A long-standing request for the iPhone has been a way to quickly browse and connect to available Wi-Fi networks and Bluetooth devices without having to dig through the Settings app. With iOS 13, Apple has finally built this essential feature into Control Center, giving you quick access to wireless settings from anywhere, including the lock screen.

NetBIOS is a service that allows for communication over a network and is often used to join a domain and legacy applications. It is an older technology but still used in some environments today. Since it is an unsecured protocol, it can often be a good starting point when attacking a network. Scanning for NetBIOS shares with NBTScan and the Nmap Scripting Engine is a good way to begin.

A relay is an electrical component that works like a light switch, where it's turned on or off with an electrical signal. By connecting a relay to a Wi-Fi connected microcontroller like an ESP8266, you can build a connected switch that can be controlled from the web browser of any device connected to the same Wi-Fi network — all for just a couple of dollars.

Many popular IoT devices have terrible security. For instance, a hacker who's on the same Wi-Fi network as a Sonos speaker can assume direct control over the device's behavior. If an IoT device doesn't secure the messages used to control it over a network, it's easy for somebody to write a few Python scripts to make it do whatever they want.
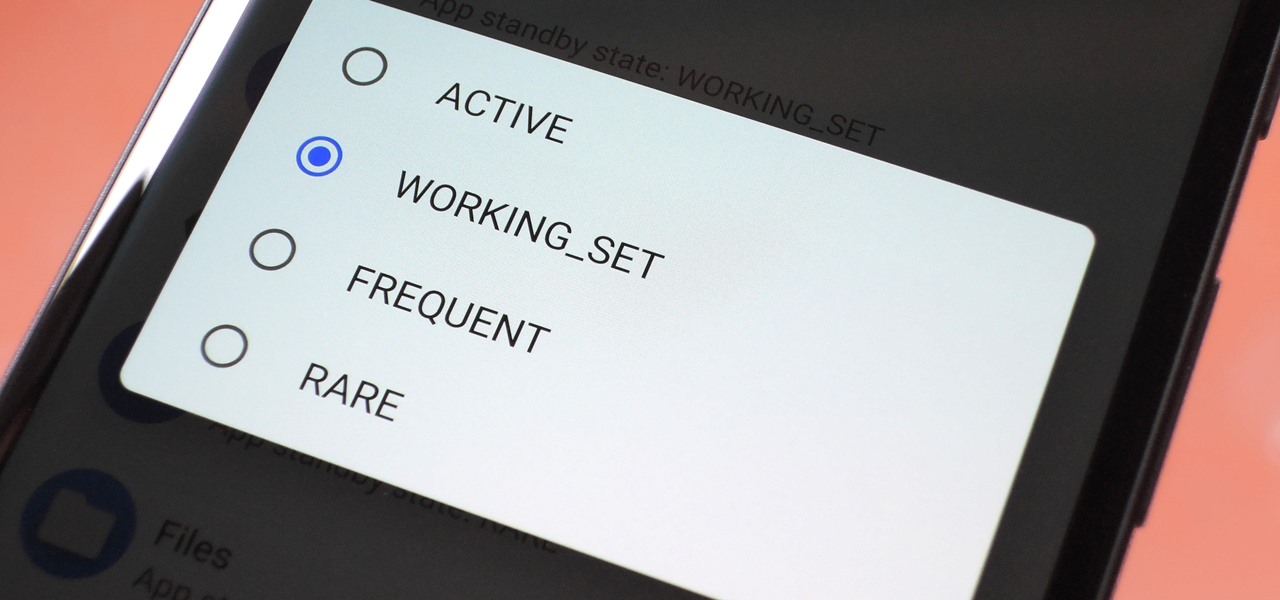
Battery drain is a major pain point for Android users, though that promises to change thanks to Android Pie's new Adaptive Battery feature. But Google hasn't said much about the inner workings of this feature, only publicly stating that it uses AI to boost battery life. So we dug in to find out what's really going on under the hood.

Augmented Reality beauty tools have become quite popular lately, and while CoverGirl's didn't exactly turn heads, the new Wanna Nails app by Wannaby looks like a great tool for anyone who uses nail polish.

Some of us woke up at the KRACK of dawn to begin reading about the latest serious vulnerability that impacts the vast majority of users on Wi-Fi. If you weren't one of those early readers, I'm talking about the Key Reinstallation Attack, which affects nearly all Wi-Fi devices.

Nvidia has emerged as the indisputable leader in chips for Level 3 and even more advanced driverless applications, catching some of the world's largest semiconductor makers and automotive suppliers by surprise.

To hack a Wi-Fi network using Kali Linux, you need your wireless card to support monitor mode and packet injection. Not all wireless cards can do this, so I've rounded up this list of 2019's best wireless network adapters for hacking on Kali Linux to get you started hacking both WEP and WPA Wi-Fi networks.

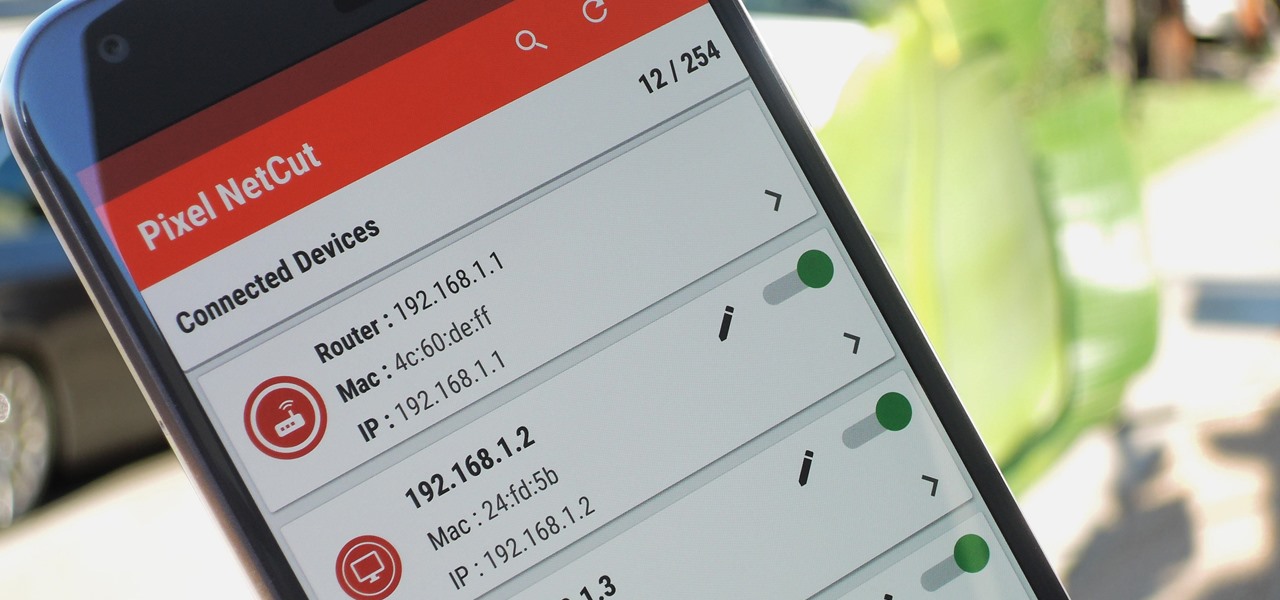
It's no secret that devices leak data, but sometimes they do so in ways you may not expect. Your phone, laptop, printer, and IOT devices leak Wi-Fi information that can (and is) used to track you.

Apple announced upcoming changes today to prevent third-party tracking of users and prevent autoplay, on Safari. Safari will prevent the recording (by anyone other than Apple) of users' browsing behavior, and by doing so prevent advertisers from targeting ads based on individuals' history.

Those of us with modern smartphones know that 4G LTE networks have provided us with a phenomenal experience. One light years beyond what we had access to before. For some time, AT&T has been teasing its dive into the next iteration of network speeds, agonizingly doing so without any specific dates for when they would actually deliver. But today, AT&T confirmed what they call the "5G Evolution," and it's available now.

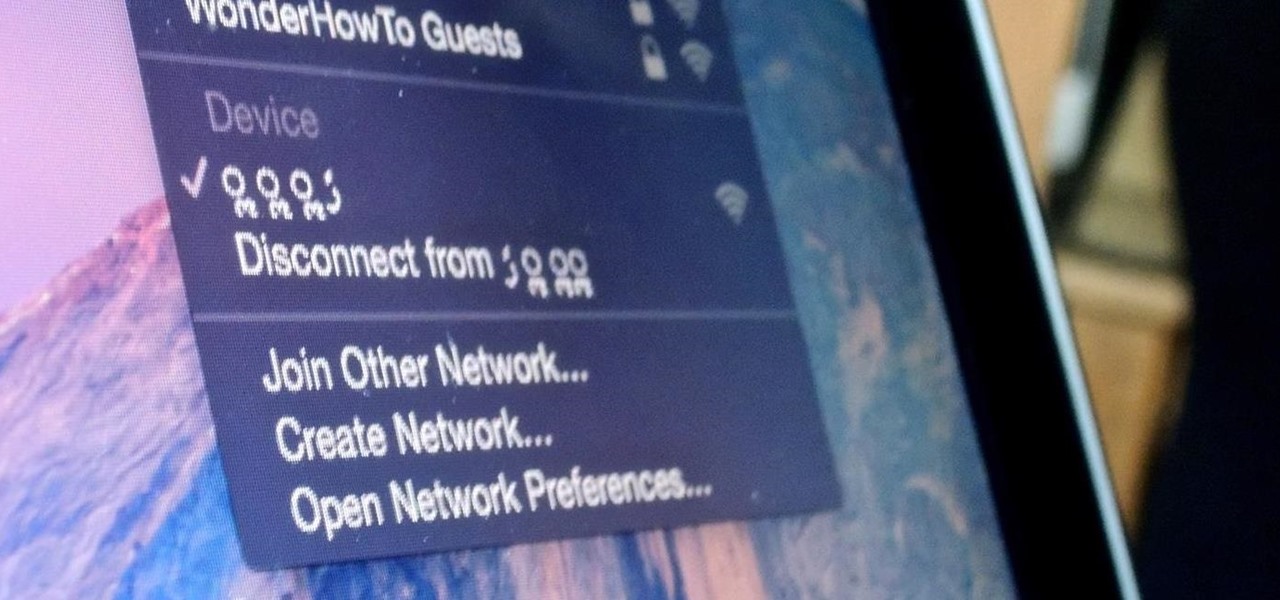
Let's say you gave your Wi-Fi password to your neighbor a while back, under the assumption that they'd only use it while they were at your house sharing stuff via Chromecast. But now, your connection is slower than it normally should be, and you have this sneaking suspicion that the dude in apartment 3C is flat-out piggybacking off of your home network.

If you want to make some money from catching bugs and are sick of pentesting Facebook, Google, and Microsoft's products, Uber may be your new favorite playground.

Welcome back my networking geeks. In this part we are going to keep discussing about IP Addressing and I hope after you finish reading it you will become an IP wizzard.

Once you connect all of your devices to your Wi-Fi router at home, you'll never need that long, complicated Wi-Fi password ever again, right?

As mobile devices become more and more popular, service providers have unfortunately resorted to capping data. What this means is that, depending on the plan you have with your ISP, you could have limits placed on how much data you can use for a set period of time. Once you've hit the limit, your ISP could drastically slow down or throttle your internet speed or charge you outrageous overage fees.

Relentless in its fury, the iOS text messaging exploit that exploded onto the scene late last week seems to do more damage than initially reported.

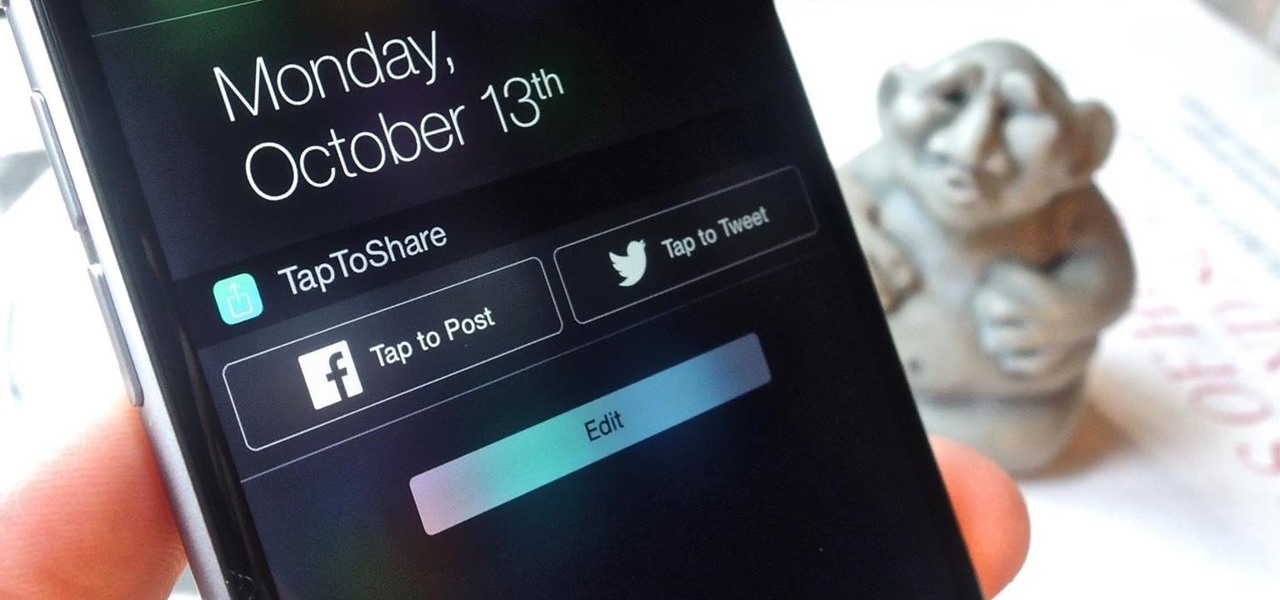
Back in the days of iOS 6, iPhone users were able to send a quick tweet from their notification center, but that has long since been removed. This convenient feature was missed enough on iOS 7 for devs to create a jailbreak tweak in its absence. Thankfully, due to the new widget capabilities of iOS 8, we can have Twitter back in the Notification Center along with Facebook.

UPDATE (February 26, 2014) Yesterday, the U.S. House of Representatives passed H.R. 1123 with a 295-114 vote decision. The ruling repeals the 2012 Library of Congress (LOC) decision that limited the ability to legally "unlock" your smartphone (see below).

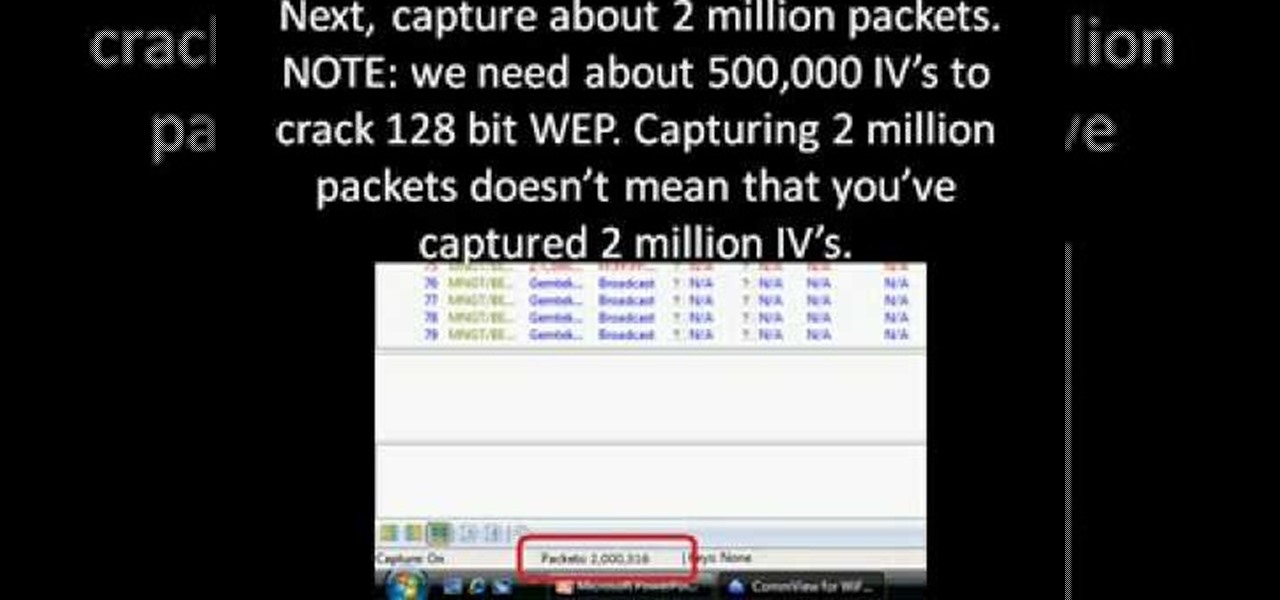
First you need to download Aircrack-ng and Second thing you need to download is CommView for Wi-Fi. Now you have to install CommView for Wi-Fi and then install the right driver.

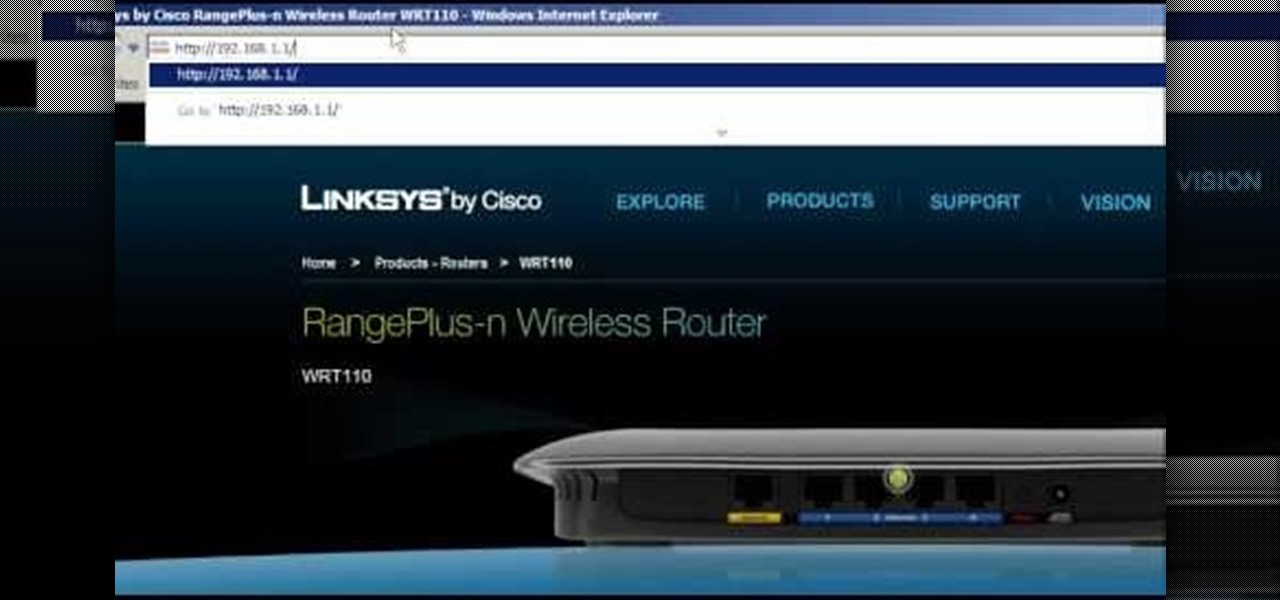
1. Describes how to setup a VPN connection on Windows XP. 2. Goto Start-> Control Panel-> Network connections.

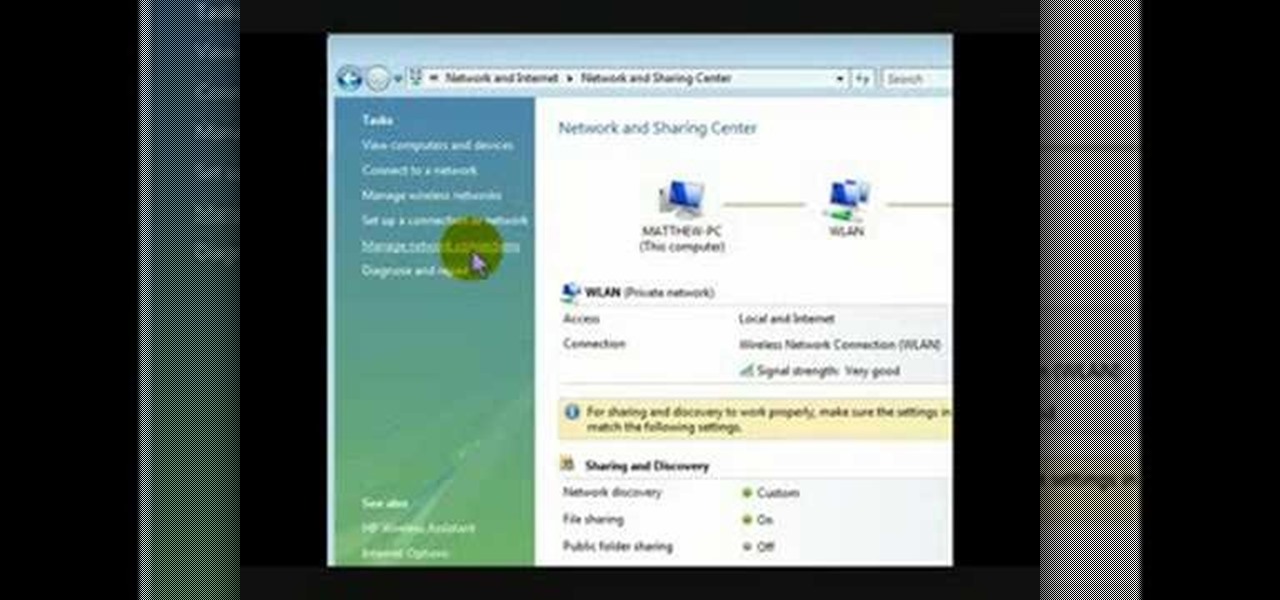
This is a video that is describing how to connect your xbox360 to the internet using a laptop. First what their showing is going to the start menu, and then to the right of it, click on control panels. A little page will pop up, and you click on network and internet. It takes you to another page and then you click network and sharing. It will take you to another page, where you see three computers, and to the very left of that page there it says "tasks" look in the columns under tasks and cli...

Wrestling with the whys are wherefores of WiFi? Can't figure out how to secure your network? Take heart: This remarkably thorough, seven-part home networking tutorial will get you up and running faster than you can say `Wireless G.'

Mike Biggly shows us how to set up our home internet and networks. Part 1 of 20 - How to Set up your home internet and network.

In this video, we learn how to pull a compilation of computer pranks on a friend. The first trip is a mouse prank where you will open up the control panel and find the mouse settings. From here, you can switch the buttons from left to right and change the speeds of the mouse. Next, you can do network pranks by running cmd.exe as administrator. Then, go and see who is on the network and type in "msg /server:(ip address) and message". You can also do a ghost typing prank, which you will create ...

First click the explore button, this will open a fold in which you will click homegroup and the second computer in the network. By clicking on that you will see what is in the homegroup. For example clicking on the video icon shows you all the videos available. If you right click on the video you can choose to watch it, open it, send it to different places, drag it onto your computer or copy and paste it into another directory.

Today we learn how to brine pork and poultry with the Food Network. You only need to have salt and water to make your brine for your pork. First you need to grind up your salt into a fine powder, which will make dissolving easier. Now dissolve your salt into your water. Complete submersion is very important when soaking your meat. If you're soaking a turkey or a goose use a cooler for full submersion. Let it soak for ten hours. Now your cuts of meat will be more juicy and tasty.

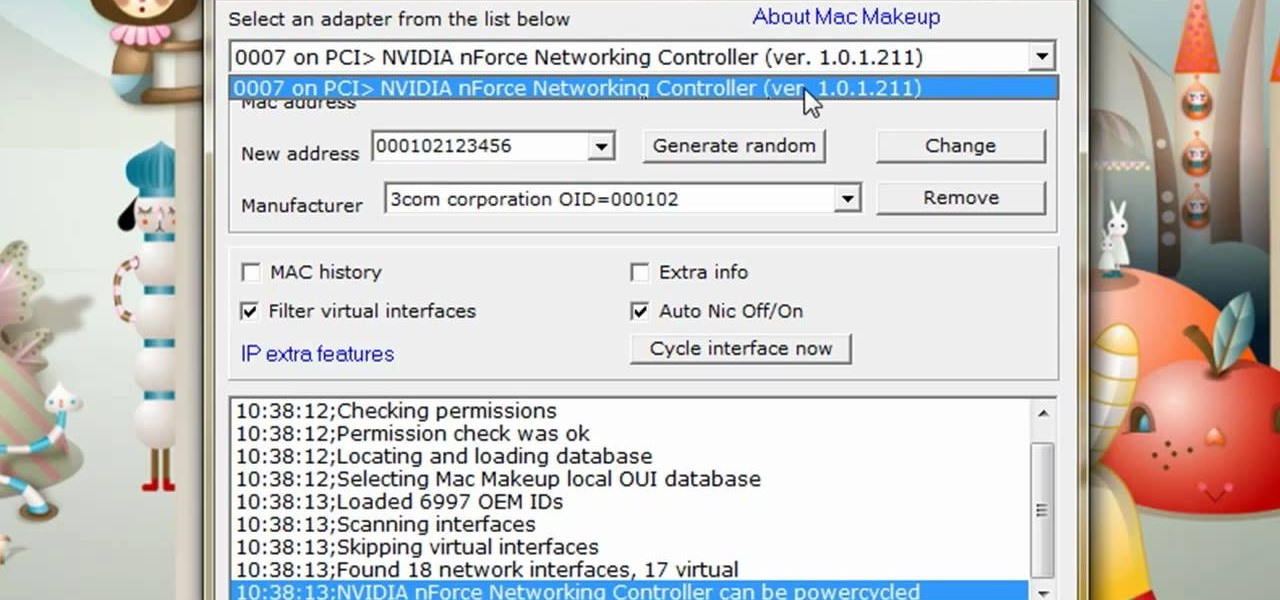
The video is about how to change the IP address. MAC address is the unique identifier a site of the most network adapters. MAC address is used to determine what IP address the computer will have and one way to change the IP address is by changing the MAC address. The method is only applicable for the windows systems and for the MAC systems you need to look at the link provided. In Windows in the start menu, type cmd in the run/search box, which will launch the command window. Type ipconfig/al...

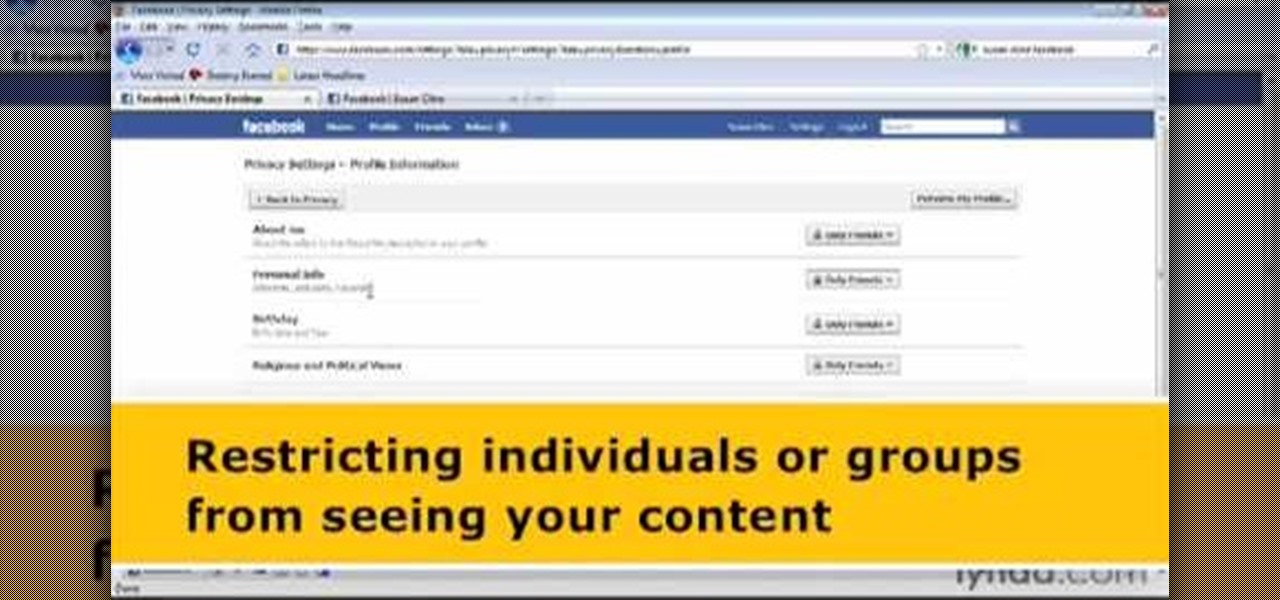
Facebook is one of the most popular social networking sites out there, so make sure you are being safe! Susan Kline shows you in her Facebook Essential Training series how to Restrict certain aspects of your profile. Login to Facebook and view your Privacy Settings. From there you can pick your About Me, Personal information, Wall Post, Photos and more and restrict showing it to people. You can pick everyone, certain friend lists, Networks, and even individualize it down to one person.

Do you long for a Polynesian vacation? Do you wanna go back to your little grass shack in Hawaii? Well, if you can't afford that, you can at least have a stylish "staycation" at home with your own homemade tike bar. You'll learn to build one in this Decor It Yourself video tutorial.

Save the trees! Have a few extra wire hangers hanging around? Make your own retro Christmas tree for your next holiday season out of old hangers, wiring, and shiny tinsel. With help from ThreadBanger's Decor It Yourself, your new Christmas tree will be done in no time, standing tall and eco-proud!

Have you ever heard of wet felting? Well, it's the oldest form of textile making and relatively easy to work, thanks to this tutorial by ThreadBanger. Learn how to create a classic-looking beret for this winter season. No sewing required!

ThreadBanger give us a great recipe to make a unisex bomber hat using just a flannel shirt, white faux fur, a measuring tape, the bomber hat pattern, a sewing machine, and two and a half hours of your creative time. Add pom-poms at the ears to give it extra flavor! Super cool look for both dudes and ladies.

This week Corinne shows us how-to make a classic back to school accessory that can be worn by both the guys and gals. This quick and easy tie is sharp, and will start the school year off right. Just follow along with the steps in this how-to video and you'll be on an honor roll.

The Great Zenovka and her lovely assistant show us how-to make a cowl neck halter top. Just get an old t-shirt, follow along with this how-to video, and you're ready to go in style.

To kick off T-shirt Madness week, Threadbanger forum member ArtCrazed shows us how-to make an adorable purse out of two old tees! Follow along with the steps in this how-to video and learn how to refurbish some old clothes into something new!

This week Megan Nicolay returns to show us how-to make a sexy halter with a plunging neckline from her new book, Beyond Fashion. So get out the old tees and get to cuttin'.

You wanted more summer lessons, you got em. This week learn how to take an old mens shirt and turn it into a rockin new rockabilly swim suit. Just follow along with the steps in this video and take your new stylish suit to the beach.