If you pre-ordered your Samsung Galaxy S4, it might very well be possible that you're reading this on your brand spanking new Android device. As is commonplace with the release of popular smartphones, rooting instructions are usually released simultaneously. I mean, what's the point of paying so much for an expensive phone if you can't have a little fun? Android developer Dan Rosenberg (aka djrbliss) recently announced that you can root your Samsung Galaxy S4 using the root exploit he origina...

What if the Dark Knight used Apple's state-of-the-art Maps application for turn-by-turn driving directions? Well, let's just say you wouldn't want to be in a shopping mall when Batman is in a hurry. Movieclips posted some hilarious parodies of film characters using Apple's new Maps app for directions. Just see what happens when Batman tries to use his iPhone 5 to navigate Gotham on his way to save Rachel in The Dark Knight.

Apple's Reminders app on your iPhone or iPad now comes equipped with a new way to organize your tasks: sections. With sections, you can better sort through reminders in your lists by placing tasks into likeminded buckets or even in kanban-style columns for more efficient workflows.

Whether you've celebrated multiple cake days or you're just now getting your feet wet with Reddit, it's a rite of passage to choose your preferred smartphone client. Quick spoiler: Your best option most certainly is not the official Reddit app.
Now that the transfer tool for migrating your Google Play Music library to YouTube Music is rolling out, more fans of the former, which will meet its end in 2020, are giving its replacement a try.

Transferring hundreds of screenshots, webcam recordings, keystroke logs, and audio recordings between your VPS and a local Kali machine can be tricky. Services like Dropbox don't always have the best privacy policies and suffer data breaches just like any other website. To mitigate these risks, we'll use a secure, open source, and decentralized alternative.

Having your home and work addresses set in Apple Maps makes them incredibly easy to navigate to no matter where you're located. If you move to a new house, stay in a hotel or resort while vacationing, report to a different office, or have multiple job sites to visit regularly, updating these addresses isn't only straightforward — there's more than one way to do it.

There are over 3 million apps in the Google Play Store, all optimized for the small screen in your hands. While that number sounds staggering, there are still many online tools and websites that require you to use a mobile browser since app development is expensive. However, that's where Progressive Web Apps (PWAs) come into play, a cost-effective way to turn websites into mobile apps.

Welcome back, my greenhorn hackers! A few years back, Microsoft implicitly recognized the superiority of the Linux terminal over the GUI-based operating system by developing PowerShell. Since Windows 7, every Windows operating system has had PowerShell installed by default, and they even made PowerShell capable of running Linux commands on Windows!

Welcome back, my rookie hackers! The Golden Fleece of hackers is to develop a zero-day exploit, an exploit that has not been seen by antivirus (AV) software or and intrusion detection system (IDS). A zero-day exploit is capable of skating right past these defenses as they do not contain a signature or another way of detecting them.

Welcome back everyone. As many of you know, reconnaissance is extremely important in any successful hack. Without proper reconnaissance, we won't know what we're about to get into, literally.

This is my first How-To on Null-Byte, so I hope it's not too complicated written, because I am not a native english speaker. I don't use pictures, but this Tutorial is a good supplement for my updated Tutorial here.

Welcome back, my tenderfoot hackers! Now that we have begun this trip down web app hacking lane, we need to first address target reconnaissance. Like any hack, reconnaissance is critical. (Are you tired of me saying that yet?)

Most Android devices allow you to simply replace a ZIP file in your /system/media folder if you want to change your boot animation. Unfortunately, though, this isn't the case for the Galaxy S5, as it's been buried deep in Samsung's TouchWiz skin.

Transition animations are an essential element of any mobile operating system. They give the user a sense of what's happening on the screen, where the apps are coming from, and where they're going.

Welcome back, my hacker novitiates! In previous guides, we have used one of the most powerful hacking platforms on the planet, Metasploit, to perform numerous hacks. They ranged from exploiting Windows XP and Windows 7/8 vulnerabilities, to installing a keylogger and turning on a webcam remotely. We have even been able to save the world from nuclear annihilation, see if our girlfriend is cheating, spy on suspicious neighbors, evade antivirus detection, and more.

Greetings. This how-to on hacking Windows 7/8/10 etc. admin account passwords using Windows Magnifier is focused on adding, changing, or deleting an admin level account on a Windows 7/8/10 etc.

Welcome back, my fledgling hackers! If you're like most aspiring hackers, at one time or another you've probably spent too much time playing Call of Duty and not enough time preparing for your final exams.

It's common for IoT devices like Wi-Fi security cameras to host a website for controlling or configuring the camera that uses HTTP instead of the more secure HTTPS. This means anyone with the network password can see traffic to and from the camera, allowing a hacker to intercept security camera footage if anyone is watching the camera's HTTP viewing page.

If you're using a mobile device, it's a pretty safe bet that your apps are sending lots of information back and forth from their servers. To make sure there is no inappropriate data collection going on, it's worth setting up a web proxy to spy on this traffic, so you know exactly which apps are "phoning home" and when.

During a penetration test, one of the most important aspects of engaging a target is information gathering. The more information you have coming into an attack, the more likely the attack is to succeed. In this article, I'll be looking at SpiderFoot, a modular cross-platform OSINT (open-source intelligence) gathering tool.

In this video a user shares how to use an external monitor as the main display on the Mac. For instance a recently purchased flat screen TV can be used as the primary display. So if you want to use your external monitor as your primary display then all you have to do is follow these simple stops.

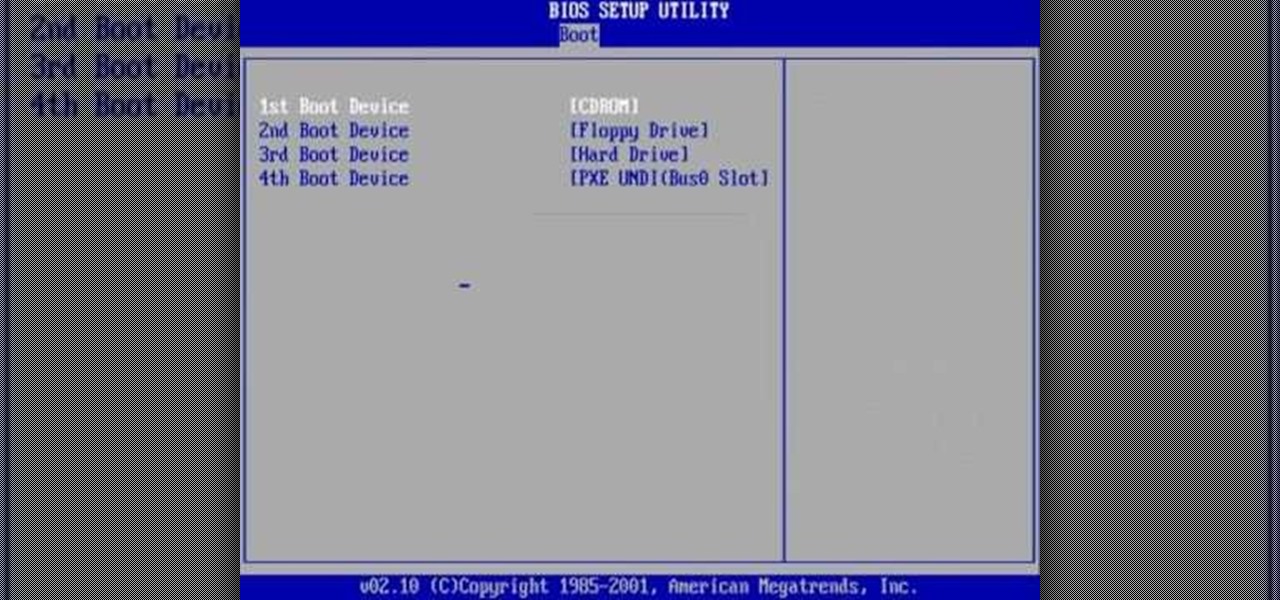
The video shows users how to change the boot sequence in a computer with an older AMI (American Megatrends, Inc.) BIOS to boot from the CD/DVD drive. This is required, for instance, if you need to reinstall an operating system, or fix a corrupted windows installation by running Windows Setup from the installation CD. Users should first enter the BIOS setup by pressing the delete key when prompted shortly after powering the computer on. Once the Bios Setup screen has loaded, users may navigate...

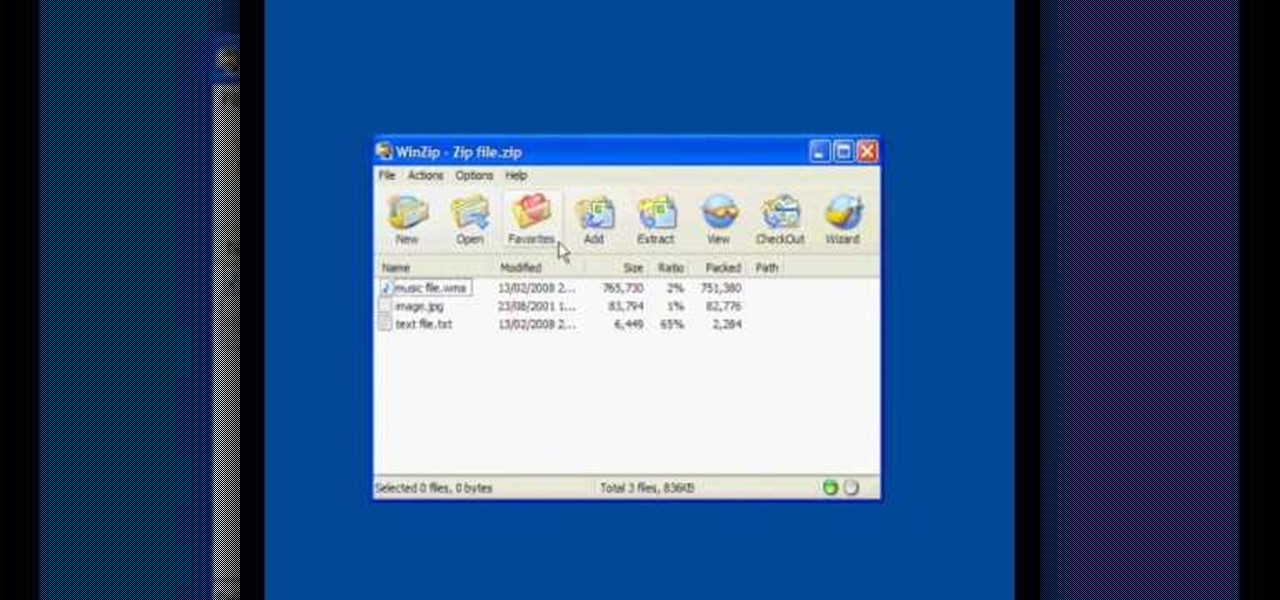
Do you have a hard time extracting/unzipping files using WinZip? If you follow along we will be shown a couple simple steps on how to unzip files using WinZip.

In this instructional video on how to use Facebook, you will learn how to remove or delete applications from your Facebook profile. The author guides you through the process, step by step, on how to navigate to and find the page containing all the applications associated with your profile. She then leads you through the steps to find the application you wish to delete, and shows you where the "Remove" button is located, and explains that you can either remove the application completely from y...

Need to easily convert Fahrenheit to Celsius? What about Rankine and Kelvin? There's an easy way to do it online, and this video tutorial shows you how. Navigate your browser to Tampile, where you'll find an easy to use temperature converter. The drop-down menu in the center of the page allows you to choose between Fahrenheit, Celsius, Rankine, and Kelvin. All you have to do is input a temperature and then press the "Convert Temperature" button. The results will appear in a table directly bel...

File collaboration is one of the best integration features between Office 2003/Office 2007 and SharePoint. These task panes allow you to access and modify content in a SharePoint site from within Office without having to navigate to the site using your browser. The feature is available in the following Office 2003 and Office 2007 applications: Word, Excel, Microsoft Project, OneNote, PowerPoint, and Visio.

Businesses leave paper trails for nearly every activity they do, making it easy for a hacker or researcher to dig up everything from business licenses to a CEO's signature if they know where to look. To do this, we'll dig into the databases of government organizations and private companies to learn everything we can about businesses and the people behind them.

It's easier than you might think to hack into Wi-Fi routers using just one unrooted Android phone. This method doesn't require brute-forcing the password, a Windows OS for converting PowerShell scripts into EXE format, a reliable VPS for intercepting hacked Wi-Fi passwords, or Metasploit for post-exploitation tricks.

Fans attending the US Open Tennis Championships in Queens, New York, which kicks off on Monday, will have the opportunity to meet tennis star Venus Williams in an augmented reality game sponsored by American Express.

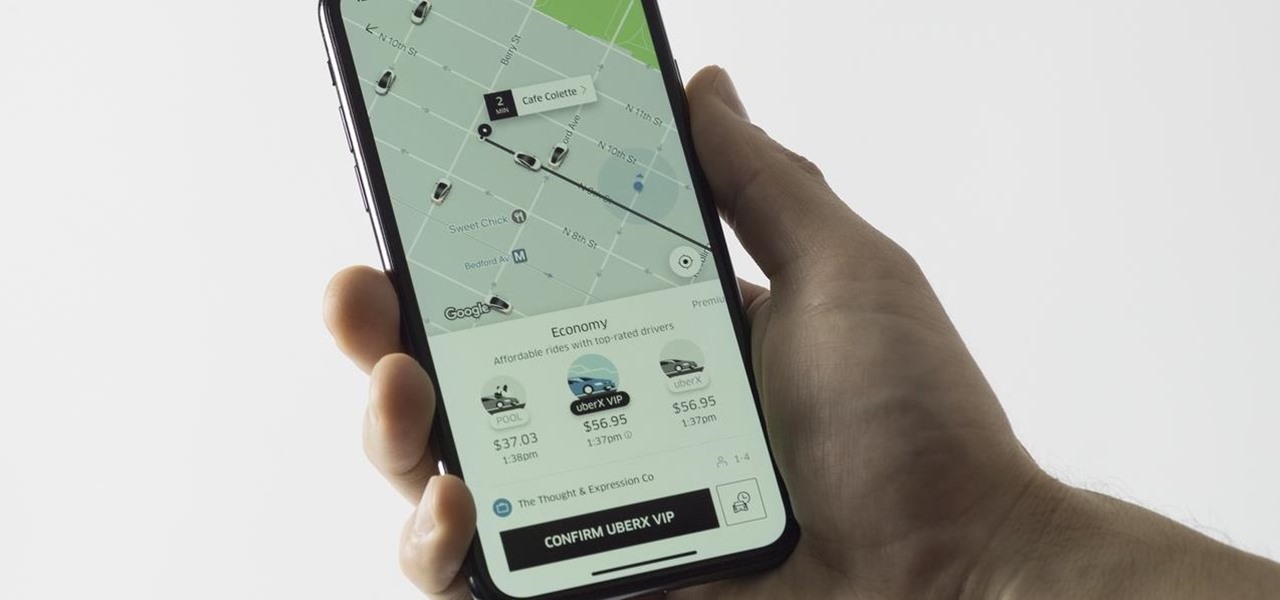
Uber is one of the best ride sharing services out there, allowing you to travel without needing to be tethered to a car of your own. Still, if you're a frequent flyer, you may get tired of entering the same few locations into your app every time you use it. Fortunately, Uber lets you streamline this process.

Earlier this year, we got our first taste of Android Pie in the form of Developer Preview 1. As with all past Android previews, DP1 was limited to Google devices — but at Google I/O 2018, Google announced that Developer Preview 2 would be accessible to other devices, including the Essential PH-1.

Many wonder how driverless cars will ever be able to navigate through any driving condition imaginable — but the point is self-taught machines, in theory, have the innate ability to adapt to chaotic and extreme driving conditions in ways far superior to what humans are capable of.

Xiaomi phones run a skinned version of Android known as MIUI, which, over the years, has been a popular custom ROM. One of the standout features Xiaomi has added to the mix is something called Quick Ball, which lets you navigate your phone by swiping inward from a small circle that resides on the edge of your screen.

If your mechanical home button or capacitive navigation keys are on the fritz, doing something as simple as navigating your phone's interface becomes a tedious chore. In this situation, some users have turned to root mods that enable Android's software navigation bar to solve the problem, but not everyone is willing or able to root their device.

Today at the Unite '16 conference in Los Angeles, Unity's Timoni West and Amir Ebrahimi showed off its new virtual reality authoring and world editor, EditorVR, using the HTC Vive. Coming in December to Unity is a version of its editor that works inside a VR headset, which will change the way developers interact with the worlds they build—even if they aren't building for VR.

MagicTree is often the go-to tool for data collection and reporting for many pentesters. It organizes data in nodes in a tree-structure which is very efficient at managing host and network data. Reports can be completely customized to meet the user's needs. Also, MagicTree allows you to import XML data and has XSLT transforms for Nessus, Nmap, OpenVas, Burp, Nikto. MagicTree comes pre-installed in Kali.

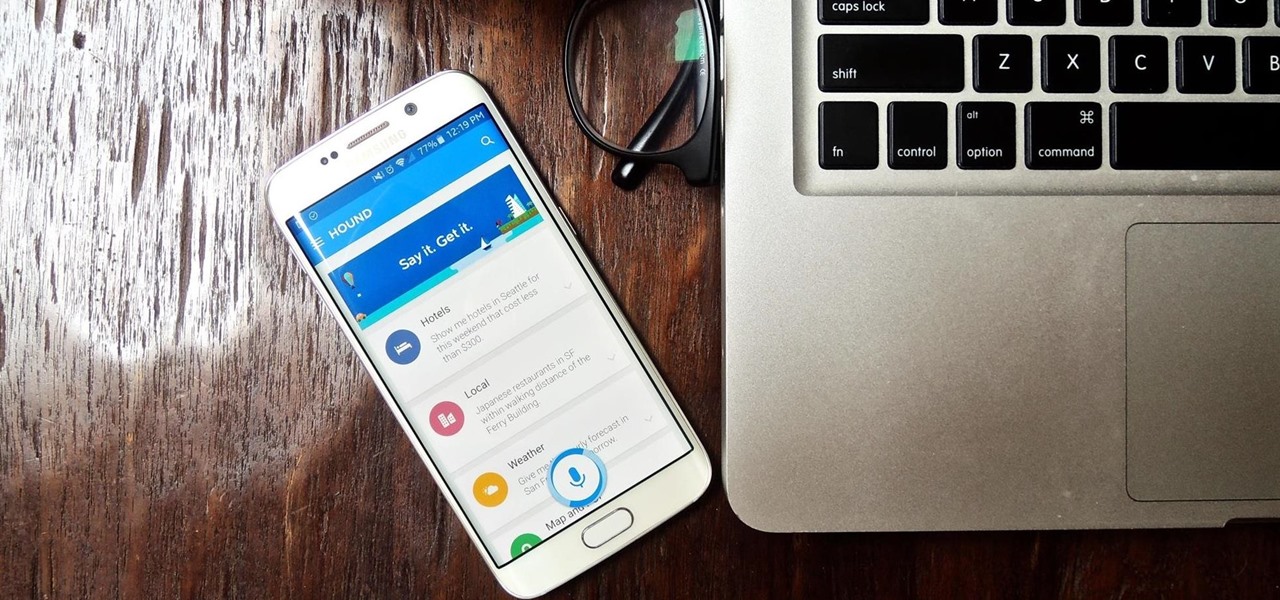
SoundHound's new virtual assistant application, Hound, is gaining a lot of buzz in the tech world—especially after a demo video showed just how awesome it works (it has amassed over 1.6 million views in under a week).

Since the days of Android Jelly Bean, Samsung has implemented an energy preservation feature known as dynamic voltage and frequency scaling, or DVFS for short. What this essentially does is limit or adjust the frequency of the microprocessor to conserve power and prevent excessive heat from being generated.

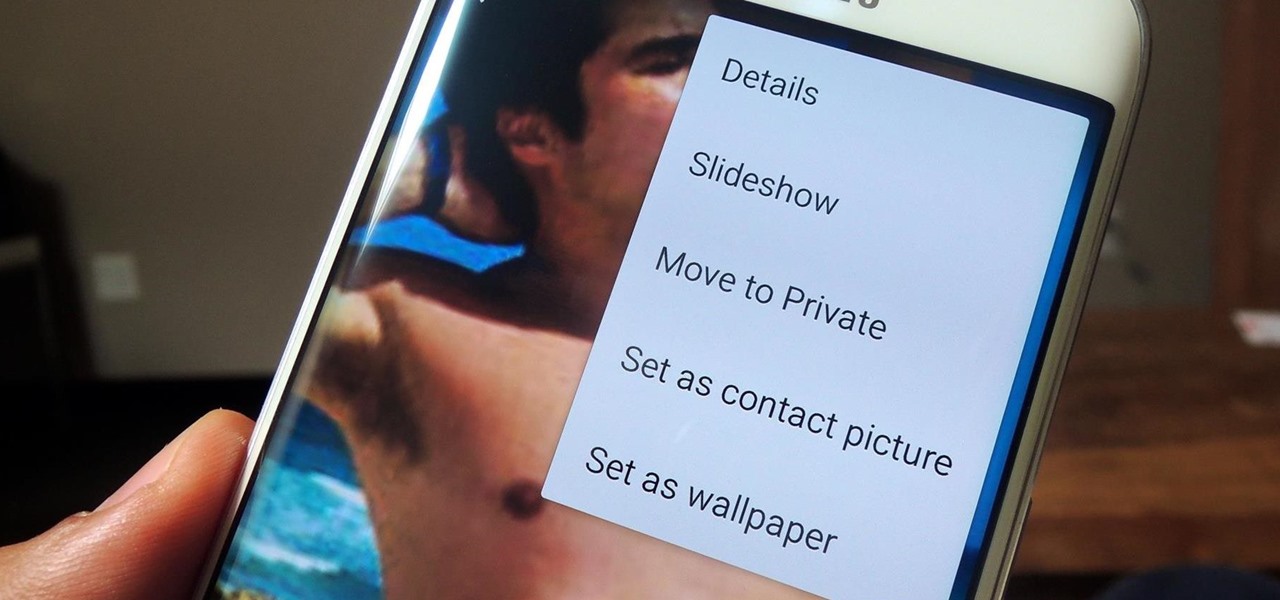
If you have a smartphone, chances are you have something on it you don't want others seeing. Whether it be photos, videos, or documents, some things are best left private. Not everyone is a saint, after all.