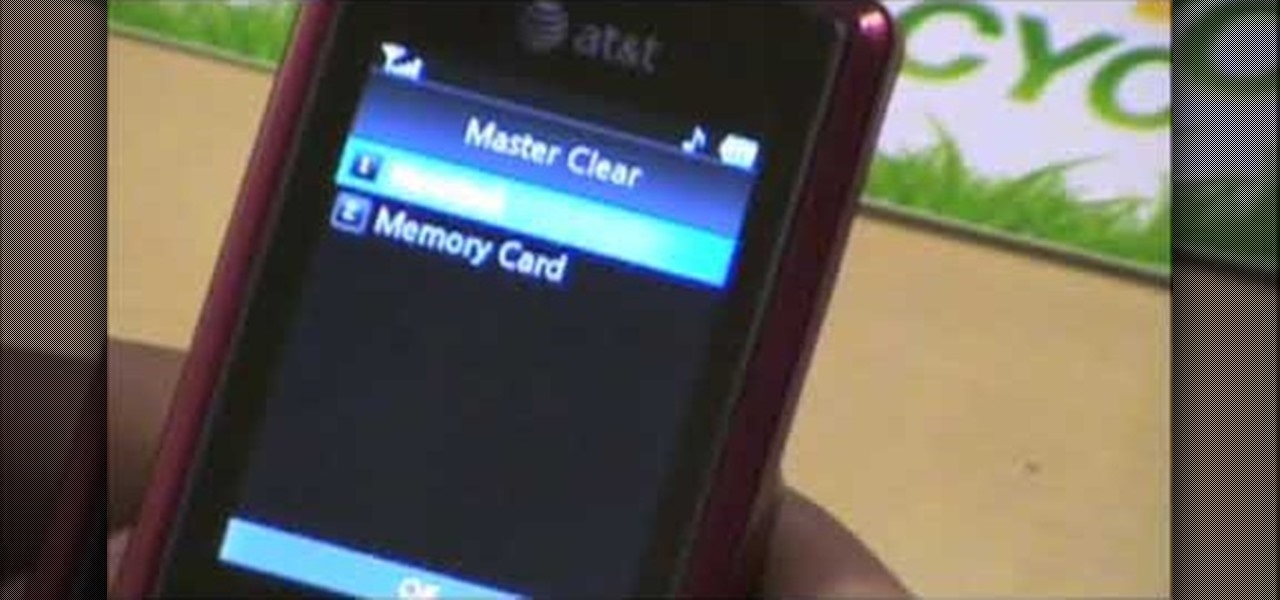
In this video tutorial, viewers learn how to data clear and erase an LG CU720 Shine mobile phone. This task is very fast, easy and simple to do. Begin by clicking on the Menu button and select Settings. Then scroll down the list or press the # sign to select Reset Settings. Now select Master Clear and select Handset. If there is data in the memory card, clear it as well. Click on Yes to confirm the resetting and type in your security code. This video will benefit those viewers who have a LG S...