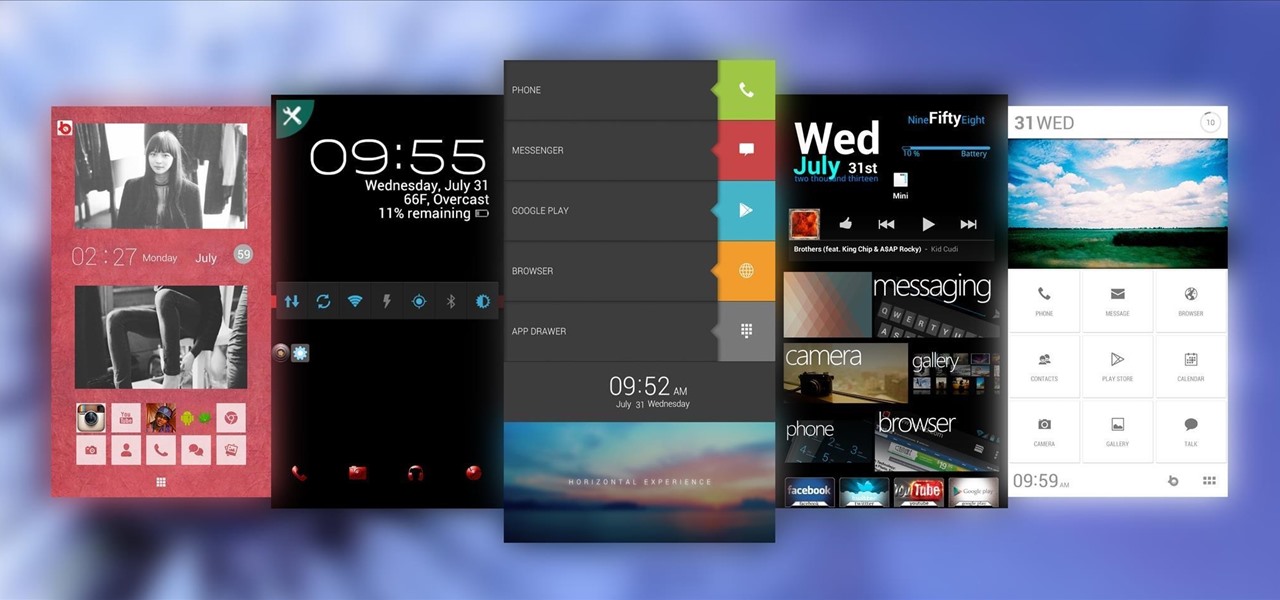
Apple just unveiled iOS 8 at the Worldwide Developer's Conference, and it has a lot of exciting features to play around with. Unfortunately, it won't be available to the public until this coming fall—but that doesn't mean you can't get it right now.
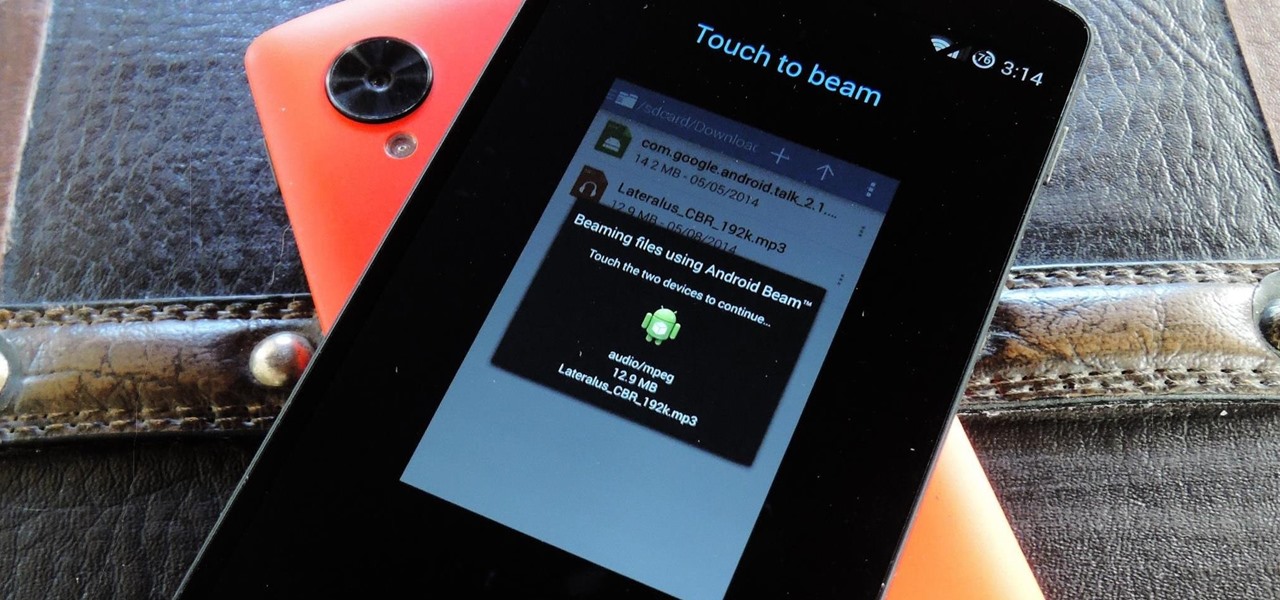
Your Nexus 5 comes with a pretty cool feature baked in called Android Beam. Using NFC, or Near Field Communication, this functionality allows you to send information to another compatible device by simply touching the two together. Most flagship devices have NFC built into them these days, so there is a broad range of devices that your Nexus 5 is capable of sharing information with wirelessly.

Welcome back, my hacker noviates! In a recent post, I introduced you to Shodan, the world's most dangerous search engine. Shodan crawls the globe from IP to IP address, attempting to pull the banners of each web-enabled device and server it finds.

We Nexus users are fairly spoiled. There's a ton of third-party development for our phones, which translates to a virtually endless stream of custom ROMs being made available to us.
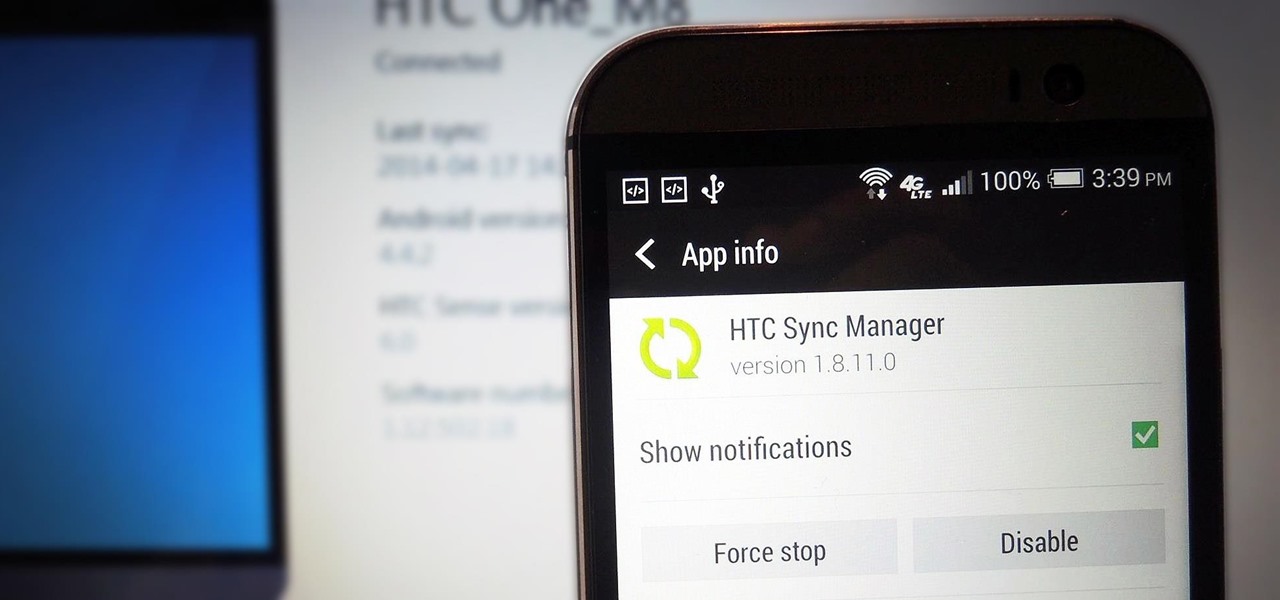
If you've just upgraded to an HTC One M8, chances are you've got some media files you want transferred over from your computer or previous phone. Even after you've done that, there will be times when you want to transfer content back to your computer for safe keeping.

If you're as bad at locking your Nexus up as I am, you have the "slide" option set for your screen lock. It may not be the most secure option, but it's definitely the easiest way to unlock your device while being able to utilize lock screen widgets.

Flashing ROMs can be a tricky process, and sometimes you can end up leaving yourself without a ROM at all, often referred to as a soft brick. If you accidentally wiped your internal memory before a flash or forgot to download the ROM before wiping your system partition, don't worry, there is always a way to get your phone back up and running.

HTC's recent release of a new flagship phone brought tons of fanfare along with it. Dubbed The All New HTC One, the M8 edition of the popular One series phone also marked an update to the HTC Sense UI. Manufacturer skins like Sense can be a bit of a polarizing subject, especially amongst Nexus owners who are used to experiencing Android's interface exactly as Google envisioned it.

As the Chromecast becomes more and more popular (it's even available overseas now), the market has seen an avalanche of Chromecast-compatible apps. We can play games, cast TV stations, and even mirror our screens, but today I'm going to show you a multifaceted tool that'll do everything from broadcasting your camera to displaying your documents.

You've unlocked your bootloader and rooted your HTC One running KitKat, but there's still one lingering aspect of security you've yet to rid yourself of—S-On—the extra security measure HTC implemented into Sense.

Welcome back, my hacker novitiates! Recently, I demonstrated a hack where you could redirect traffic intended for one site, such as bankofamerica.com, to your fake website. Of course, to really make this work, you would need to make a replica of the site you were spoofing, or better yet, you could simply simply make a copy of the original site and host it on your own server!

Nokia's recent foray into the world of Android brought a plethora of goodies along with it. The Finnish smartphone manufacturer offers a slightly different take on our favorite mobile operating system, with customizations ranging from ringtones to its very own app store.

Welcome back, my aspiring hackers! Domain Name System (DNS) is one of those things we seldom think about unless it doesn't work. Then, it can be very frustrating when we attempt to navigate to a website and we get that frustrating error message.

Welcome back, my novice hackers! We've done a number of tutorials using one of my favorite hacking tools, Metasploit. In each of them, we've used the msfconsole, which can be reached through either the menu system or through simply typing "msfconsole" from the terminal.

A long time ago, we recommended the Hover Zoom extension for Chrome as an easy way to blow up small image thumbnails without actually have to "click" on the images themselves. Over the past year, there have been reports that Hover Zoom now collects and sells your browsing data to third-party advertisers without your consent.

Currently, all Nexus tablets running Jelly Bean or higher can enjoy multiple user accounts. With tablets often migrating between various people in the same household, there’s no reason for Dad’s finances to mingle with little Tammy’s candy crushing. Multiple users, each with separate profiles, just makes sense on an Android tablet.

It's time. You've experimented with apps from the Play Store, you've switched your lock screen, and maybe you've taken different launchers out for a spin. If, throughout your tinkering, you've found yourself chanting, "More. More. Give me more!" then now is the time. It's time to root.

For my money, one of the greatest improvements brought about from the smartphone revolution is the advent of visual voicemail. No longer do we have to slog through dial menus or trudge through every single message to get to the next. We can just look at our messages, right there on our screens, organized neatly like emails or text messages.

Welcome, my hacker novitiates! As part of my series on hacking Wi-Fi, I want to demonstrate another excellent piece of hacking software for cracking WPA2-PSK passwords. In my last post, we cracked WPA2 using aircrack-ng. In this tutorial, we'll use a piece of software developed by wireless security researcher Joshua Wright called cowpatty (often stylized as coWPAtty). This app simplifies and speeds up the dictionary/hybrid attack against WPA2 passwords, so let's get to it!

Welcome back, my rookie hackers! When Wi-Fi was first developed and popularized in the late '90s, security was not a major concern. Unlike wired connections, anyone could simply connect to a Wi-Fi access point (AP) and steal bandwidth, or worse—sniff the traffic.

The NSA's massive internet spying efforts will continue. In President Obama's latest press conference, he went public to (in so many words) say that the NSA's spying efforts will continue uninterrupted. This, coming just weeks after the Amash Amendment which would have defunded the program, was narrowly defeated in the House (you can check if your congressmen voted against it here).

Welcome back, my fledgling hackers! Nearly every commercial enterprise worth hacking has an intrusion detection system (IDS). These network intrusion detection systems are designed to detect any malicious activity on the network. That means you!

Customizing isn't all rooting and ROMs—there are plenty of ways to customize your Samsung Galaxy Note 2 or other Android device without gaining superuser access. One of the easiest ways is to install an Android launcher, sometimes called a home launcher, that matches your style.

Welcome back, my greenhorn hackers! Continuing with my Wi-Fi hacking series, this article will focus on creating an invisible rogue access point, which is an access point that's not authorized by the information technology staff and may be a significant security vulnerability for any particular firm.

Welcome back, my nascent hackers! Earlier, I wrote a guide on finding operating system and application vulnerabilities in Microsoft's own security bulletins/vulnerability database. In this tutorial, I will demonstrate another invaluable resource for finding vulnerabilities and exploits by using the SecurityFocus database.

Welcome back, my rookie hackers! Several of you have written me asking about where they can find the latest hacks, exploits, and vulnerabilities. In response, I offer you this first in a series of tutorials on finding hacks, exploits, and vulnerabilities. First up: Microsoft Security Bulletins.

Welcome back, my hacker novitiates! Many of you have written me that you're having difficulty installing and running Metasploit on a variety of platforms. No matter if you're using Mac, Linux, or Windows, I strongly recommend you install BackTrack as your secondary OS, a virtaulization system, or on an external drive. This particular Linux distribution has many hacking and security tools integrated—including Metasploit.

One of the best things about the Samsung Galaxy S3 is the ability to modify the device in countless ways, as with any other Android device.

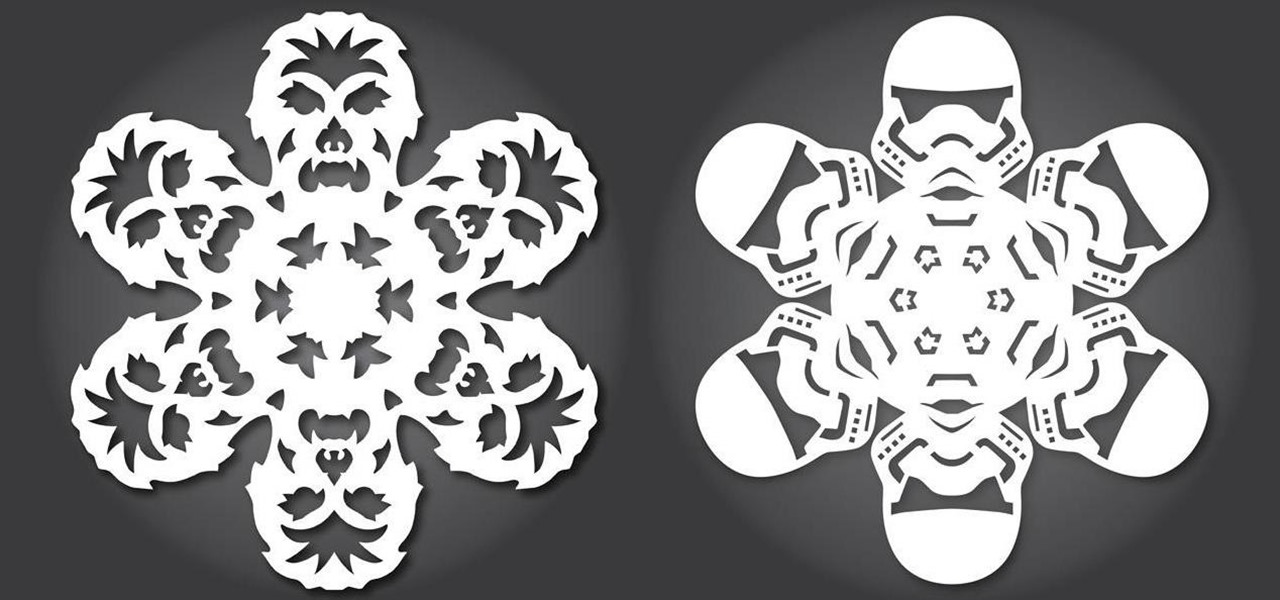
Everyone knows how to make paper snowflakes, but the kind you learned to cut in kindergarten can get a little boring. However, they are free DIY holiday decorations, and they don't have to be a generic snowflake design. They can be anything you want, from nerdy math kirigami to all the Star Wars characters you can think of!

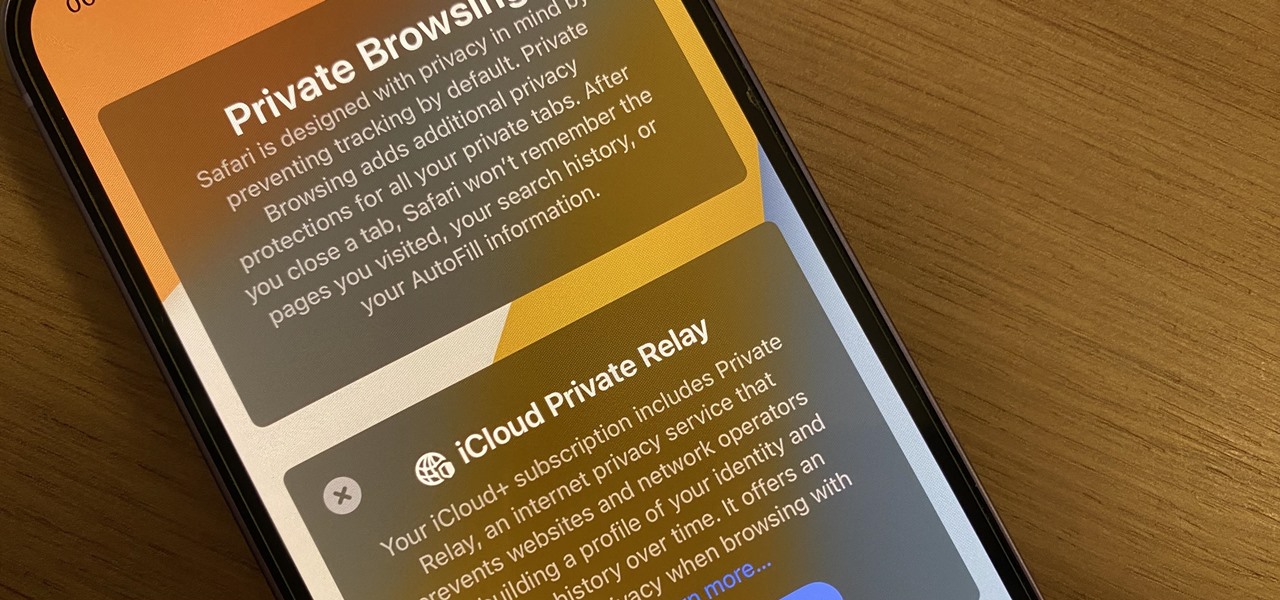
Safari's massive upgrade in Apple's latest iPhone software update includes new features you won't find in any other web browsers on iOS, from better ways to stay organized to enhanced security and further privacy protections.

Apple's Live Voicemail lets you preview what an incoming caller is speaking to your voicemail system in real time. It's a revolutionary feature like Visual Voicemail on the original iPhone, only better since it helps you screen calls to quickly decide whether to answer or ignore callers. It's similar to answering machines, whose popularity peaked in the mid-90s, but you quietly read transcribed messages instead.

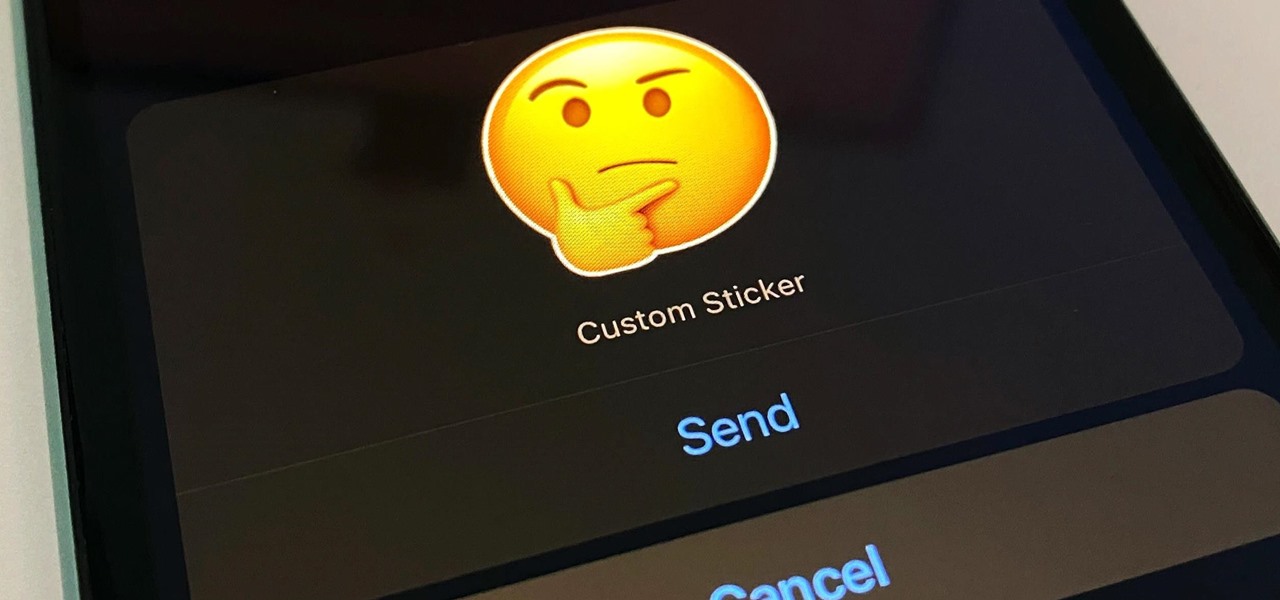
WhatsApp has a new sticker-making tool in the iPhone app that lets you create custom stickers directly in chats using your own images, eliminating the need to rely on third-party apps to make them.

It's easy to accumulate hundreds of Safari tabs on your iPhone, which makes hunting for specific tabs more difficult, especially when they're spread across different groups. Having too many tabs can even slow down Safari itself. You can close all tabs in a group quickly, but not if you want to save some. To prevent this mess, Safari can automatically weed out the tabs it thinks you don't need.

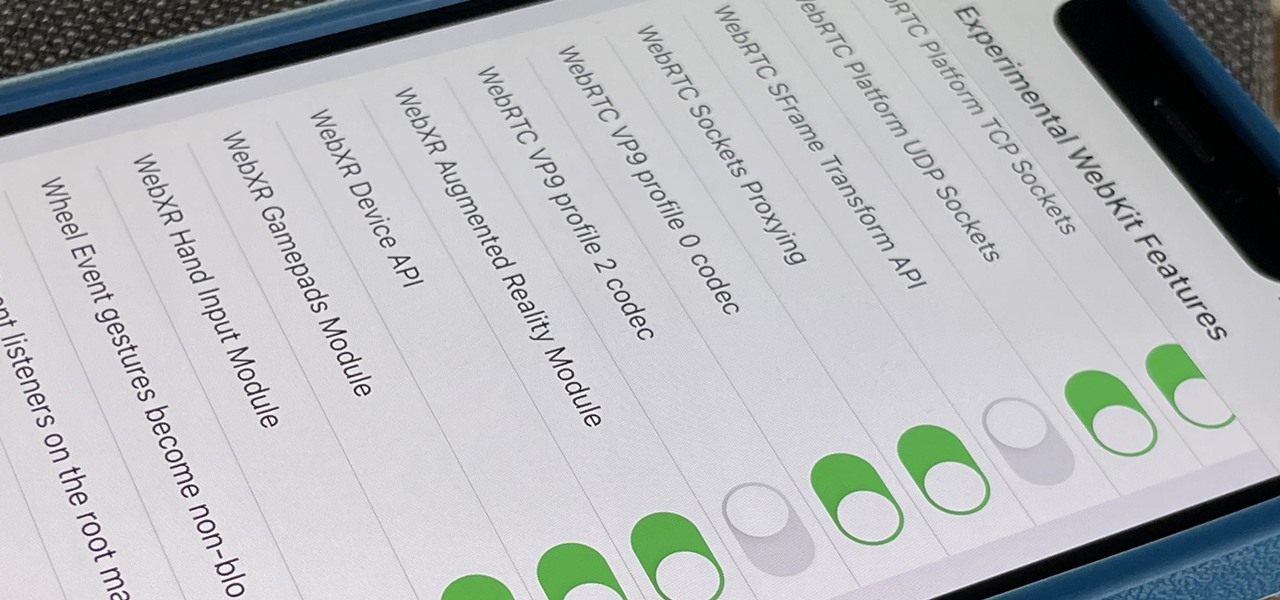
Safari's advanced experimental features give you access to new browser initiatives, upcoming web tools, element changes, behavior adjustments, and other preliminary feature tests in development by Apple. If you use them on your iPhone, you can either improve your Safari experience or wreck it. Resetting the flags provides a fresh start.

After receiving $100 million in funding in 2018, smartglasses maker Rokid is going the crowdfunding route to finance its latest product.

When you first open Safari after updating your iPhone to iOS 15, you might be a bit surprised by the design change. Apple attempted to make browsing the web on its smartphones more natural and cohesive, but it may leave you wondering just how to actually navigate your tabs.

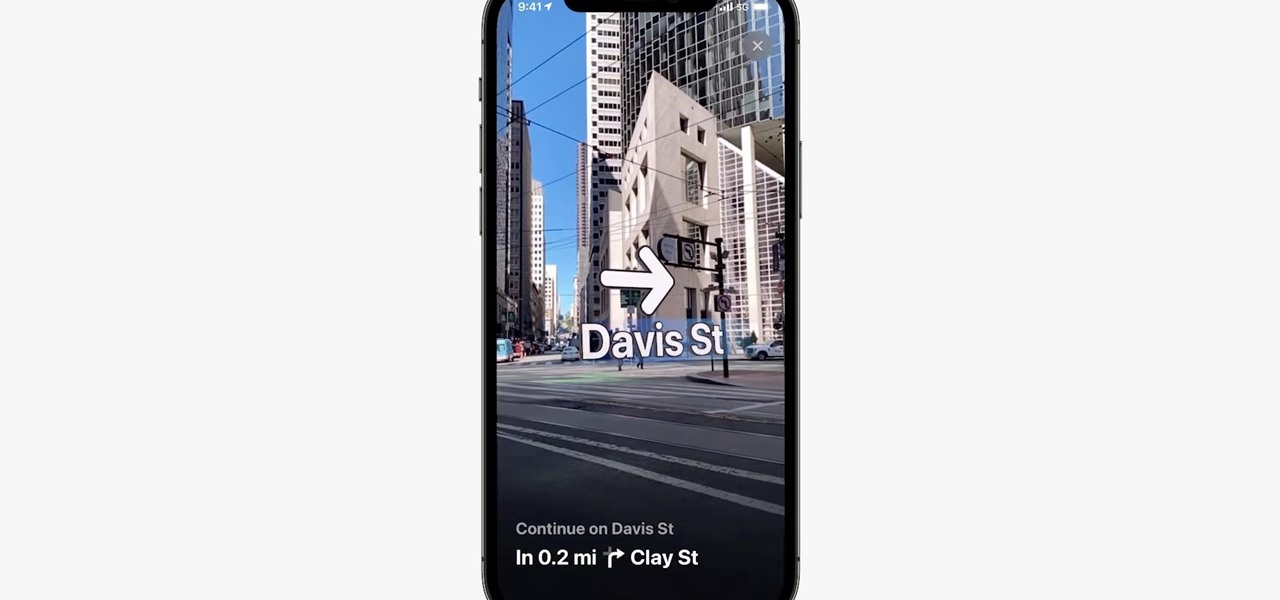
Mobile augmented reality for iOS typically comes through apps via ARKit, but Apple is borrowing a few pages from Google's playbook and bringing AR directly to iOS 15.

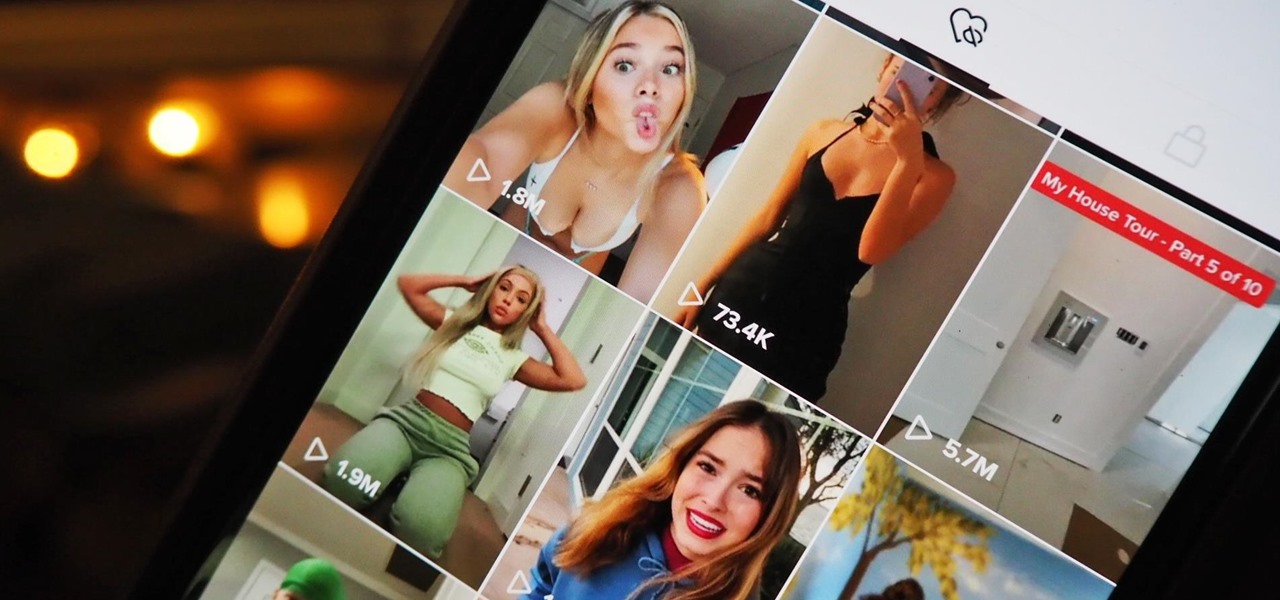
Every video you like on TikTok, whether it's a stranger performing a series of choreographed movements or a celebrity showing off their new workout, is saved to your profile. If you want to watch your liked videos at any time in the future, you can easily do so from your profile — but so can everyone else.

Even with the convenience of online storage like iCloud and Google Drive, data management can be a constant struggle on your iPhone. If you continuously find yourself having to delete messages, photos, videos, and other files to make room for other things, know that there's an easy way to free up space without erasing anything important or having to dig through documents and data yourself.

The virtual collaboration tool known as Spatial has consistently been one of our favorites due to its ability to leverage high-end augmented reality headsets to more easily facilitate remote meetings.