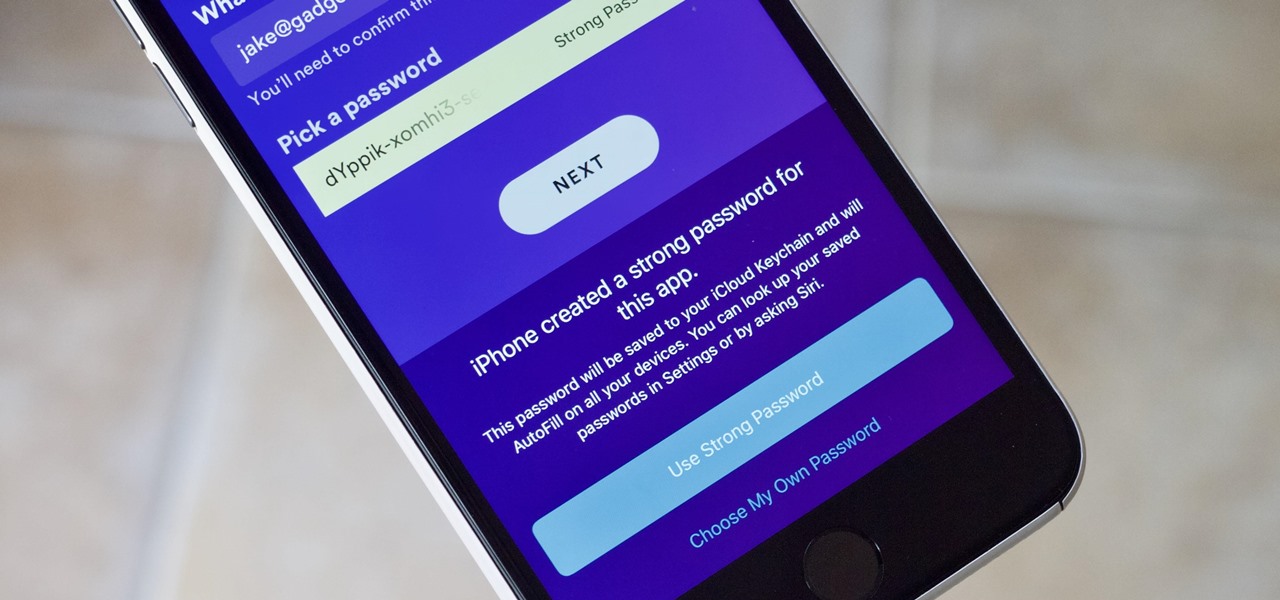
Maybe you prefer writing passwords in a notebook. Maybe you like creating your passwords yourself. Whatever the case, you don't like iOS 12's new automatic password generator, and you don't need it to pop up every time you enter a new password in Safari or a third-party app. Lucky for you, iOS 12 lets you disable the feature altogether. Unfortunately, that perk comes with a catch.

Google Photos integrates with Google's ecosystem to bring you awesome features like the ability to identify landmarks, track down products you've photographed, and so much more. Now, if you need to translate foreign words in any of your pictures, the app has you covered as well.

Russian cyber disinformation campaigns have many missions, but one of particular interest is using technology to monitor, influence, and disrupt online communications surrounding culturally sensitive topics or protests. The ability to watch these events, and even filter positive or negative tweets to amplify, gives rise to the ability to execute a number of disinformation campaigns.
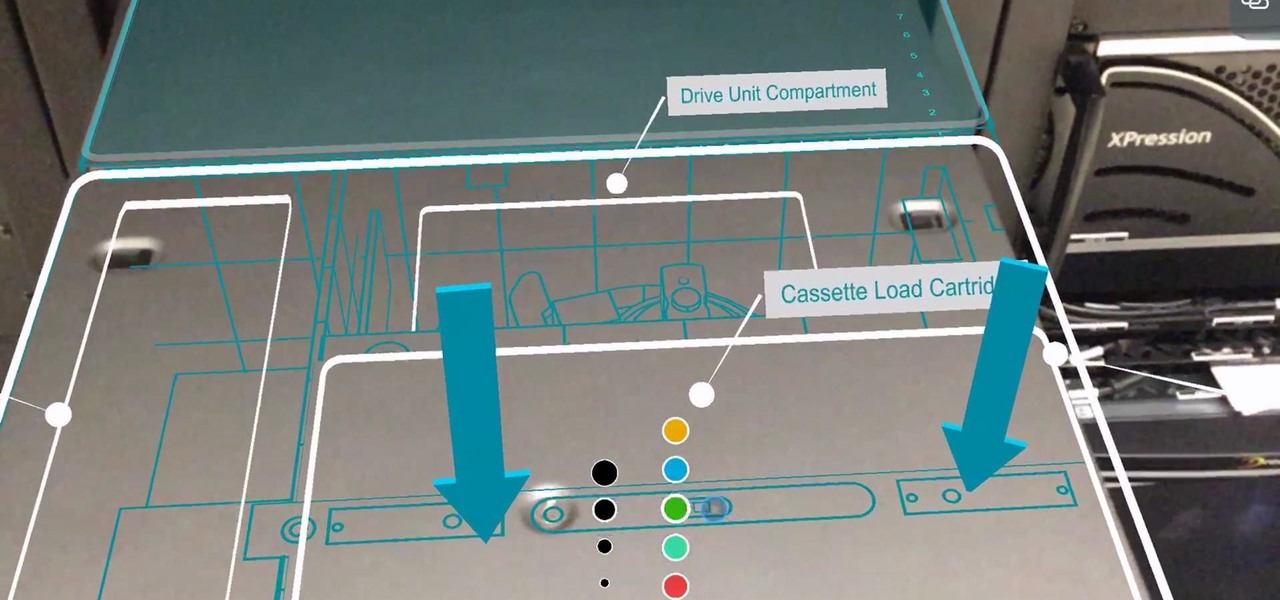
Enterprise augmented reality software maker Scope AR is bringing the powers of its two productivity apps together like the Wonder Twins into the form of a single app.
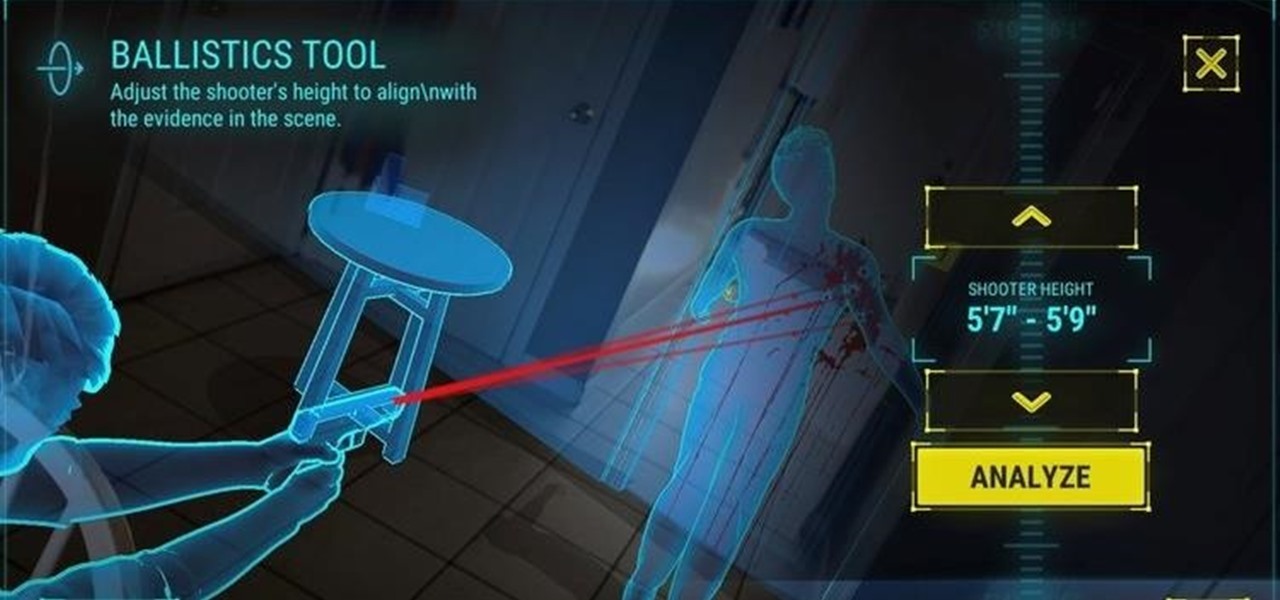
The crime procedural show is the perhaps the most direct path to the average TV viewer's heart. Could the same hold true for augmented reality games?
Following San Francisco-based Occipital's successful Structure Sensor Kickstarter campaign, the release of its Bridge AR/VR headset, as well as a string of technology and company acquisitions, the company has built a rather strong name for itself in the AR community. And now, with the first public release of its Bridge Engine on Thursday, the company continues to expand the features its platform has to offer, with hopes of bringing in more developers to utilize it.

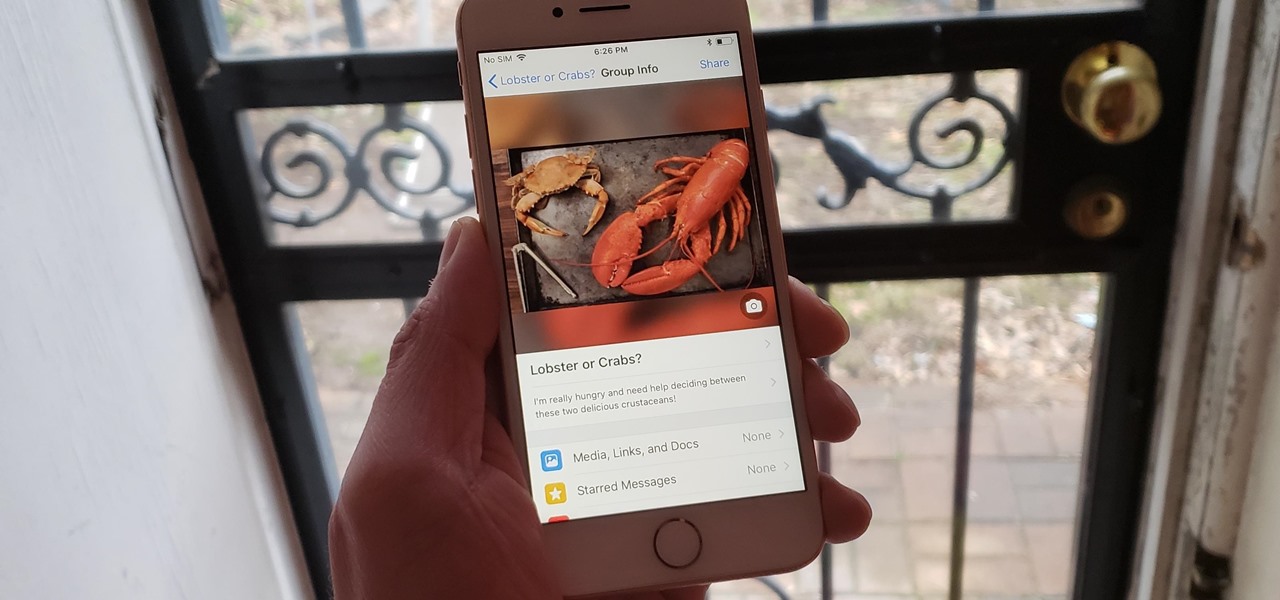
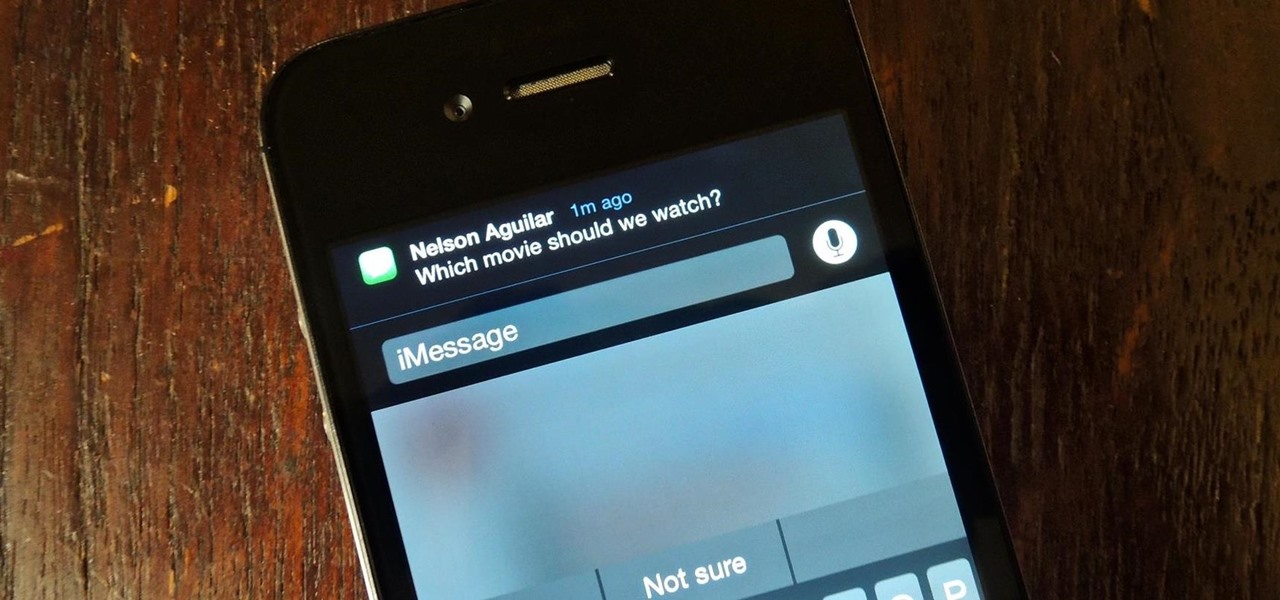
There's a fine line between order and chaos in group chats. With all the cross-talk, threads can easily devolve into a random mess that has nothing to do with the original discussion topic. WhatsApp group chats certainly aren't immune to this problem, but they've recently taken a step in the right direction.

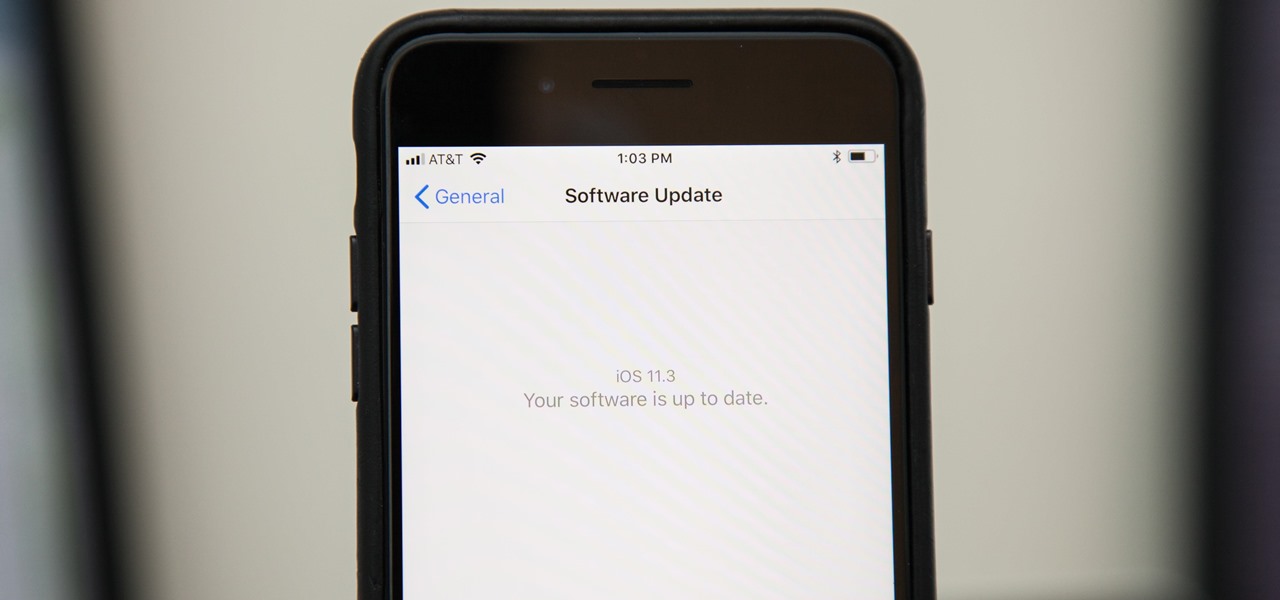
Three months after its promise, Apple has pushed out an iOS update that gives you important information about the health of your iPhone's battery. This means you no longer need tools such as Geekbench and Battery Life to determine whether or not you need a replacement battery.

As expected, Apple began pushing out the final version of iOS 11.2.5 to all iPads, iPhone, and iPod touches today after 41 days of beta testing. Highlights include a fix for the ChaiOS vulnerability, a persistent Now Playing bar in Music, and some signs of AirPlay 2 just in time for the HomePod launch on Feb. 9.

As the Samsung world anxiously awaits an official Android Oreo update, some Galaxy Note 8 users are waking up to find their devices have jumped the line. Are you one of them?

Researchers at Disney have demonstrated the ability to render virtual characters in augmented reality that are able interact autonomously with its surrounding physical environment.

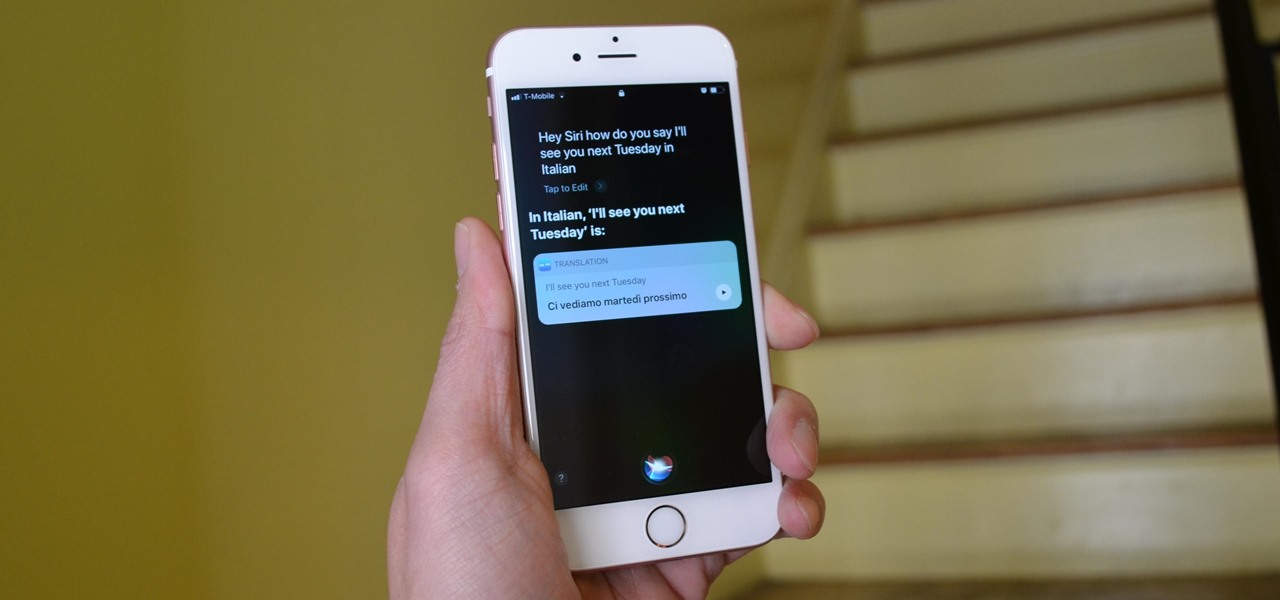
With iOS 11, Apple is working hard towards breaking down language barriers to bring people closer together than ever before, as evidenced by Siri's newfound ability to directly translate words and phrases in different languages. In the near future, it's easy to imagine Siri as our very own real-life BabelFish.

While the USB Rubber Ducky is well known by hackers as a tool for quick in-person keystroke injection attacks, one of the original uses for it was automation. In this guide, I'll be going the latter, explaining how we can use it to automate Wi-Fi handshake harvesting on the Raspberry Pi without using a screen or any other input.

Beijing- and Seattle-based DataMesh have announced the release of a new enterprise geared mixed reality middleware — MeshExpert. This solution for collaborative interaction with dynamic data is made up of two primary components: MeshExpert Live!, a 4K mixed reality capture system built off of the Microsoft Spectator View, and MeshExpert DataMix, which offers the ability to blend different types of data with XR and mobile hardware.

Just like in the Spy Kids 3D movie, US soldiers may soon upgrade their mission planning from 2D to 3D. Welcome to the wonderful world of augmented reality, US Army.

360world, a Hungary-based tech company involved in motion control and augmented reality, released information today about their latest products, the CLAIRITY HoloTower and CLAIRITY SmartBinocular. These tools are designed to bring augmented reality into the hands of air traffic controllers, via Windows Mixed Reality, to greatly improve their workflow over tools already in use.

A new study just out reveals that HIV takes hold in the human body with the help of cells that usually work to heal, not kill.

Mimesys, whose core focus has always been about creating holographic representations of humans for virtual and augmented reality, has released a video showing off their holographic communication platform in action. This new communication tool uses a combination of virtual reality, with the HTC Vive and a Kinect, and mixed reality, with the HoloLens, to allow the users to have virtual meetings from anywhere in the world as though they are in the same room.

"Necessity, not novelty," is a phrase I use often when it comes to HoloLens development. It would be fair to call it my mantra, or mission statement, as I prototype and explore software creation on this new frontier of mixed reality.

A scary piece of malware just got a lot more terrifying this week. Security firm Comodo reports that "Tordow," a banking Trojan first uncovered in September 2016, received a massive update this December.

I've seen my fair share of heartbreaks when it comes to used phones. As a repair tech, I often had to try and help out customers who bought used handsets which turned out to be useless, either because it was stolen or not working on their carrier's network. More often than not, there was very little I could do. To help you from being stuck in the same situation, here are some tips to prevent you from getting scammed out of your hard earned money when buying a used handset.

Dutch police are using a system very similar to Pokémon GO on smartphones, but they aren't walking around trying to catch little pocket monsters. The purpose of this system is to give augmented reality help to first responders who may be less qualified to work a fresh crime scene. If successful, the idea of a contaminated crime scene could be a thing of the past.

Social engineering is a pretty important item in a hacker's toolkit. In Mr robot there was a time, we saw Elliot using social engineering to gain access to his therapist's boyfriend's email and bank accounts by calling him and pretending to be someone from his bank, then Elliot asked him for some info that were really useful to gain access to his account, the target believed to be someone from the bank and gave him the info Elliot was looking for. But How Is It in the Real World?

If you haven't read the last article, feel free to stop by and give it a read, but abstaining from reading it will not, for the most part, be detrimental to your understanding.

Scanners are much too cumbersome to fit in a pocket, but with the use of just one application, you can replace all that bulky hardware with your Android smartphone and take it with you wherever you go. All you need to do is find the scanning app that fulfills your needs. Here are our five favorites that are good for business pros and average joes alike.

Unless you've been living under a rock or ignoring recent news headlines, Ashley Madison, the dating site for married people (or individuals in a committed relationship) has recently been hacked. Millions of their users are shitting their pants, and for good reason, as all of those accounts have just been leaked.

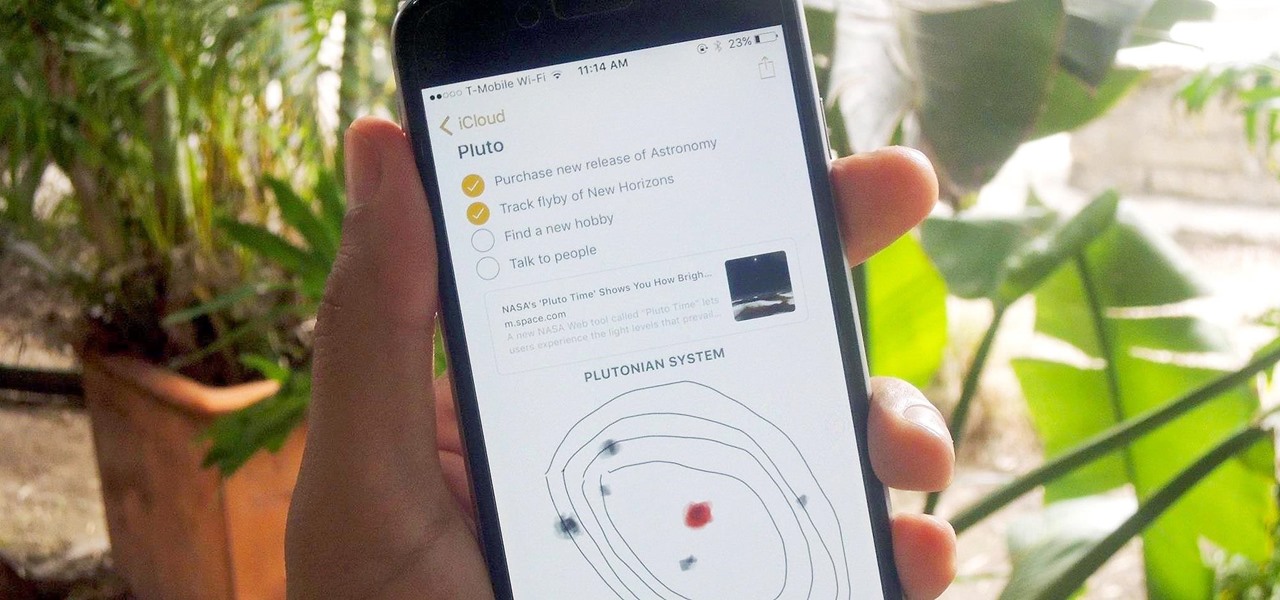
Notes on iOS has never been a particularly great app due to a lack of overall features compared to other note-taking apps like Evernote or Microsoft OneNote.

Hi there again, aspiring hackers (and veterans as well)! I'm going to explain how to perform a dictionary attack on a WPA/WPA2 protected network with Wifite. Please note that this doesn't work with WPA Enterprise For that end, you'd have to use an Evil Twin to get the "Enterprise" auth attempt, and then crack it.

In the shadow of Facebook's announcement for third-party app development on Messenger, the company has announced the release of a whole new application called Riff, a creative tool for making videos with friends.

While I consider myself to be a pretty organized guy, there are often times where I just can't find a file I put on my phone. Most of the time, when I download a file it goes automatically into my Download folder, but when I use a third-party to download other files, like torrents, they could end up in a number of places. Filtering abilities on file explorers often fall short, so it was time to find an app that would automatically sort files in real time.

It's not enough for me to just listen to a mindless EDM song that can be retooled as a torturing method for Guantanamo Bay. As an actual fan of music, I yearn for substance and depth. Artists like Morrissey, Kurt Cobain, and John Lennon impacted lives with not only their music, but the subject matter of their songs.

Thanks to the steady increase in quality of smartphone cameras, it's easier than ever to take amazing photos or video without thinking twice. If you've been to a concert in the last five years, you undoubtedly know what I mean. But it turns out that using your camera as a new set of eyes might actually be ruining your ability to remember events on your own, rather than helping you to hold on to the good times.

Notification banners and alerts aren't new to iOS, but the ability to expand and interact with them is. Apple's new iOS 8 has ushered in some small, yet convenient features to the banner and alert notifications that make them truly interactive. The new additions, as you will see, makes it easy to complete simple tasks without leaving the current screen you're in.

The older I get, the more my Friday nights involve watching Netflix at home with a bottle of Maker's Mark and a box of Oreos. Netflix is a big part of my life, and I'm not alone. YouTube and Netflix make up over 50% of all activity on the Internet, so it might be worth your time to understand why Netflix seems to cause so many headaches and what can be done about it.

One draw that Samsung's Galaxy S line has had over the Google Nexus 4 and 5 and the HTC One (though the M8 appears to be following suit) is expandable storage. Pop a microSD card into the slot and you have extra storage for music, photos, and even apps themselves in some cases.

Welcome back, my neophyte hackers! Have you ever had a neighbor that you're certain is up to no good? Maybe you've seen him moving packages in and out at all hours of the night? Maybe you've seen people go into his home and never come out? He seems like a creep and sometimes you hear strange sounds coming from his home? You know he's up to no good, but you aren't sure what it is exactly.

Welcome back, my fledgling hackers! The database is the hacker's "pot-of-gold," as it contains information that is very valuable to both the business and the hacker. In this, the second of my series on hacking databases, we're on the "hunt" for Microsoft's SQL Server. Although far from the most commonly used database (Oracle hold's that title), Microsoft's SQL Server is very often found in small-to-medium sized businesses. Even a few big businesses use it.

Welcome back, my fledgling hackers! One of the first issues any hacker has to address is reconnaissance. Before we even begin to hack, we need to know quite a bit about the target systems. We should know their IP address, what ports are open, what services are running, and what operating system the target is using. Only after gathering this information can we begin to plan our attack. Most hackers spend far more time doing reconnaissance than exploiting.

Welcome back, my fellow hackerians! Today we'll be hacking Facebook profiles on your local network. You may think, "How is this useful, nobody but me is using my network." Well, you can use this on other Wi-Fi networks that are available for free (like at Starbucks) and crack their precious Facebook profile!

Welcome back, my nascent Hackers! In my last blog, we looked at a passive way to gather information necessary for a hack. The advantage of using passive recon is that it's totally undetectable, meaning that the target never knows you're scouting them and you leave no tracks. The disadvantage, of course, is that it's limited to only some websites and not entirely reliable.