Considering how much smartphones cost in the first place, we're understandably reluctant to throw them out when we've bought a newer model. And this is probably the best practice, too, as there are many great uses for an old Android device.

Often, the most frustrating part of crafting the perfect dinner is feeling like you have to clean every single pot and pan in your kitchen after cooking just one meal. With so many components, it can feel like each step of a single dish requires its very own pot.

Caramel is delicious, but it can be a tricky flavor to incorporate into baking. Traditionally, caramel is a liquid, and that doesn't always suit dessert preparation since adding extra liquid to baked goods can ruin them. So how do you get that buttery, toffee-like flavor?

Step aside, ginger ale; ginger beer is here, and it's delicious. Ginger beer is made by fermenting a combination of ginger simple syrup, yeast, and water, which gives it its robust flavor and sparkling quality. It's extremely simple to make, but you do have to wait a bit for the final product. After a few days, though, your ginger beer will be sparkling and ready to drink as is, or in your favorite cocktail.

You can put spices in a scramble or fry an egg in bacon fat, so why poach eggs in just plain water? Water doesn't add any flavor whatsoever, so you're wasting a valuable opportunity to give your poached eggs more oomph—an extra important step if you're not frying your poached eggs afterward.

Why, for the love of God, do people keep inventing ridiculous devices that make the simplest things more complicated in the name of convenience? This may be a rhetorical question that will forever go unanswered—because these crazy gadgets just keep rolling out, one after the other.

Store-bought marinades and sauces have an ability to jazz up the simplest items. But after a while, those favorite tastes seem a bit repetitive and mundane, and that got us to experimenting with different add-ins to make our marinades stand out. Fruits, herbs, spices—all of the usual suspects were delicious, but not spectacular.

We keep at least half a dozen hard-boiled eggs in the fridge for times when we're on the go and need a quick snack. Often, we eat them sliced in half with a pinch of sea salt and black pepper, or we just make some deviled eggs or a quick egg salad—but these gets old very quick, and our creativity tells us to do otherwise.

There are countless recipes for mug cakes (and breads) on the internet, but not all of them are good. Mug cakes promise a warm, moist, and fluffy cake after a few minutes and with minimal work... but sometimes, all you end up with is a chewy, rubbery mess.

The potato masher is one of the most dreaded tools in my kitchen; it always gives me flashbacks to when I had to mash potatoes for Thanksgiving dinners while growing up.

Counter-Strike is one of the most popular first-person shooters of all time, and deservedly so. What originally started out as a third-party Half-Life mod garnered such a cult following that Valve had to hire the developers and purchase the intellectual property to make it an official standalone release.

Desserts always taste better when they are sugar-coated—and even more so when they're coated in powdered sugar. In particular, crinkle cookies—cake-y cookies that are chewy on the inside and crispy on the outside—are famous for the powdered sugar that creates their cracked appearance.

If you love quenching your thirst with an ice-cold glass of lemonade but aren't a fan of artificial powder mixes, then this hack is for you. When your next lemonade craving strikes, instead of reaching for a glorified Kool-Aid packet, get an instant sip of summer by using pre-made, frozen lemon cubes to create your favorite drink. And this recipe isn't just easy to make, it's perfect for any number of servings, from single to several, or even a pitcher, if necessary.

Welcome back, everyone! In this lesson, I'm going to go over the use of the echo function and variables, as well as basic syntax.

It's been a while since I wrote up an article for this series but I did say that I'd be covering some WinAPI. So if you're interested in programming for the Windows platform, hop aboard and follow along.

We like our Egg McMuffins around here, albeit homemade with our preferred ingredients: whole wheat (or homemade sourdough) English muffins, a slice of thick Tillamook cheddar cheese, a meat, perhaps, like Canadian bacon, and finally—that perfectly-fried, perfectly-shaped egg.

Creamer, milk (whole or skim), sugar, or even butter—you've probably added at least one of these to your coffee to improve its taste at some point. If you're looking for something different, though, try a new twist with a dash of cinnamon. This sweet, sharp spice can do so much more than improve coffee's taste, and I've got 10 examples for you to consider.

Welcome back, my rookie hackers! The Golden Fleece of hackers is to develop a zero-day exploit, an exploit that has not been seen by antivirus (AV) software or and intrusion detection system (IDS). A zero-day exploit is capable of skating right past these defenses as they do not contain a signature or another way of detecting them.

Everyone has their own reality, and in that same vein, everyone has their own guidelines for what makes the "perfect fried chicken." Now, I'm not saying that my version is the ultimate for everyone, but it's definitely a crowd pleaser in my experience.
Fugu - a simple virus in bash. I once told a friend of mine I'd written a virus in bash and he scoffed - "You can't write a virus in bash!" - he sniggered, like an ignorant idiot.

Whether you are vegan, lactose-intolerant, or cooking for someone who is, standing before the non-dairy milk shelf in the grocery store can be daunting. Instead of playing it safe with the two most common milk alternatives—soy and almond—perhaps you should explore a few other choices that tend to be overlooked.

Welcome back, everybody. In the previous article, we covered the ideas and concepts of well-known ports and trust exploitation in order to evade a firewall. Today, we'll be building the shell, the part that receives commands, executes them, and sends the output back to the attacker.

Nothing about living in a snowy climate is easy, but life with a snowy, frozen car doesn't have to be the worst part of your day. With a few clever hacks and some anti-weather tactics, you can fight off frozen windshields, icy locks, and even stubborn car doors, while keeping your car running smooth all winter. 1. Deice Your Car Locks in Seconds

For many people, the two main advantages of buying a Nexus device are prompt updates and the ability to root without much hassle. But in a cruel twist of fate, these two features are almost mutually exclusive, since OTA updates will refuse to run on rooted devices.

Welcome back, my budding hackers! One of the most basic skills the forensic investigator must master is the acquisition of data in a forensically sound manner. If data is not captured in a forensically sound manner, it may not be admissible in court. In my Kali Forensics series, I showed you how to acquire a forensically sound, bit-by-bit image of a storage device such as a hard drive or flash drive, but now let's dive into live memory.

This is the easiest cookie batch you'll ever bake, I promise. And no, take-and-bake cookie dough doesn't count. With this recipe, it'll take you less than 20 minutes to go from your sad, cookie-less life to cookies in your absolute favorite flavor... of cake.

Welcome back! In the last training session we covered how to write and execute scripts. But today we'll be getting back to the code!

Almost every bread recipe will tell you to look for a golden brown crust or to tap on the bottom of your loaf and listen for a hollow sound. That visual and sound technique will work most of the time, but it can still come up short, leaving you with a soft and gooey spot in the middle of your loaf.

When you hand your unlocked iPhone to somebody so they can use the internet real quick, check out some cool photos, or do whatever, there's a possibility that they could snoop around where they don't belong. If you have some secret recipes, login credentials, intellectual property, or other sensitive information in your notes, you'll want to add some protection to them.

Greetings fellow hackers. This tutorial is about creating "safe" passwords. This is different from strong passwords. Safe passwords is just creating a password that is not used by someone else or colleague, my definition. But how do you prevent something like this from happening? Of course you won't ask your friend if s|he is using the password you are about to create. Before I show you some of my tele-psychic powers like Professor Xavier, you might want to read this for advice on creating "s...

Welcome to an introduction on writing basic malware, an optional sub-series in which I expose you to malware and its technologies. This is written for those who wish to seek a beginning in malware analysis or enlightenment on the subject. We will be justifying the writing and covering types of malware.

Most of us lead busy, work-filled lives, often clocking in a 9-to-5 five days a week. And when that clock signifies the hour to leave, the last thing on anyone's mind is: "Time to go to the grocery store to pick up more fresh produce!" (Well, to be fair... maybe more people are psyched about this, but I know with certainty that I am not one of them.)

A trip to any grocery store's produce section will quickly reveal that bananas are often picked from the tree well before their prime—which is necessary for them to arrive at our local store without going bad. In fact, bananas are refrigerated en route to our supermarkets in order to stave off the ripening process... which makes sense, since they travel quite the distance (from the Tropics around South America or Africa to our proverbial doorstep).

After seeing the title of this post from me, you might be thinking, "Why did The Joker made another post on a topic on which we already have a nice sticky post?"

Managing hard drives in Linux is crucial to understanding your system and its operation as well as understanding the system you are exploiting or conducting a forensic analysis on. Linux has numerous commands that can provide us with information, control, and management of hard drives, and in this tutorial, we will examine a number of the most important ones.

Before I get ostracized by all of you whisky lovers who live and die by whisky served neat, let me say my piece.

With over 10,000 possible combinations, a four-digit passcode may seem secure, but it's fairly easy for someone to crack your code—no matter how clever you think it is. Luckily, there are many other options for securing your iPhone's lock screen—especially if your running iOS 9.

Welcome back, my novice hackers! More and more, the world is turning to and adopting the smartphone platform as the digital device of choice. People are not only using smartphones for voice communication, but also web services, email, SMS, chatting, social networking, photography, payment services, and so on.

Welcome back! In the last iteration of how to train your python, we talked about functions, and we even made our own! We're going to move on to more types of data arrays (much like lists) in today's discussion.

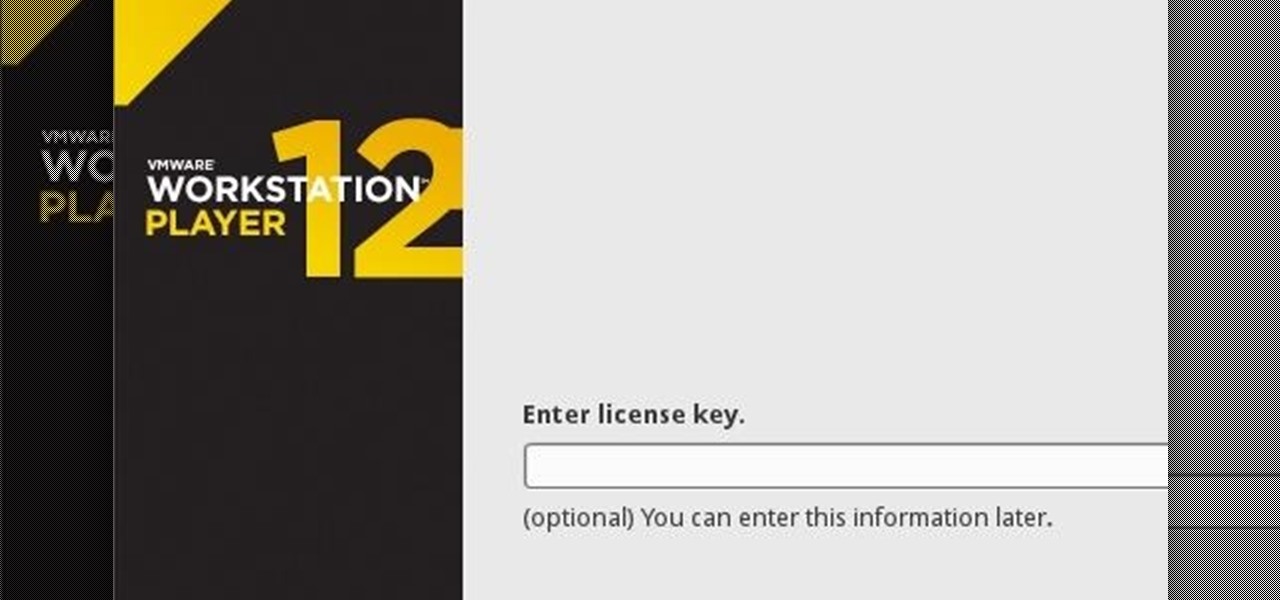
If you have never heard of a Virtual Machine (VM) before you might think it to be some new kind of gamers virtual reality system, and that would be incorrect. A virtual machine is a Virtually a real computer that exists inside of your own computer. You can run Kali inside of a Windows environment via your VM. Not quite the same as an actor portraying an actor on TV. A virtual machine will have it's own IP address and you have the ability to network to it from your Real (Host) computer and bac...