How To: Setup a wireless home network
So you know how to setup a network in your home, but how do you go wireless? The Lab Rats, Andy Walker and Sean Carruthers show you how to setup a wireless (WIFI) network.


So you know how to setup a network in your home, but how do you go wireless? The Lab Rats, Andy Walker and Sean Carruthers show you how to setup a wireless (WIFI) network.

With CES in full swing, it seemed like Magic Leap would have little to announce at the major tech event, but it turns out that one of its partners has weighed in with a rather substantial update regarding the company.

It really is possible to bring out a persons psychic ability, why? because it is already buried somewhere inside everyone who has a heartbeat! John Green helps you develop your psychic ability in this video.

This video tutorial is in the Computers & Programming category where you will learn how to secure your wireless internet connection. If you don't secure your wireless internet connection you are allowing others to enter in to your network. Open the set up CD and first change the network name from the default name to anything that you like. For this go to step 3 of 'naming your network', type in your network name and click 'next'. Then you enable security on the network by choosing 'WPA2'. Nex...

The Lab Rats, Andy Walker and Sean Carruthers, explain Media Access Control (MAC) addresses. Filtering MAC addresses allow you to very specifically control access to your wireless network.
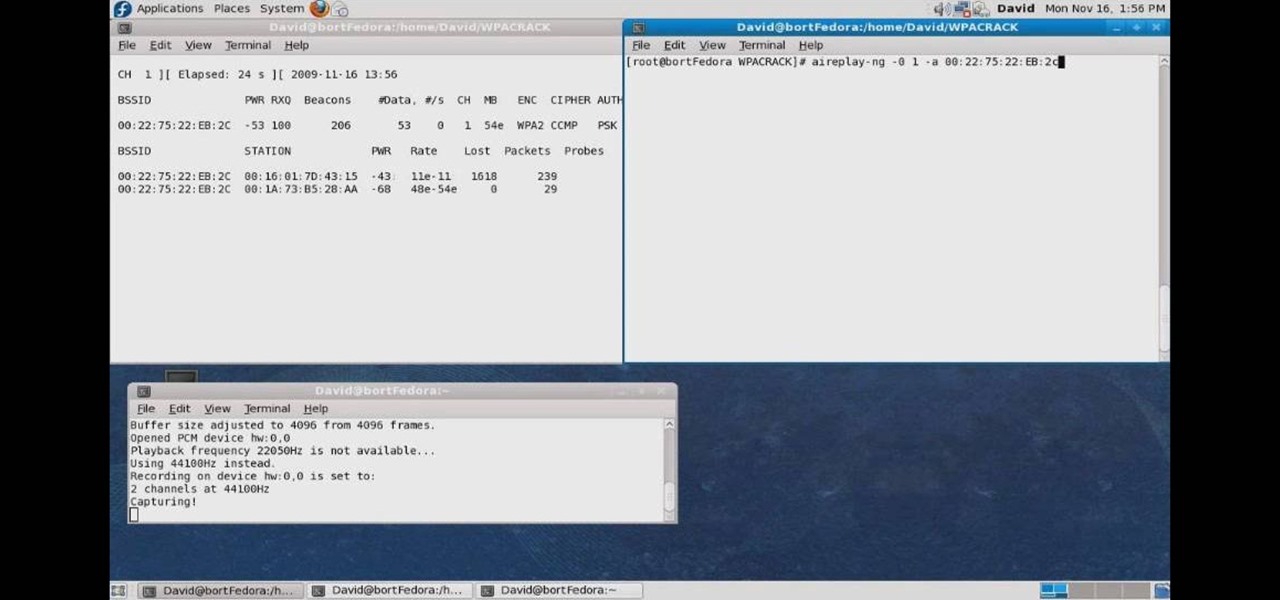
In this how to video, you will learn how to crack a WPA encrypted wireless network. To do this, you will need the Air Crack package for Linux. First, disable the wireless adapter and enable monitor mode. Next, identify the channel in the wireless network and Mac address. Once you have this, you can listen to the traffic coming to and from this point. Wait for the handshake or disconnect something in order to force it to reconnect. From here, you are ready to perform the attack. With any encry...
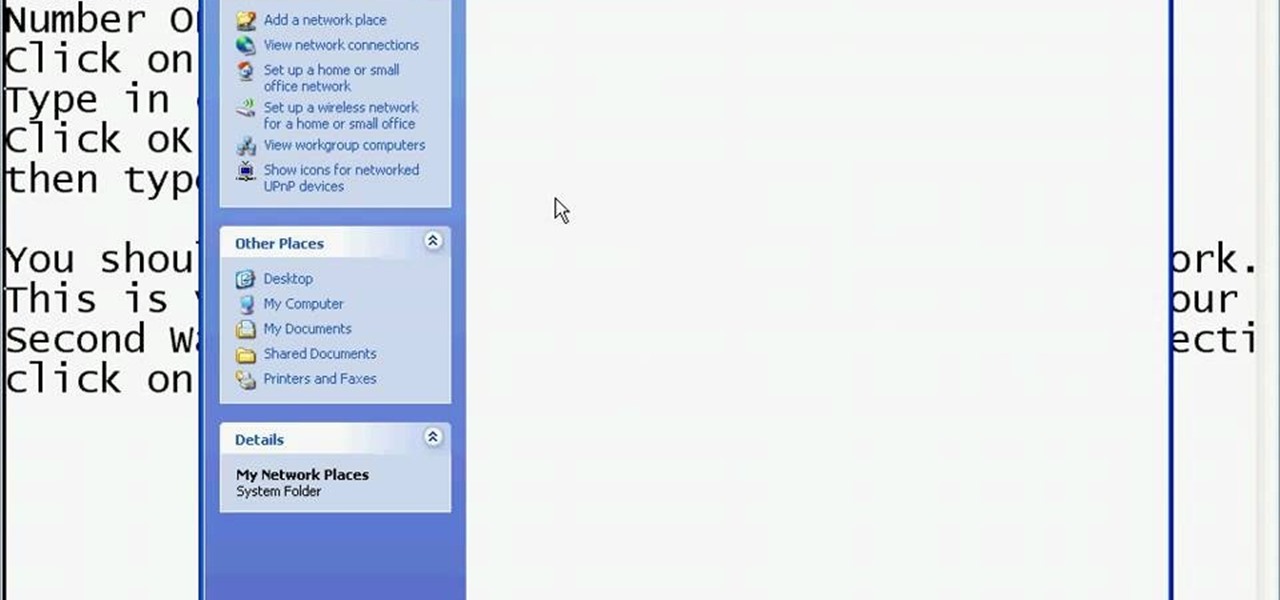
This video shows you the method to find if someone else is using your Internet connection. There are two methods for this. The first method involves opening the start menu and click on 'Run'. Type cmd in the text box which opens as a result of clicking on 'Run'. Type NET VIEW at the command prompt. This will show all people using your network. The second method involves going to Start menu. Go to Connect to and Show all connections. Click on My network places. Click on 'View workgroup compute...

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to map networks with Spiceworks.

Nokia, the Finnish telecommunications company, is about to shake things up a bit after its networks sales in the final quarter of last year declined 14% compared to sales in 2015.

Good day people, today we will examine some basic, for some people well-known attacks, also we will take a look at some advanced attacks.
After I traded in my Samsung Galaxy S5 for an iPhone 5S, the one feature I truly missed was the Smart Remote app. My television remote was broken and the S5 saved me from, you know, actually having to get up and change the channel.

If you're spending hours on your phone playing games like Angry Birds and Candy Crush Saga, or posting online to Google+ and Pinterest, you're probably being spied on. The latest releases from NSA whistle blower Edward Snowden reveal that the National Security Agency, and its UK counterpart, GCHQ, are mining the ad networks utilized in these apps to collect a trove of information on you.
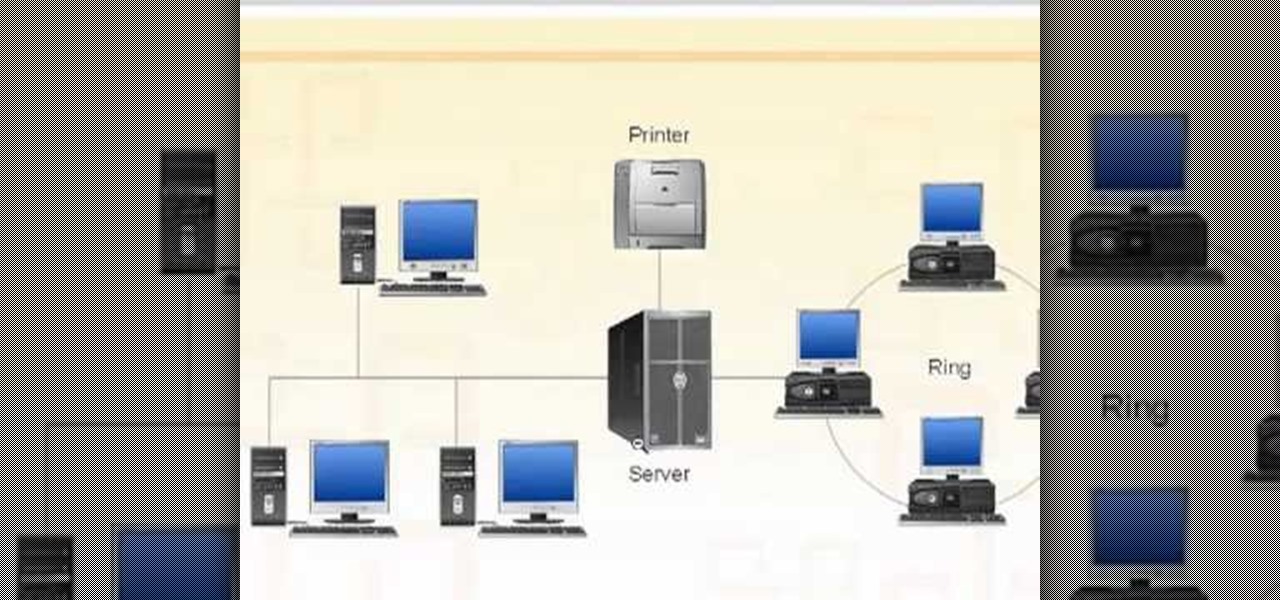
Need some help figuring out the ins and outs of LAN networks? They're easy enough to understand. And this brief video tutorial from the folks at Butterscotch will teach you everything you need to know. For more information, and to learn more about LAN networks yourself, watch this helpful video guide.

Roughly half of all Americans believe in extra sensory perception... Are you part of that statistic? Ever get the feeling you have a paranormal ability? You can investigate your psychic abilities and hone your skills with these tips.

The first of a two part series on setting up your linux server and network for external access through your cable modem or DSL. Covers modifying the Linux servers network setting to a static IP address.

If you want to connect your Mac notebook or desktop to a wireless network, you'll need to set up the wifi connection on your computer first. Take a look at this walkthrough to find out how to find and connect to available wireless networks in OS X. This is a great skill to know if you own an Apple laptop and need to connect to the Wi-Fi networks at different locations.
When Microsoft came out with it's big XBox 360 firmware update at the beginning of last year, one of the cool abilities that they added to the console is the ability to install games directly to the hard drive. This will make your games load much faster and improve your gameplay experience. If you're lucky enough to have a big hard drive on your XBox 360, you should really do this to you whole library.

No matter what sports you play, multi-directional explosiveness, or the ability to change direction and run in that direction quickly and explosively, is vital. This video demonstrates some techniques for training this ability into young athletes, including resistance training and keeping proper form.

What if you could easily visualize which access point every Wi-Fi device nearby is connected to in a matter of seconds? While programs like Airodump-ng can intercept this wireless information, making it easy for hackers to use and understand is another challenge. Fortunately, a tool called Airgraph-ng can visualize the relationships between Wi-Fi devices from only a few seconds of wireless observation.

While augmented reality made more of a cameo appearance during Samsung's official grand unveiling of the Galaxy S10 line-up on Wednesday, it's the company's move into 5G connectivity that has huge implications for AR.

After finding and monitoring nearby wireless access points and devices connected to them, hackers can use this information to bypass some types of security, like the kind used for Wi-Fi hotspots in coffee shops, hotels, and in flights high above the ground. By swapping their MAC address for that of someone already connected, a hacker can bypass the MAC filter and connect freely.

The research team at Google has found yet another way for machine learning to simplify time-intensive tasks, and this one could eventually facilitate Star Wars-like holographic video.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to build a free XMPP/Jabber server in ten minutes.
Nmap ("Network Mapper") is a free and open source (license) utility for network exploration or security auditing. Many systems and network administrators also find it useful for tasks such as network inventory, managing service upgrade schedules, and monitoring host or service uptime. Nmap uses raw IP packets in novel ways to determine what hosts are available on the network, what services (application name and version) those hosts are offering, what operating systems (and OS versions) they a...

This video will show you how to subnet using CIDR notation. If you're curious about how to determine networks, subnet masks, broadcast addresses and what makes a host range valid. A great video for anyone currently studying computer networking technology.
This video will teach you how to hack a WEP wifi network on a Mac. You'll need to follow the link, grab the prog and follow the steps. It's not too hard, so give it a try. Remember, stealing is illegal!

Want to see whether your PC is being accessed by hackers? Netstat (network statistics) is a command-line tool that displays network connections (both incoming and outgoing), routing tables, and a number of network interface statistics. It is available on Unix, Unix-like, and Windows NT-based operating systems. This video tutorial presents a basic introduction to working with the netstat tool. Determine whether you've been hacked with this how-to.

Anyone can set up their own wireless network. All you need is a little know-how. You will need a computer with wireless capability, a high-speed modem, a wireless router, and a broadband internet connection. Don't get tied to the wall; a wireless connection will allow you to move the computer freely around your home and still get an internet connection. Watch this video tutorial and learn how to hook up a wireless network at home.

Tekzilla shows you how to troubleshoot network woes with ping and traceroute.
One of the great things about Myspace, is the ability to customize the layout on your homepage. It gives you the ability to be as creative as you want and show as much personality without being restricted. So in this tutorial, you'll learn how to make a custom Myspace 2.0 layout using easy to use computer programs. Good luck and enjoy!

Check out this video to learn how to read the head line on your or someone else's palm. This video is cool because it is very easy to do while watching. (I tried it--apparently, I have more creative ability than writing ability, can you tell by this description?)

WPA-secured wireless networks, or WiFI Protected Access, is a form of internet security that secures your wireless LAN from being accessed by unauthorized users. Safer than WEP, or wireless equivalent privacy, WPA still has weaknesses that are prone to cracking - IF, that is, you know what you're doing.

Wi-Fi networks come in two flavors: the more common 2.4 GHz used by most routers and IoT devices, and the 5 GHz one offered as an alternative by newer routers. While it can be frustrating to attack a device that moves out of reach to a 5 GHz Wi-Fi network, we can use an Alfa dual-band adapter to hack Wi-Fi devices on either type of network.

The first question people ask me when they come to my apartment is usually "What's your Wi-Fi password?" While I'm happy to give my friends free access to the internet, it's hard to walk each person through my secure password. Luckily, there's a way to create a QR code that will let people easily connect to a Wi-Fi network.
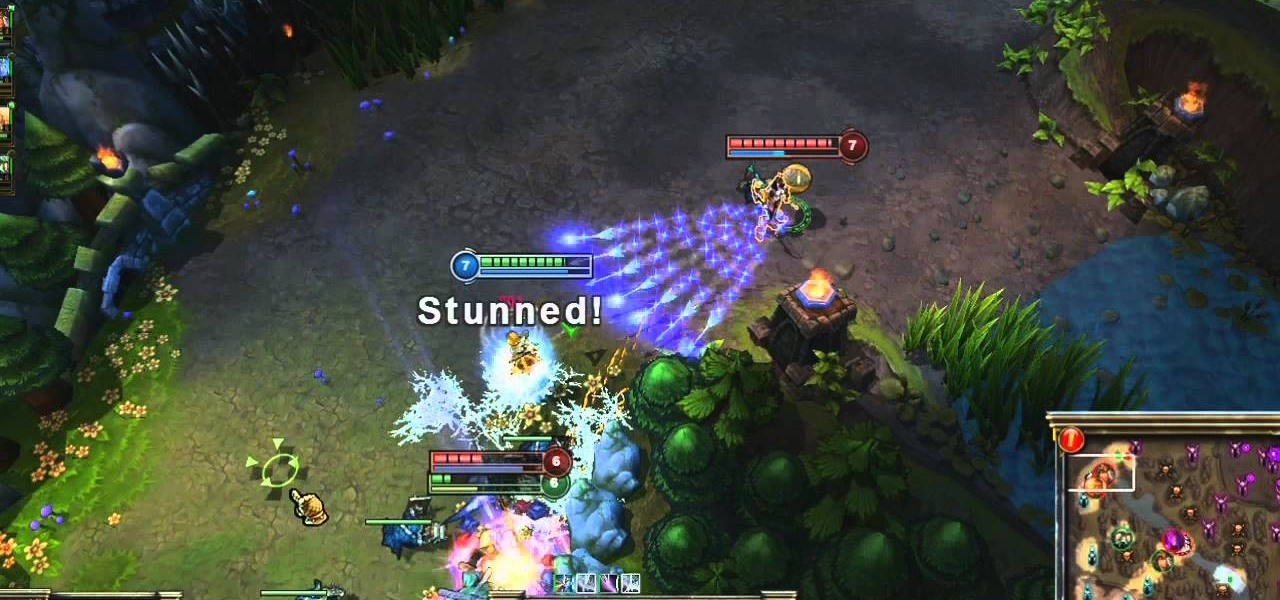
Orianna is a unique champion that focuses her abilities on the use of a ball she carries with her. The ball allows you to pull off some pretty cool tricks, including slowing your opponents in an AOE around it and harassing with it during the laning phase.
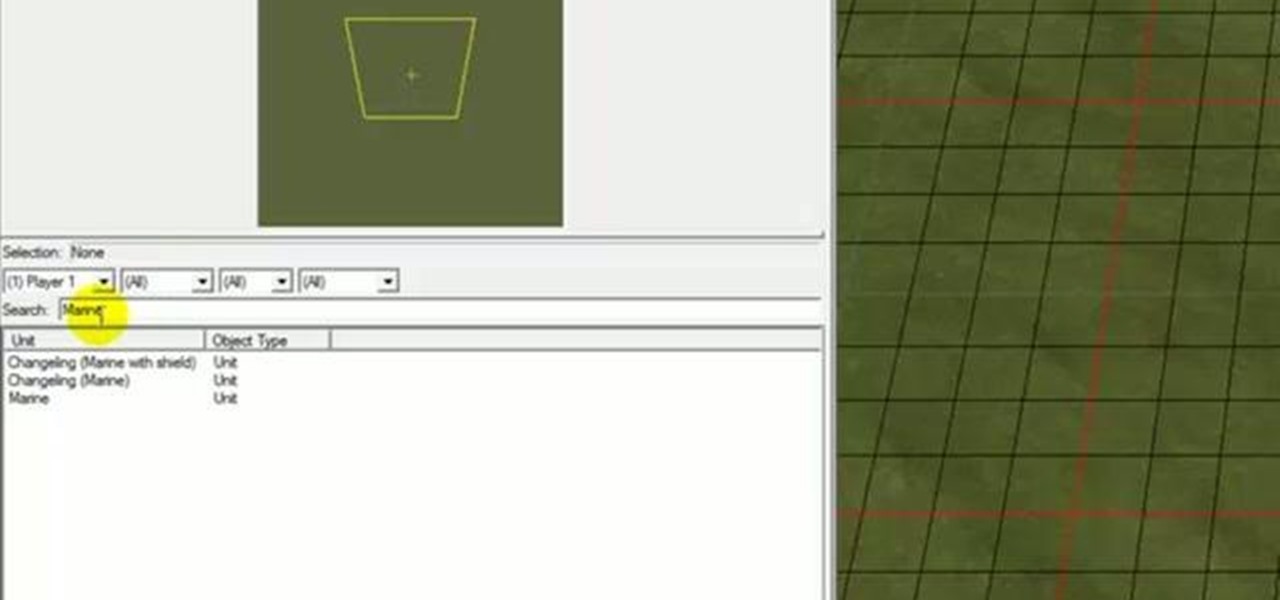
Starcraft 2, like so many modern games in this age of modding, has a really robust level editor that's going to extend the lifespan of the game for years. You can edit almost anything about any of the game's many units buildings and maps, and make the game however you want it to be. This video will show you how to create a map, add custom abilities to a Terran unit, then blow up some Zerg with it. It's quick, fun, and a great place for beginners at Starcraft level editing to get started.

Need some help figuring out how to put a password on your wireless router? This home-computing how-to from the folks at CNET TV will teach you everything you'll need to know to do just that. For detailed information, and to get started protecting your own wireless network helpful video guide.

Netcat is a featured networking utility which reads and writes data across network connections, using the TCP/IP protocol.

If you're just itching for an excuse to reuse that retired desktop PC or laptop sitting in your closet there here's your chance. This tutorial offers a look at the basics of installing FreeNAS, an open-source DIY NAS. So instead of spending money on off the shelf options why not save yourself some cash and make use of the stuff you already have and get a super customizable network storage device to boot?
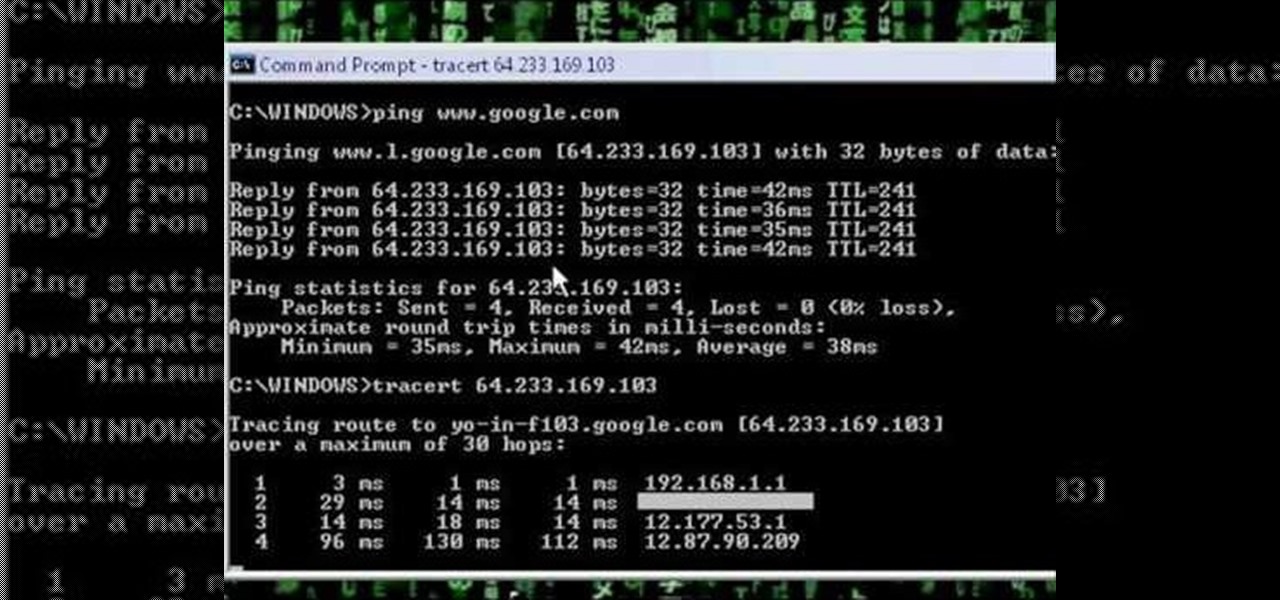
A network security tutorial on using ping and tracert to show th IP of a webserver, your own IP, your ISP's IP, who they connect to, and what computers your request goes through before reaching a destination.