Emoji characters give you a multitude of colorful characters to express yourself with on social media and within messages, and stickers give you even more symbols to play with. While Android and iOS both have a healthy arsenal of emoji and stickers, Android goes a step further for even more emoji madness.
By default, everyone on WhatsApp can see when you're using the app. If someone recently messaged you and sees you're currently online, they may think you're avoiding them if you don't respond right away — especially if you don't share read receipts. However, you can block them from seeing your online or last seen status and apply it to everyone or just specific contacts.

One of the best recent outings in the Marvel universe is the animated series What If...?, which explores alternate universe takes on various superhero storylines that deliver fascinating scenarios if one single factor had been different in the story.
Apple's iOS 14.5 overhauled the Podcasts app, combining new aesthetics with smart and efficient features. While you might find the app better at playing your favorite podcasts than past versions, you might also find something negative about the update on your iPhone: it may be eating up your storage.

The rapid advance of Lens Studio as a platform for easily developing augmented reality experiences is just one indicator that immersive computing is becoming the norm.

For some, one of the coolest new features in iOS 14 is the Picture in Picture mode, which had previously only been available on the iPad. With it, you can continue watching a video from an app in an interactive floating overlay window on the home screen or within other apps. But for others, it can be annoying when it appears unexpectedly all of the time, and there's a way to stop it.

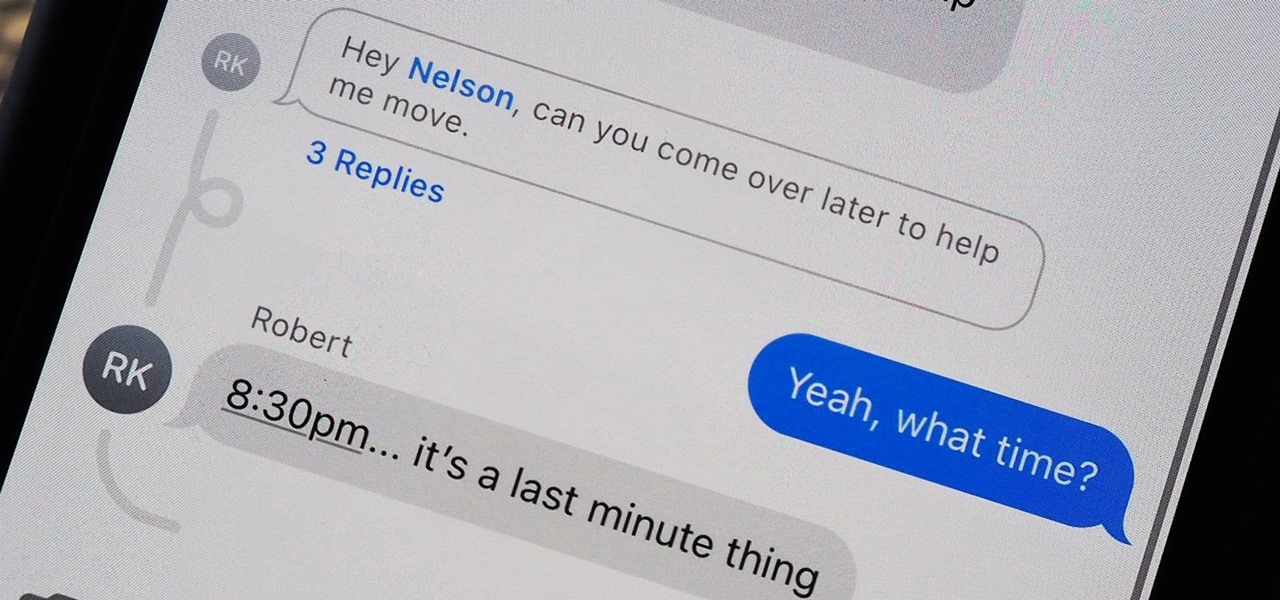
A group conversation can be a chaotic place. Even with a small number of people, you still may get more messages than you can keep track of on your iPhone. What makes it even worse is trying to sort through all of the conversations within conversations. Apple, however, wants to make things easier on all of us, which is why iOS 14 allows you to respond to specific iMessages using inline replies.

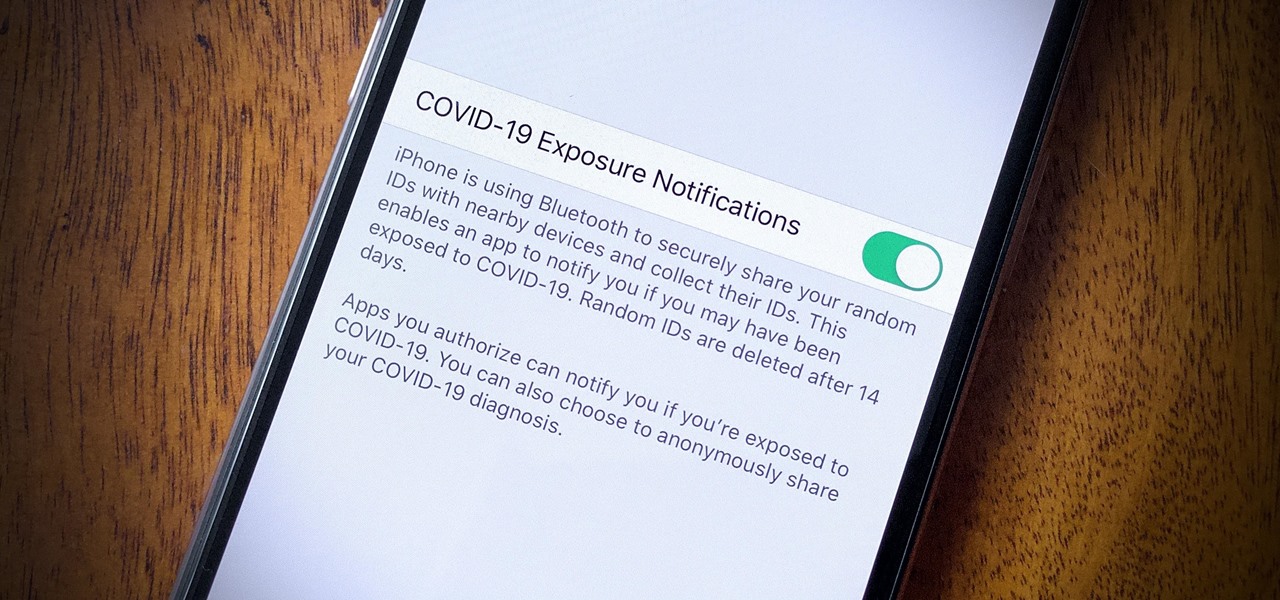
In iOS 13.5 and later, developers can create and release contact tracing apps for iPhone, which could help slow the spread of the novel coronavirus in the U.S. With these apps comes COVID-19 exposure notifications, which you may or may not want to receive. If you don't want to get these alerts, you can disable them.

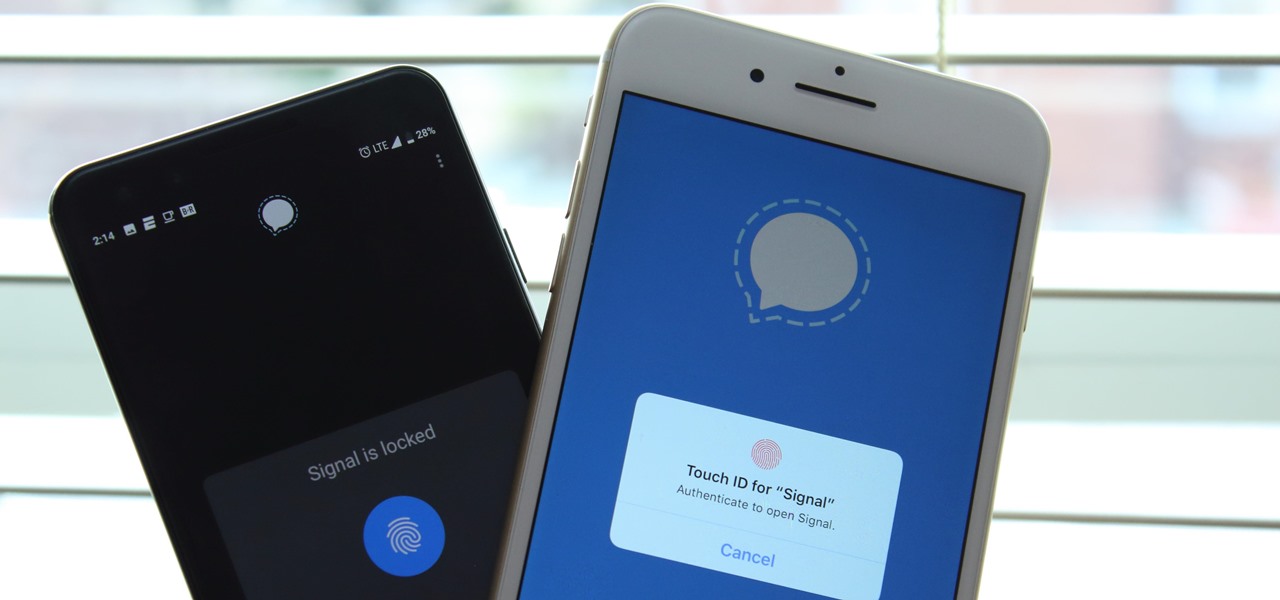
Signal is one of the best end-to-end encrypted messengers on the market. It offers robust security, keeps minimal information about its users, and is free to use. Switching to it as your main messenger can be a bit daunting, so to help, we created a guide to walk you through the process.

Mystery is a tricky thing. Used correctly, it can give onlookers the impression that wondrous and perhaps valuable things are afoot. However, once the veil of suspension of disbelief is removed in any significant way, that same mystery can quickly turn into not just skepticism, but outright anger at what may have seemed like an attempt to dupe trusting onlookers.

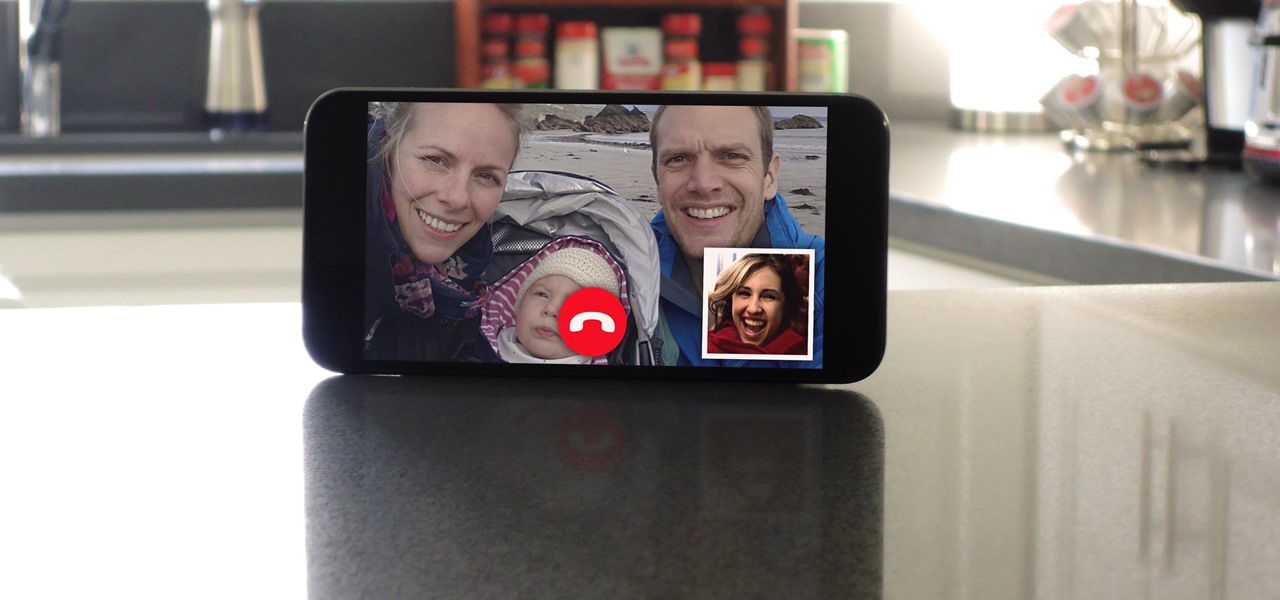
You know your infant is advanced. Maybe you want to give her or him a head start at learning things like writing code to develop the next big Fortnite game. Or maybe you just want to play Fortnite with your infant. But the American Academy of Pediatrics discourages screen time for kids under than 18 months, with just one exception: video chat.

If you're on the hunt for a profitable side-gig, or even a completely new way to to make money, you'll want to take a look at Upwork, a leading freelancing platform that connects skilled freelancers with clients from all over the world.

As we enter the second half of 2018, rumors for the second season of flagships have started to emerge. On the Android side, this means the latest iterations of the Google Pixel, Galaxy Note, LG V series, and Huawei Mate. Thanks to FunkyHuawei and XDA, we now have some solid rumors regarding the Huawei Mate 20.

Analysis of photographs and social connections can be a huge component of social engineering. Understanding who a person is, as well as who they know, can establish links within a company. This information could be used by hackers to execute elaborate social engineering attacks.

Conducting phishing campaigns and hosting Metasploit sessions from a trusted VPS is important to any professional security researcher, pentester, or white hat hacker. However, the options are quite limited since most providers have zero-tolerance policies for any kind of hacking, good or bad. After researching dozens of products, we came out with 5 potentials that are ideal for Null Byte readers.

The war on dehydration is a commercially burgeoning marketplace. An increasingly sophisticated consumer population hoping to conquer everything from 26-mile marathons to vodka shots is deconstructing every functional remedy in the fight to quell the effects of severe dehydration.

Coinhive, a JavaScript cryptocurrency miner, was reportedly discovered on the BlackBerry Mobile website. It was placed there by hackers who exploited a vulnerability in the site's e-commerce software that allowed them to anonymously mine cryptocurrency every time the website was viewed. There's no doubt Coinhive, an innovative mining method, is being abused and exploited by hackers in the wild.

The mysterious technology product teased via an eccentric TED Talk nearly five years ago has finally been revealed, and it's called the Magic Leap One: Creator Edition. After all of the non-disclosure agreements, furtive comments from CEOs and insiders given early access to the device, and a seemingly never-ending string of hints dropped by the company's CEO, Rony Abovitz, on Twitter, we finally have a real look at the product.

Video chatting has become an important factor in the overall smartphone experience. Even just a few years ago, 37% of teens were making video calls on a regular basis, and that number has surely grown. 85% of households with infants have used video chat apps to call relatives in other cities, and it's been shown that toddlers can create bonds and learn from visual cues in video calls.

Now that smartphones have ensured that we're connected to the internet 24/7, online privacy has become more important than ever. With data-mining apps hoping to sell your information for targeted ads, and government agencies only one subpoena away from knowing every detail of your private life, encryption has become our last line of defense.

Hi, everyone! Recently, I've been working on a pretty interesting and foolish project I had in mind, and here I'm bringing to all of you my findings. This guide's main aim is to document the process of building an Android kernel, specifically a CyanogenMod kernel and ROM, and modifying the kernel configuration to add special features, in this case, wireless adapter Alfa AWUS036H support, one of the most famous among Null Byters.

Things just got a lot better in your iPhone's Messages app, and the most significant change lets you text Android users with iMessage-like features such as typing indicators, read receipts, large file sharing, high-quality photos and videos, and even emoji reactions.

The last iOS software update was a modest one, but iOS 17.4 has a lot more for your iPhone, including changes to emoji, Podcasts, security, Safari, widgets, Apple Cash, CarPlay, and more.

The recent announcement that Facebook will begin inserting advertisements into its VR experience on its Oculus Quest headset has set the VR and augmented reality industry into a frenzy.

The tech world was taken by surprise this week with the unexpected unveiling of Snap's augmented reality Spectacles smartglasses.

A lot of digital ink has been spilled heaping scorn on Magic Leap. Much of that media schadenfreude was due to what some believed were unmet promises versus some of the early hype around the product. Others just seemed to be rubbed the wrong way by the startup's Apple-esque secrecy and penchant for attempting to coin new terms and frameworks for things that were, mostly, already in play.

There are a lot of cool shortcuts you could run on your iPhone, but in iOS 13 and iOS 14, you'll likely see a notification any time you try to run an automation. Shortcuts should feel seamless when their actions are performed, and getting a banner alert each time one initializes takes away the seamlessness of it all. But there is a way to block them.

The "Zoombombing" trend is still strong on the Zoom video meetings service, despite security measures Zoom put in place to stop it. That's why it's up to you, as either a host or co-host, to be proactive about preventing Zoombomber harassment, as well as stopping it whenever it slips through the cracks.

It's pretty much a given at this point that Facebook has a lot of data on us. While you might be conscious of the data you share with Facebook when you post, upload photos, or chat with friends on Messenger, you might not be thinking about all the data it receives from websites and apps you use outside the social media giant. Now, you can actually do something about it.

While hackers know and love the Raspberry Pi, many don't know of its cheaper cousin, the microcontroller. Unlike a Pi, which can be used more or less like a regular computer, microcontrollers like the Wi-Fi connected ESP8266 require some necessary programming skill to master. In this guide, we'll build an Arduino program from scratch and explain the code structure in a way anyone can understand.

In just a few weeks, on May 29, the annual AWE (Augmented World Expo) conference will take place once again in Silicon Valley (Santa Clara, California, to be exact).

Twitter's official iOS app is adequate if you're not much of a tweeter, but if you are, there's a lot of useful features that are missing. Luckily, there are plenty of free Twitter clients available that you can use on your iPhone. These third-party apps have features such as customizable interfaces, post scheduling, and different browser options for opening links, to name just a few.

You can mod every aspect of your phone's software with root, but if you want to make changes at the hardware level, you'll need a custom kernel. If you've looked into custom kernels before, one name undoubtedly kept coming up: ElementalX. It's easily the best custom kernel out there, and the reason for that is its awesome developer, flar2, aka Aaron Segaert.

Unlike VR, when you're talking about augmented reality, describing what an experience is like can be incredibly difficult — primarily because the experiences are even more contextual than relatively static virtual worlds that don't involve real-world settings.

Your childhood "social networking" may have been to go outdoors to the neighbor's — and outdoors is a great place for kids to be. But these days, the terms educational, digital media, entertainment, and toddlers don't have to be mutually exclusive. Like most things in life, it's about balance, and these apps can aid your child with social-emotional development when not playing with friends.

Performance and stability improvements, as well as new features, are just some reasons to install iOS 12, but new changes mean new battery health challenges. It can be difficult to boost battery life while taking advantage of everything this update has to offer. Luckily, there are plenty of ways to avoid unnecessary battery drain when using iOS 12 on your iPhone.

Around this time in 2016, the predictions for the next year had reached something of a consensus: 2017 would be the year of augmented reality. But a funny thing happened on the way to the future — nothing much, really. At least not for the first half of the year.

The one thing that separates a script kiddy from a legitimate hacker or security professional is the ability to program. Script kiddies use other people's tools, while hackers and security pros write their own tools. To that end, we're going to see how a stack overflow vulnerability allows us to flood a variable with enough input to overwrite the instruction pointer with our own commands.

One of the most popular usages of modern-day smartphones is listening to music. It doesn't matter if you download or stream your tunes, you are part of a massive group of users who do exactly the same. While statistics are a bit foggy on how many smartphones users download music, we do know that over 68% of American smartphone owners stream music on a daily basis.

While music may not technically be a "universe language," it is the one language listened to by all. There are over 1,500 music genres today—rap, classical, rock, jazz, trap, hip-hop, house, new wave, vaperwave, charred death, nintendocore... and the list goes on. And if you're like most people, you now probably listen to the majority of your music on your phone.