Your email inbox is a treasure trove of personal data. The people you contact, your writing style, which messages you flag as spam — all of this information and more can be used to paint a clear picture of you. Google knows this as well as anybody, so they use this data to constantly improve your experience in Gmail.

Screenshots taken from a compromised computer can provide hackers with access to private emails, photographs, and information found in sensitive documents. This data can be used by the attackers to build profiles of a target for social engineering attacks and blackmail or even just to release the information out in the wild.
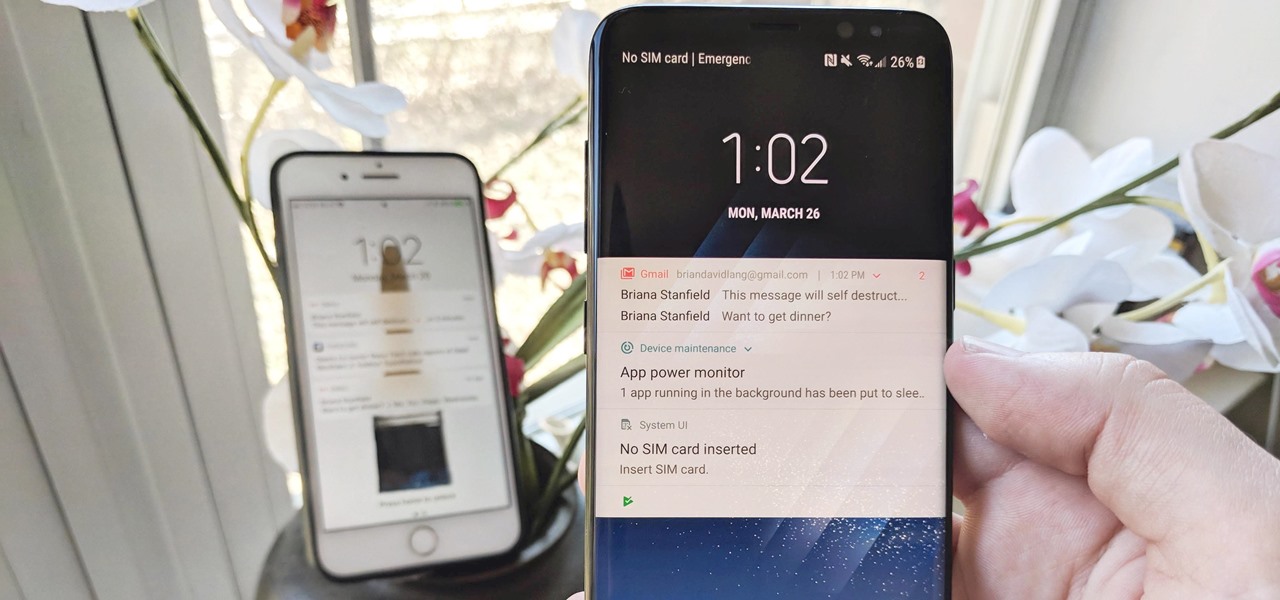
The iPhone vs. Android debate is almost as old as smartphones themselves. While there are a number of reasons to skew towards one operating system or the other, the Samsung Galaxy S9 models have a ton of great features that help set them apart from Apple's iPhones. The coolest feature, in my opinion, is the way notifications are handled.
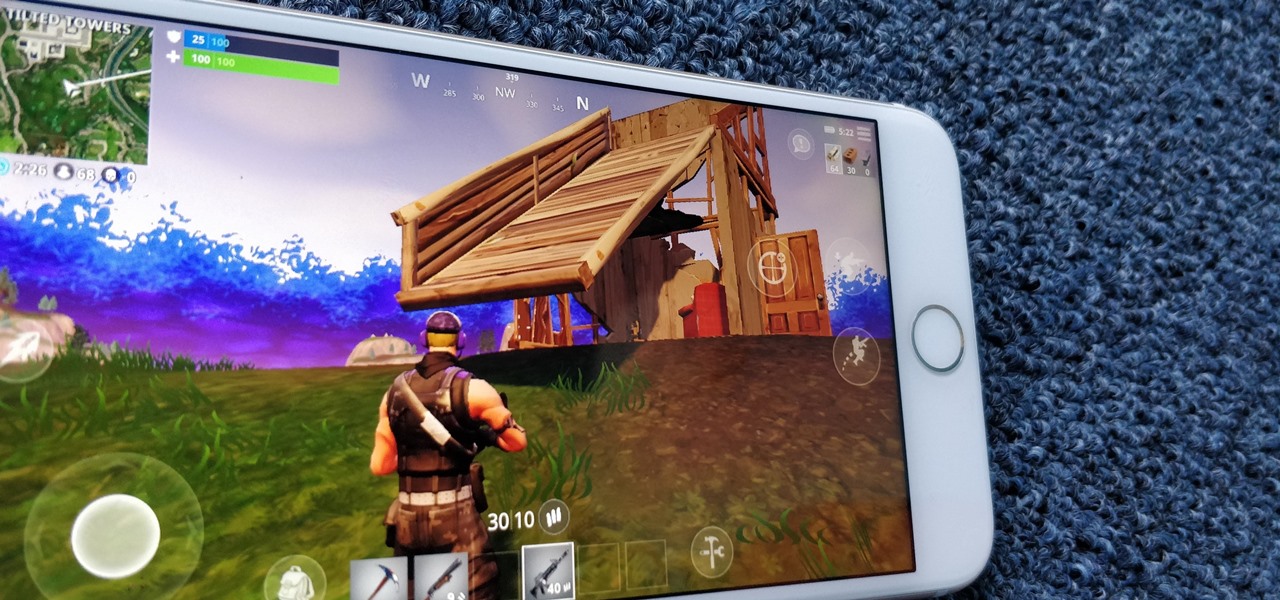
With ultra competitive games like Fortnite Battle Royale and PUBG taking the mobile world by storm, gamers are looking for ways to get a leg up on the competition. One of the biggest advantages you can give yourself is the ability to aim and shoot while on the move, but that's not exactly easy with a touchscreen.

After more than a year and a half of silence, the rumors have morphed into reality: Microsoft has finally released an update for the HoloLens. And with that update comes a collection of new features that hint at big plans for the HoloLens this year.

A powered-off Windows 10 laptop can be compromised in less than three minutes. With just a few keystrokes, it's possible for a hacker to remove all antivirus software, create a backdoor, and capture webcam images and passwords, among other highly sensitive personal data.

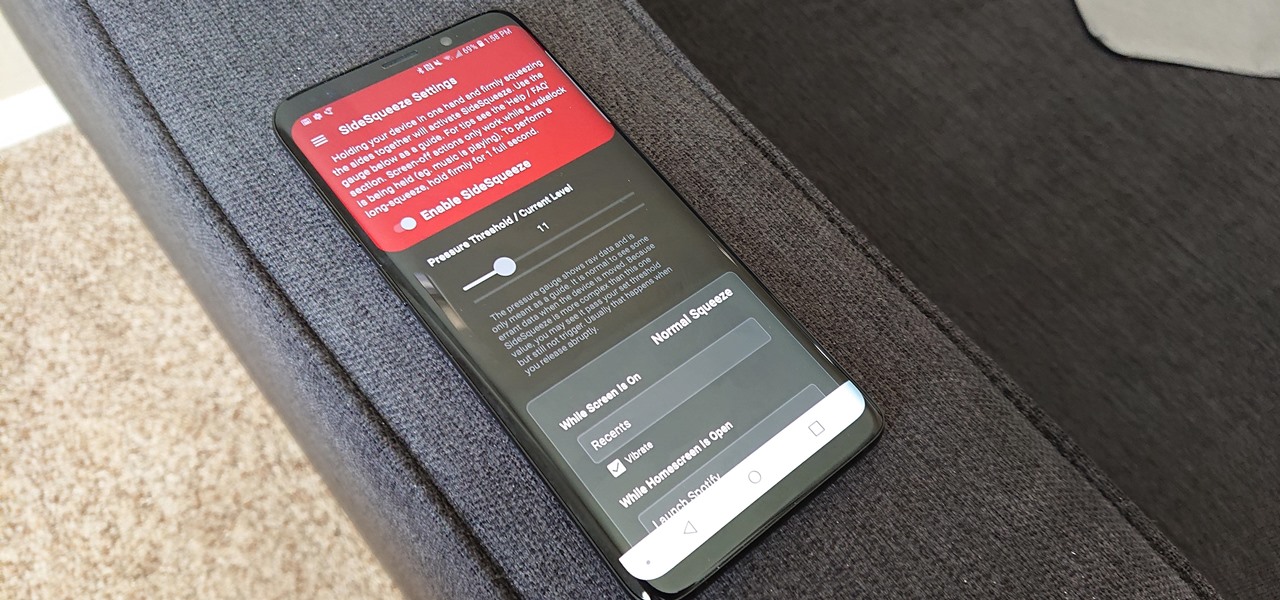
All the Android fans out there undoubtedly remember the squeeze gestures introduced with the HTC U11. Google continued the trend by bringing the gestures to the Pixel 2 and Pixel 2 XL. Thanks to a brand new app, you can now enable similar squeeze actions on your Galaxy S9 or S9+, and even some older Samsung phones.

Update February 25: The Nokia 9 PureView was announced at Mobile World Congress! Read all of the official specs and details at our full rundown of Nokia's latest flagship.

One of the more unique aspects of Fortnite Battle Royale is the ability to create structures. Using in-game materials, players can create walls and ramps for cover and to extend mobility. But creating isn't limited to just the basic generic structures. To really maximize their benefits, great players edit their creations to fit their needs.

In mid-2017, Instagram added the ability to archive posts you've previously shared so that only you could see them going forward. As easy as it is to archive one of your Instagram photos or videos, it can be just as easy to forget how to unarchive it so others can see it again in all its glory.

After setting up your phone, there are a number of things you should do immediately before download your favorite apps. Specifically, now that your data is on the device, you need to take steps now to ensure it's both protected and retained. Fortunately, most of these steps are a one-time process.

Continuing our series on building a dynamic user interface for the HoloLens, this guide will show how to rotate the objects that we already created and moved and scaled in previous lessons.

When you don't want somebody you're calling to know the real phone number associated with your iPhone, whether it's for privacy reasons, to avoid being called back, or to prevent being ignored, there are multiple things you can do to block it on their caller ID.

As with most social media platforms, Instagram can be a double-edged sword. On one hand, it's a great way to share and express yourself — but on the other, it can be just as effective at compromising your privacy. Thankfully, there are a few things you can do to protect yourself.

As the third-largest smartphone manufacturer in the world, Apple devices are a constant target for hackers everywhere. While iOS has seen fewer common vulnerabilities and exploits (CVEs) in recent years, iPhones still aren't hack-proof. Fortunately, you can strengthen your security with the help of a few apps.

Your home has walls for privacy, but Wi-Fi signals passing through them and can be detected up to a mile away with a directional Wi-Fi antenna and a direct line of sight. An amazing amount of information can be learned from this data, including when residents come and go, the manufacturer of all nearby wireless devices, and what on the network is in use at any given time.

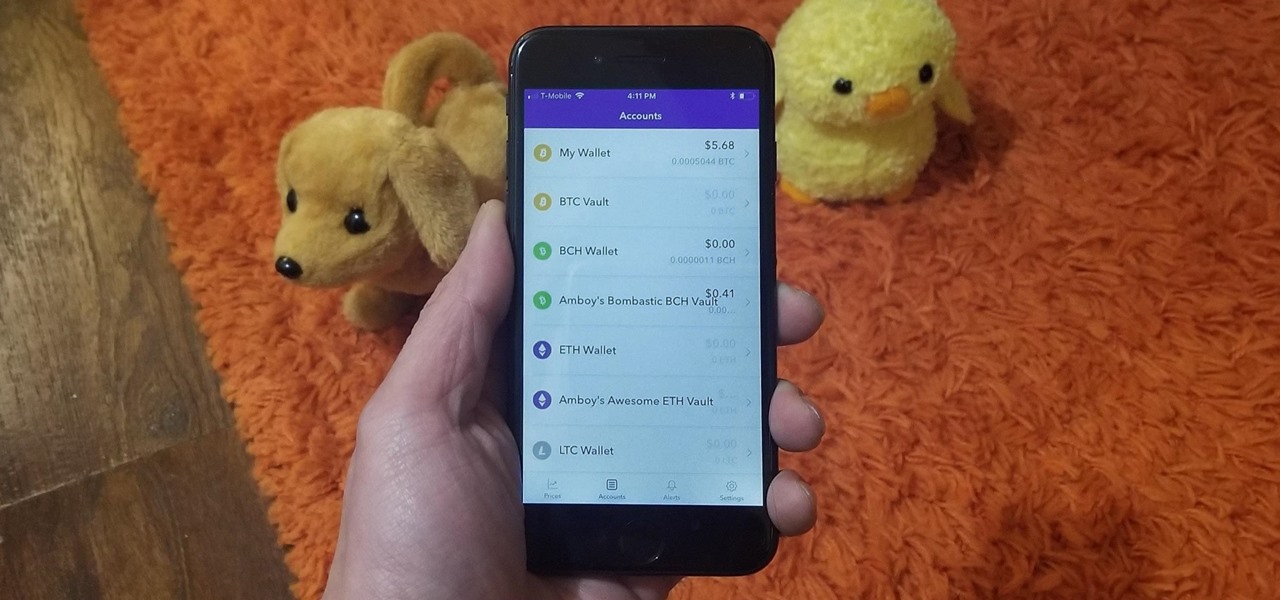
As cheesy as it sounds, #HODL became a thing for a reason. A lack of discipline when dealing with cryptocurrencies can lead to impulse buys and panic selling, and ultimately, depleted funds. Luckily, Coinbase has a way to safeguard your cryptocurrency savings to not only protect them against thieves, but to also help you resist the urge to sell off your investments.

Nmap is possibly the most widely used security scanner of its kind, in part because of its appearances in films such as The Matrix Reloaded and Live Free or Die Hard. Still, most of Nmap's best features are under-appreciated by hackers and pentesters, one of which will improve one's abilities to quickly identify exploits and vulnerabilities when scanning servers.

Many people think antivirus apps are useless — why pay a subscription fee when most malware can be avoided with common sense? But the thing is, there were an estimated 3.5 million malicious Android apps discovered last year, with many of them making their way onto the Play Store. As this number continues to rise, can you truly depend on common sense to protect you?

For years, PuTTy has reigned supreme as the way to establish a Secure Shell (SSH) connection. However, those days are numbered with the addition of the OpenSSH server and client in the Windows 10 Fall Creators Update, which brings Windows up to par with macOS and Linux's ability to use SSH natively.

If you're a regular reader of Next Reality, you're more likely to spread the joy of augmented reality than most others. But it can be difficult to introduce newbies into the AR fold if you don't give them exactly the right starting point in terms ease-of-use and affordability. But fear not, oh gift-giving AR pioneer, we're here to help!

Proxies can be quicker to use than a VPN for specific applications, like web browsers or torrent clients. Both services will hide your true IP address, but a VPN is slowed down because it encrypts all data through a VPN network, while a proxy just acts as a middleman for fetching and returning requests from a server on your behalf. When speed is needed, go proxy.

This is a very exciting time for mixed reality developers and fans alike. In 2017, we have seen a constant stream of new hardware and software releases hitting the virtual shelves. And while most of them have been in the form of developer kits, they bring with them hope and the potential promise of amazing things in the future.

This year, two new OEMs are trying to enter the crowded smartphone space. The first was Essential, and now Razer has entered the market with the Razer Phone. Utilizing the team they acquired from Nextbit in January, Razer has created a powerhouse of a device designed for gamers. Coincidentally, Razer announced their new device a day before Apple's biggest revision to the iPhone was released.

Samsung has finally rolled out the Android Oreo update for the Galaxy S8 and S8+. If you're just now getting the update, you'll be happy to know that your Galaxy just got upgraded with plenty of cool new features. Like previous updates, Samsung has improved upon its software by including a new look and new functionality.

Razer just made a big step into the mobile industry by releasing an absolute beast of a smartphone. The gaming-centric Razer Phone tries to provide the best experience for its target audience: Gamers. With that in mind, they created a top-tier device with some of the best specs available on Android. But how does it compare to the current spec champion, the Samsung Galaxy Note 8?

Karen Gillan must have had an absolute blast chewing the scenery as Nebula in Guardians of the Galaxy Vol. 2, seeing as how Nebula is a ball of pure, seething fury pretty much 24/7. Combine that larger-than-life personality with her iconic blue and silver cyborg look, and you have a guaranteed hit for cosplay or Halloween.

With the recent launch of the LG V30 and the Pixel 2 XL, LG has reintroduced the world to POLED. This display tech was showcased at CES 2015 and billed as a rival to Samsung's AMOLED displays, then promptly disappeared from the market for two years. But now that two of the biggest flagship phones this year are using the technology, many folks will be wondering what makes POLED different.

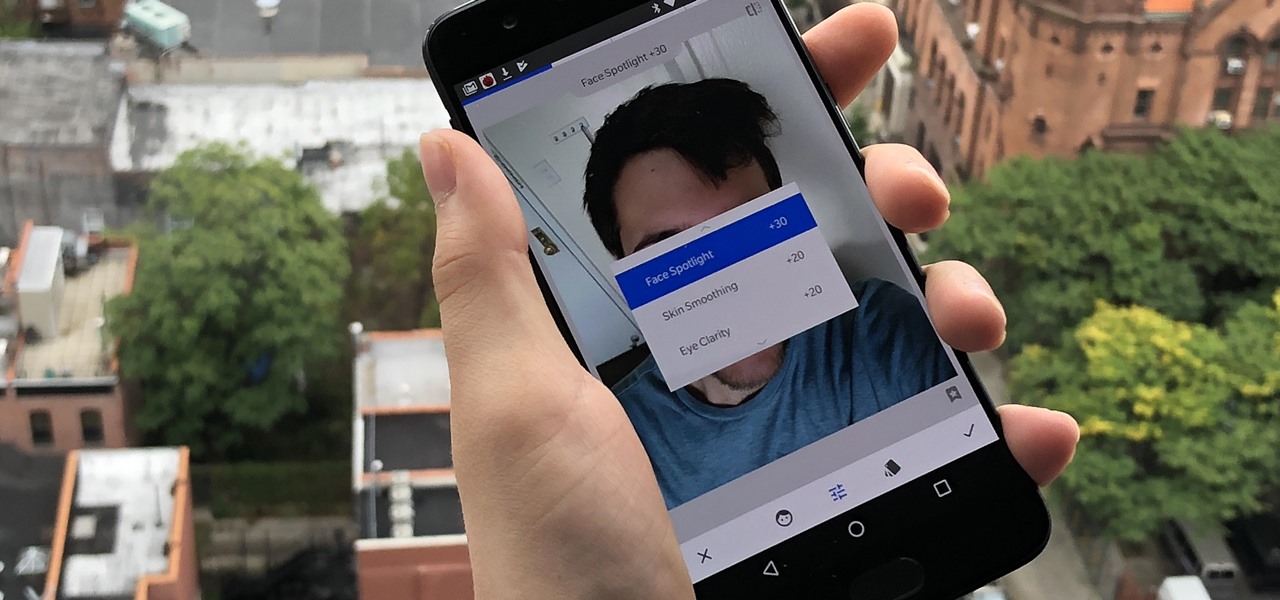
Google's Snapseed app has a plethora of editing tools to help make your photos even better. But did you know it has specific tools designed to edit your face? Not that it needs any help, of course!

Every other year, Apple comes out with "S" model iPhones that enhance and speed up their main series models from the previous year. This year, however, because of the highly-anticipated 10th anniversary iPhone, aka the iPhone X, Apple has dropped the "S" and moved straight to the iPhone 8 and 8 Plus.

Andre was enjoying the carefree life of a 12-year-old with his friends, riding his bike and playing sports, like all kids that age. Schoolwork wasn't hard for him, and his grades showed that.

A remote administration tool, or RAT, is a piece of software used for remotely controlling machines. They are commonly used by tech support to gain remote access for troubleshooting purposes, but RATs are also an important part of a hacker's advanced persistent threat (APT) toolkit. Unlike standard administration RATs, these tools are designed to be delivered stealthily and operate undetected.

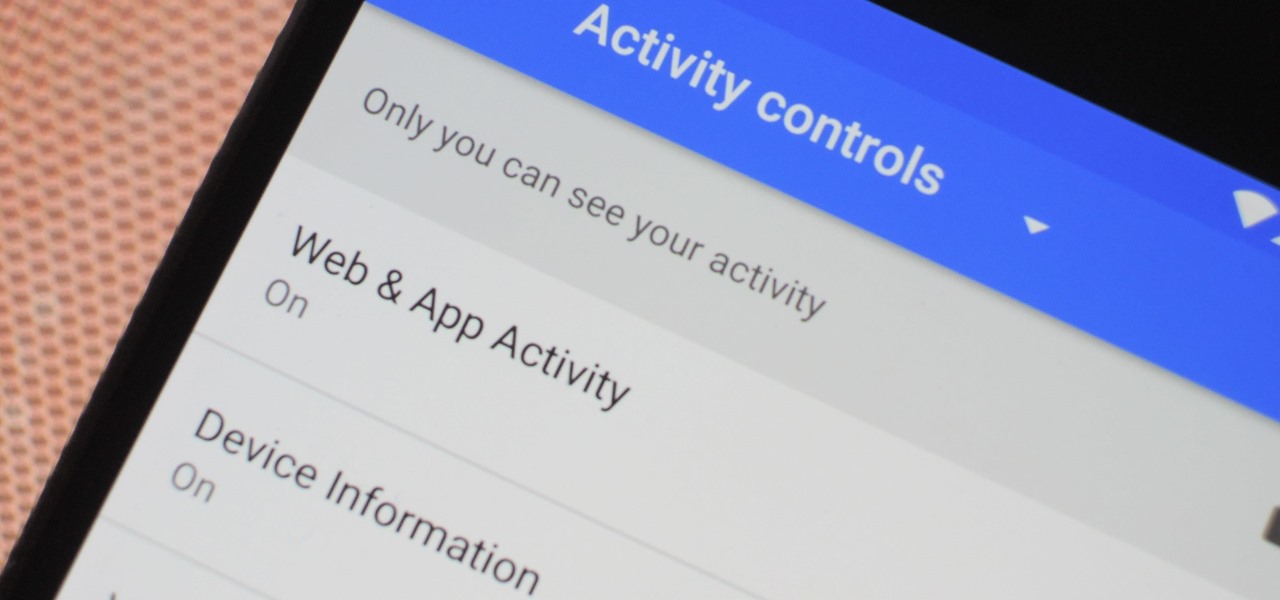
The Google Assistant is an incredibly useful tool that's now available for both Android and iOS. You can use plain English to send voice commands that range from turning off your smart lights to answering almost any question — but many of these features won't work properly if you have certain Google activity controls disabled.

Young girls, especially those who live in areas where HIV is epidemic, like sub-Saharan Africa, are particularly vulnerable to becoming infected with HIV. A vaginal ring containing the antiviral agent dapivirine has been shown to decrease the chance of developing HIV-1 in adult women over 21 and now in the first step for use in adolescents, the ring has been shown to be safe and well-tolerated in that younger age group.

Mobile augmented reality developer Blippar has updated its mobile app for iOS and Android with an augmented reality face profiles feature based on the company's real-time facial recognition engine.

The Operative Framework is a powerful Python-based open-source intelligence (OSINT) tool that can be used to find domains registered by the same email address, as well as many other investigative functions. This reconnaissance tool provides insight about your target through examining relationships in the domains they own.

Tell the truth. The bat picture creeps you out. You are not alone. But in reality, bats truly are some of our best friends. They gobble thousands of disease-spreading bugs a night. But they also carry viruses that can be deadly to humans. So, bats — friend or foe?

Apple's been hard at work adding new features and finishing touches to iOS 11, and there's evidence of it everywhere. But there's one place where these changes are more noticeable than perhaps anywhere else — Safari.

In our first part on software-defined radio and signals intelligence, we learned how to set up a radio listening station to find and decode hidden radio signals — just like the hackers who triggered the emergency siren system in Dallas, Texas, probably did. Now that we can hear in the radio spectrum, it's time to explore the possibilities of broadcasting in a radio-connected world.

On April 7, 2017, residents in Dallas, Texas, woke to the sound of emergency sirens blaring all over the city. No one could shut them off, and after repeated efforts to contain the situation, the city had to shut down the entire system. While the media reported a sophisticated computer hack was responsible, the truth was much less high-tech.