Hacking from a host machine without any form of proxying is reckless for a hacker, and in a penetration test, could lead to an important IP address becoming quickly blacklisted by the target. By routing all traffic over Tor and reducing the threat of malicious entrance and exit nodes with a VPN, we can configure Kali to become thoroughly private and anonymous.

Apple's iOS 11 is finally here, and while they showed off several of the new features it brings to your iPhone, iPad, and iPod touch back at WWDC 2017, they've only just touched the surface of what iOS 11 has to offer. There are a lot of cool new (and sometimes secret) features to explore, so we've collected them all here for you.

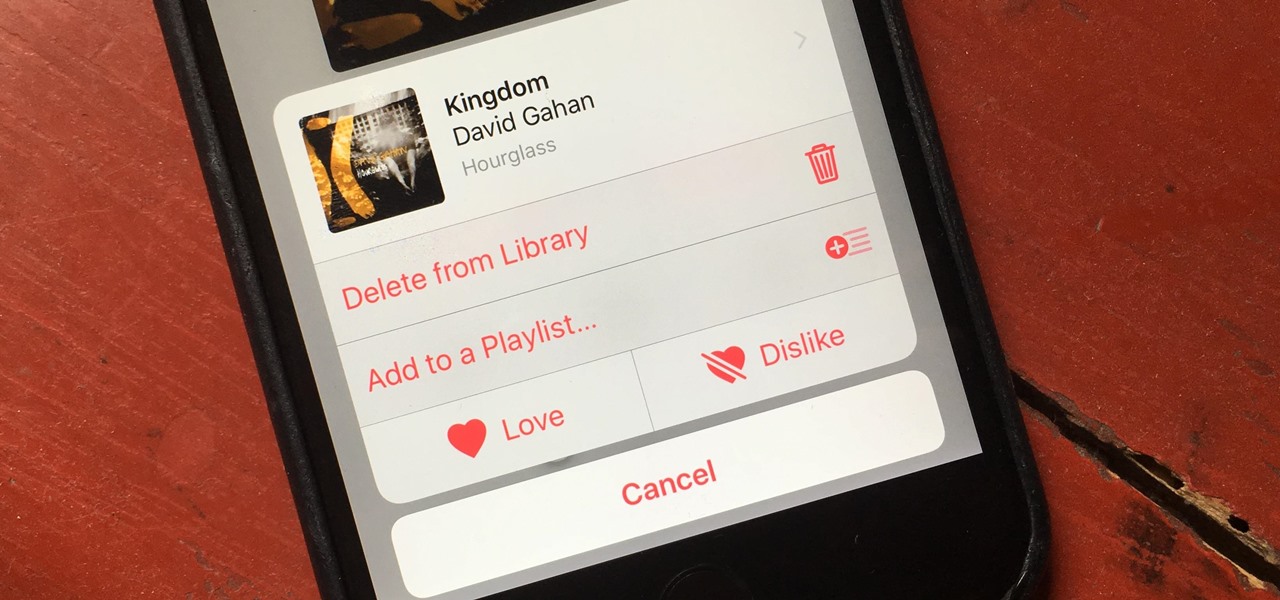
The pictures we upload online are something we tend to think of as self-expression, but these very images can carry code to steal our passwords and data. Profile pictures, avatars, and image galleries are used all over the internet. While all images carry digital picture data — and many also carry metadata regarding camera or photo edits — it's far less expected that an image might actually be hiding malicious code.

Aircraft equipped with ADS-B are constantly shouting their location into the radio void, along with other useful unauthenticated and unencrypted data. In this guide, we will make an ADS-B receiver using a Raspberry Pi with a software-defined radio (SDR) dongle, which we can use to track aircraft anywhere in real time.

In my previous article, we learned how to generate a vulnerable virtual machine using SecGen to safely and legally practice hacking. In this tutorial, we will put it all together, and learn how to actually hack our practice VM. This will provide some insight into the methodology behind an actual attack and demonstrate the proper way to practice on a VM.

Quanergy CEO and founder Louay Eldada is, by any standard of measure, a pioneer in the development of LiDARs for driverless vehicles.

In recent years, Apple has been pushing health and safety as cornerstones of its technology, and iOS 11 is no exception. Apple's latest entry in its mobile operating system brings a new emergency feature called Emergency SOS, which gives you easy access to contact 911 if you press the sleep/wake button five times. It's a useful way to contact emergency services when you might otherwise not be able to.

The Galaxy S8 has finally touched down, and it's an absolutely gorgeous device. Samsung's brand new flagship comes jam-packed with new features — some refined, and some that aren't. Luckily, we've compiled some major features to help you get started as quickly as possible so you can go about the rest of your day and show off your shiny new S8 to friends and coworkers.

It looks like Chris Urmson has spent the six months since he left Google's Self Driving Car Project trying to build a get-rich-quick self-driving unicorn, along with Sterling Anderson, formerly with Tesla Motors. At least that is one of several scandalous accusations in a Tesla lawsuit aimed at the pair, and their secretive startup Aurora Innovation, LLC.

All day I dream of eggs: scrambled, poached, over easy, hard-boiled, fried, baked, raw... Okay, the last one is a joke (unless you're Gaston, which means that you eat five dozen of them and you're roughly the size of a barge). But eggs are freaking good in just about any cooking prep, and more often than not are the foundation of your favorite baked goods.

Whether you're riding the subway on your way home from work, or stuck in the backseat of the car on a long road trip, there are times when you need to entertain yourself without a mobile data connection. A good mobile game would pass the time perfectly, but not every game works without an internet connection.

After enabling disk encryption, creating encrypted disk images, installing KeePassX and iTerm2, and using Git with local repositories, the next step to getting your Mac computer ready for hacking is setting up a package manager that can install and update open-source hacking tools. There are multiple options to choose from, but Homebrew has a slight advantage.

With some of the groundwork out of the way in getting a Mac set up for hacking, it's time to start looking at toolboxes. Our first toolbox is Git, which will be used throughout future tutorials.

There's a lot of great things to be excited about with iOS 10 on your device. You can remove annoying stock apps, search emails better, remember where you parked, and much, much more. Seriously, there's actually more outstanding features in iOS 10 than in Apple's latest iPhone 7 models.

Google Now, Siri, and Cortana aside, the main way you interact with your smartphone is through the keyboard. Every app you use, every search you perform, every message you send—the most fundamental interface between you and your device is that handful of characters and those 26 letters on the bottom half of your screen.

Hello people again, I wrote my last post about crypto about 10 months ago, now I will introduce something not fresh for the science, but fresh for the people who wants to learn. In my http://null-byte.wonderhowto.com/forum/cryptography-0161538/ post of crypto concepts, there is just basics, today we will see something that targets wide concepts like Symmetric crypto, Public Key Cryptography, Hashing, Keys etc...

Eating out is great, but being able to cook the delicious ethnic foods you eat at restaurants is even better. It may seem daunting to put together a bunch of ingredients with which you might not be familiar (some with names you've never even heard of!), but with the guidelines below, you'll be making your own versions of ethnic favorites in no time.

YouTube's massive user base comprises almost one third of all people on the internet, and collectively, users spend well over 100 million hours on the site watching billions of videos each day. Add it all up, and this means that YouTube is viewed by more people than any U.S. cable network—making it by far the favorite "TV station" of the internet generation.

Chrome apps and extensions are powerful tools for students: they can help optimize your web browsing experience by helping you take notes, check your grammar as you compose documents and emails, and even help you squeeze a little more juice out of your laptop's battery by freezing unused tabs and optimizing YouTube streams.

For people that like to get things done, Android's home screen widgets are almost indispensable. Rather than packing your launcher with a bunch of icons, you can utilize widgets to get quick information in a beautiful package or provide one-tap access to a particular functionality within your apps.

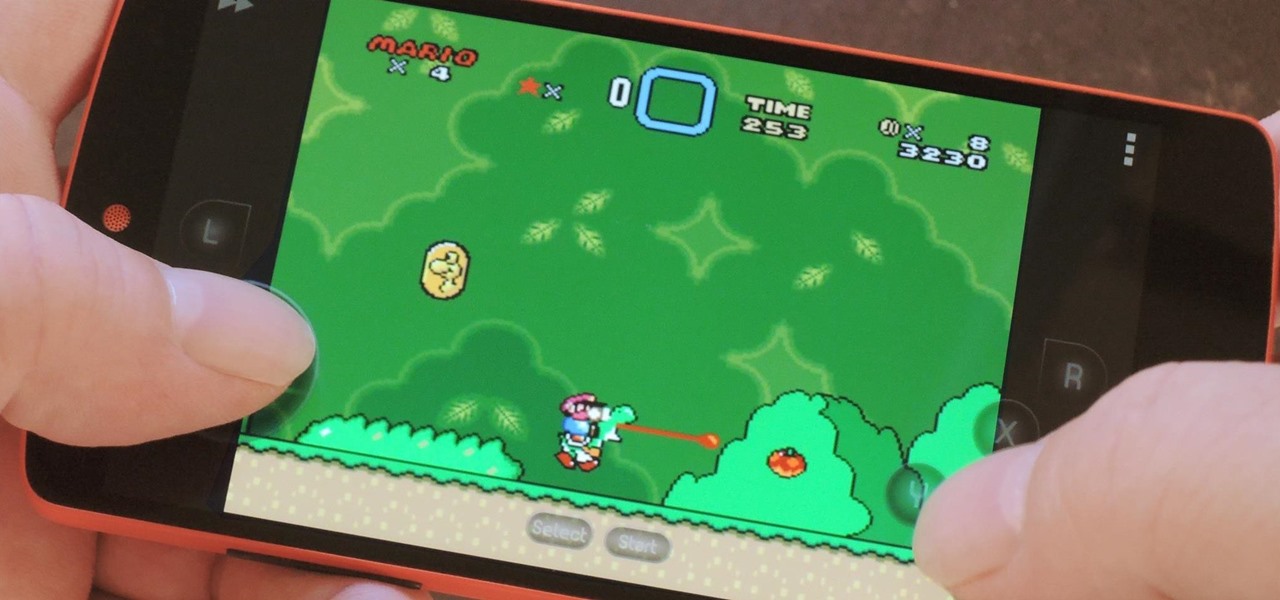
Smartphone games are getting pretty good these days, but they still can't beat the retro appeal of a good emulator. I mean, who wouldn't want to have their all-time favorite console and arcade games tucked neatly in their front pocket? Classics ranging from Super Mario Bros. to Pokémon can all be played at a silky-smooth frame rate on today's devices if you can just find a good emulator to run them on.
Welcome back Hackers\Newbies!

Stop! Do not pour that leftover wine, coffee, or bacon grease down the drain. And those herbs that have been in your fridge so long they've literally turned on you? And what about when that recipe only calls for two tablespoons of heavy cream, a quarter cup of tomato purée, or three cloves of garlic? Unless you plan on using the leftovers again in the next week or so, don't bother refrigerating them because they won't last.

These days, that pocket-sized computer we call a smartphone is home to your entire digital life. But with the onset of mobile payments and online banking, the line between your virtual world and the physical realm is becoming increasingly blurred.

Update (February 2019): The methods below will help on older Android versions, but we've recently revisited this topic. So if you have a newer Android phone and you want to get rid of Google, head here.

Welcome back, my tenderfoot hackers! As hackers, we often are required to get past antivirus (AV) software or other security measures. To do so effectively, we need to have some understanding of how AV software works. In this tutorial, we will take a cursory view of how AV software works so that you can better strategize on how to evade detection by it.

In recent years, Hollywood has taken a shine to hackers, with hackers appearing in almost every heist or mystery movie now. This can be both good and bad for our profession. As we know, whichever way Hollywood decides to depict our profession is how most people will perceive it.

You either love kimchi or you hate it, but for those of us who love it, its salty, briny, spicy crunch is the stuff of life. Honestly, if you're not eating it regularly, you should start, since it's being studied for an amazing list of health benefits, including anti-cancer, anti-aging, and antioxidant properties; obesity and high cholesterol prevention; and promotion of immunity and skin health. The beauty of kimchi is manifold:

It seems like every day now that we see a new headline on a cyber security breach. These headlines usually involve millions of records being stolen from some large financial institution or retailer. What doesn't reach the headlines are the many individual breaches that happen millions of times a day, all over the world.

Staying healthy is a progressive challenge we all face throughout our lives, and figuring out just how to do that can be a challenge when it's not your job. For doctors, however, it is. Here's how they keep themselves healthy day to day.

Each day, we read about another security breach somewhere in our digital world. It has become so commonplace that we hardly react anymore. Target, J.P. Morgan, iCloud, Home Depot, and the list goes on and on.

Go to a chain supermarket, and chances are you'll see one type of garlic—maybe two or three if you're lucky. However, there's a mouthwatering slew of Allium sativum out there, far beyond those papery white bulbs most of us encounter at the nearest Stop 'n' Shop.

People who know that I am a professional hacker often ask me what they can do to make their computers and personal information safe from people like me. The answer, of course, is that nothing will make you completely safe, but there are a number of measures any computer user can take to reduce the chances of being a victim of a hacker.

The paper towel is a wondrous invention. It allows cooks to wipe up really gross stuff without having to constantly do laundry and drain fried foods so they're crunchy and crispy instead of oily and heavy. But did you know that your humble paper towel has several other uses besides the obvious ones? Read on to find out these essential hacks.

Just the fact that you own an Android device means you're privy to an entire world of third-party development. Many of the mods you'll see here on Gadget Hacks can be performed fresh out of the box, but with root and Xposed, the list grows longer. But to truly be able to take advantage of all that Android's massive development community has to offer, you'll need to have a custom recovery installed.

There's a 2800mAh battery powering the Samsung Galaxy S5, but even it's no match for the constant day-to-day torture you put it through. Taking photos, watching videos, and playing games can make your fully charged S5 powerless in no time.

Hard-boiled (also known as hard-cooked) eggs are notoriously easy to mess up. We've all ended up with tough, rubbery egg whites and overcooked yolks that have that unappetizing gray-green ring around the edge. An ideal hard-cooked egg has a firm yet tender white, while the yolk is creamy and well-done without being mealy.

I am writing this to first pregnant moms. I am 25 weeks along and I have some advice as to getting through an uncomfortable pregnancy.

There's a lot of cool features rumored to be included in next year's HTC One 2 (M8), the follow up to the flagship HTC One smartphone, including a fingerprint scanner, Android 4.4 KitKat, and Sense 6.0, but it's just too far away to get really excited about yet.

There are definitely some great things about iOS 7, but like any good piece of software, it's got some things to kink out—and how wallpapers work seems to be one of the biggest issues, since it's so much different than in previous iOS versions.