
Hack Like an Elite: Batch Scripting for Malicious Purposes: PART 3 (The Main One)
At last, what you all finally waited for! Hi! Fire Crackers,


At last, what you all finally waited for! Hi! Fire Crackers,

OR rather How to make the Backdoor Persistent: Hello, my Cold and Merciless Hackers,

Welcome back, my aspiring hackers! Those of you who use Windows in a LAN environment understand that Windows machines can share directories, files, printers, etc. using "shares." This protocol dates back to the 1980s when the then dominant computer firm, IBM, developed a way for computers to communicate over the LAN by just using computer names rather than MAC or IP addresses.

Welcome back, my budding hackers!

If you've ever noticed that the stock launcher on an Android device seems to just feel faster than any third-party home screen replacement app, this is not a placebo effect. Most manufacturers, Samsung included, force their stock launchers to reside permanently in your phone's memory, thus reducing the risk of redraws.

Many Android games use large, storage-heavy OBB files to store supplemental data. Generally, games with high-end graphics download these extra files when you install them from the Google Play Store.

Welcome back, my tenderfoot hackers! As you know, DNS, or Domain Name System, is critical to the operation of the Internet. It provides us with the ability to type in domain names such as www.wonderhowto.com rather than the IP address. This simple service saves us from having to memorize thousands of our favorite website IP addresses. Instead, we simply type in a domain name to retrieve the website.
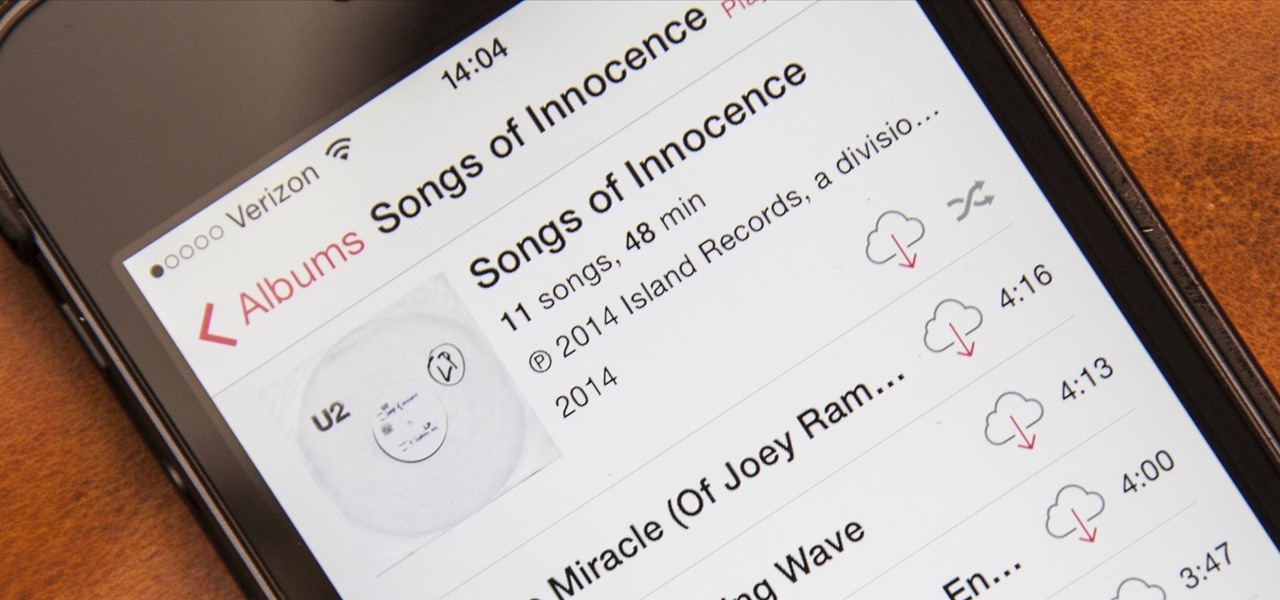
From my experiences, there are only two types of U2 people: those that love them and those that hate them. I'm the latter, so it's pretty damn annoying that Apple just added U2's new album, "Songs of Innocence," to my iCloud. If you find it creepy that U2 is appearing on your iPhone or in iTunes, don't worry—I've found a few ways to deal with it. UPDATE: How to Delete U2 Forever & Ever

Welcome back, my tenderfoot hackers! In continuing my series on digital forensics using Kali, I want to introduce you to two complementary tools, both built right into Kali Linux. These are Brian Carrier's tools Autopsy and Sleuth Kit.

Welcome back, my tenderfoot hackers! Not too long ago, I showed how to find various online devices using Shodan. As you remember, Shodan is a different type of search engine. Instead of indexing the content of websites, it pulls the banner of web servers on all types of online devices and then indexes the content of those banners.

Sony has been hard at work refining its Xperia line of flagship phones. With a 6-month release cycle, they've managed to slim bezels, increase viewing angles, and boost processing power in the 1.5-year span between the original Xperia Z and the Z2.

Welcome back, my tenderfoot hackers! We have looked at a number of ways that we sniff traffic on the network with such tools as Wireshark, tcpdump, dnsiff, and others, but each of these tools is only capable of pulling packets off the wire.

We've all been there. Stranded in a large lot or parking garage, braving the rows upon rows of identical cars in an endless concrete landscape because, for the very life of us, we can't remember where we stashed the very ride that brought us there.
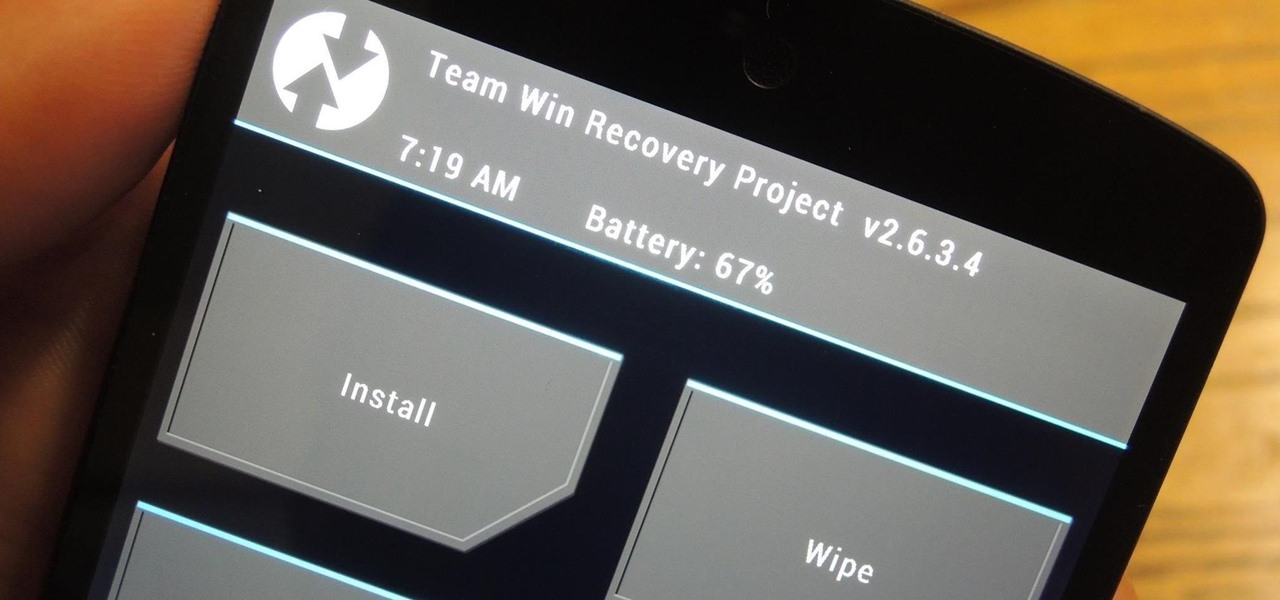
A rooted Android device means we're on our way to some truly amazing customization options. But there may be a few steps left to completing that journey, and a major one is installing a custom recovery.

For my money, one of the greatest improvements brought about from the smartphone revolution is the advent of visual voicemail. No longer do we have to slog through dial menus or trudge through every single message to get to the next. We can just look at our messages, right there on our screens, organized neatly like emails or text messages.

Welcome back, my aspiring hackers!

Welcome back, my nascent hackers! Earlier, I wrote a guide on finding operating system and application vulnerabilities in Microsoft's own security bulletins/vulnerability database. In this tutorial, I will demonstrate another invaluable resource for finding vulnerabilities and exploits by using the SecurityFocus database.

Welcome back, my hacker trainees! A number of you have written me regarding which operating system is best for hacking. I'll start by saying that nearly every professional and expert hacker uses Linux or Unix. Although some hacks can be done with Windows and Mac OS, nearly all of the hacking tools are developed specifically for Linux. There are some exceptions, though, including software like Cain and Abel, Havij, Zenmap, and Metasploit that are developed or ported for Windows.

Welcome back, my novice hackers! Most of my tutorials up until this point have addressed how to exploit a target assuming that we already know some basic information about their system. These include their IP address, operating system, open ports, services running, and so on.

Welcome back, my neophyte hackers! Several of you have written me asking how to crack passwords. The answer, in part, depends upon whether you have physical access to the computer, what operating system you are running, and how strong the passwords are.
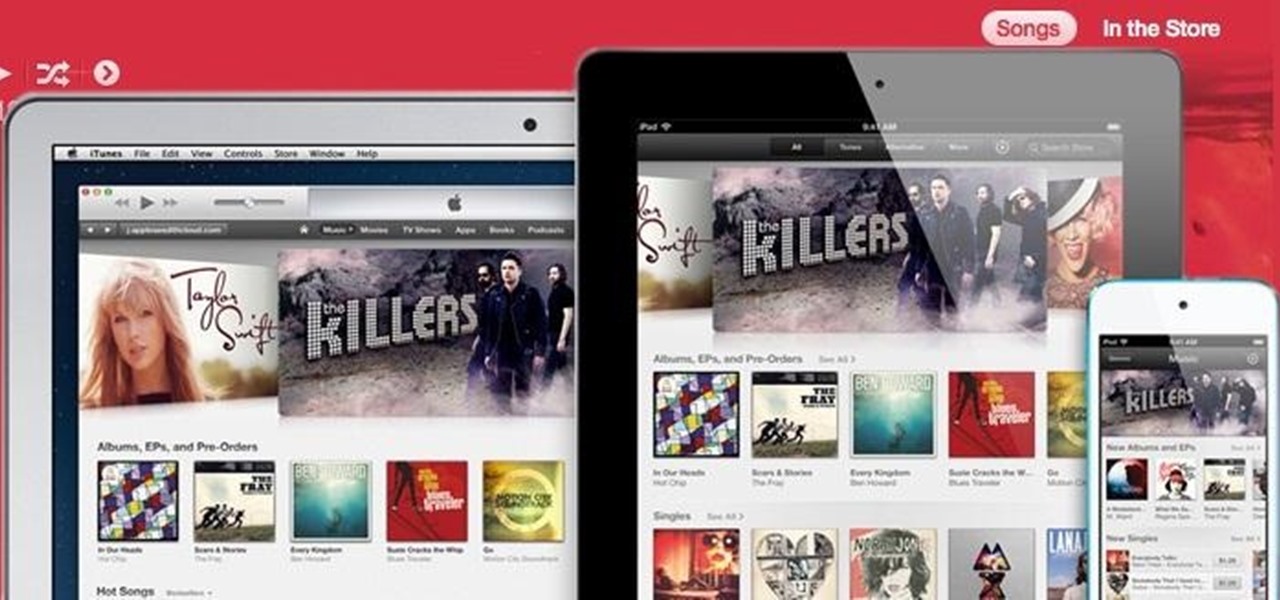
After a two-month delay, Apple has finally released iTunes 11, which was initially slated to be released alongside iOS 6.

Shot at the Brambuk National Park and Cultural Centre in Australia, this video shows how to properly throw a boomerang. Take a look this video and give it a try.

The dance of the Philippines uses movements and costumes to tell cultural stories. Learn about Filipino dancing in this free dance lesson video from an award-winning Filipino dancer.

Burmese dance is an ancient cultural dance style that uses simple movements and gestures to tell a story. Learn more about this dance from Burma in this free dance lesson video series from a professional Burmese dancer.

Those of us who've taken the time to learn how to code are relatively well-suited for shakeups in the economy. Despite the recent and notable disruptions caused by the COVID-19 outbreak, demand for talented and trained programmers and developers is still high, and it will likely keep rising as companies in every industry adapt their business models to a more remote world.
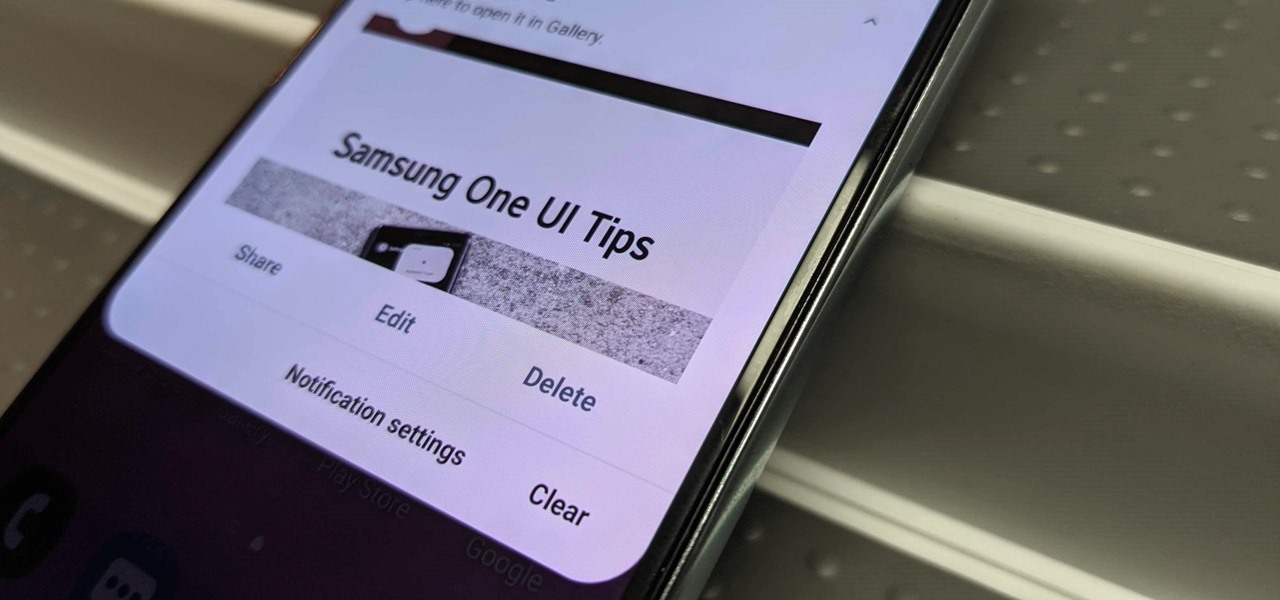
An unfortunate byproduct of Samsung's One UI version of Android is redundancy, where you have the Google/AOSP way of doing things mixed with Samsung's methods at the same time.
One of the greatest trends to emerge from this period of home isolation is the live concert broadcast from bedrooms and living rooms across the planet. Though public gatherings are on hold, you can still impact people with your music and mixes. In fact, it's helping many people get through this confusing time.

With No Time to Die, the 25th installment in the James Bond saga, arriving in April and Black Widow, the first solo film for the Marvel Cinematic Universe's own secret agent, following a month later, what better way to get in the espionage mood than some augmented reality spy gaming?

Augmented reality already seemed like the ideal technology to advertise for a movie based on the premise of being sucked into a video game world the first time around. For the sequel, how about two times the immersion?

Magic Leap took years to launch, but when it did, the company managed to quickly become the leading rival to Microsoft's HoloLens (at least when it comes to experimental immersive experiences).
Apple seeded public testers the second beta for iOS 13.3 eight days ago. That update mainly added stability patches to iOS as a whole, as did the public releases of iOS 13.2.2 and iOS 13.2.3. Now, following the release of iOS 13.3 developer beta 3 earlier today, Apple seeded the same beta to public testers.
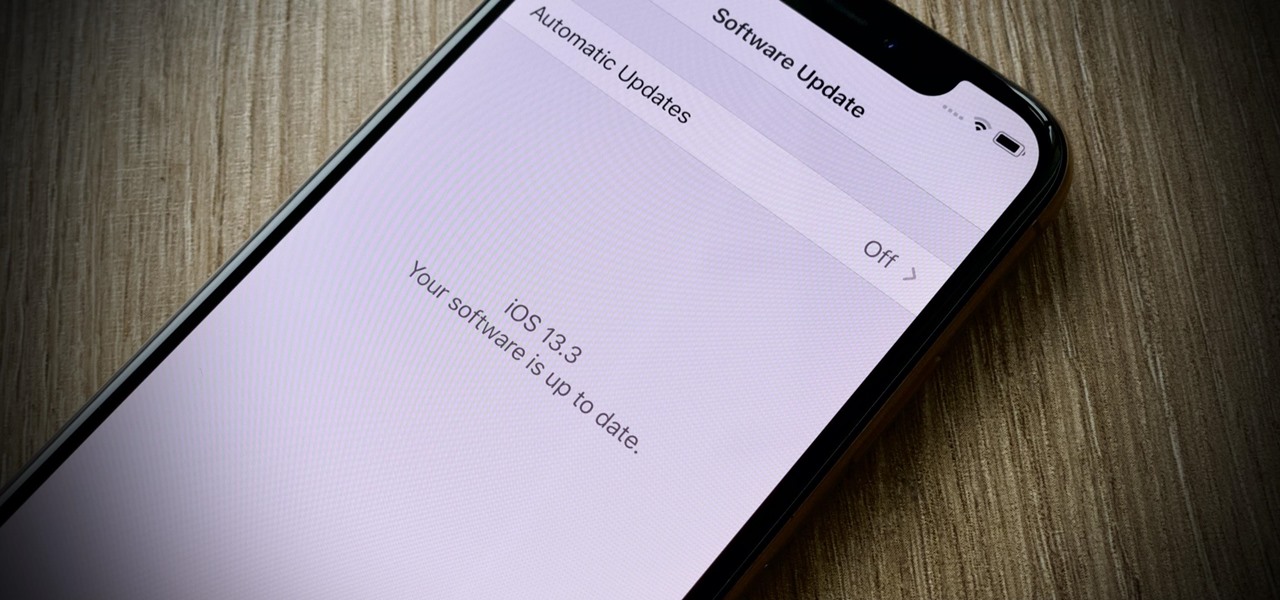
Just two days ago, on Nov. 18, Apple released iOS 13.2.3 to the general public, which included stability updates for bugs affecting iOS 13.2 and earlier. Today's update isn't for the general public, however. Instead, Apple just pushed out iOS 13.3 developer beta 3 for software testers.
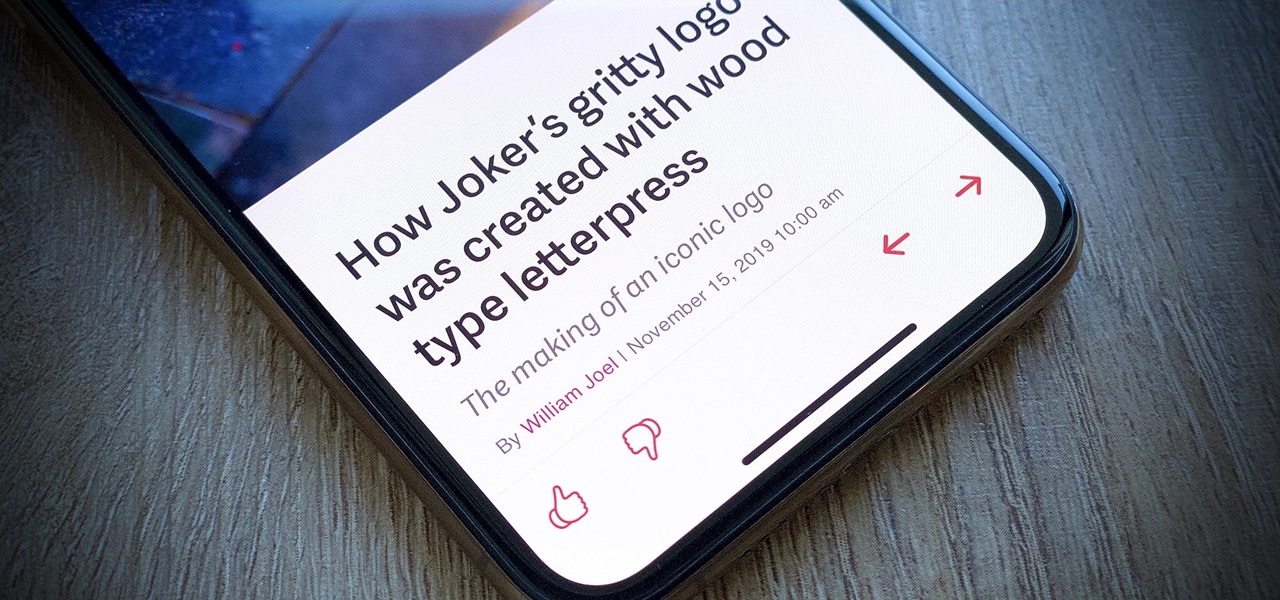
Apple's upcoming iPhone update, iOS 13.3, doesn't add as many new features as iOS 13.1 or 13.2, but there's one under-the-radar change you'll love if you use Apple News on a daily basis.

Starbucks is spicing things up ahead of this holiday season with a little augmented reality joy. This week the company launched its first Instagram filter, called Holijoy, delivered like an early Christmas gift and packing four seasonal lenses.

Google has started to release a Go line of Android apps. These apps offer a minimalistic version of their major app counterpart. So far, we have Go versions of Maps, Photos, Gmail, and more. Who are these apps for and why would you want to use them? Here's a quick overview of Google Photos and Gallery Go.

Look Around in Apple Maps gives you a high-resolution 3D view of roads, buildings, and other imagery in an interactive 360-degree layout. We haven't had anything like this in Apple Maps since iOS 5 when Google's Street View was incorporated. Now, in iOS 13, seven years later, we have street-level views again, only better. But Look Around isn't available everywhere yet.

Cosmetics augmented reality specialist ModiFace appears to be really benefiting from the brand power of L'Oréal, which acquired the company last year.

After winning the 2015 FIFA Women's World Cup, the USA Women's National Soccer Team is ready to defend its title in the 2019 tournament.

Directory traversal, or path traversal, is an HTTP attack which allows attackers to access restricted directories by using the ../ characters to backtrack into files or directories outside the root folder. If a web app is vulnerable to this, an attacker can potentially access restricted files that contain info about all registered users on the system, their permissions, and encrypted passwords.

The wildfires that spread across Northern California for two weeks in November were among the deadliest and most destructive in the state's history. Ultimately, the incident claimed 85 lives, and hundreds of people are still missing in the wake of the disaster, which impacted over 154,000 acres of land.