Hackers and makers are often grouped under the same label. While hackers draw on computer science skills to write programs and find bugs, makers use electrical engineering to create hardware prototypes from microprocessor boards like the Arduino. We'll exercise both sets of skills to program a $6 NodeMCU to display the status of a Wi-Fi link via an LED, allowing us to monitor for jamming attacks.

Due to weaknesses in the way Wi-Fi works, it's extremely easy to disrupt most Wi-Fi networks using tools that forge deauthentication packets. The ease with which these common tools can jam networks is only matched by how simple they are to detect for anyone listening for them. We'll use Wireshark to discover a Wi-Fi attack in progress and determine which tool the attacker is using.

Identifying vulnerable devices and services on a target router can be difficult without leaving logs and other traces of an active attacker on the network. However, there is a way to covertly decrypt and view Wi-Fi activity without ever connecting to the wireless network.
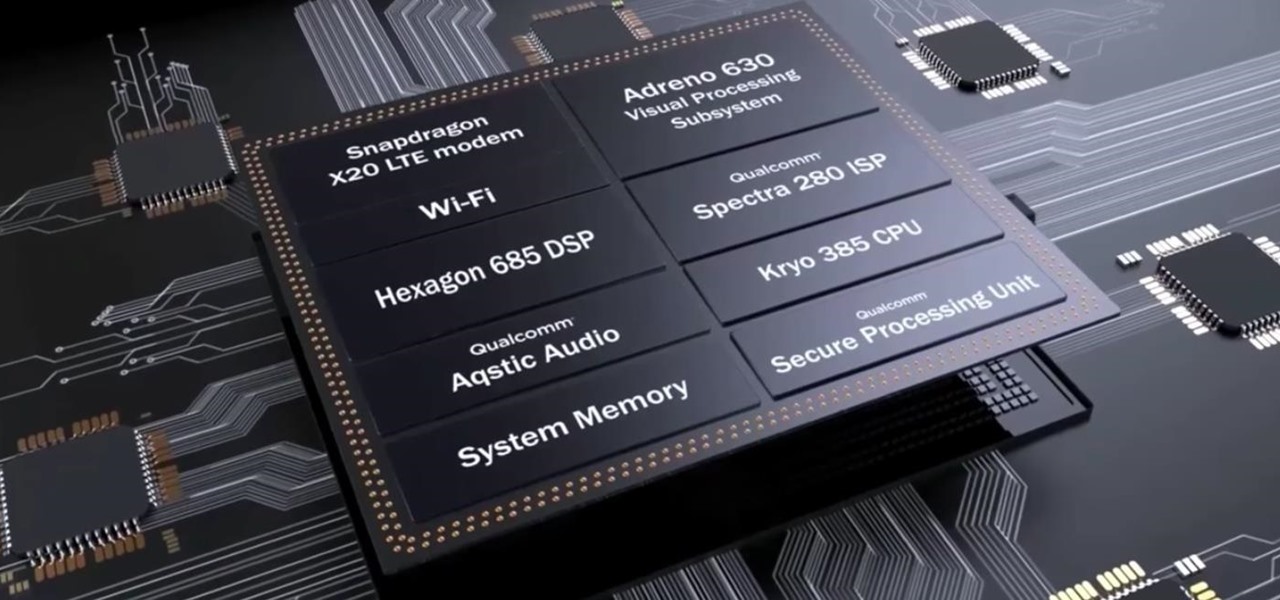
After the success of the Snapdragon 835, Qualcomm now has its eyes set towards the future with the arrival of its next-generation SoC, the Snapdragon 845. Debuting alongside the Samsung Galaxy S9, the 845 is now set to take over the market for flagship Android phones in 2018.

Local port forwarding is good when you want to use SSH to pivot into a non-routable network. But if you want to access services on a network when you can't configure port-forwarding on a router and don't have VPN access to the network, remote port forwarding is the way to go.

Last month, BMW rolled out its playful take on augmented reality with Snapchat, and now the automaker is bringing that same immersive computing whimsy to iOS directly.

A weak password is one that is short, common, or easy to guess. Equally bad are secure but reused passwords that have been lost by negligent third-party companies like Equifax and Yahoo. Today, we will use Airgeddon, a wireless auditing framework, to show how anyone can crack bad passwords for WPA and WPA2 wireless networks in minutes or seconds with only a computer and network adapter.

Hackers can be notoriously difficult to buy gifts for, so we've curated a list of the top 20 most popular items Null Byte readers are buying during their ethical-hacking studies. Whether you're buying a gift for a friend or have been dying to share this list with someone shopping for you, we've got you covered with our 2017 selection of hacker holiday gifts — just in time for Christmas.

Augmented reality is making many of our childhood dreams from Star Wars come true. A week after Lenovo gave us the ability to actually play Holochess, Apple has now made it possible to take live video of ourselves and layer on a (non-3D) hologram-like effect, closely resembling the famous Star Wars hologram scene featuring Princess Leia decades ago.

The Watch Dogs video game series came out in 2014, enamoring audiences with the idea of a seemingly magical smartphone that could change traffic signals, hack web cameras, and even remotely control forklifts. This may sound like science fiction, but The Sonic uses a customized flavor of Kali Linux to allow you to unleash the power of Kali from any smartphone — all without the need to create a hotspot to control it.

The dark web is an intimidating place for a newbie hacker, but it's a powerful tool once you've learned to navigate it safely. To help you out with that, this guide will cover some need-to-know information for traversing the dark corners of the internet while keeping your identity and data safe. (Hint: Using Tor is not enough.)

Two salsa dancers who also happen to be programmers are soon releasing an app called Dance Reality, made with Apple's ARKit. Through this app, you will be able to practice your dancing with augmented reality as your teacher right from your iPhone.

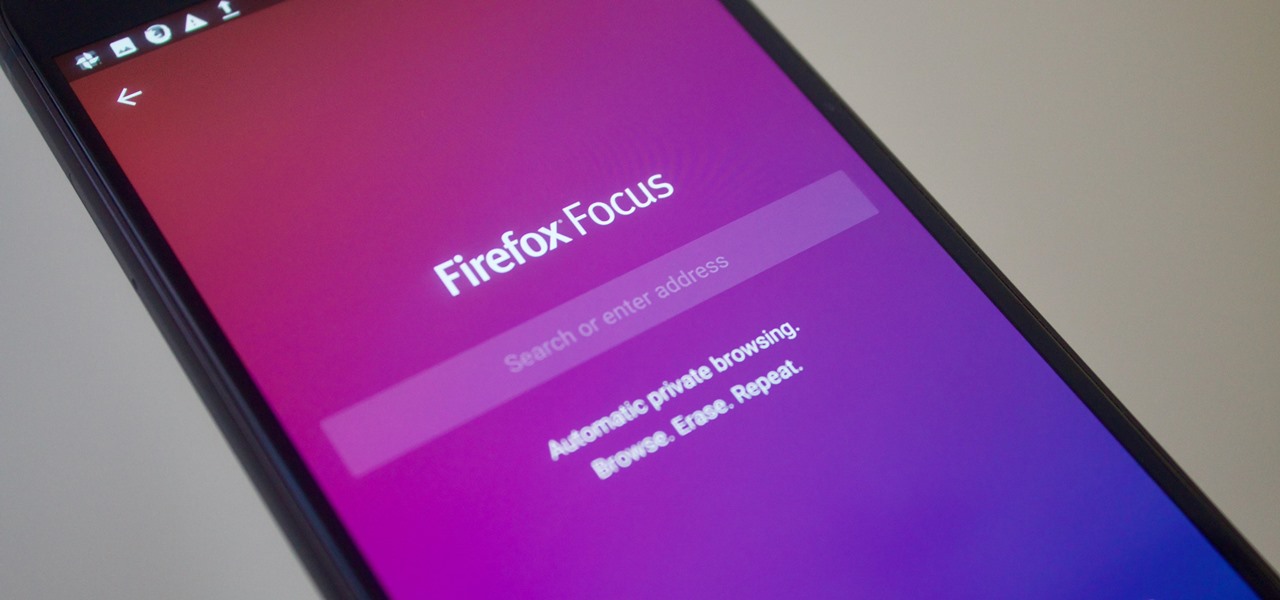
Firefox Focus is Mozilla's effort to make your internet experience a little more secure. Originally released in November 2016 for iOS, Focus blocks internet trackers, search history, anything that gets in the way of a clean, private browsing experience.

Shapr is a new networking app that aims to help professionals connect more efficiently, and draws much of its format from dating-focused social networking apps. Shapr could be especially useful for those who have recently moved into their industry or location, and for those seeking employers or employees. For example, the app already has 65,000 users just in New York City alone.

An innovative new wound dressing has been developed by a research team at Lodz University of Technology in Poland that uses crustacean shells to create a bandage that packs an antimicrobial punch — and even more potential to help solve a global problem.

It was nice while it lasted. Samsung users who managed to get their hands on the Galaxy S8 or S8+ early enjoyed the ability to launch any app through the dedicated Bixby button. Unfortunately, Samsung wasn't all that down with us using the Bixby button for purposes other than its intended use — to provide quick access to Samsung's new virtual assistant.

To keep fungal pathogens at bay in their crowded homes, wood ants mix potions to create powerful protection for their nest and their young.

Cortana, a strong competitor to Apple's Siri and the Google Assistant, has just been updated for beta testers on Android. The update introduces some sleek redesigns of both the look and features of the app, developing anticipation for the official update.

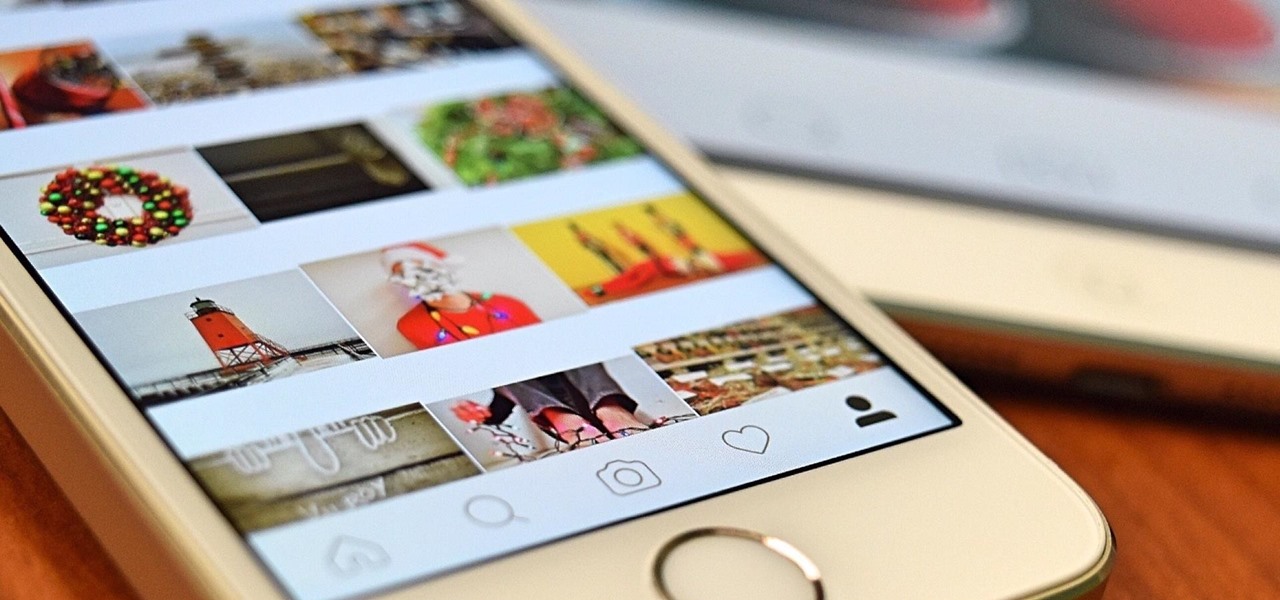
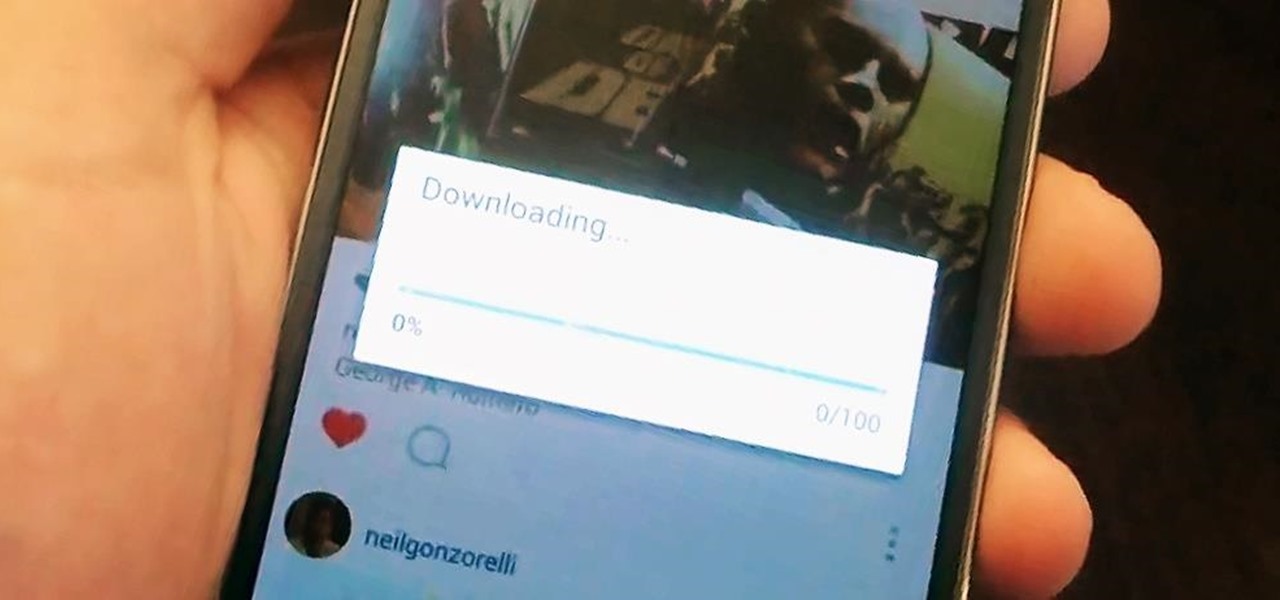
Starting today, you'll have the opportunity to save all your live Instagram videos to your phone at the end of each broadcast session. The latest update to the Instagram app now allows you to rewatch already-played broadcasts and gives you the ability to share them later on.

With tools such as Reaver becoming less viable options for pen-testers as ISPs replace vulnerable routers, there become fewer certainties about which tools will work against a particular target. If you don't have time to crack the WPA password or it's unusually strong, it can be hard to figure out your next step. Luckily, nearly all systems have one common vulnerability you can count on — users!

HoloMaps, an application by Seattle-based Taqtile, is available for free on the Windows Store. Taqtile, whose Vice President of Product Management was Microsoft's former Director of Business Development, is one of the few partners currently in the Microsoft HoloLens Agency Readiness Program. This interactive 3D map they have created, powered by Bing, offers more than just a top-down view of the world on the HoloLens.

The Microsoft HoloLens mixes the digital world with the physical one, allowing you to coexist with holograms of your choosing. But those worlds won't fully blend until we can experience it all together and create for each other. Vuforia could make that possible in the near future.

As we get closer to the release of the iPhone 7 this September, more and more details are emerging about the features the new smartphone could have. The well-regarded analyst Ming Chi-Kuo of KGI Securities, who has an uncanny ability to predict new Apple features, has reported another detail involving a dual-lens camera on the upcoming iPhone 7 Plus model.

At Apple's highly anticipated special event held today at their headquarters in Cupertino, California, it was announced that their latest software update, iOS 9.3, would be available to the public complete with several new additions. The most notable element of this announcement was two-fold, in the form of new modifications to the Night Shift mode and the Notes app. With regards to Night Shift, the feature is designed to prevent your iPhone from giving you restless nights by adjusting settin...

Five Phases of Hacking:- The five phases of Hacking are as follow:

These days, if you're having friends over, they'll probably ask to log into your Wi-Fi network before asking for a drink. But if you've forgotten your password, it can be quite hard to find, since most devices obscure the characters with asterisks.

Welcome back, my greenhorn hackers! As expected with Null Byte's dramatic growth over the last year, we have added many new aspiring hackers who are still lacking in the basics of networking. In addition, with the new "White Hat" certifications coming out shortly, the exam will require some basic networking skills and knowledge to pass.

I am very new to Null Byte but I find much of its content and community incredibly interesting. I spent quite a bit of time just chronologically going through the posts and I noticed a common theme in many of the beginner posts. Many people seem to want to know the 'secret' or a paragraph on "How to Hack" and become a hacker in a few minutes. I started off this post as a reply to a question from a beginner but thought it might be beneficial to have for those stumbling across this site.

Long time reader, first time 'How To' poster. This tutorial has been highly requested. Here are the steps to perform a Pixie Dust attack to crack a WiFi password that has WPS enabled.

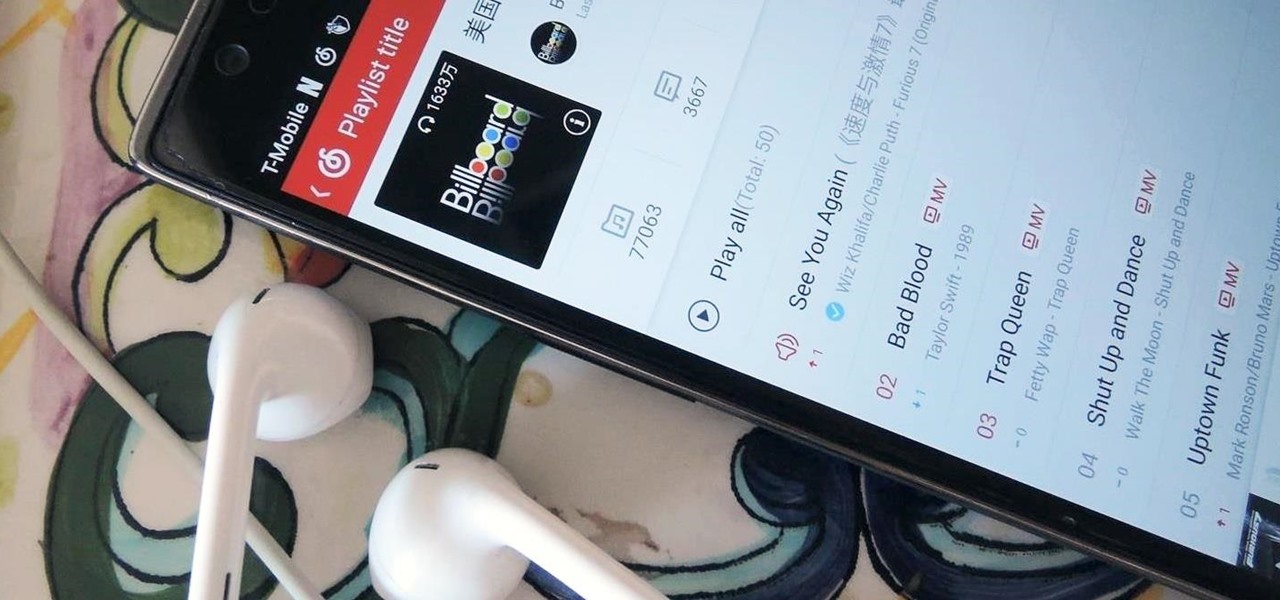
We recently lost Grooveshark, the free music streaming service that supplied users with a huge catalog of free music anytime, anywhere. Since its shutdown, I have been scrambling to find a half-decent alternative, and my expectations were more than exceeded when I found NetEase Music.

Considering how the Apple Watch works as an extension to your iPhone, it would've seemed like a no-brainer to include the ability to view your iPhone's battery life from the Watch, but in true Apple fashion, they did not.

Just recently, Snapchat decided to implement a feature that it had long been lacking—the ability to play music and record a video at the same time. For those of us that are jailbroken, we've had this feature for some time, but now that everyone has the ability, how should you use it?

Welcome back, my tenderfoot hackers! A short while ago, I started a new series called "How to Spy on Anyone." The idea behind this series is that computer hacking is increasingly being used in espionage and cyber warfare, as well as by private detectives and law enforcement to solve cases. I am trying to demonstrate, in this series, ways that hacking is being used in these professions. For those of you who are training for those careers, I dedicate this series.

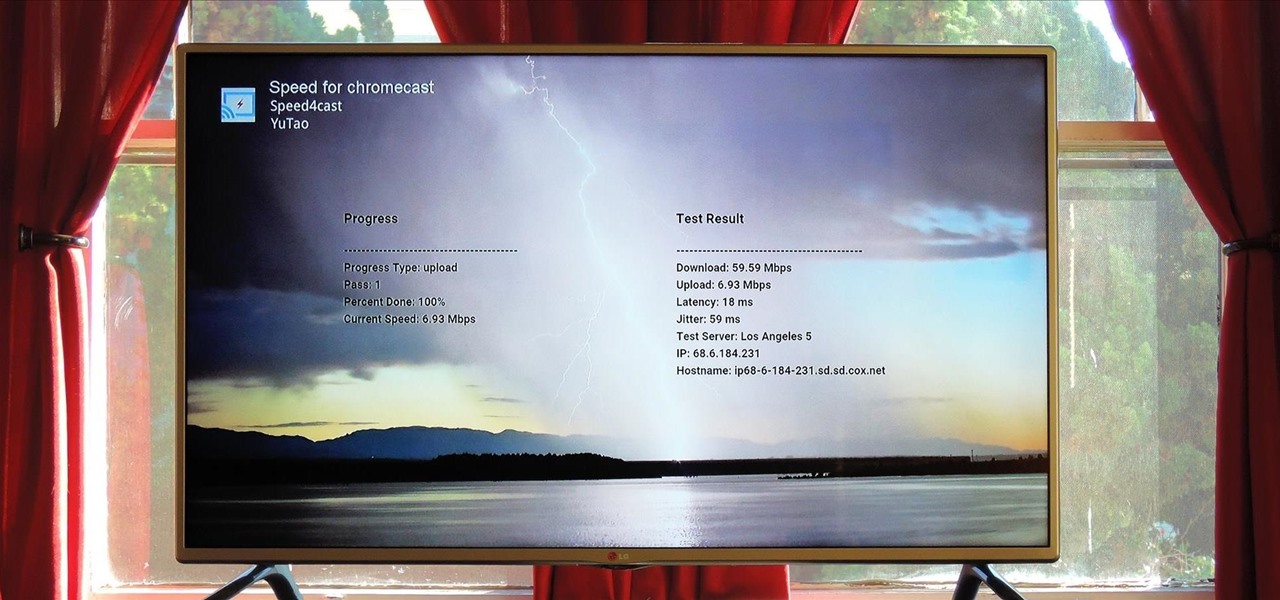
At its core, the Chromecast is essentially a web browser on a stick. When you cast content from your computer or smartphone, all you're really doing is telling the Chromecast which website to load.

Scrolling through my Instagram feed, I inevitably come across an image or video that I genuinely like amongst the countless selfies and plates of food porn. Naturally I want to save this image before it's buried under new posts from the heaps of people I follow, but I'm left stranded with only the ability to take a screenshot.

Watching a YouTube video while surfing the web is real multitasking, and easily achievable on the LG G3. Like the "Multi Window" feature on Samsung Galaxy devices, the G3 has the ability to run two separate apps simultaneously with its Dual Window feature.

While the legality of recording phone conversations varies from state to state, it's still a sought-after feature for most people. How else are we going to shame all of those bad Comcast customer service reps? Since it's a legal gray area, HTC and other smartphone manufacturers have omitted call recording capabilities from their devices.

The term "selfie" is taking the world by storm. Having been around since 2002, the slang word for "self-portrait" went into hyperdrive thanks to the addition of front-facing cameras on mobile devices. It's even popular enough to have been included in the Oxford Dictionary, and to have broken Twitter (thanks to the Oscars selfie taken by Ellen DeGeneres).

Welcome back, my hacker apprentices! I recently began a new series on digital forensics to show aspiring hackers what the forensic investigator can do and see while investigating a cyber attack. This is the second installment in that series and will focus upon network forensics. In other words, what can a network forensic investigator learn about the attacker during an investigation and how.

Why unlock your Samsung Galaxy S3 to use with a different SIM card? One possible reason is that you love your phone, but not your cellular provider because of the poor service or an unreliable connection. If you purchased a Samsung GS3 with AT&T, T-Mobile, etc. on a contract, it might be locked for a specific amount of time called the contract period.