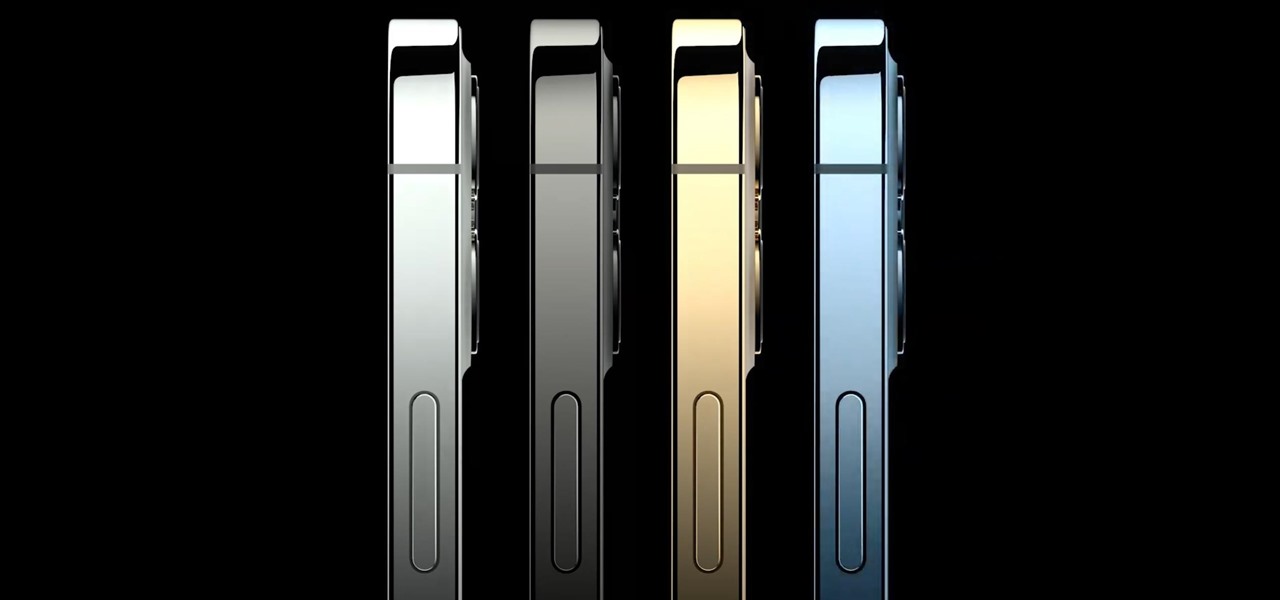
For the first time, Apple has announced four new iPhone models at the same time. At the Oct. 13 web-only event, Apple revealed the iPhone 12, iPhone 12 mini, iPhone 12 Pro, and iPhone 12 Pro Max. This year, it made a phone for everyone. But when can you get your hands on one of these 2020 models?

Nearly every native app on the iPhone received an upgrade or new features in iOS 14 — and Safari is no exception. The web browser now has better password protection, faster performance, privacy reports, and built-in translations, just to name a few. Some of the Safari updates went unnoticed by many, but they're there and ready to use in iOS 14.
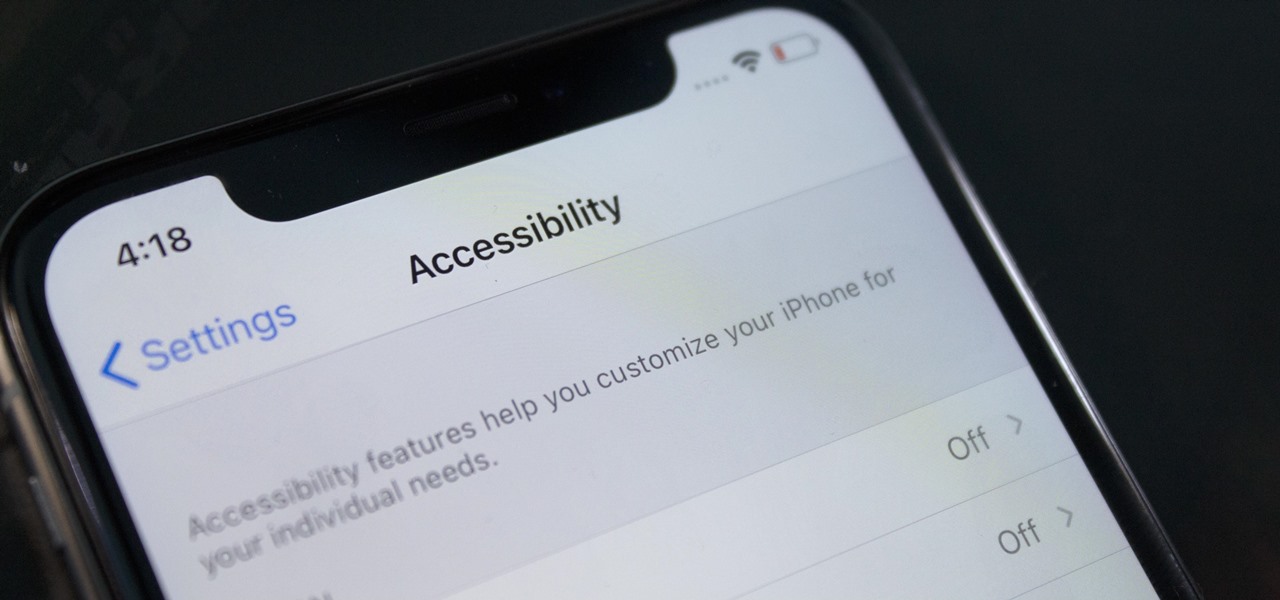
According to the CDC, one in four U.S. adults has a disability, where limitations can involve vision, cognitive function, hearing, motor skills, and more. That's why the iPhone has accessibility features; so that everyone can use an iPhone, not just those without any impairments. Apple's iOS 14 has only made the iPhone even more accessible, and the new tools benefit everyone, not just those that need them.
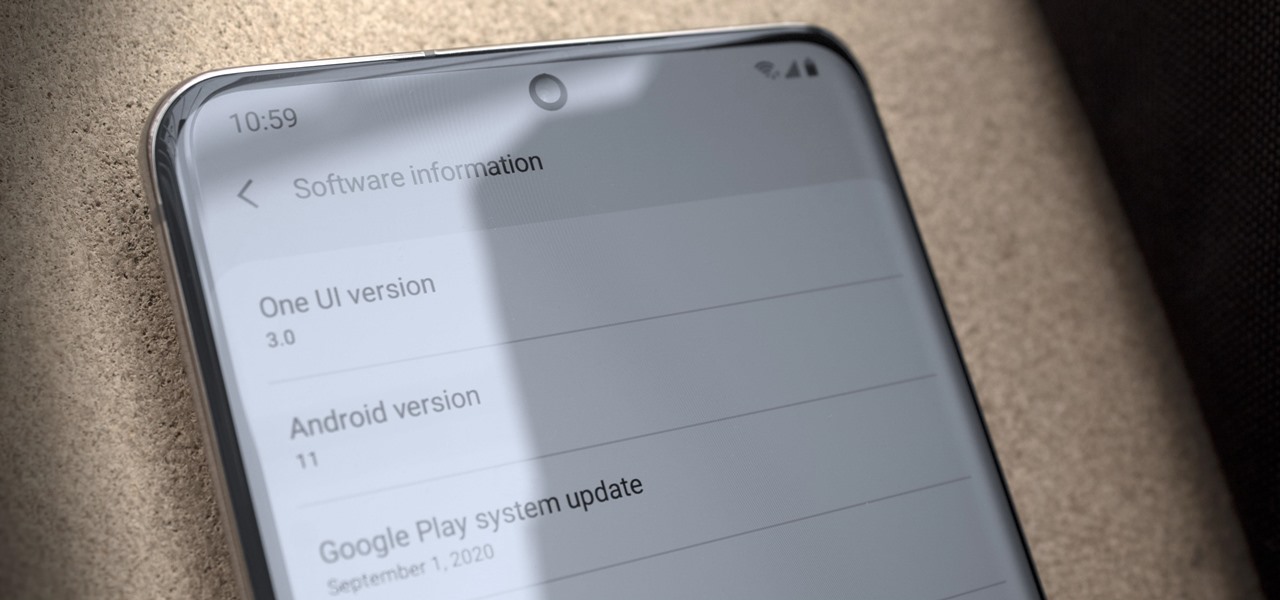
Just days after Google released the official Android 11 update, Samsung already had a pre-beta build of One UI 3.0 available for developers to test their apps on. So this year's main OS upgrade is likely hitting Galaxy phones even earlier than we thought.
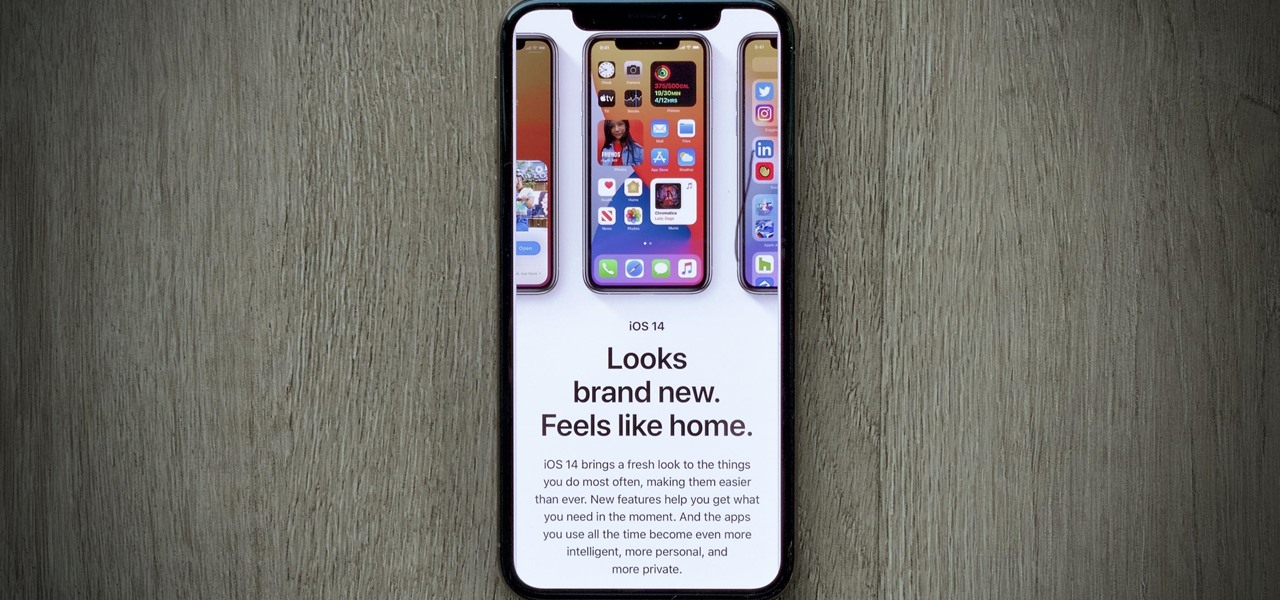
Apple's iOS 14 is here. With it, you'll see over 200 new features and changes hit your iPhone, including home screen widgets, inline replies in Messages, and cycling routes in Maps. Here's how you can get your hands on the brand new update.

The new iOS 14 for iPhone arrived Wednesday, Sept. 15, 2020, alongside iPadOS 14, and there are a lot of features to uncover. Improved widgets. Better home screen customization. Exciting Messages improvements. New abilities in Camera and Photos. There's so much here that it'll take months for you to learn everything by heart.

Apple just seeded developers and public beta testers the GM (golden master) for iOS 14 on Tuesday, Sept 15. The update (18A373) comes just after Apple's "Time Flies" event, and six days after Apple released iOS 14 beta 8 for both developers and public testers.

If you've ever been into custom ROMs, you likely know the Dirty Unicorns name pretty well. It's been synonymous with unique features and awesome tweaks when compared to stock. Recently, Dirty Unicorns has returned again in a big way with some neat features for Android 10.

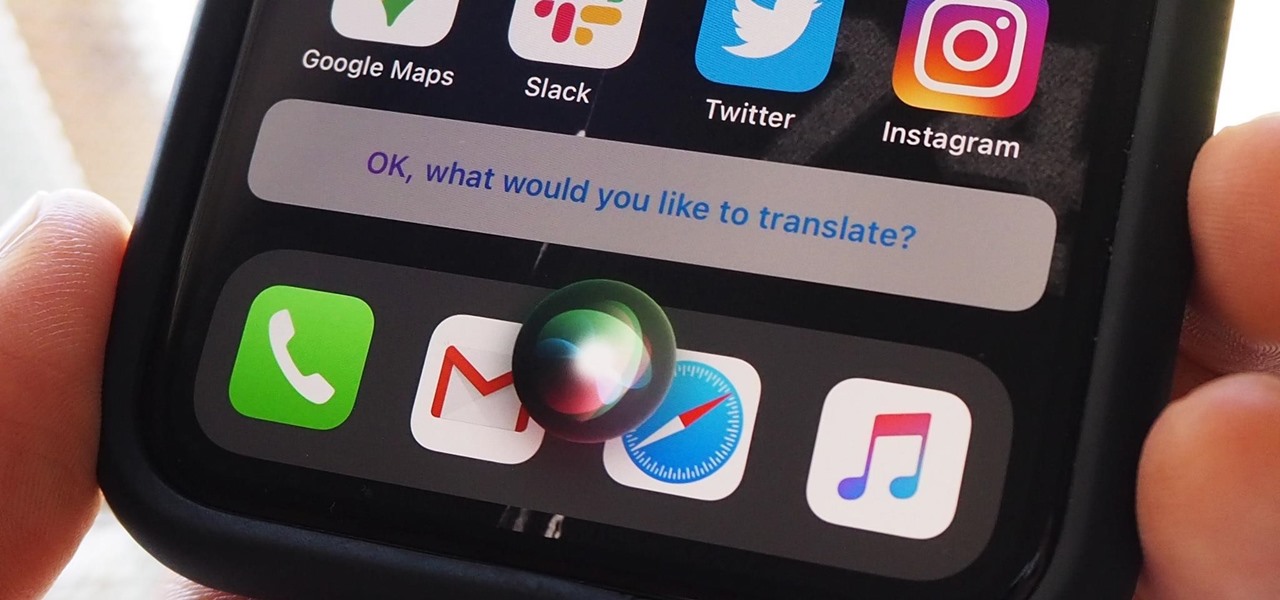
According to Apple, Siri serves 25 billion requests per month — an enormous number for a feature that was only released nine years ago. But when you think about how much work Apple has put into Siri over the years, it makes sense that the virtual assistant is being used more and more by users with iOS, iPadOS, macOS, watchOS, tvOS, AirPods, and HomePod.

The art of fuzzing is a vital skill for any penetration tester or hacker to possess. The faster you fuzz, and the more efficiently you are at doing it, the closer you come to achieving your goal, whether that means finding a valid bug or discovering an initial attack vector. A tool called ffuf comes in handy to help speed things along and fuzz for parameters, directors, and more.

PowerShell is an essential component of any Windows environment and can be a powerful tool in the hands of a hacker. During post-exploitation, PowerShell scripts can make privilege escalation and pivoting a breeze, but its execution policy can put a damper on even the best-laid plans. There are a variety of methods, however, that can be used to bypass PowerShell execution policy.

Samsung's lineup of Galaxy Note devices for 2020 include the specs-behemoth Galaxy Note 20 Ultra and the slightly more cost-effective Galaxy Note 20. Excuse the pun, but there's a lot to unpack here in terms of unique features and hardware.

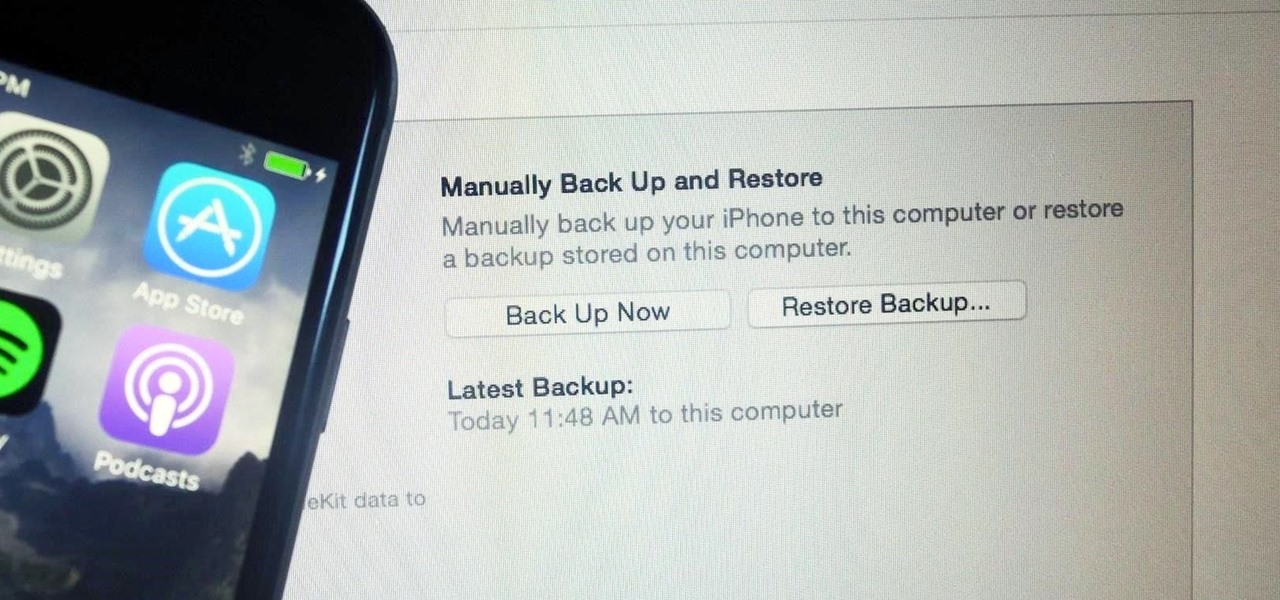
It's easy to back up and restore your iOS devices using iCloud, but there are a few downsides to encrypted iCloud backups. For one, Apple holds the key to decrypt all the data. Plus, you're limited to only 5 GB of data for free before you have to upgrade your storage to 50 GB, 200 GB, or 2 TB.

Kali Linux has come a long way since its BackTrack days, and it's still widely considered the ultimate Linux distribution for penetration testing. The system has undergone quite the transformation since its old days and includes an updated look, improved performance, and some significant changes to how it's used.

The internet has undoubtedly changed the way we work and communicate. With technological advances, more and more people can collaborate on the web from anywhere in the world. But this remote-friendly environment inherently brings security risks, and hackers are always finding ways to exploit systems for other uses.

Despite making great phones for years, Sony continues to struggle to penetrate the US market. Sales volume has fallen year after year, with 2019 limited to only 5 million units sold globally. To help alleviate this drop, last year, Sony released the Xperia 5, the return to compact smartphones. This year, rumors indicate a sequel is first on their agenda.

Individually addressable LEDs, also commonly called "NeoPixels" after the popular Adafruit product, are a bright and colorful way to get started with basic Python programming. With an inexpensive ESP8266 or ESP32 microcontroller, it's easy to get started programming your own holiday lighting animations on a string of NeoPixels with beginner-friendly MicroPython!

There's never been a better time for streaming movies and TV shows on the go. With so many services available, the only limitation to your enjoyment is your phone's accessories. Whether you're buying for yourself or someone else, here are some of the best gifts that improve the movie-watching experience on mobile.

Christmas is just one week before Jan. 1. That means a lot of New Year's resolutions filled with promises to better ourselves with increased productivity, focus, and work ethics — but getting started can be challenging. Give the people in your life a leg up this holiday season with these smartphone gifts to keep them on-task in 2020.

Cases and stickers are always great, but they aren't the only way to customize an iPhone. The software on your device is full of customization options, from a better-looking home screen and cooler lock screen wallpapers to app icon changes and a system-wide dark mode. There's literally over 100 ways to make iOS on your iPhone genuinely unique, some of which are hiding in plain sight.

Well before Magisk was in our lives, the Xposed framework was where all the mods and magic happened. Magisk was built on a similar concept with the ability to customize your system via modules. We can thank Xposed for where we are today in terms of root-related mods, but it's not done just yet — it's still very much alive and kicking after all these years.

Data can be injected into images quickly without the use of metadata tools. Attackers may use this knowledge to exfiltrate sensitive information from a MacBook by sending the pictures to ordinary file-sharing websites.

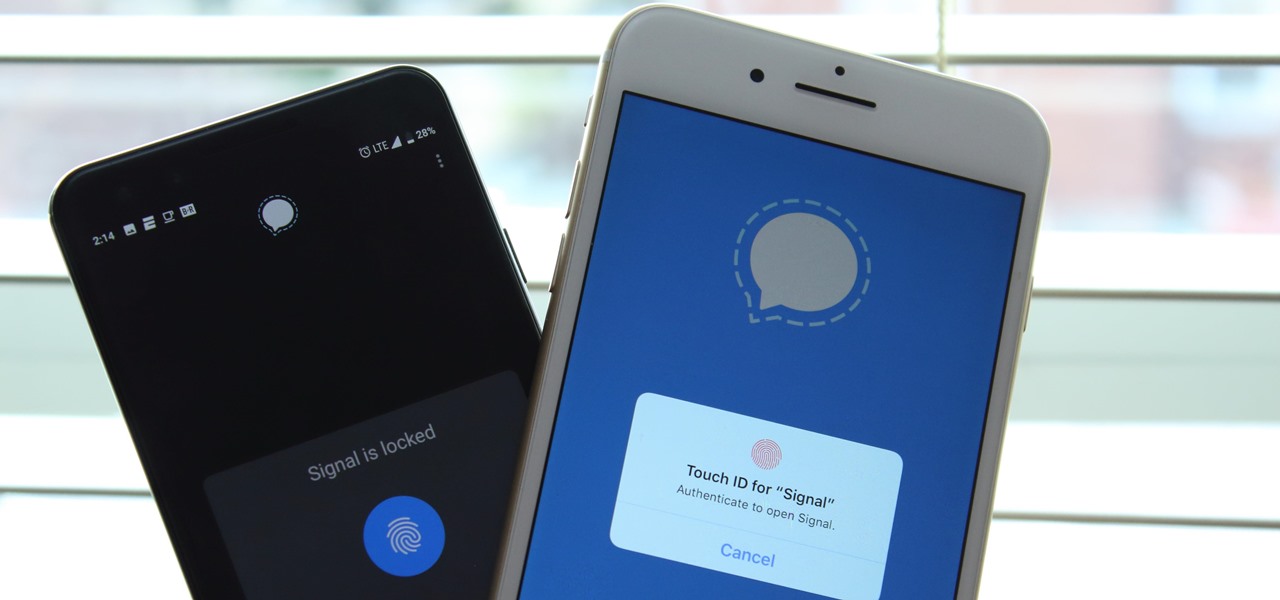
Signal is one of the best end-to-end encrypted messengers on the market. It offers robust security, keeps minimal information about its users, and is free to use. Switching to it as your main messenger can be a bit daunting, so to help, we created a guide to walk you through the process.

Need a unique gift idea for the techy person in your life? Look no further than that phone they always have in their hand. There are plenty of great accessories, apps, subscriptions, and other smartphone-related goodies that will improve their quality of life, and thoughtful gifts like that are always the best-received.

Let's say you want to download an Instagram video to your iPhone. What do you do? While Instagram doesn't offer an official solution, there are backchannel methods that exist to get the job done. However, if you want native support for downloading Instagram videos directly to your Photos app, you can start by updating your iPhone to iOS 12 and installing Shortcuts.

You've protected your Ubuntu system from physical attacks, annoyed network hackers, and sandboxed potentially malicious applications. Great! Now, the next logical steps to locking down your OS include thoroughly auditing Ubuntu for weak points, using antivirus software that respects your privacy, and monitoring system logs like a boss.

Once you've installed Ubuntu with security in mind and reduced the possibility of network attacks on your system, you can start thinking about security on an application level. If a malicious file is opened on your system, will an attacker be able to access every file on the computer? The chances are much slimmer if you put the proper defenses in place.

There's a lot more to your iPhone's dialer screen than just entering phone numbers and hitting the green call button. It's not very obvious, but there are secret codes that you can enter on the dialer to find out information about your device, help troubleshoot issues, and mask outgoing calls, to name just a few things.

To name just a few companies, VK, µTorrent, and ClixSense all suffered significant data breaches at some point in the past. The leaked password databases from those and other online sites can be used to understand better how human-passwords are created and increase a hacker's success when performing brute-force attacks.

A PirateBox creates a network that allows users to communicate wirelessly, connecting smartphones and laptops even when surrounding infrastructure has been disabled on purpose or destroyed in a disaster. Using a Raspberry Pi, we will make a wireless offline server that hosts files and a chat room as an educational database, a discreet local chat room, or a dead-drop file server.

Flight disruptions can cost billions of dollars, but most modern commercial flights rely on air traffic control systems that harbor serious vulnerabilities. The Federal Aviation Administration uses an infrastructure called NextGen, which relies on Automatic Dependent Surveillance – Broadcast, or ADS-B for short.

Airgeddon is a multi-Bash network auditor capable of Wi-Fi jamming. This capability lets you target and disconnect devices from a wireless network, all without joining it. It runs on Kali, and we'll cover installing, configuring, and using its jamming functionalities on a small, inexpensive Raspberry Pi. When done correctly, it will deny service to a wireless network for up to several blocks.

Besside-ng is the hidden gem of the Aircrack-ng suite of Wi-Fi hacking tools. When run with a wireless network adapter capable of packet injection, Besside-ng can harvest WPA handshakes from any network with an active user — and crack WEP passwords outright. Unlike many tools, it requires no special dependencies and can be run via SSH, making it easy to deploy remotely.

Android comprises an entire ecosystem of apps, games, functions, and features, so it would only make sense that it has its own lexicon. Words, phrases, and acronyms that didn't exist ten years ago are now used in an off-the-cuff style by developers and support technicians across the web.

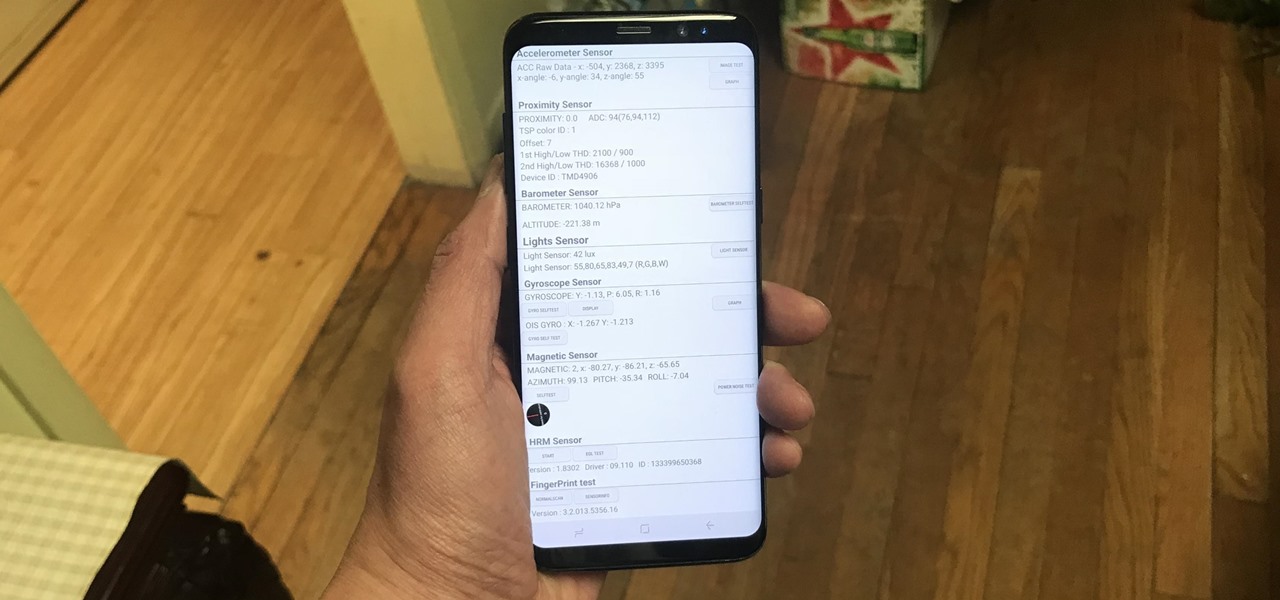
Besides obvious features like a touchscreen and biometric sensors, the modern smartphone comes with an array of state-of-the-art hardware in the form of various sensors that help your device sense the environment around it. And if you have a Samsung handset, chances are, you have a handy feature built in that enables you to check if these sensors are functioning 100 percent.

A hacker from Anonymous broke off communication with an FBI agent posing as a Symanec employee after being offered $50,000 to not publish the Symantec pcAnywhere code online. And in a not surprising turn of events... the code was released today on peer-to-peer networks.

We’ve all been there before. Relentlessly refreshing Ticketmaster and filling in those CAPTCHA codes only to receive the miserable “No tickets are available at this time” message. That’s because ticket brokers with a dozen screens and God knows how many browsers snatch up anything and everything.

On sports teams, especially youth sports teams, the players are never one and the same. Young athletes are all different, which means they all have different skills and abilities out on the field or in the arena. As a coach, you can't treat them as a whole, but you need to treat these young players as individuals of a whole. This video covers some practices and techniques, as well as gives advice for better coaching skills for teaching a "team". This is coach psychology.

Check out these easy steps for developing your psychic abilities. Develop your psychic abilities.

If you love playing those WarCraft and StarCraft strategy games on your PC, chances are you've also heard of a game called League of Legends.