A couple of months ago at the Black Hat security conference, hacker Cody Brocious gave the hotel industry a nasty surprise when he figured out how to hack the locks made by Onity that are used in millions of hotels worldwide.

It seems like every other day there's a new security threat or data leak in the news. Whether it's your credit card PIN or your smartphone's apps leaking your email address, no one wants their personal information out there, especially passwords. And if you use the same email address and/or password for more than one site, the effects of someone getting hold of your credentials can be catastrophic.

If you bought the new iPhone 5 or upgraded your old one to iOS 6, you may be having issues when you try to upload photos to Facebook. After updating, the first time you try to share an image from the Facebook app, it will ask you to allow access to your Camera Roll.

Want to know when you have a visitor, even if you're not home? You could always set up a security system and live-stream it with your iPhone. But if you don't have a spare iPhone, or just don't want to go to the trouble, this simple hack will add text message alerts to your doorbell so that it lets you know when someone's there.

Windows users have been getting a lot of bad news about their security lately. First, we found out that passwords in Windows 7 and 8 can easily be exploited if password hints are enabled, and now, Russian password-cracking software developer Elcomsoft has found another huge vulnerability.

If you use apps on your smartphone, chances are you have no idea what those apps are doing with your information. Just this year, there have been several scandals involving apps transmitting user data, like Path uploading users' entire address books onto its servers, HTC's Security Flaw, and Brewster exposing users' personal information (even Ashton Kutcher's). A new service called Mobilescope wants to make sure you always know where—and to whom—your data is going. Lots of apps copy your cont...

Want an electric car without the price tag? You could always build your own, or maybe just hack your old gas guzzler into an eco-friendly electric machine... This weekend at Defcon, security consultant David Brown showed off his "Voltswagon" project, a 1974 Beetle named Shocky that he converted to electric for only $6,000. He removed the old combustion engine, radiator, and a few other unneeded parts to make it lighter. Then he loaded it with batteries front and back, ten Interstate DC-29, 12...

Some of us use our smartphones for almost everything. Manufacturers know this, so they try to make their devices as convenient as possible to use, but sometimes that convenience comes with a cost to security. The very same technology that allows you to easily share music with friends and make purchases can also put you at risk. Photo by sam_churchill

Elvira, Mistress of the Dark, was created in 1981 by Cassandra Peterson. She was the hostess of a local Hollywood horror movie show that became nationally syndicated. Elvira was the first horror host to be nationally syndicated, first person to be broadcast in 3-D on TV, and first female celebrity to do a national beer campaign and market her own beer.

There's a lot of fighting to endure in the Xbox 360 game Bayonetta. In Chapter 1 - The Angel's Metropolis, it's your first real battle. Central Station Platform - Go to the far side of the platform and go through the security gates. The door on the far side of this hall is locked, but on one wall in the hallway you'll see a strange sphere. Walk up to it and start doing combos to open a door.

The quickest way to get a gorgeous lawn is to lay sod, uniform patches of grass-covered soil held together by matted roots. It will go more smoothly if you know a few landscaping tricks. Learn how to lay sod for a perfect lawn with this how to video.

Knit blankets are comfortable and scream home and security, but they are expensive and making them is an arduous task. If you want to get started on a major knitting project, watch this video, and learn in general terms how to knit a blanket.

Take a look at this video and learn how to hack into a wireless Linksys router. This hack isn't applicable for all security enabled networks, only ones that use generic passwords.

SQL injection is a type of code injection that takes advantage of security vulnerability at the database level. It's certainly not the easiest form of hacking, but if you're serious about turning a website upside down then this is the way to do it.

The Thule Snug Tite hitch lock is for carrier to receiver security. This video shows you how it assembles first, then how the lock is applied to a bicycle rack.

This video demonstrates how to install or replace a dead bolt in your door. Having a dead bolt lock gives you a added sense of security, because it is more secure than just the lock on the door handle.

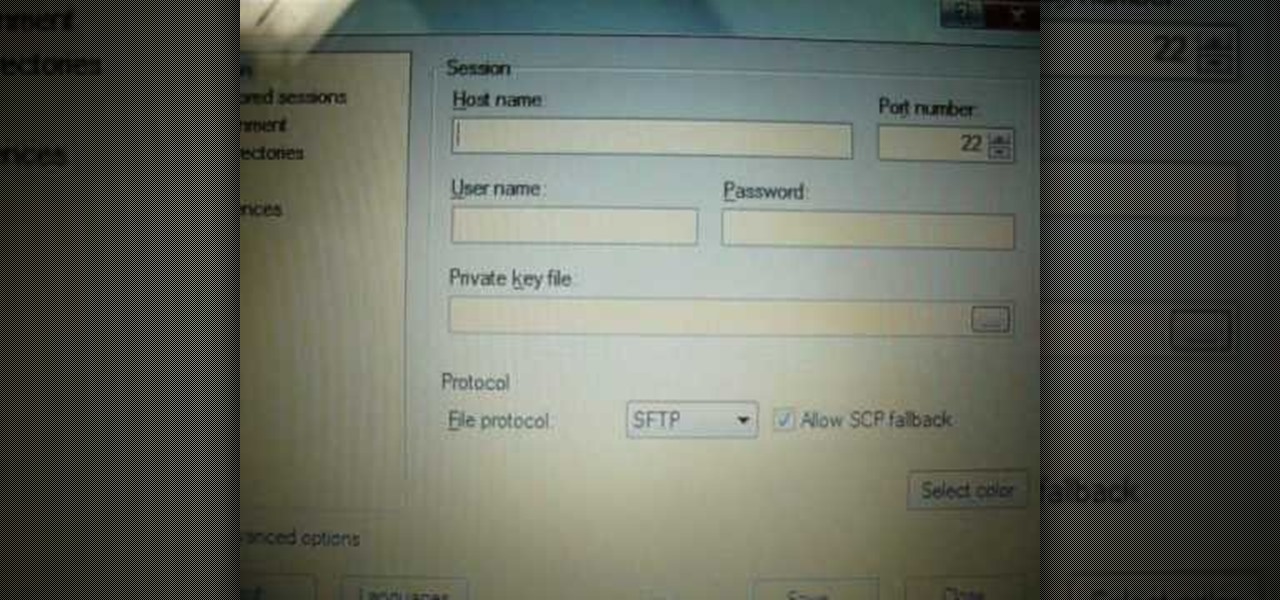
iPodTouchedMaster shows how one can easily SSH into their iPod Touch with all firmware! To SSH is the ability to hack into your iPod Touch's file system. First, your iPod Touch must be jailbroken. Next, you'll have to open Cydia. Click "Featured Packages" or search for the terms "Open SSH" (it will be listed under Console Utilities & Daemons). When you have OpenSSH click on it and click 'Install' and 'Confirm'. After this is finished, click return to 'Cydia'. This may take a lot of battery po...

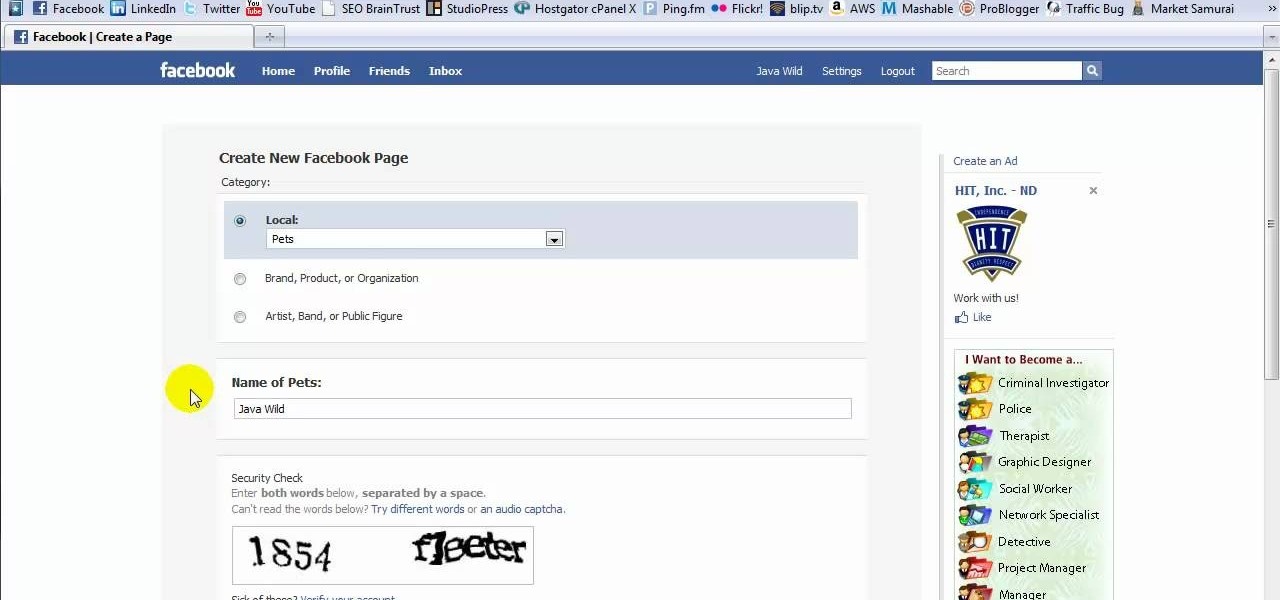
This tutorial is in response to mail to Facebook. Scott Wilde leads you through the process. You can start by creating a brand new profile page. In this case, Mr. Wilde created a profile page for his dog Java Wilde so he could have a fresh new page without having to alter his initial profile page. Fan pages are different than your base profile. Your base profile is not indexed, it is not public, it is private and limited to 5000 friends. A fan page is unlimited up to millions of fans and it c...

This video is a step by step guide for creating exposed teeth makeup . This is loosely based on the Harvey Dent character from Batman: the Dark Knight.

Reduce your chances of becoming the seatmate everyone hates by learning how to head off a screaming jag.

Make the most of summer's bounty by learning how to preserve it for winter. You Will Need

To grow beautiful flowers and plants in an outdoor garden, you need to feed your soil the right plant food – a fertilizer that will help your plants thrive. Watch this video to learn how to choose plant fertilizer.

Research shows that color can have a powerful effect on our emotions. Start harnessing that power today. Watch this video to learn how to improve your life with chromotherapy.

Make everyone in your neighborhood green with envy over your lush lawn with these landscaping secrets. Learn how to get your lawn green with this Howcast landscaping guide.

This video includes instructions on how to get your PlayStation Portable (PSP) onto the BGSU wireless network.

Learn how to do cheerleading stunts and routines in this free video series from a national cheer leading champion.

Shot at the Brambuk National Park and Cultural Centre in Australia, this video shows how to properly throw a boomerang. Take a look this video and give it a try.

If you think you might be a likely target of a black-hat hacker, there's a new iOS security feature that offers extreme protection for your iPhone against spyware, phishing attempts, and other highly sophisticated cyberattacks.

The Internet of Things (IoT) is changing everything in our homes and at work, from security systems and lighting fixtures to smartphones and speakers. An estimated 50 billion devices are now hooked up to IoT.

It is well documented that what you say and do online is tracked. Yes, private organizations do their best to protect your data from hackers, but those protections don't extend to themselves, advertisers, and law enforcement.

Whether you miss the good old days of Telnet or you want to know what hacking was like when security was nothing but an afterthought, Telehack is the game for you. The text-based hacking game is a simulation of a stylized combination of ARPANET and Usenet, circa 1985 to 1990, with a full multi-user universe and player interactions, including 26,600 hosts.

Smartphones are more like computers than actual telephones. Unfortunately, thieves, hackers, and other bad actors know this and are always looking to make money off your personal data. Thankfully, your Galaxy S20, S20+, or S20 Ultra has tools to combat these threats — as long as you know where to look.

A virtual private network is a necessary part of your arsenal if you're insistent on surfing the web privately and securely on your iPhone. The App Store is littered with hundreds of different VPN services that encrypt traffic and mask your IP address, but what they all have in common are connectivity issues.

With all the talk about privacy concerns recently, Google's name keeps coming up because they are a very data-driven company. As an Android user, they know basically everything about you based on your device usage. That can easily scare some people off who are worried about their privacy and security. You do have some say in what personal data Google controls, but what if you want total control?

Windows 10 passwords stored as NTLM hashes can be dumped and exfiltrated to an attacker's system in seconds. The hashes can be very easily brute-forced and cracked to reveal the passwords in plaintext using a combination of tools, including Mimikatz, ProcDump, John the Ripper, and Hashcat.

If you've ever used the Find My iPhone and Find My Friends apps in iOS 12 and below, you may be surprised to hear that those apps have joined forces in iOS 13. Now, instead of two separate apps, they're combined into one convenient package. But what does that mean for you and your privacy and security?

The next libSSH or OpenSSH exploit may be just around the corner. Keep your SSH service out of Shodan's database before hackers find new ways to bypass the password protecting the server.

It is a great time to be a mobile gamer. Not only are there millions of mobile games on the Play Store and App Store, but thanks to some recent developments, we can also even play PC games. AMD recently released an app, which, among other things, lets you play your favorite PC games on your phone.

A lot of people still trust their web browsers to remember every online account password for them. If you're one of those users, you need to adopt a more secure way of managing passwords, because browser-stored passwords are hacker gold mines. With a USB Rubber Ducky and physical access to your computer, they can have a screenshot of all your credentials in their inbox in less than 60 seconds.

Information gathering is one of the most important steps in pentesting or hacking, and it can often be more rewarding to run things on the target itself as opposed to just running scripts against it remotely. With an SQL injection, a hacker can compromise a server and, ultimately, upload and run the "unix-privesc-check" script locally in order to further identify possible attack vectors.